Cryptocurrencies gained recognition as a legitimate currency for the purchase of goods and services because of their perceived anonymity when used and the online market’s speculation of their value. And with the proliferation of internet-connected mobile devices, online transactions using these currencies are expected to increase in popularity and use.
Unfortunately, it has also gained notoriety mostly because of the way cybercriminals cash in on its growing value and popularity.
Cryptocurrencies and cryptocurrency mining, explained
Cryptocurrency is a digital form of currency. Broken down, it’s an encrypted data string denoting a unit of currency that is organized, monitored, and secured by a peer-to-peer network known as a blockchain. Cryptocurrency transactions are secured, verified, and anonymously executed as millions of computers are simultaneously updated on all trades. Cryptocurrencies have a finite supply available as disclosed by their respective source codes. Despite the number of kinds of cryptocurrencies, this limitation determines the fluctuating capitalization worth and perceived market value of the currencies.
Meanwhile, cryptocurrency mining – or cryptomining – is the process that involves validating user transactions and adding them to the blockchain. Verification is done by solving complex mathematical problems: Find a randomly generated number – a nonce – combined with a generated cryptographic hash to solve the complex equation. Miners are rewarded with cryptocurrency as an incentive for the undertaking. The resource-intensive process involves the use of specialized hardware such as application-specific integrated circuits (ASICs) because the equations increase in difficulty as more miners solve the problems. Considering this, the profitability of the miner depends on the number of equations that can be solved in the shortest amount of time.
The entire system is decentralized, meaning there are no central banks, governments, or corporate entities overseeing the processes of mining, currency exchange, or transactions. The cryptocurrencies can be collected and kept by users in a personal digital wallet or traded on digital stock exchanges.

Are cryptocurrencies and cryptomining bad?
No. As mentioned, cryptocurrencies can be used as a secure way to pay for offline or online purchases, and are considered legitimate currencies in some countries. Unfortunately, its anonymity and increasing market value expectedly attracts cybercriminal threats such as cryptocurrency mining malware, cryptojacking, and digital wallet theft. Authorities also found that more than 80% of initial coin offerings (ICOs) in 2017 were scams, and more cases continue to be filed. And as in the case of cryptojacking, infecting other systems with miner malware does not involve sophisticated programming or hacking skills: Cryptojacking kits are available for as low as US$30.
As the mining process occurs in the background, infected systems continue to use computing resources unnoticed. The constant load on the infected system’s resources result in overheating units, damaged fans or vents, increase in power and bandwidth usage, slow processing runs, or the sudden overuse of available memory resources in computers and servers. Ultimately, affected enterprise assets will have to be replaced sooner, resulting in disrupted operations and financial losses.
Cryptocurrency miner malware infection and attack routines
Over the years, cybercriminals have developed methods to deliver and run cryptocurrency mining malware stealthily. More recently, some routines have used legitimate tools and fileless malware to deliver a miner payload, while others have exploited search engine vulnerabilities. Other sophisticated and organized groups have resorted to targeting specific industries or users, while others use available online tools to look for exposed servers to infect with miners. More persistent attacks have gone after cryptocurrency exchanges, either by unauthorized trading of currencies from other users’ wallets or by going after the exchanges’ reserves and its customers. Others use cryptocurrencies and investments in it as lures for other malware infections. Old techniques such as social engineering have also caused waves of infections, and malicious actors continue to exchange techniques in the underground.
In 2018 and 2019, Trend Micro’s telemetry detected a fluctuation in attacks and infection attempts in a number of countries.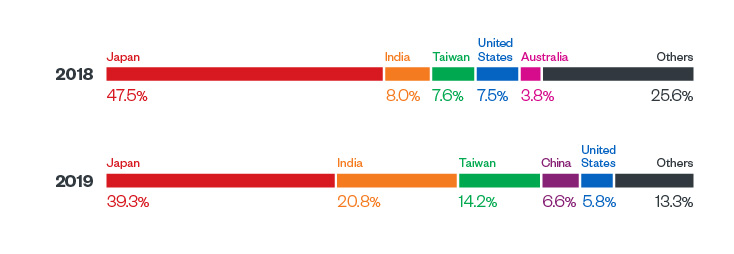
Figure 1. Snapshot of the five countries with the most detected cryptocurrency miner malware infection attempts for 2018 and 2019. Data derived from Trend Micro’s Smart Protection Network’s (SPN) detections.
As mentioned in Trend Micro’s annual security roundup, the sudden increase in cryptocurrency miners in systems — bundled with a number of other malware such as ransomware and botnets — became apparent in attacks against enterprise infrastructures as tools and services became prominent in the underground. Inspired by cryptocurrency’s growth in demand and market value, more criminals explored the possibility of exploiting internet-of-things (IoT) devices to mine cryptocurrency. Despite their limited processing capabilities, the sheer volume of IoT devices can make it worthwhile.
However, the decline in detections for miner malware and attacks in 2019 (as documented in Trend Micro’s midyear security report) does not equate to a loss of interest. Illicit cryptocurrency mining may have simply reached a point of maturity; threat actors are being more selective with their targets, employing more sophisticated routines, and refining attack techniques. Moreover, despite the decreased detection numbers, cryptocurrency miner threats still remain the most detected malware.
[Read: Beyond bad trades: Cybersecurity risks to cryptocurrency exchange users]
Symptoms of a cryptocurrency malware in the system
Cryptocurrency miners require a lot of computing power, which raises some red flags that could indicate an infection. Here are a number of symptoms:
Slower computer performance.
As previously mentioned, cryptocurrency miners use a lot of processing power. This results in abnormally high CPU usage (even when the system shouldn’t be running any resource-intensive tasks), hogging computing resources that legitimate tasks need.Increase in network traffic, internet usage bandwidth, and computer processing despite normal or minimal use.
The flow of normal internet traffic usually involve message lengths with short incoming requests and long outgoing responses. By comparison, cryptomining’s incoming hash length is short, with longer outgoing results (as it updates the blockchain). A trained user and traffic monitoring teams may observe a spike in upload traffic even during expected office downtimes such as a weekend or holiday.Unusual increase in server activity.
Cybercriminals can inject malicious code into websites or online ads to run miners on visitor’s systems. These scripts are automatically executed, even without user prompts or interactions. Enterprises with their own websites connected to physical in-house or cloud servers can observe a sudden activity in specific pages of their respective websites, even in pages that do not normally require long standby periods.Defending against this threat
Cybercriminals will continue attacking and infecting systems with cryptocurrency miner malware, with some bundling it with other malware to make an infection more profitable. Additionally, given the anonymity that it affords, cryptocurrency miner malware is expected to remain among cybercriminals’ more preferred tools for making a profit.
Here are a few best practices for defending your systems from malware:
- Regularly update devices’ software and firmware as vendors release patches. Malicious actors can exploit vulnerabilities to install unknown components, codes, or commands in devices.
- Be wary of unknown URLs, embedded links and ads, attachments, and emails from unknown senders, especially with redundant requests for information, urgency, or insistence on immediate action. Double-check websites before logging in or signing up with sensitive information as these can be used against you with social engineering techniques, luring victims even after an initial attack.
- Enable multifactor authentication (MFA) on all online accounts and platforms whenever they are available, and bookmark frequently visited websites to ensure legitimacy.
- Apply network segmentation. Implementing separate networks in the enterprise for specific purposes can minimize the effects of a compromise.
- If actively using trading platforms, refrain or avoid using the trading platform account as a wallet for cryptocurrencies; a compromise on the platform can lead to a compromise of the wallet, the user’s information, and the cryptocurrencies stored. Consider using a hardware wallet for your assets, and consider using multiple trading platforms. Make sure to read through the terms and conditions of the trading platform/s before creating an account, especially for the users’ and platforms’ accountability in the event of a compromise.
- Companies still using legacy systems and end-of-life products should pay attention to emergency patches released by vendors, especially for critical and important vulnerabilities. Legitimate virtual patches and hotfixes are also released by security vendors.
Trend Micro solutions
Trend Micro solutions powered by XGen™ securitycan detect related malicious files and URLs and protect users’ systems. Trend Micro Smart Protection Suites and Trend Micro Worry-Free™ Business Security, which have behavior monitoring capabilities, can additionally protect from this type of threat by detecting malicious files, thwarting behaviors and routines associated with malicious activities, as well as blocking all related malicious URLs. XGen protects against today’s threats that bypass traditional controls, exploit known, unknown, or undisclosed vulnerabilities, either steal or encrypt personally identifiable data, or carry out malicious cryptocurrency mining. Smart, optimized, and connected, XGen powers Trend Micro’s suite of security solutions: Hybrid Cloud Security, User Protection, and Network Defense.
Trend Micro™ Deep Security™ and Vulnerability Protection provide virtual patching that protects servers and endpoints from threats that abuse vulnerabilities. OfficeScan’s Vulnerability Protection shields endpoints from identified and unknown vulnerability exploits even before patches are deployed. Trend Micro™ TippingPoint™ provides virtual patching and extensive zero-day protection against network-exploitable vulnerabilities via DigitalVaccine™ filters.
Trend Micro™ Deep Discovery™ provides detection, in-depth analysis, and proactive response to attacks using exploits through specialized engines, custom sandboxing, and seamless correlation across the entire attack lifecycle, allowing it to detect threats that may exploit vulnerabilities even without an engine or pattern update.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Ultime notizie
- The State of Criminal AI: Market Consolidation and Operational Reality
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One