Security 101: Protecting Serverless and Container Applications with RASP (Runtime Application Self-Protection)
The demand for container and serverless technologies has increased in recent years. According to a market research and consulting firm, the global market size for containers is expected to grow from US$ 1.2 billion in 2018 to US$4.98 billion by 2023, while serverless architecture is projected to grow from US$7.6 billion in 2020 to US$21.1 billion by 2025. The increased demand for container and serverless technologies is due to the fact that enterprises can rely on them for scalability, efficiency, and cost-effectiveness when developing and deploying applications.
However, as with any burgeoning technology, container-based and serverless applications are not immune to risks and threats. It is only a matter of time before malicious actors, who are always casting wider nets to reach more potential victims, start targeting them frequently for various schemes. In this light, how can enterprises strengthen the security of such applications against potential attacks?
This article zeroes in on certain security considerations that developers need to know and the ways that they can build the best defense for container-based and serverless applications through runtime application self-protection (also known as RASP), a tool that incorporates security into an application at runtime.
What is RASP?
RASP is a security tool that runs on a server and begins functioning every time that an application runs. Simply put, RASP is designed to detect malicious behavior in real time. RASP is capable of protecting applications from attacks by analyzing both an application’s behavior as well as the context of that behavior.
What are the benefits of RASP?
In essence, RASP provides real-time protection to applications. RASP can intercept all kinds of traffic that indicate malicious behavior like SQL injection, cross-site scripting (XSS), vulnerabilities, bots, and attacks deployed through email, Slack, and other message types.
Because RASP is built directly into an application, it is innately capable of monitoring application behavior. Thus, RASP can prevent attacks with high accuracy as it can discern between attacks and legitimate requests, thereby reducing false positives and allowing security engineers to focus on combatting more serious problems.
In addition, RASP also offers better protection from zero-day exploits. RASP offers a short-term fix if a patch for an application is not readily available for an extended period. To add, RASP is not dependent on any type of signature for an exploit because the baseline for proper operation is the application itself.
How RASP protects serverless applications
To illustrate how RASP secures serverless applications, we demonstrate how a function of Amazon Web Services (AWS) Lambda — a serverless service that allows enterprises to run code without server provisioning and maintenance — can be secured using Trend Micro Cloud One™ – Application Security.
In the Trend Micro research paper “Securing Weak Points in Serverless Architectures: Risks and Recommendations,” Alfredo de Oliveira, a Trend Micro Senior Security Researcher, created a proof of concept that involves an AWS Lambda function granted with high permissions to highlight the risks of implementing bad code on a serverless system. Under such a condition, threat actors could alter the Lambda function timeout and subsequently perform attacks such as privilege escalation and data exfiltration. It should be noted that for this proof of concept, we have configured the Lambda administrative privileges. By default, Lambdas have no permissions aside from those defined by the customer. In this light, customers should always follow the principles of least privilege when defining an execution role.
Figure 1 illustrates the attack chain involving an AWS Lambda function granted with high permissions, as described in the above paragraph. It should be noted that Cloud One – Application Security libraries are already preinstalled in the system.
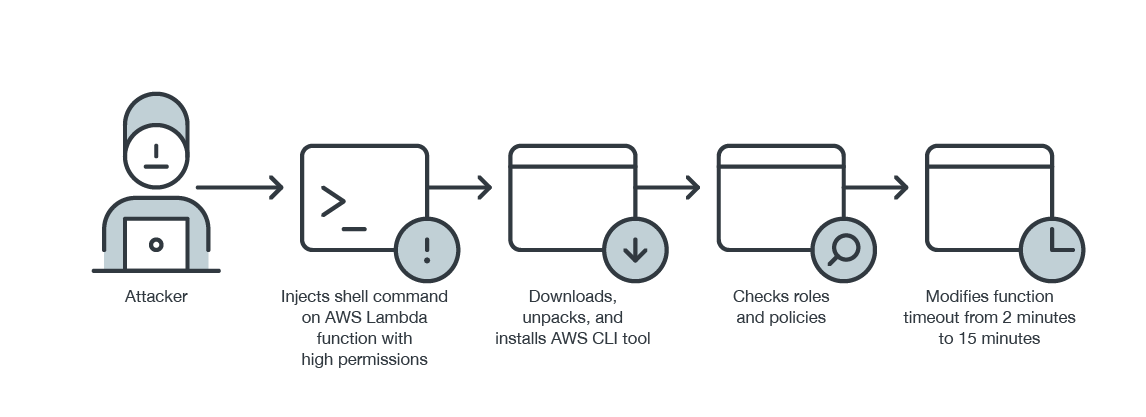
Figure 1. An attack chain involving an AWS Lambda function with high permissions
As shown in Figure 2, the Cloud One – Application Security console blocks the command injection attack.
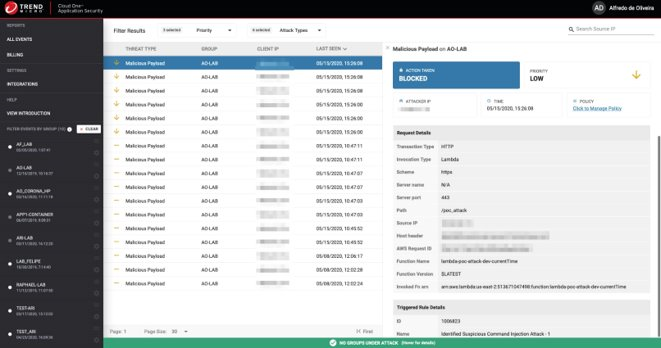
Figure 2. The Cloud One – Application Security console is able to detect the command injection attack.
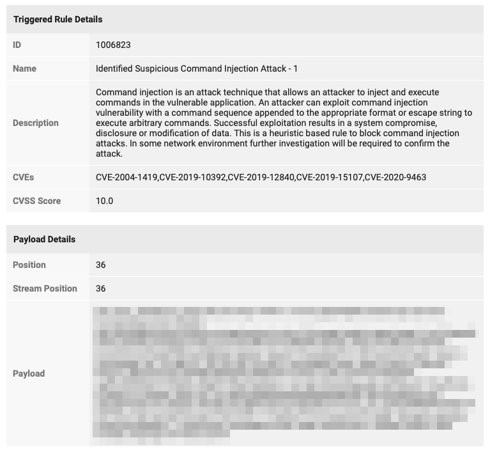
Figure 3. The Cloud One – Application Security console also provides a description of the suspected attack, the associated CVEs, and payload information.
The aforementioned Trend Micro research paper also highlights the need to secure different cloud services involved in developing serverless applications. As shown in Figure 4, Trend Micro Cloud One™ Conformity blocks IAM roles that are too permissive from being executed within the system.
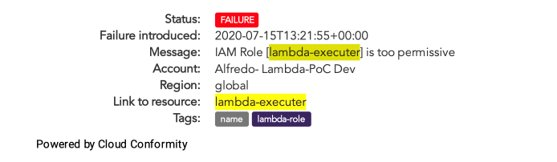
Figure 4. IAM roles that are too permissive are blocked by Cloud One – Conformity from being executed within the system.
How RASP can protect containers
In this section, we demonstrate how to secure a running container-based application on Azure Container Instances against SQL injection, as detailed in a LinkedIn article by Chuck Losh, a Trend Micro Solutions Architect.
First, a new deployment needs to be run and a purposely vulnerable PHP-based container of a DVWA image from a private Azure Container Registry needs to be pulled. In this test, Cloud One – Application Security libraries are already preinstalled in the system, as shown in Figure 5.
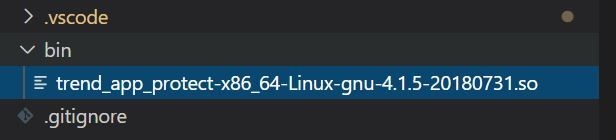
Figure 5. Cloud One – Application Security libraries that are added into the container image code
Once the deployment is executed through the Azure portal shown in Figure 6, we will see if everything works as intended. The end result should have the application calling to the Cloud One – Application Security dashboard for real-time protection.
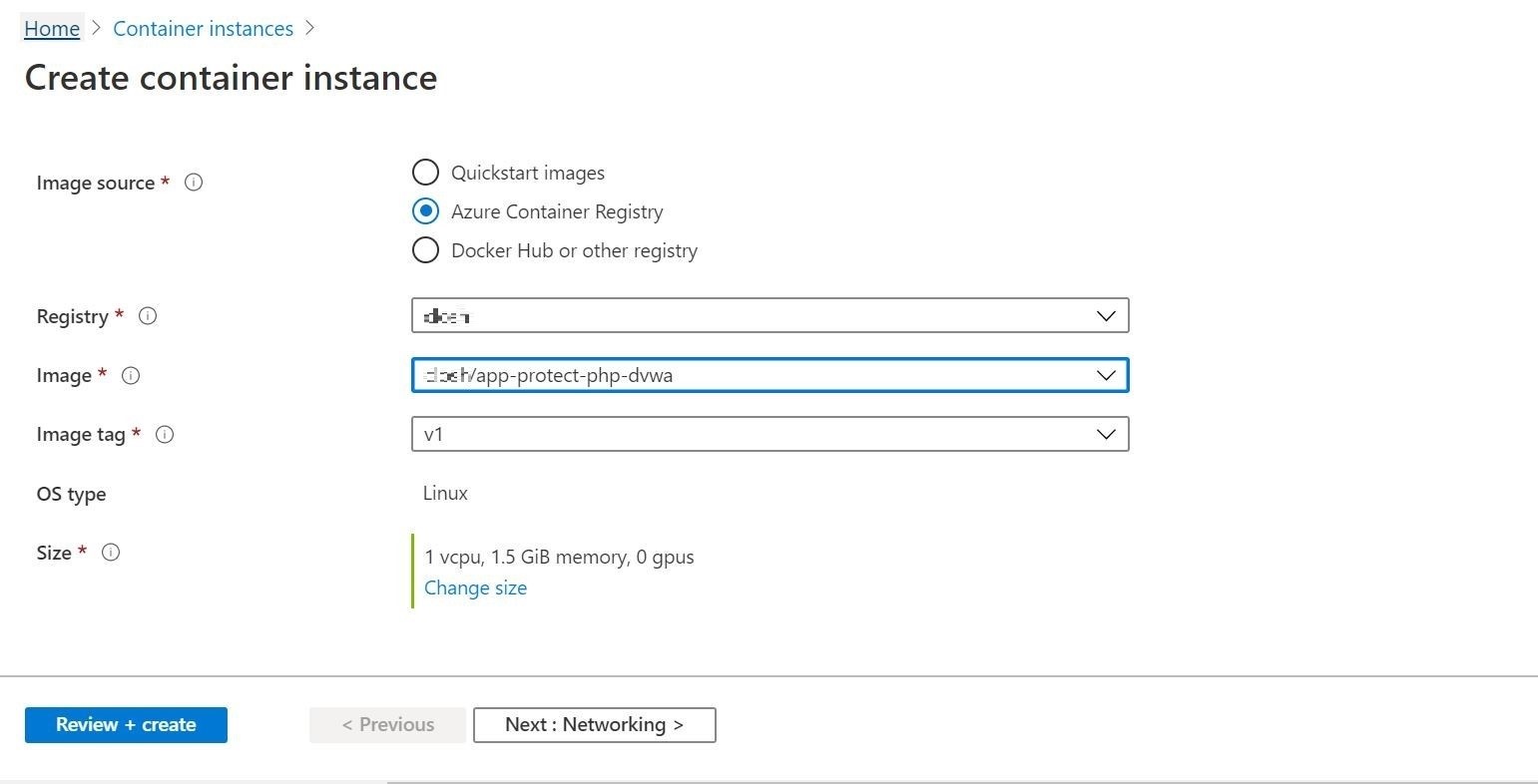
Figure 6. The container image that is executed through the Azure Portal
Upon configuring the setting requirements, the container instance should already start running. This can also be verified in the Azure Portal output, as shown in Figure 7.
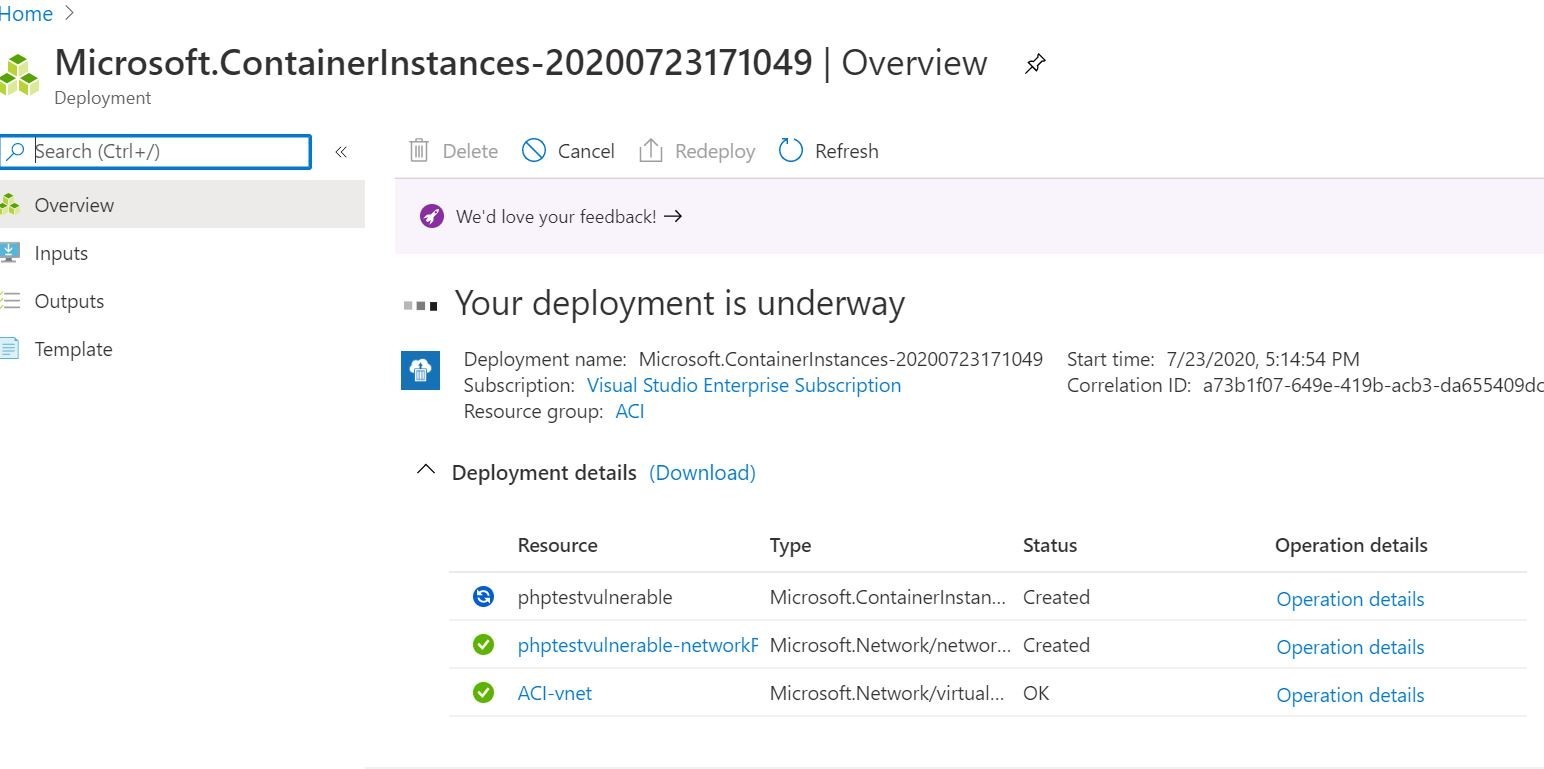
Figure 7. The Azure portal shows that the container deployment is already underway.
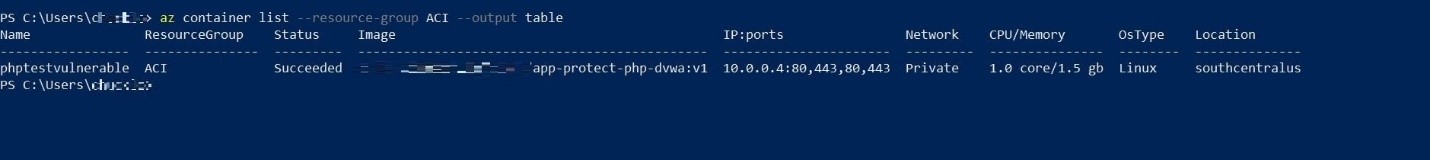
Figure 8. To further check if the container instance is running, the Azure CLI output can also be viewed.
The test web application can now be accessed. After logging in to the DVWA container-based web application, we will send an SQL injection attack, as shown in Figure 9. We can check the Cloud One – Application Security console later on if it can detect such malicious behavior.
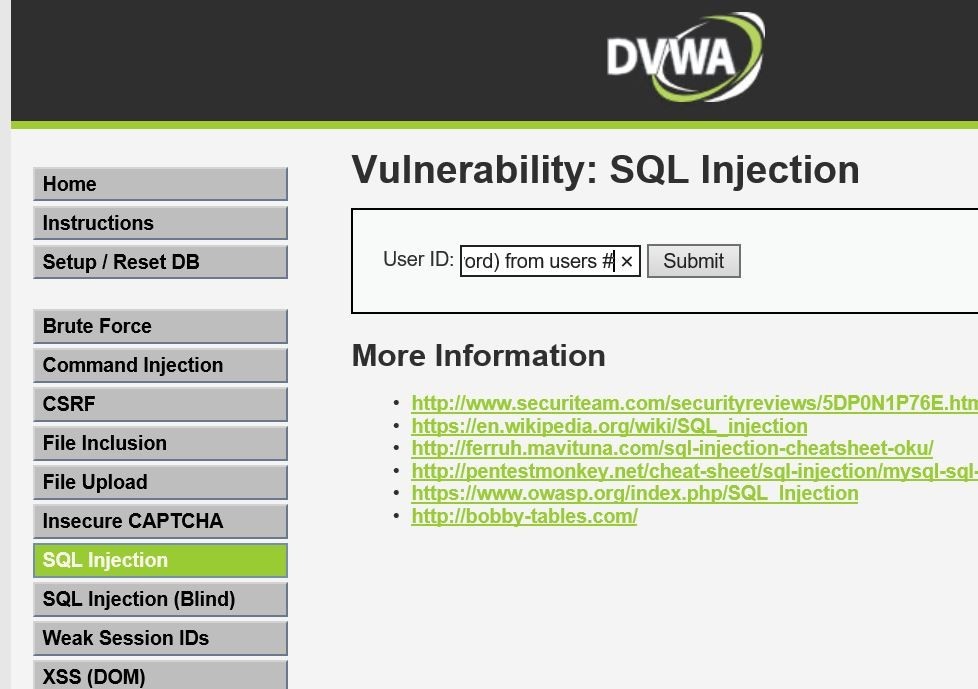
Figure 9. The SQL Injection attack submitted to the container-based application
As shown in Figure 10, the submitted request was blocked and detected by the Cloud One –Application Security console in real time.
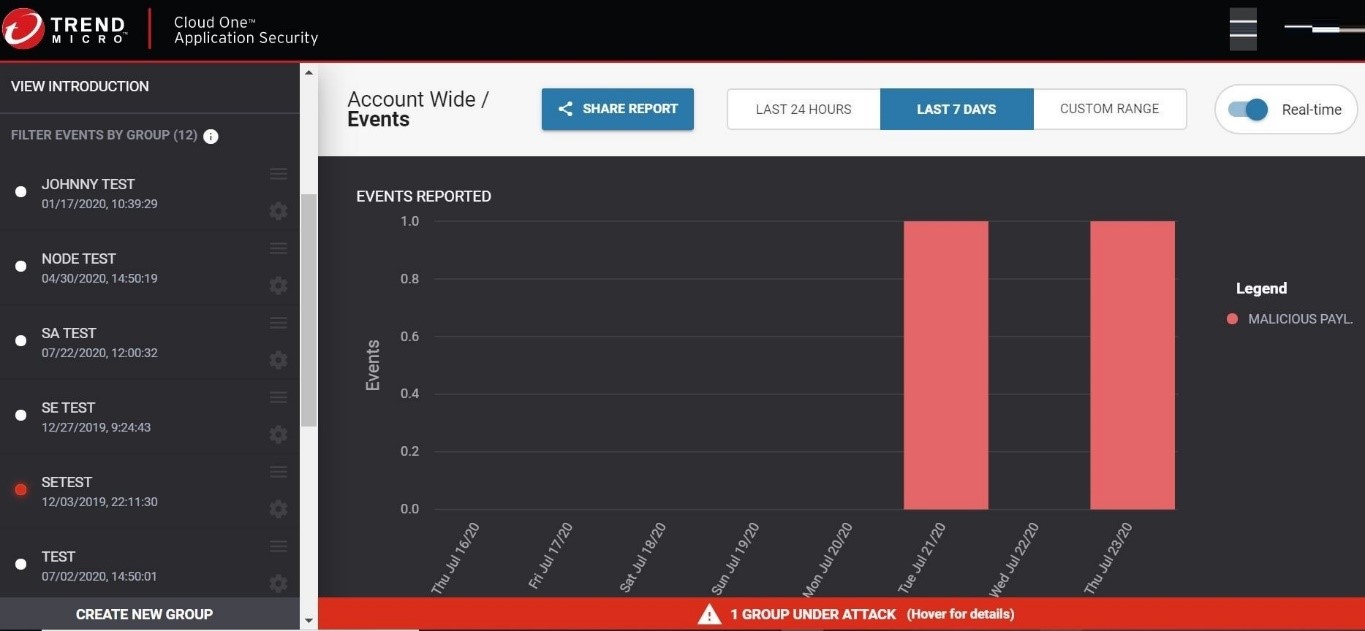
Figure 10. The Cloud One – Application Security is able to detect the SQL injection attack.
How to automate RASP
Automating RASP is an even more effective approach to securing serverless applications. An AWS Lambda function template (for example, CloudFormation) contains the necessary RASP components to integrate Cloud One – Application Security into the AWS Lambda.
By providing these pieces of information in a CFN template, development teams can be empowered to launch an AWS Lambda function with the assurance that security is already a part of the application itself. This also limits the numerous manual steps that were mentioned previously.
Conclusion
RASP is a tool that enables organizations to “shift left,” which is an important direction that allows developers to use secure, well-understood patterns for secrets management and resilient coding practices.
On another note, while some might champion the benefits brought about by new security technologies like RASP, it is also possible that some skeptics who work under traditional processes might resist these changes. Still, these skeptics could be enlightened if organizations were to hold inclusive discussions about how each team or department can bridge the gap and work together toward building a strong DevSecOps culture. This culture, in turn, could be fostered by having development and security teams conduct proper software testing, integrated security, and operational visibility at all times.
Trend Micro Cloud One
While cloud service providers (CSPs) provide guidance and security features for their services, enterprises should still ensure that they improve the security of the services that are connected to their computing environment.
Adopting the shared responsibility model is key to securing these services as it requires both the CSP and the user to maintain areas of responsibility to keep their computing environment protected. In the case of AWS Lambda, it should be noted that the execution role only launches with permissions defined by the user. Therefore, customers should follow the principle of least privilege when defining an execution role.
Enterprises can also rely on the Trend Micro Cloud One security services platform. Cloud One provides enterprises centralized visibility over their hybrid cloud environments and real-time security with the following automated and flexible services:
- Application Security is an embedded security framework that proactively detects threats and protects applications and APIs on their containers, serverless, as well as other cloud computing platforms.
- Cloud Conformity performs hundreds of automated checks against industry compliance standards and cloud security best practice rules, improving the cloud infrastructure’s security and compliance posture.
- Container Security detects threats, vulnerabilities, and exposed sensitive data such as API keys and passwords within container images.
- Workload Security can automatically protect legacy systems with virtual patching and cloud workloads from evolving threats through machine learning (ML) technology.
- File Storage Security protects cloud file/object storage services that are on cloud-native application architectures via malware scanning and integrating into custom workflows.
- Network Security defends virtual private clouds by blocking attacks and threats and detecting infiltrations.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Forecasting Future Outbreaks: A Behavioral and Predictive Approach to Proactive Cyber Risk Management
- Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report
- The Industrialization of Botnets: Automation and Scale as a New Threat Infrastructure
- From Holiday Snap to Custom Scam in 30 Minutes: How AI Turns Public Photos Into Targeted Attacks
- From LinkedIn to Tailored Attack in 30 Minutes: How AI Accelerates Target Profiling for Cybercrime

 Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report
Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One