SHA1 Collision Signals the End of the Algorithm’s Viability
 The most significant danger for a hash algorithm is when a “collision”—which happens when two different pieces of data produce the same hash value—occurs. While the theoretical chances of a SHA1 collision have been covered before, there have been no reports of an actual collision until recently.
The most significant danger for a hash algorithm is when a “collision”—which happens when two different pieces of data produce the same hash value—occurs. While the theoretical chances of a SHA1 collision have been covered before, there have been no reports of an actual collision until recently.
Researchers from Google teamed up with the CWI Institute in Amsterdam to publish a proof of concept which is the first documented case of a SHA1 collision. The new research presented two PDF files that displayed the same hash but had different visual content.
According to Google, while the collision took a significant amount of computational resources to pull off, it is still much faster than trying to crack a SHA1 hash algorithm using brute force methods.
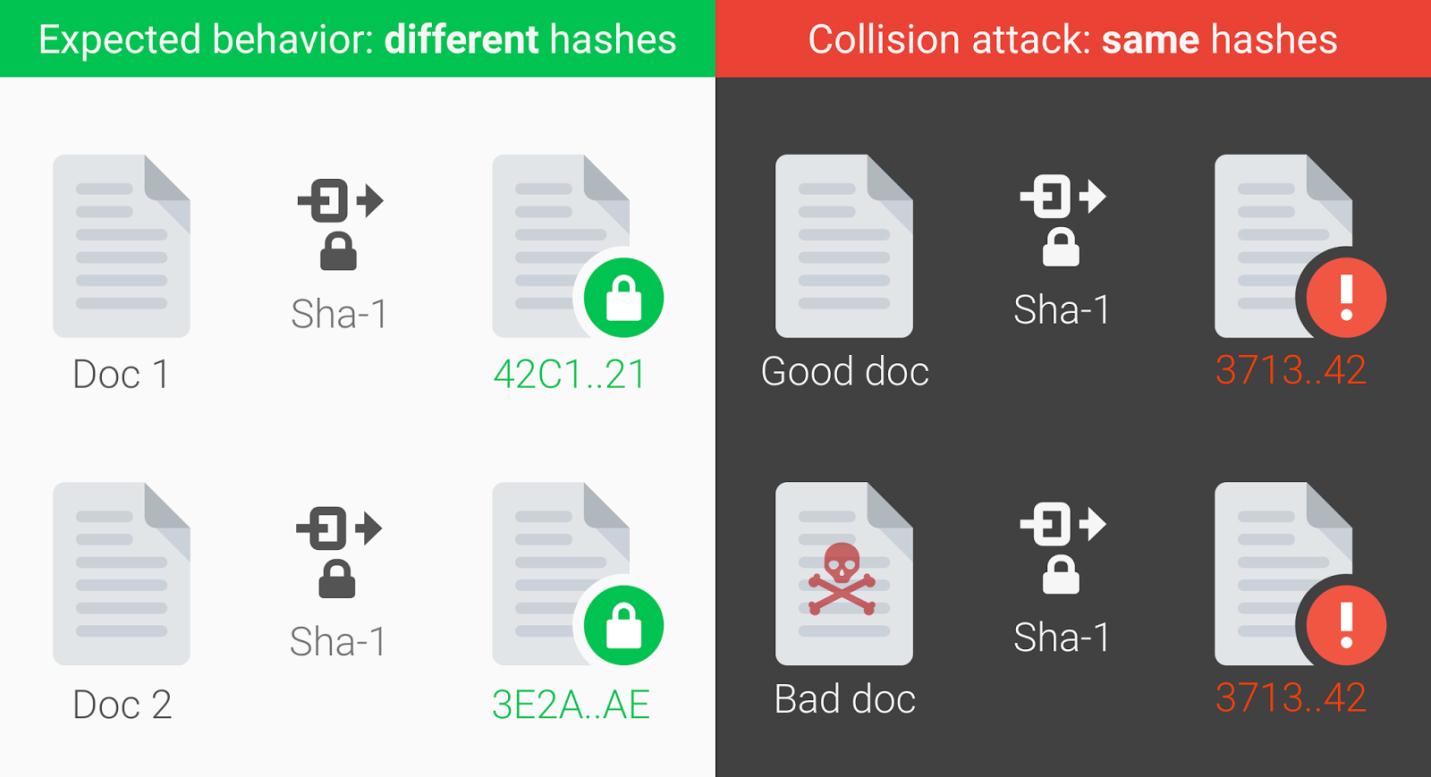
Image via Google Security Blog
What does this development implicate?
A cryptographic hash function can be compared to a person’s fingerprint. Theoretically, each piece of data comes with its own unique identifiable hash value, so even seemingly similar files that have minute differences would still have different hashes. A SHA1 collision is similar to a person “copying” another person’s fingerprints, then using the copied fingerprints to gain access to areas or files that require biometric data.
In the case of a SHA1 collision, HTTPS websites that use SHA1 certificates will be vulnerable to attacks that duplicate a specific digital data’s SHA1 hash value. Seemingly “secure” websites that are protected by the HTTPS protocol might turn out not to be safe at all, making the content of these sites susceptible to man-in-the-middle attacks.
SHA1 security concerns are nothing new, as the algorithm’s vulnerabilities have been an issue long before the collision attack. In fact, vendors such as Microsoft and Google have already implemented plans to gradually phase out SHA1 before the end of the decade. Microsoft announced SHA1 deprecation in 2013, while Google followed suit a year later. Mozilla announced in October 2016 that starting 2017, the Firefox browser will show an “Untrusted Connection” error whenever users access websites that still use SHA1 certificates. The US government itself recommended as early as 2015 that federal agencies stop using it for applications that require collision resistance such as the creation of digital signatures and time stamps.
While the SHA1 collision is definitive proof that the algorithm can be compromised, it still took Google and CWI’s researchers a massive amount of computing power (nine quintillion SHA1 or 6,500 CPU and 110 GPU years’ worth of computations) despite all the technology available to them. This means that these kinds of attacks will be relatively rare since they require a large amount of resources. Still, with computational power simultaneously becoming more powerful and more affordable, the chances of these kinds of attacks happening only increase with time. As such, security professionals need to be prepared for potential scenarios involving actual SHA1 collision attacks.
Google has announced that the source code used in the attack will be published in 90 days, essentially giving websites that still use the SHA1 algorithm a deadline for migrating to more secure hash algorithms such as SHA256 and SHA3.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One