ANDROIDOS_DOUGALEK.A
Android.Dougalek (Symantec)
Information Stealer
Android OS


Threat Type: Trojan
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This malware may arrive using certain package names and installed as certain applications.
This application displays videos from remote sites.
In the background it executes its malicious code to gather certain information. It then sends these information to certain remote websites.
This Trojan may be unknowingly downloaded by a user while visiting malicious websites. It may be manually installed by a user. It may be downloaded from app stores/third party app stores.
TECHNICAL DETAILS
Arrival Details
This Trojan may be unknowingly downloaded by a user while visiting malicious websites.
It may be manually installed by a user.
It may be downloaded from app stores/third party app stores.
NOTES:
It may arrive using the following package names and installed as the following applications:
| Package Name | Application Name After Installation |
|---|---|
| jp.animedouga.apk | アニメ動画 |
| jp.bizindouga.apk | 美人動画 |
| jp.geinoudouga.apk | 芸能動画 |
| jp.gurabiadouga.apk | グラビア動画 |
| jp.himatubusidouga.apk | 暇つぶし動画 |
| jp.kowaidouga.apk | 怖い動画 |
| jp.nikonikodougamatome.apk | ニコニコ動画まとめ |
| jp.oomosirodougamatome.apk | 面白動画まとめ |
| jp.waraerudouga.apk | 笑える動画 |
| jp.youtubebedouga.apk | youtube動画 |
| jp.youtubedougamatome.apk | youtube動画まとめ |
| jp.yoututubebedouga.apk | ユーチューブ動画 |
| jp.youtuubedougamatome.apk | ようつべ動画まとめ |
| jp.yoyotubedouga.apk | ようつべ動画 |
| jp.yuutubedougamatome.apk | ユーチューブ動画まとめ |
| jp.nakerudouga.apk | 泣ける動画 |
| jp.douzinviewer.apk | 同人ビュワー |
| jp.eroperiax.apk | エロぺリアX |
| jp.hhhdougakan.apk | HHH動画間 |
| jp.iketerudouga.apk | イケてる動画 |
| jp.kabukichogozennizi.apk | 歌舞伎町午前2時 |
| jp.poruchiokupaa.apk | ポルチオクパぁ |
| jp.setunaigirl.apk | 切ないガール |
| jp.subarasikidouga.apk | 素晴らしい動画 |
| jp.yutorinohutomomo.apk | ゆとりの太もも |
This application displays videos from remote sites. Upon execution, it displays the following:
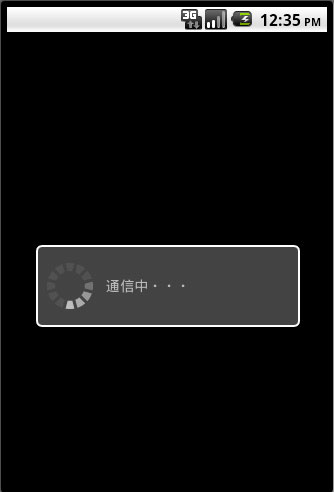
In the background it executes its malicious code to gather the following information:
- android ID
- contacts details (name, mobile number, email address)
- mobile number
It then sends these information to any of the following remote sites:
- http://{BLOCKED}t.bulks.jp/get37.php
- http://{BLOCKED}t.bulks.jp/get43.php
- http://{BLOCKED}t.bulks.jp/get46.php
- http://{BLOCKED}t.bulks.jp/get47.php
- http://{BLOCKED}t.bulks.jp/get55.php
The videos it plays come from any of the following remote sites:
- http://{BLOCKED}t.bulks.jp/movie/movie37.mp4
- http://{BLOCKED}t.bulks.jp/movie/movie43.mp4
- http://{BLOCKED}t.bulks.jp/movie/movie46.mp4
- http://{BLOCKED}t.bulks.jp/movie/movie47.mp4
- http://{BLOCKED}t.bulks.jp/movie/movie55.mp4
However, during testing the URLs are already inaccessible. The app displays the following error message:
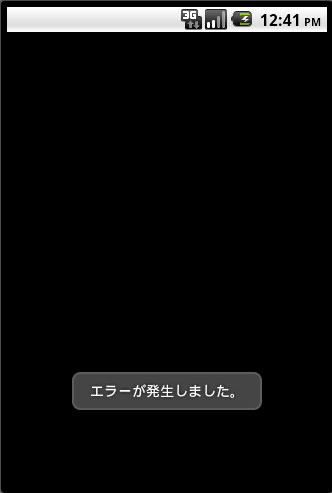
SOLUTION
Step 1
Trend Micro Mobile Security Solution
Trend Micro Mobile Security Personal Edition protects Android smartphones and tablets from malicious and Trojanized applications. The App Scanner is free and detects malicious and Trojanized apps as they are downloaded, while SmartSurfing blocks malicious websites using your device's Android browser.
Download and install the Trend Micro Mobile Security App via Google Play.
Step 2
Remove unwanted apps on your Android mobile device
Step 3
Scan your computer with your Trend Micro product to delete files detected as ANDROIDOS_DOUGALEK.A. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.


