Ransom Notes: Know What Ransomware Hit You
The ransomware landscape has grown exponentially from when it was first seen, and with the unending introduction of newer families and variants, as well as updates to existing ones, all signs tell us that the ransomware problem is still growing. One thing that makes ransomware work is its effective use of scare tactics that elicit fear among its would-be victims, which leads to users giving in to the demands defined by the ransom note.
The ransom note usually provides payment info and the threat—how to send payment and how much you need to pay, and what happens if you don't. Those who have been hit are going to want more information, and possibly other ransomware prevention or removal solutions, like a free decrypt tool online. But first, you're going to need to know what kind of ransomware hit you. Here are the ransom notes from some of the most popular ransomware types right now to help you out.
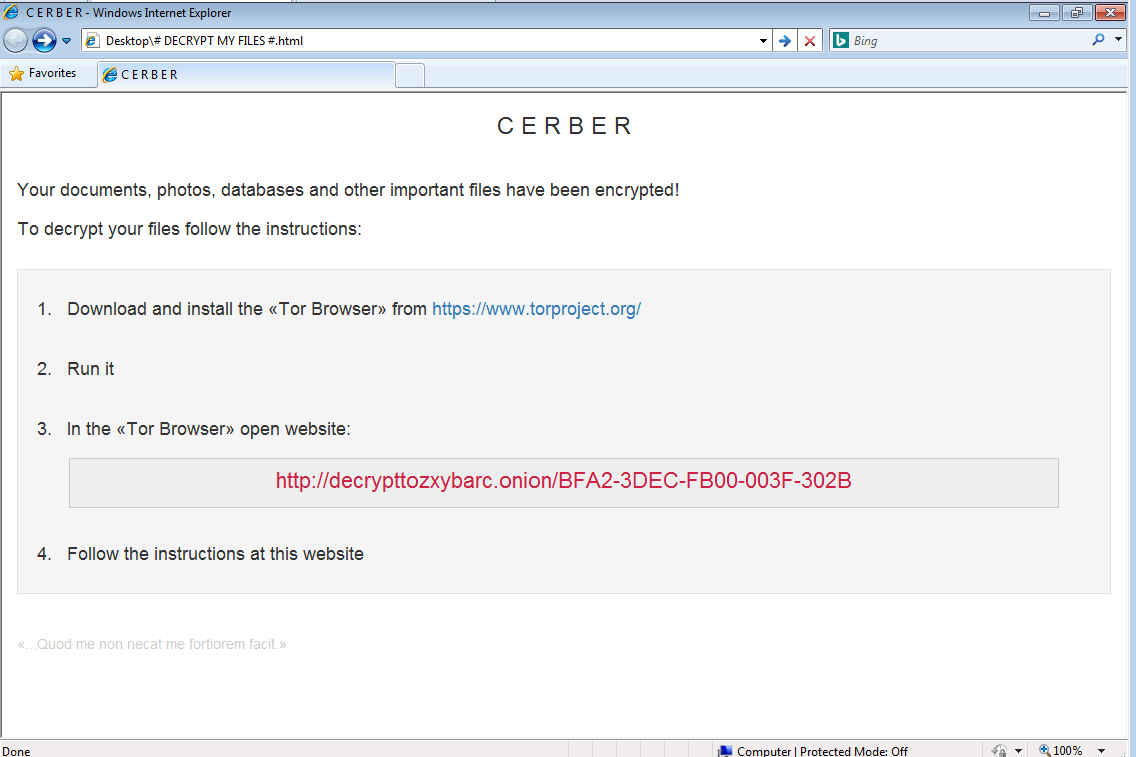
Cerber
Cerber (detected by Trend Micro as RANSOM_CERBER.A) is notable for having a 'voice' feature that reads out its ransom note, verbally coercing its victim to pay the ransom. The cybercriminals behind Cerber requires its victim to settle a ransom of 1.24 BTC (around US$824 as of July 15, 2016), with a seven-day deadline, after which the price doubles. As the ransom note states, photos, databases, and other important documents get encrypted. Files with extensions .doc, .docx, .jpg, .pdf, .pps, .pptm, .rar, .txt, .xls, .mov, .mp3,.config,.css,.csv,.dds,.flv,.html,.key,.lit,.mov,.mp3,.mp4,.mpg will be searched from the victim’s system, and will be replaced with a .cerber extension once the encryption is done.
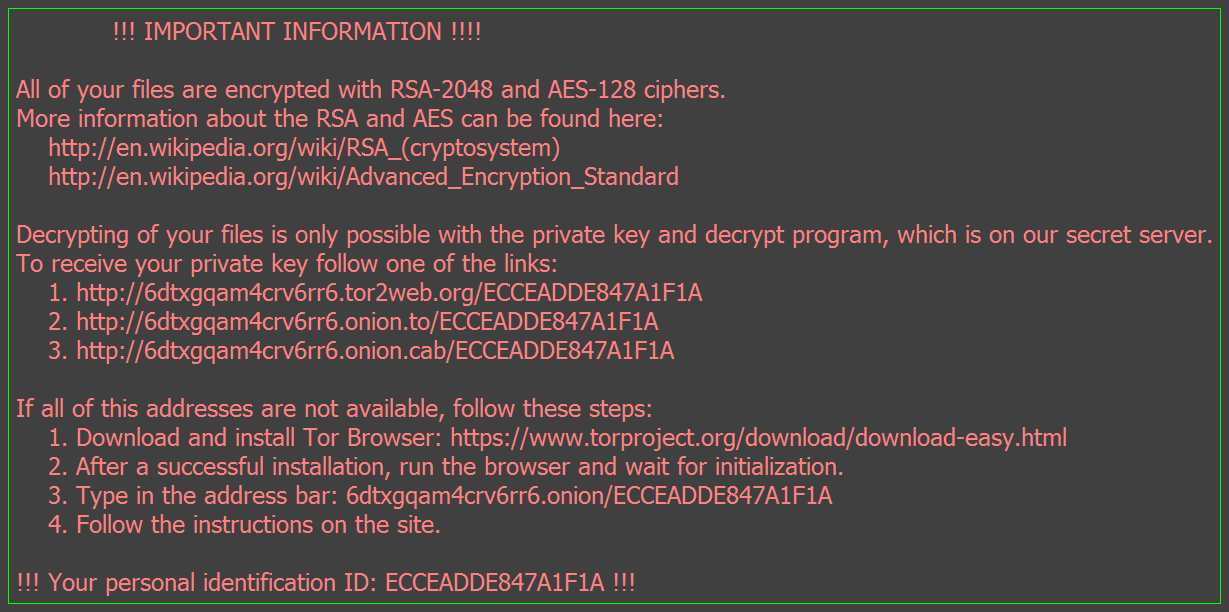
CryptXXX
When CryptXXX (detected by Trend Micro as RANSOM_WALTRIX.C) was discovered, it was seen as a descendant of an earlier ransomware variant, Reveton. Following a rather “embarrassing” appearance of a free decrypter tool shortly after CryptXXX was released, it has undergone numerous updates and facelifts that made it tougher to crack. Now, it does not only encrypt files, several CryptXXX variants have also been spotted with the capability to lock screens and preventing users from accessing their desktops (although this tactic can be seen as counterintuitive, as it also prevents access to the ransom note). CryptXXX is known to encrypt over 200 files, including those with .doc, .docx, .jpg, .pdf, .pps, .pptm, .rar, .txt, .xls, .mov, .mp3,.config,.css,.csv,.dds,.flv,.html,.key,.lit,.mov,.mp3,.mp4, and .mpg extensions, which will be replaced with a .crypt file extension. Interestingly, in one of its updates, the malware creators decided to take a “friendlier” route by giving its victims more time to settle the ransom set at $500 before the price is doubled.
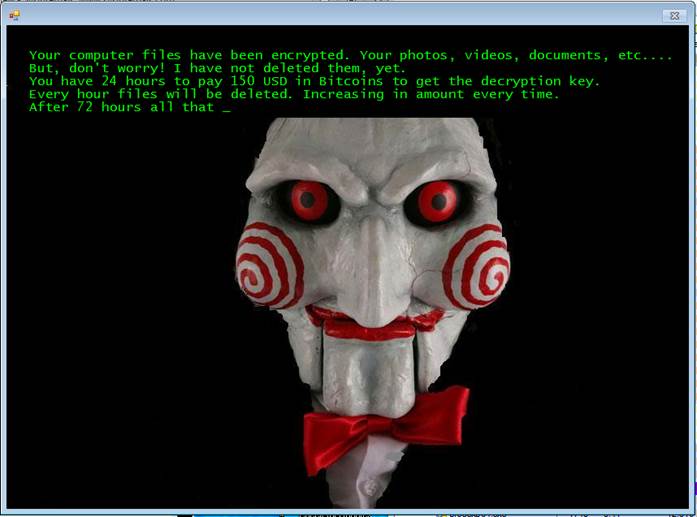
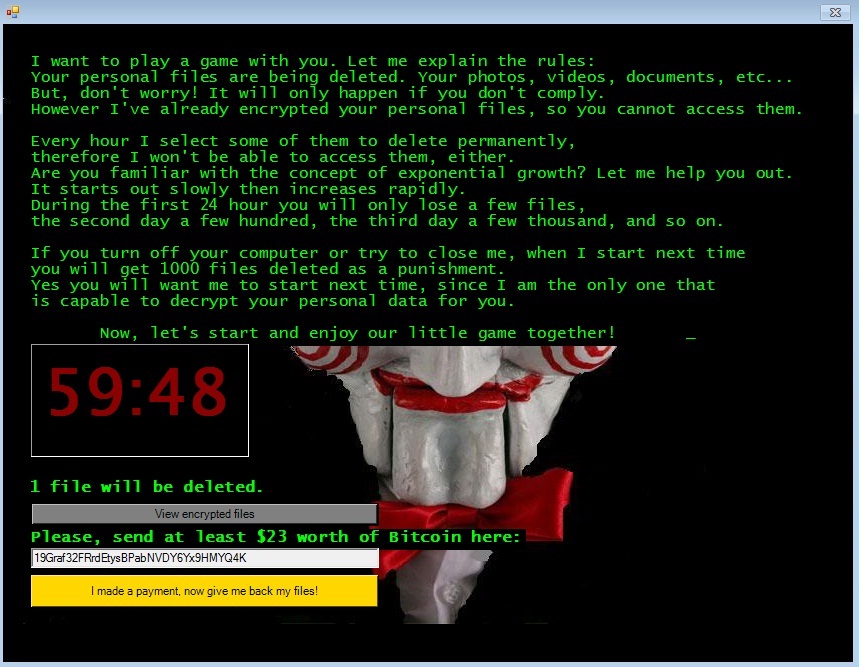
Jigsaw
Talk about getting creative with the scare tactic. When Jigsaw (detected by Trend Micro as RANSOM_JIGSAW.I) was first seen, it wasn't that difficult to figure out where it got its name. Evidently inspired by the Hollywood slasher flick Saw, the malware makes use of a countdown timer to add some urgency for the victim. Upon entry into the system, Jigsaw is known to encrypt 225 file types, including documents and media files with extensions .doc, .docx, .jpg, .pdf, .pps, .pptm, .rar, .txt, .xls, .mov, .mp3,.config,.flv,.html,.key,.lit,.mov,.mp3,.mp4, and .mpg Hourly, non-payment of the ransom set at $20 – 150 would mean the deletion of a chunk of the victim’s data every hour. After 72 hours, the entire batch of encrypted files are permanently deleted.
Locky
Locky’s introduction to the game was noteworthy, thanks a seldom-seen delivery method that involved the use of malicious macros in an attached document. Locky's malware executable file (detected and analyzed by Trend Micro as TROJ_LOCKY.DLDRA) is downloaded from a web server. Once installed, it begins looking for attached drives and even networked drives containing documents, images, music, videos, archives, database, and other web application-related files. Upon encryption, the files will then be appended with a .locky extension. The message directs victims to a Tor network to make payment in Bitcoins (0.5 BTC). Locky is notorious for its use in attacks that hit the healthcare industry, such as the ones that brought down systems of health institutions like Hollywood Presbyterian Medical Center and the Kentucky-based Methodist Hospital.
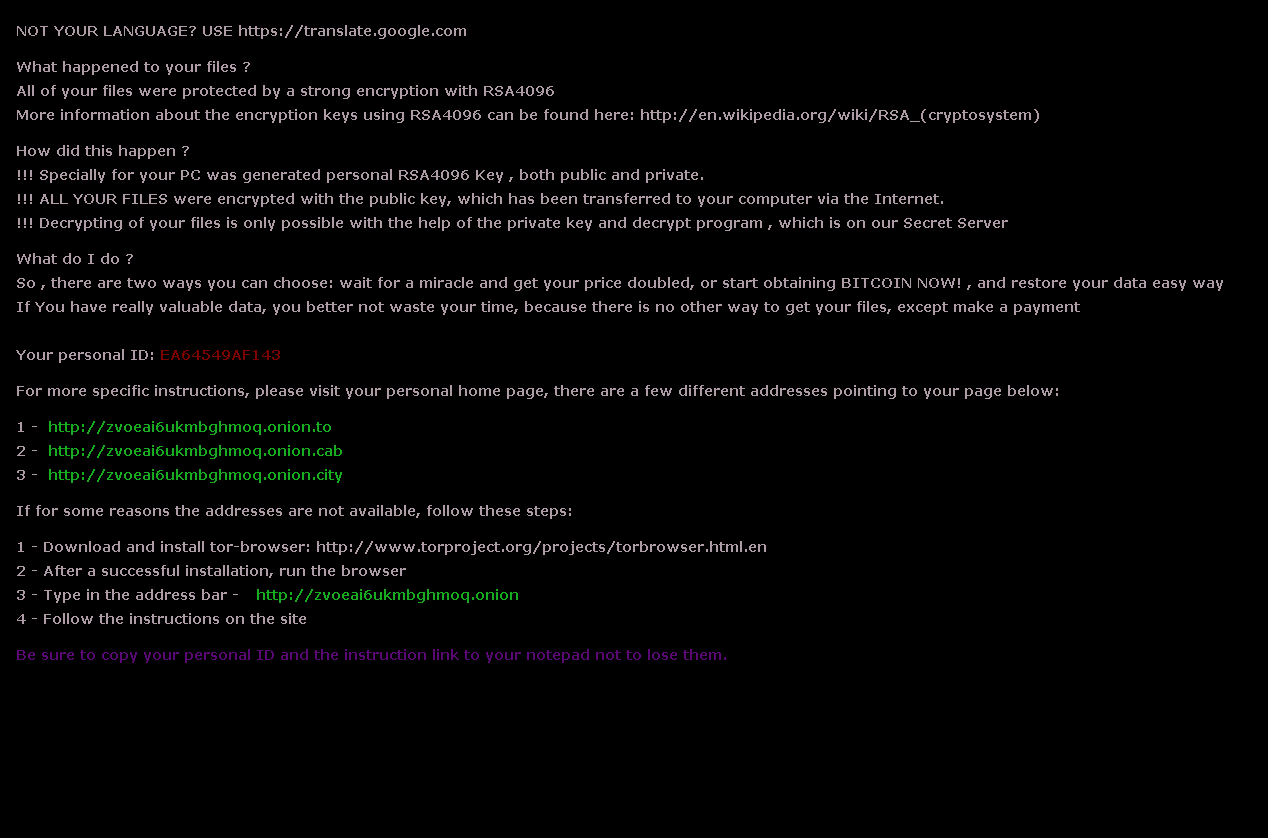
RAA
When it was first reported, RAA was notable for its use of JScript to make detection harder and obfuscation easier. Once inside the system, RAA (detected as RANSOM_JSRAA.A) searches for files with extension names .doc, .xls, .rft, .pdf, .dbf, .jpg, .dwg, .cdr, .psd, .cd, .mdb, .png, .lcd, .zip, .rar, .csv, encrypts them, and appending them with .locked. RAA was also found to be capable of dropping and extracting the data-stealing malware FAREIT (otherwise known as Pony)—capable of finding stored credentials from File Transfer Protocol (FTP) clients and other file management software, email clients, web browsers, and even bitcoin wallets. These can all be mined and sent through a command-and-control server. The ransom note, written in Russian, gives out instructions on how to pay the ransom—amounting to 0.39 bitcoins, or around US$260.
MIRCOP
MIRCOP (detected as RANSOM_MIRCOP.A) emerged at the end of June with a rather unique scare tactic. Its ransom note, which shows a hooded figure in a Guy Fawkes mask, puts the blame on its victim, highlighting that the victim has “stolen” something from them. Instead of appending encrypted files with an extension, MIRCOP prepends files with the string “Lock.”. It also encrypts common folders. When files are opened, the file’s content is changed to unreadable characters. The ransom note prompts the victims to take action. On June 23, MIRCOP notably demanded one of the biggest single ransom amounts seen of late—a hefty sum of 48.48 bitcoins (around $32,239, at a rate of $665 for 1 bitcoin on July 15th), which they claim is rightfully theirs.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering




 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One