Ransomware Recap: New Families and Updated Variants in June
The ransomware epidemic is showing no signs of slowing down. These days, not only are we seeing the surfacing of newer families, but the commitment of malware creators to create continuous updates in previously-released variants prove to be unrelenting. Today’s ransomware landscape has grown exponentially over the past two years, thanks to the number of cybercriminals turning to using the extortion malware for its easy deployment and potential for profit. In fact, an underground marketplace was uncovered last May 2016 selling goods and services related to ransomware, some for hefty prices.
This continuous onslaught of new ransomware families, updated variants, and thriving business and distribution models attest to the fact that ransomware works. In the first five months of 2016 alone, 50 new ransomware families have been discovered, which shows an average of 10 new ransomware families a month.
[Related: The Psychology and Methods Used to Distribute, Infect, and Extort]
The ransomware landscape has been as active as ever in June. Here are some of the most notable ransomware families that made news in the past month.
CryptXXX
Apart from the continuous surfacing of new ransomware types, the month of June also saw significant updates for some existing ransomware families. Such is the case with CryptXXX. When it was first discovered, CryptXXX was dubbed as a descendant Reveton. Aside from the usual ransomware routine of locking its victims files with encryption, CryptXXX has also been discovered to possess Bitcoin-stealing capabilities.
After the “embarrassment” brought about by the fast release of a “free decryption tool” made available online, CryptXXX was updated with stronger encryption. The development continued into June with an overhaul of its interface, ransom note, and payment site. Labeled as CryptXXX 3.0, the updated version also implemented a new encryption algorithm that prevented the use of free decrypter tools widely available online. After infection, the ransomware redresses its desktop wallpaper to an image similar to its revamped Tor payment site. The victim is given a 90-hour deadline to pay the ransom. Failure to do so would then double the ransom to two Bitcoins.
Not long after, researchers spotted another update. CryptXXX 3.1 added a network-scanning feature where files with extensions matching CryptXXX’s own list are queried, overwritten, then encrypted with the .cryp1 extension. On June 6, researchers determined that the developers behind the revamped CryptXXX 3.100 switched to using the Neutrino Exploit Kit for distribution—a significant change for a ransomware family that has only been seen using the Angler EK for distribution since its release.
Crysis
This new ransomware family was first detected by researchers in February, targeting individuals and enterprises. It did make security headlines in the first weeks of June after it was touted as a successor to TeslaCrypt. Crysis is spread via poisoned emails containing attachments with double file extensions that masked the malicious files as non-executable files. Apart from piggybacking on spam emails that led to malicious URLs, this ransomware variant was also distributed as installers for legitimate applications like WinRAR, Microsoft Excel and iExplorer.
After encrypting over 185 file types on fixed and removable drives, it sets its ransom at amounts that range between US$455 to 1,022 in bitcoins. Crysis also has the ability to encrypt system files, which made affected systems “unstable”.
Additional reports also show that Crysis doesn't just hold a computer’s files hostage, but it has the ability to mine user credentials found in the victim’s machine. Further, it can remotely take over an infected computer by stealing administrator privileges. And while it can infect Windows and Mac computers, its self-propagating capability can infect other devices running on the same network.
BlackShades
The new ransomware string, dubbed as BlackShades or SilentShades (detected by Trend Micro as CRYPSHED/ Troldesh) was uncovered targeting English- and Russian-speaking users with a ransom pegged at 30 USD, payable in Bitcoins via the online payment platform, Paypal. Interestingly, malware authors behind Blackshades cleverly left obfuscated strings of code that, when scrutinized, seemingly communicates to security analysts. In one instance, a researcher noted that one of the uncovered strings, when translated from its Russian-code means, “You cannot hack me, I am very hard.” Others, when deciphered, read as taunts such as, “Hacked by Russian Hackers in Moscow Tverskaya Street,” and “youaresofartocrackMe.”
The malware is known to encrypt 195 file types using 256-bit AES encryption. These are files found on the C: drive’s folders, such as, Downloads, Documents, Desktop, Pictures, Music, Videos, and Public. The victim’s ID will then be dropped in all folders and the desktop. After which, a .silent extension will then be appended to the encrypted files.
In the process, BlackShades communicates with its C&C server to relay updates on the amount of files encrypted in the computer. A Hacked_Read_me_to_decrypt_files.Html file will then be left on the desktop, serving as the ransom note, which is also copied to the start-up folders. This means that victims are greeted by the ransom note every time they log in to the computer. Afterward the malware deletes itself and leaves behind only the ransom notes. The victim is then left with 96 hours to settle the ransom. Otherwise, all the encrypted files will be deleted. Researchers opine, however, that its operators' choice of using Paypal as a payment platform is an odd choice, given its traceable nature.
Jigsaw
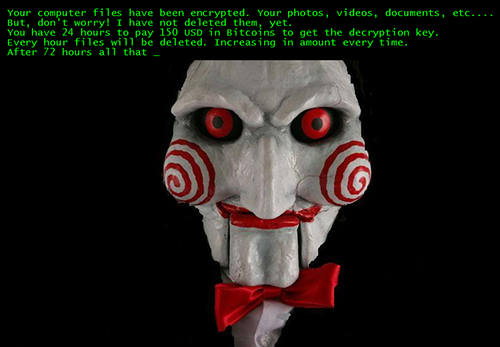
When it was first sighted, Jigsaw played games with its victims—fitting for extortion malware named after the famous Hollywood slasher flick, Saw. Bannering a ransom note in English and Portuguese with the image of the villainous character, Billy, Jigsaw threatened to delete chunks of the files it encrypted every hour that the ransom (ranging from US$20 – 150) has not been paid. The mean streak does not end as the ransom actually increases per hour.
June saw the release of new Jigsaw variants that took a “consumer-friendly” turn. Other versions chose to lessen their ransom to make it more amenable for victims to pay the demanded fee. Jigsaw’s customer-centric development took the form of a “live chat” to cater to victims and address their questions upon infection. This means that a link found on the updated Jigsaw ransom note leads to a website with an embedded live-chat platform, onWebChat. Researchers note that incorporating a “human voice” could be a strategy to influence victims to pay the ransom.
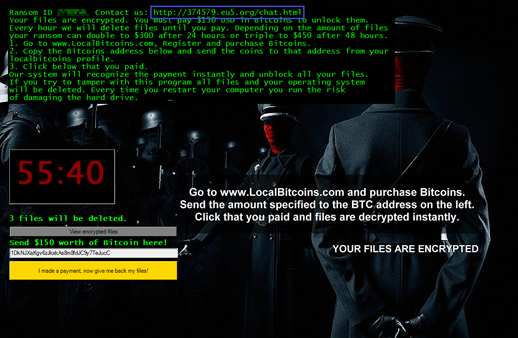
A much more recent variant of Jigsaw (detected by Trend Micro as RANSOM_JIGSAW.F116FN), reported at the tail-end of June, showed an Anonymous-themed ransom note that jumped from an original ransom of $US150 to a hefty sum of 5,000 in bitcoins. Its scare tactics even included a threat to send a copy of the victim’s credentials and email/messenger history to “all” of the victim’s contacts. The threat of exposure has yet to be verified—and is likely an empty scare tactic.
Apocalypse
Another new ransomware variant, Apocalypse, was discovered in June. This variant required communication between the victim and its data kidnapper, which is done by demanding that the victim email the hacker for ransom instructions after appending affected files with a .encrypted extension. Apocalypse also creates an autorun entry that prompts the ransomware to start when a user logs into the system. The message tells the victim to contact the cybercriminals within 72 hours or risk losing data. Interestingly, it was discovered that a would-be victim can bypass the lock screen and run a file decryptor or free tool to regain access to their locked files.
FLocker
June also saw the resurfacing of a mobile lock-screen malware, FLocker. But this time, it has jumped from infecting Android devices to smart TVs. First discovered in May 2015 (detected as ANDROIDOS_FLOCKER.A), FLocker has since amassed over 7,000 variants in Trend Micro’s sample bank. Recent numbers however show a spike that came in mid-April with over 1,200 variants.
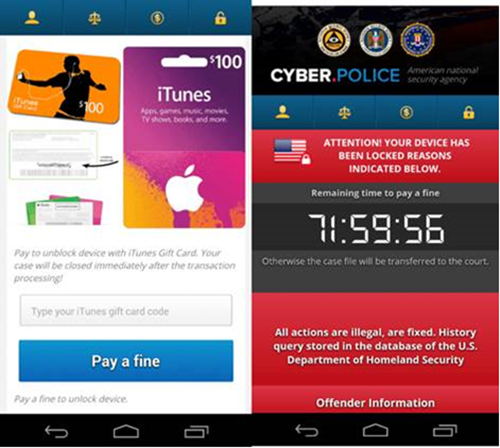
In mid-June, Trend Micro researchers identified a police Trojan variant of FLocker masquerading as the US Cyber Police or a different law enforcement agency that accuses its would-be victim of crimes unknown to them. After infection, the malware asked for a $200 ransom to unlock the encrypted files—in iTunes gift cards. Further analysis of Trend Micro researchers show that there are no major differences between an FLocker variant that is designed to infest a mobile device and that which could infect a smart TV.
RAA
Earlier sightings of this new ransomware led many to believe that it was built using the web-based language Javascript. This was considered unique as these are primarily designed to be interpreted by browsers. However, further analysis by Trend Micro then uncovered that the malware is using Jscript and not Javascript—a scripting language designed for Windows systems and executed by the Windows Scripting Host Engine via Internet Explorer (IE). Researchers believe that this was done to evade detection and to make obfuscation easier.
Written in Russian, the ransom note gives out instructions on how to pay the ransom—amounting to 0.39 bitcoins, or US$250—to unlock files appended with the .locked extension. Digging through its code, RAA was also found to be capable of dropping and extracting the data-stealing malware FAREIT (otherwise known as Pony). The malware is known to be capable of finding stored credentials from File Transfer Protocol (FTP) clients and other file management software, email clients, web browsers, and even bitcoin wallets. These can all be mined then sent through a command-and-control server.
GOOPIC
Following the fall of Angler, which was known to be the most aggressive exploit kit in terms of adding newer exploits in its arsenal, a significant decline in overall exploit kit activity was observed. However, this development also paved the way for the rise of other exploit kits.
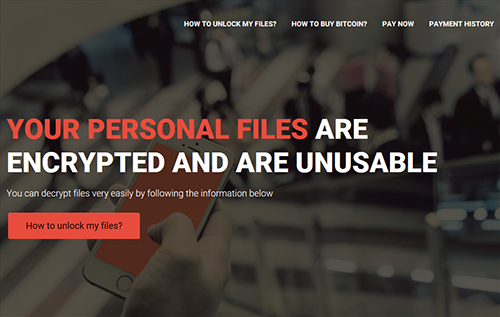
Recent exploit kit activities observed in the last week of June led to the discovery of a new ransomware family called Goopic (detected as RANSOM_GOOPIC.A). Dropped by the Rig exploit kit, Goopic asks for a $500 ransom. Interestingly, this particular ransomware variant gives its victims a relatively longer period to settle the demanded ransom—a far cry from other ransomware families that give its victims 24 to 90 hours to pay.
Kozy.Jozy
This new ransomware strain adds new file extensions to its list of files to encrypt before setting its victim’s background to a ransom note written in Russian. The files, as per the ransom note, have been encrypted with a strong RSA-2048 cipher in the background. The Volume Shadow Copies are then deleted to remove possible backups. The victim is then provided with the operator's email address with directions for making a payment in bitcoins. Reportedly, similar symbol combinations have been seen by victims, which, makes it possible that cybercriminals are selling the ransomware code in dark web forums.
MIRCOP
At the tail-end of June, a new ransomware emerged with a “unique” behavior. MIRCOP (detected as RANSOM_MIRCOP.A) puts the blame on its targets and even assumes that the victim already has an idea how to give them back the money that is rightfully theirs. The ransom note, which featured an image of a hooded figure in a Guy Fawkes mask, accuses the victim of stealing from them, prompting them take action.

As of June 23rd, the ransomware has been demanding a ransom of 48.48 bitcoins (around $28,730.70) from its users—an amount described by Trend Micro researchers to be one of the highest ransom amounts seen of late. Further, at the end of the note, the cybercriminals involved simply included a bitcoin address, unlike other ransomware families that provide step-by-step instructions. MIRCOP is known to be delivered by spam emails with a poisoned macro-enabled document masquerading as a Thai customs form. Apart from its file-encrypting capabilities, this ransomware is also capable of mining credentials from several programs like Mozilla Firefox, Google Chrome, Opera, Filezilla, and Skype.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines


 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One