Overview
The cloud allows us to innovate faster than ever before with its unique agile, innovative, and modern approach. This helps builders across the globe adopt new technologies in increasingly complex architectures using cloud native services and multi-cloud providers to deliver business goals.
With the cloud’s quickly evolving landscape comes new risk, and so the need for a robust security strategy has never been more critical. As organizations embrace the cloud to drive new applications and a more competitive strategy for their business, they are also exposed to new risks and vulnerabilities that can compromise sensitive data and operations. Recognizing this challenge, Trend Micro has continued innovating with Trend Vision One™ – Cloud Security, bringing a comprehensive set of security capabilities to protect hybrid cloud infrastructure.
This cutting-edge platform offers a comprehensive approach to cloud security, empowering cloud builders to protect their environments from development to runtime on their hybrid cloud and multi-cloud strategy.

Accidental exposure of workloads is a prevalent issue in cloud security. With a multitude of cloud configurations to manage and vulnerabilities to patch, users often fail to secure sensitive information. According to Gartner, through 2025, 99% of cloud security failures will be the customer’s fault. To address this, we must bring full visibility of cloud risks, misconfigurations, vulnerabilities, threats, predicted attack paths, and more into the dynamic cloud environment.
Optimizing visibility in the cloud with attack surface management
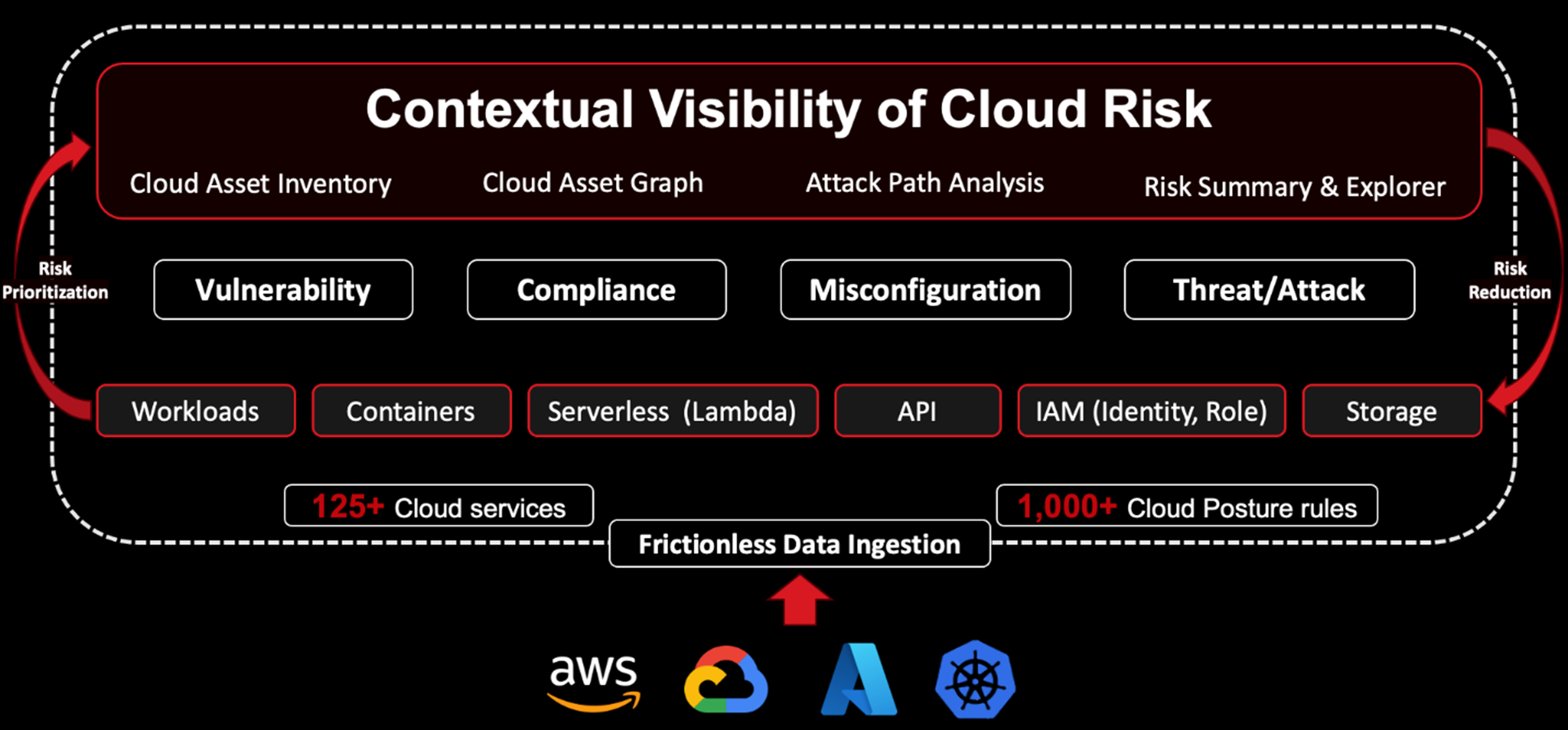
With its instant agentless scanning, Trend Vision One™ – Attack Surface Risk Management for Cloud (ASRM for Cloud) equips organizations with the necessary insights to proactively identify and address cloud risks and potential vulnerabilities.
After scanning the cloud environment, ASRM for Cloud correlates the information with our database of vulnerabilities, misconfiguration, threats, and more, and calculates an organizational risk score. This gives cloud security teams a simple, quantifiable, easy-to-digest way of recognizing and prioritizing their risk.
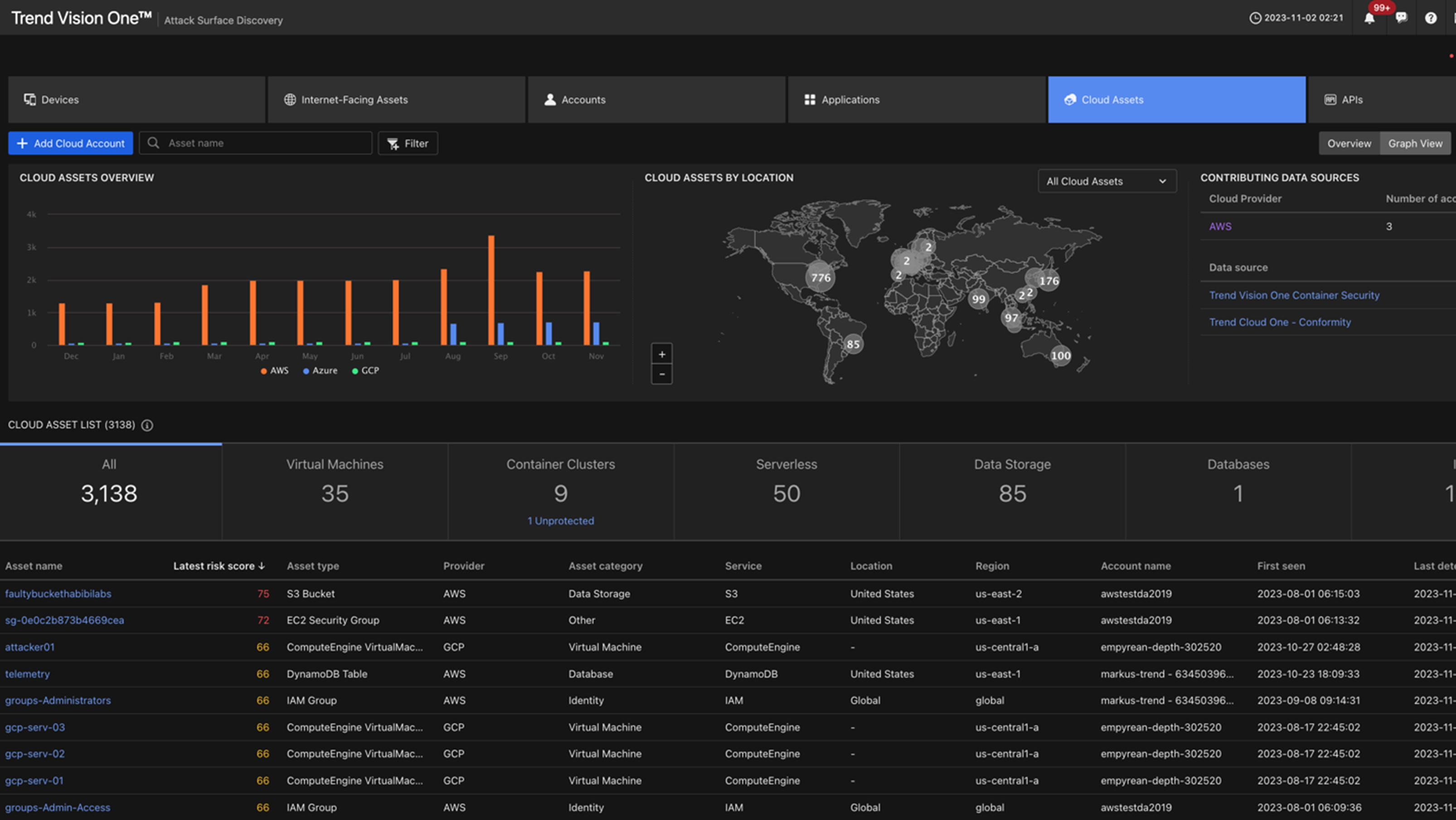
When cloud security teams need a deeper understanding of individual assets’ risk, they can drill down into each one’s asset profile and cloud asset graph, which maps out risky attack paths and gives a view of the potential attack radius of that asset on your cloud account.
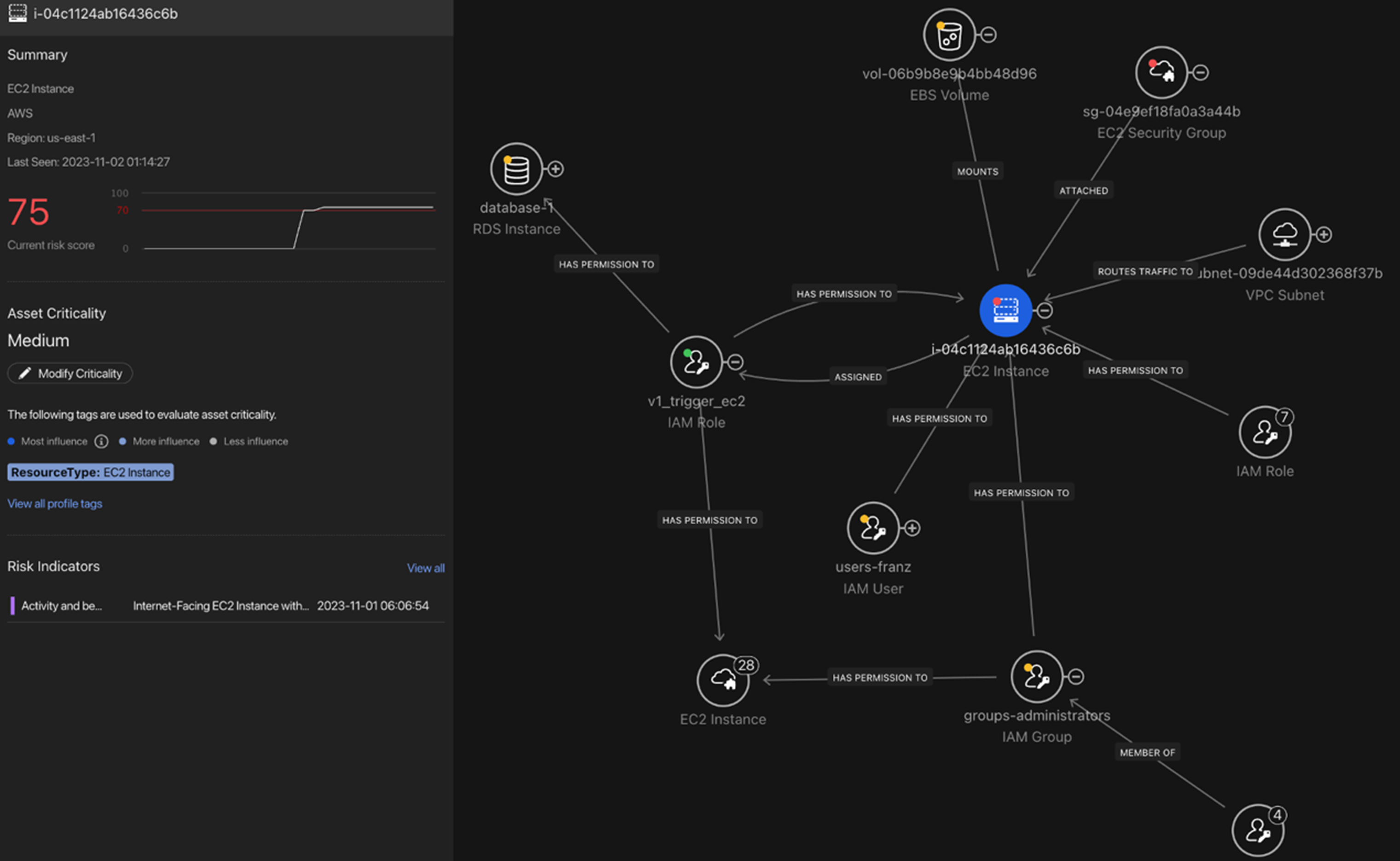
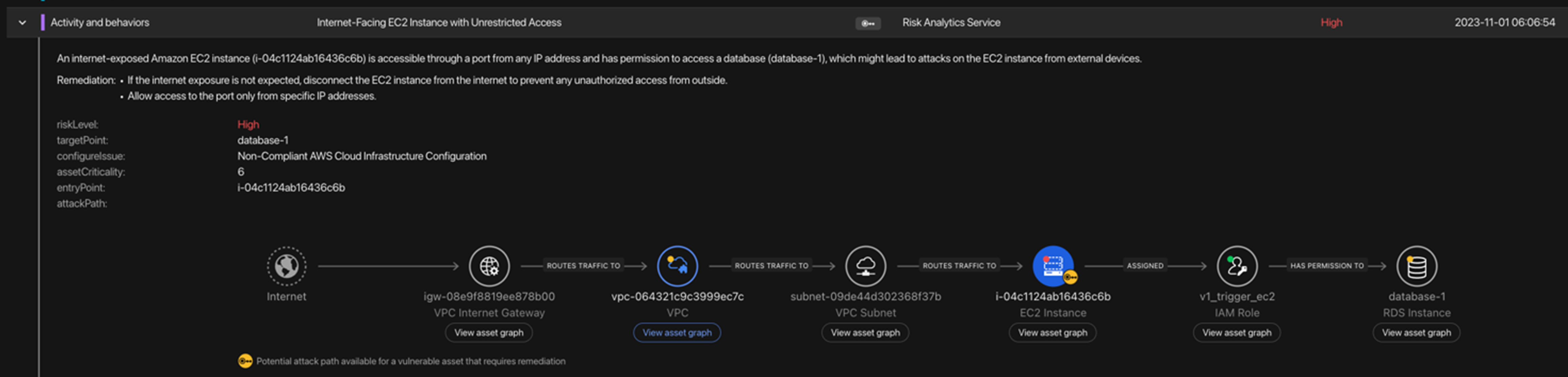
This functionality enables organizations to focus their efforts on mitigating the most critical security threats, reducing the likelihood and magnitude of successful attacks. By guiding users through the remediation process, organizations are empowered to stay one step ahead of cyber threats and safeguard their cloud assets effectively.
The capability shown below is part of the potential attack path that is result of comprehensive risk prioritization, which combines all risk factors from external exposure to critical internal asset by potential lateral movement.
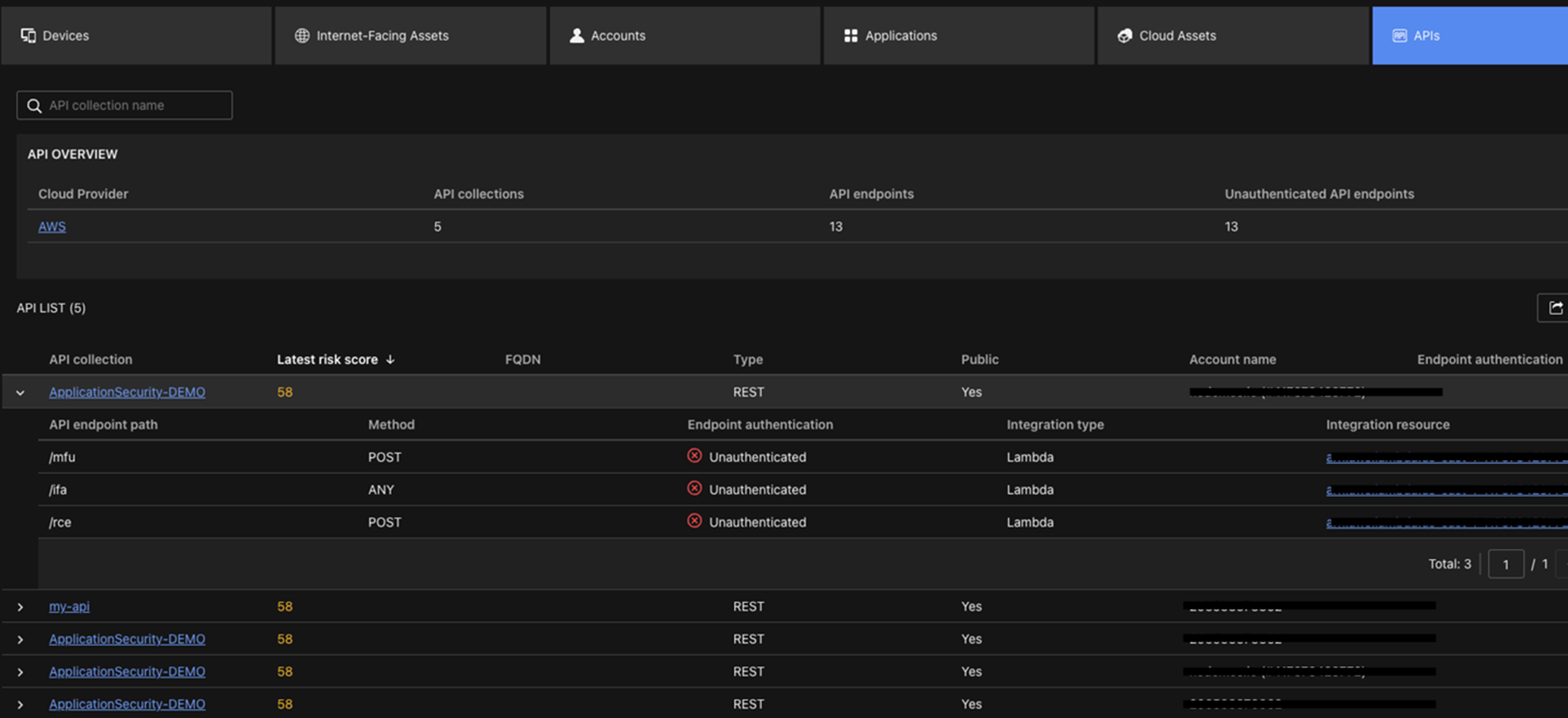
Some of those applications could be connected and architected using API gateways that also could result in misconfigurations and unauthenticated API endpoints.
Unprotected and publicly exposed APIs are difficult to identify in enterprise organizations because of the sheer number of API Gateways and API endpoints, which can total north of 10,000.
Through ASRM for Cloud, customers can now quickly identify both misconfigured and unauthenticated APIs.
An API that is unauthenticated means that it doesn’t require user authentication before facilitating a connection. Without an authentication policy, anyone that discovered the API on the internet could connect to it without a username or password, and access the unauthorized information, potentially compromising organizations.
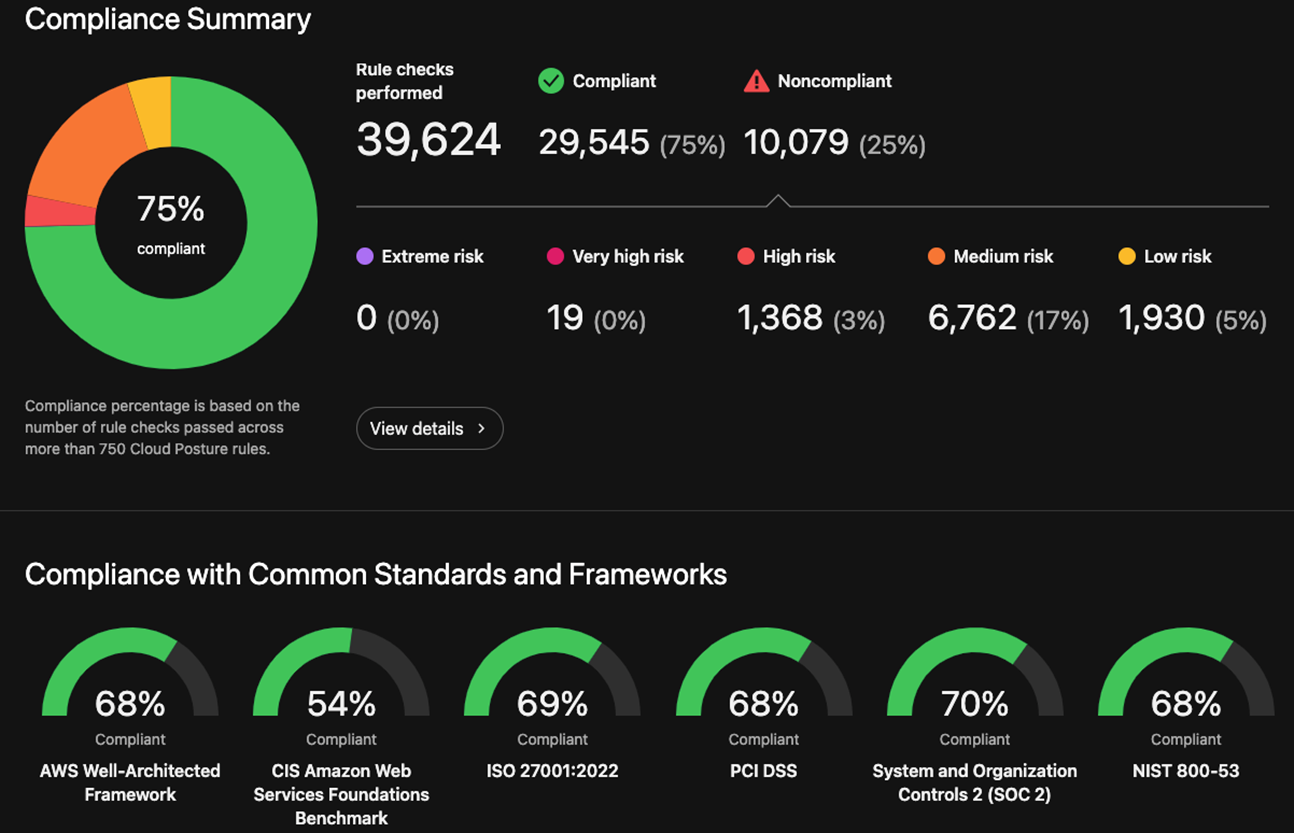
These cloud risks and misconfigurations can be headaches for applications that require compliance with major frameworks, such as PCI-DSS, HIPAA, HITRUST, NIST 800-53, GDPR, LGPD, and others. ASRM for Cloud agentless scanning can monitor your cloud accounts continually to help identify new misconfigurations in critical accounts and applications.
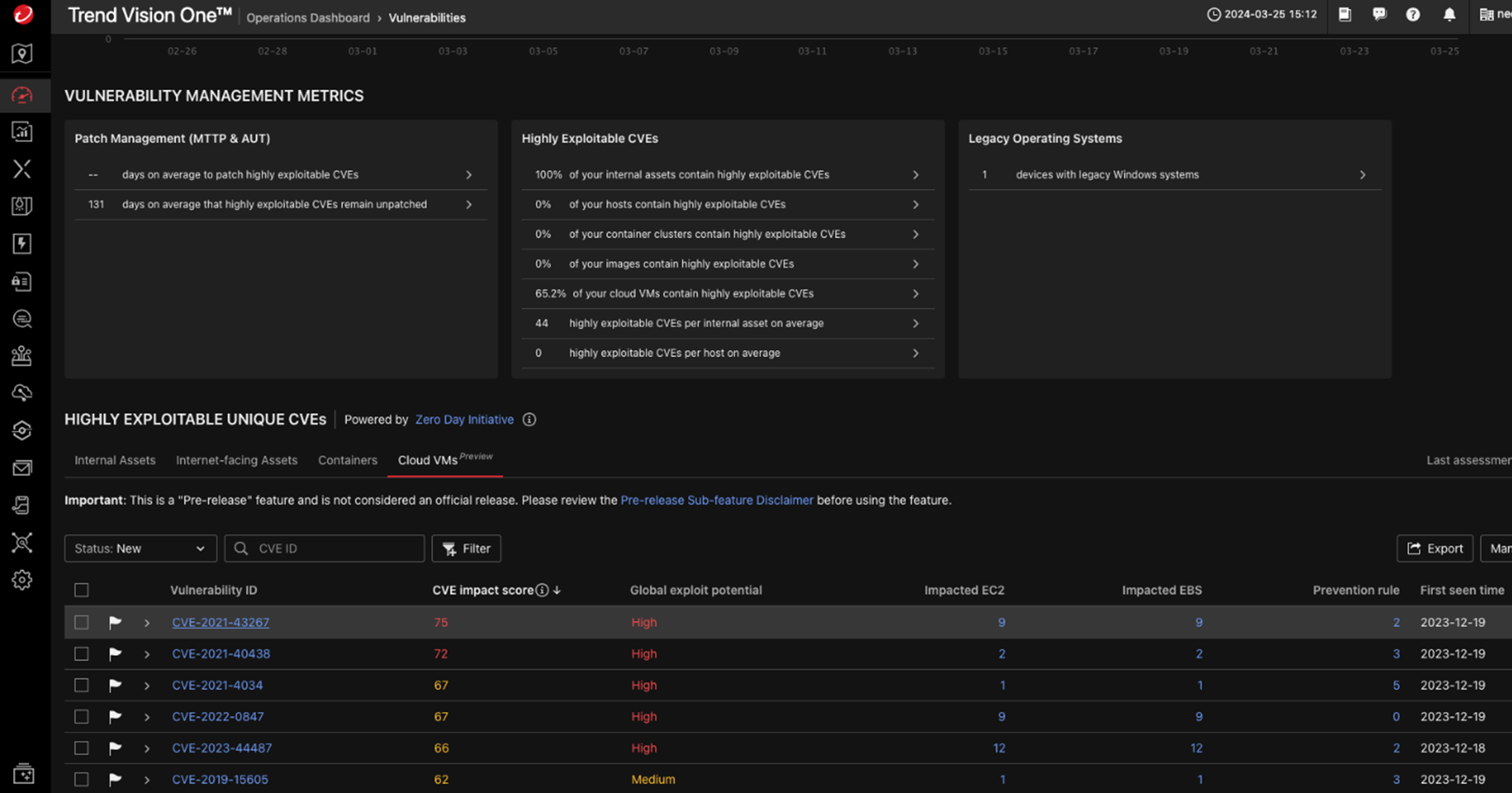
Furthermore, Trend Micro Threat Research and its Zero Day Initiative have provided the world's largest agnostic bug bounty program for nearly 20 years. This brings our customers tremendous knowledge about vulnerabilities and protection through our virtual patching and Network IDS/IPS capabilities. This helps protect customers against exploits and attacks on vulnerable applications running on your production environments.
ZDI provided Microsoft with 20% of all the vulnerabilities they disclosed in 2023. With early access to these bugs, we can provide our customers with virtual patches to protect them, on average, 96 days before a vendor patch is released.
Through the vulnerability view, customers have an easy way to see vulnerabilities on their internet facing assets, containers, container registries, and virtual machines (VMs) running in the cloud.
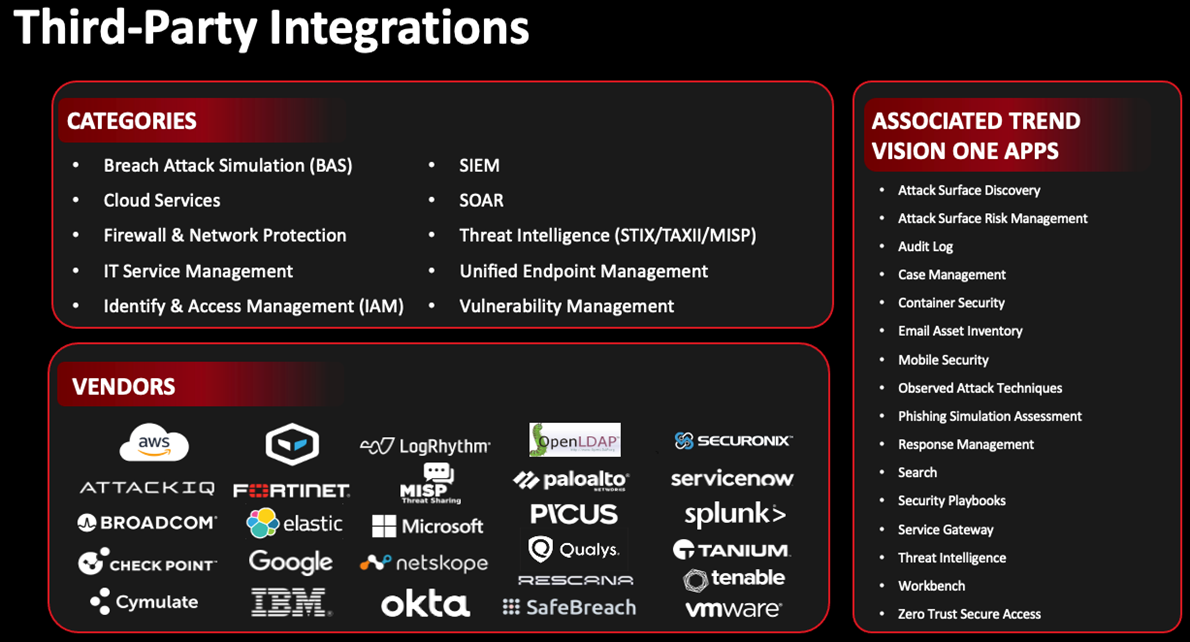
This view can also be enhanced by our third-party integration with vulnerability management vendors to bring full visibility of your vulnerabilities on your hybrid cloud applications.
In addition to its proactive risk mitigation capabilities, Cloud Security also offers preventive measures that integrate security into the development pipeline. By scanning infrastructure as code (IaC) and container images with artifact scanner for vulnerabilities and threats, before deployment and applying security measures early in the development process, it helps ensure that vulnerabilities are addressed at the source, reducing the likelihood of security incidents in production environments. This shift-left approach to security not only enhances protection, but also streamlines the overall development lifecycle.
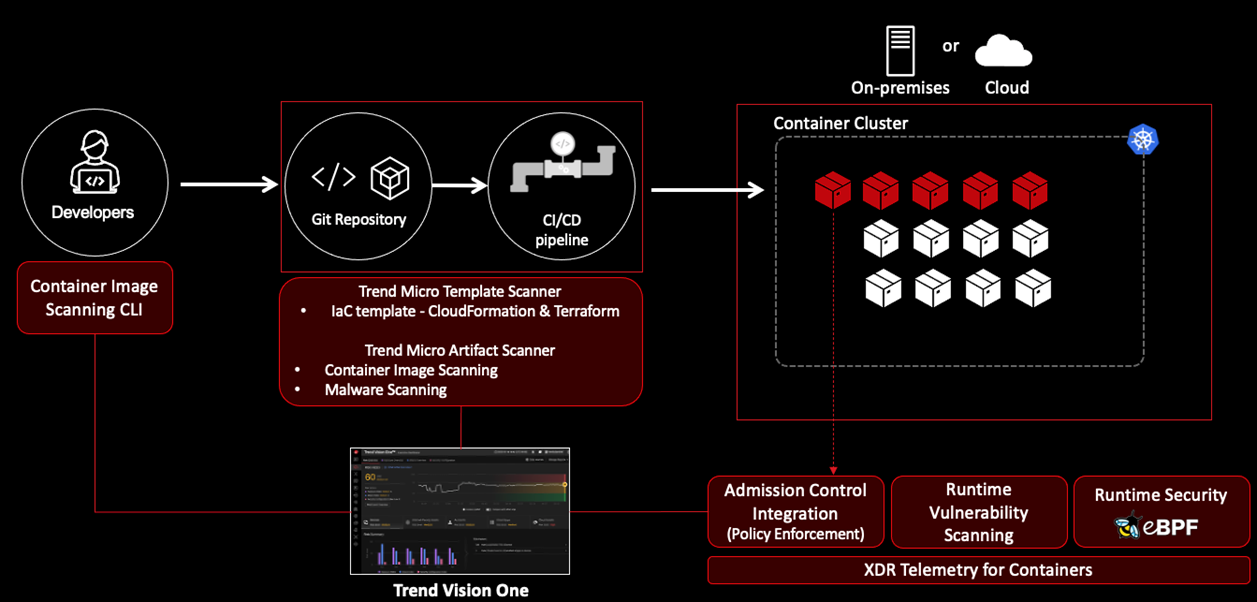
Robust runtime protection
When it comes to runtime protection, Cloud Security offers comprehensive runtime protection that plays a critical role in detecting and blocking threats and vulnerabilities in real time. By monitoring workloads continuously and responding to potential security incidents promptly, Cloud Security provides organizations with a robust defense mechanism against evolving cyber threats. This real-time protection ensures that organizations can maintain the integrity of their cloud environments and respond swiftly to security incidents as they arise.
The architecture above shows you how to operate in the cloud the right way, with development, security, and operations team working together to identify and remediate risks in CI/CD pipelines, and during runtime for modern applications running in container clusters.
The runtime security monitors for any newly discovered vulnerabilities while operating within the cluster, and it aids in the detection of suspicious activities by integrating with eBPF for high-performance monitoring of container clusters.
Conclusion
Developing securely in the cloud without slowing down innovation is paramount for cloud builders. And as the speed of innovation continues to accelerate, it’s clear that siloed, disconnected point products can no longer keep up. A cloud security platform with attack surface and vulnerability management capabilities, robust third-party integrations, threat intelligence feeds, and built-in runtime protection is paramount to meeting security and business goals.
For more information on Cloud Security, click here.

