Application Control Empowers Endpoint Security
 View infographic: Empowering Endpoint Security
View infographic: Empowering Endpoint Security
The need to safeguard classified data has enterprises scrambling for the best possible security solutions—blacklisting and whitelisting being two of those in contention. Which works best?
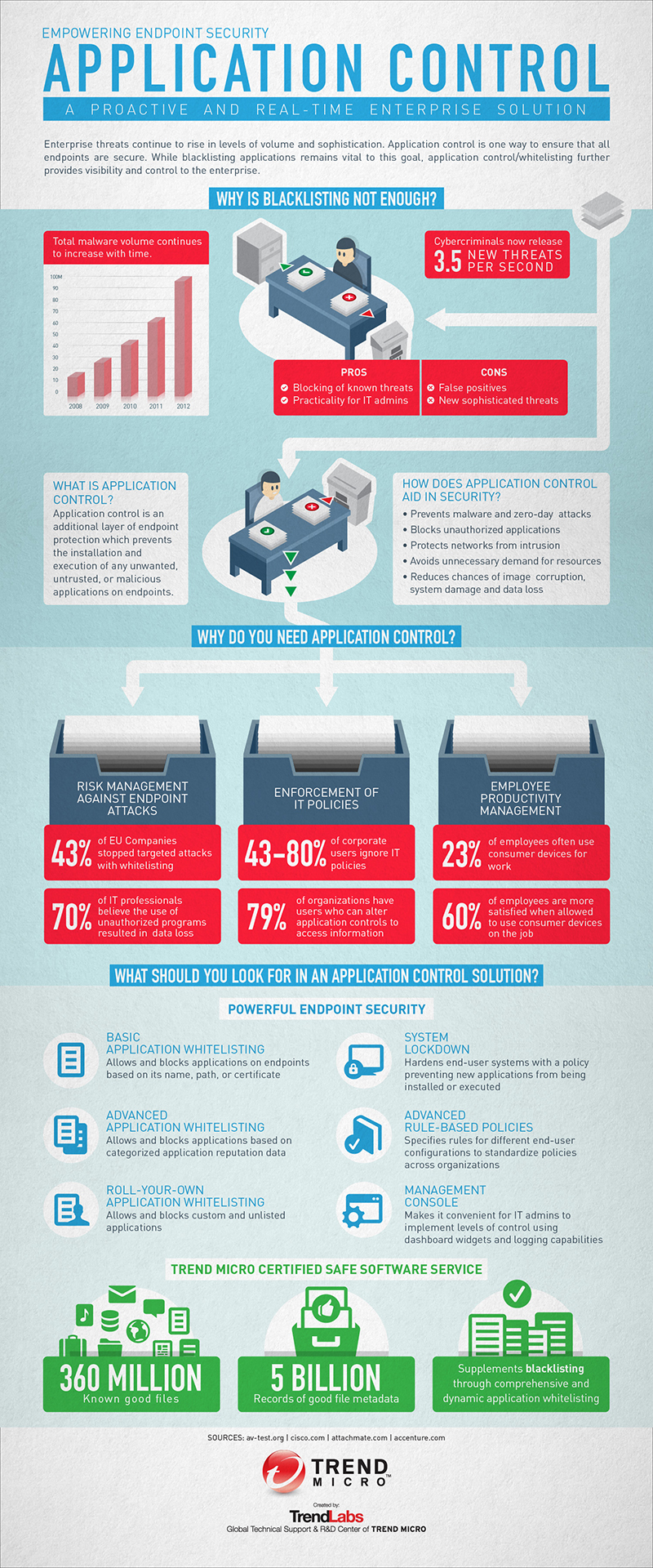
Though blacklisting is a proven method of securing enterprise data and infrastructure, it has its limits. Blacklists have their share of false positives, meaning good files can sometimes be identified as malware. Blacklists are also not foolproof against new, unidentified threats. In comes whitelisting, explained in detail in Application Control.
Think of whitelisting as a VIP list, anyone not on it are not allowed to enter. Whitelisting or application control works the same way. It prevents the installation and execution of unwanted, untrusted, and malicious applications on an enterprise system.
Application control also addresses compliance concerns since it allows enterprises to fully manage the permitted executables included in an identified whitelist. Compliance, data loss, and corporate productivity have become pressing concerns given the ongoing BYOD trend. With application control, employee-owned devices are required to comply with company-mandated network systems limitations and IT policies, like the installation and use of licensed and legitimate software.
The Trend Micro™ Smart Protection Network™ contains over 360 million known good files and 5 billion good file metadata. This helps make incident response and forensic analysis quicker and more efficient, while reducing incidents of false positives. Based on studies, whitelisting aided 43% of EU companies in mitigating targeted attacks.
It’s important to note, though, that application control doesn’t do away with blacklisting; instead, it complements it. There will always be new threats, and cyber attacks will always be launched in a million different ways. Application control, deployed with blacklisting and other Trend Micro threat protection solutions can help effectively keep your networks secure while maximizing company resources.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Threat Attribution Framework: How TrendAI™ Applies Structure Over Speculation
- AI Skills as an Emerging Attack Surface in Critical Sectors: Enhanced Capabilities, New Risks
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One