Key Strategies for Securing the Hybrid Cloud
In essence, the hybrid cloud offers the best of both worlds: the customizability and flexibility of the data center coupled with the convenience of the public cloud. This adaptability is what makes it attractive for enterprises. According to Gartner, by 2020, 90 percent of organizations will have moved to hybrid cloud infrastructure, according to Gartner.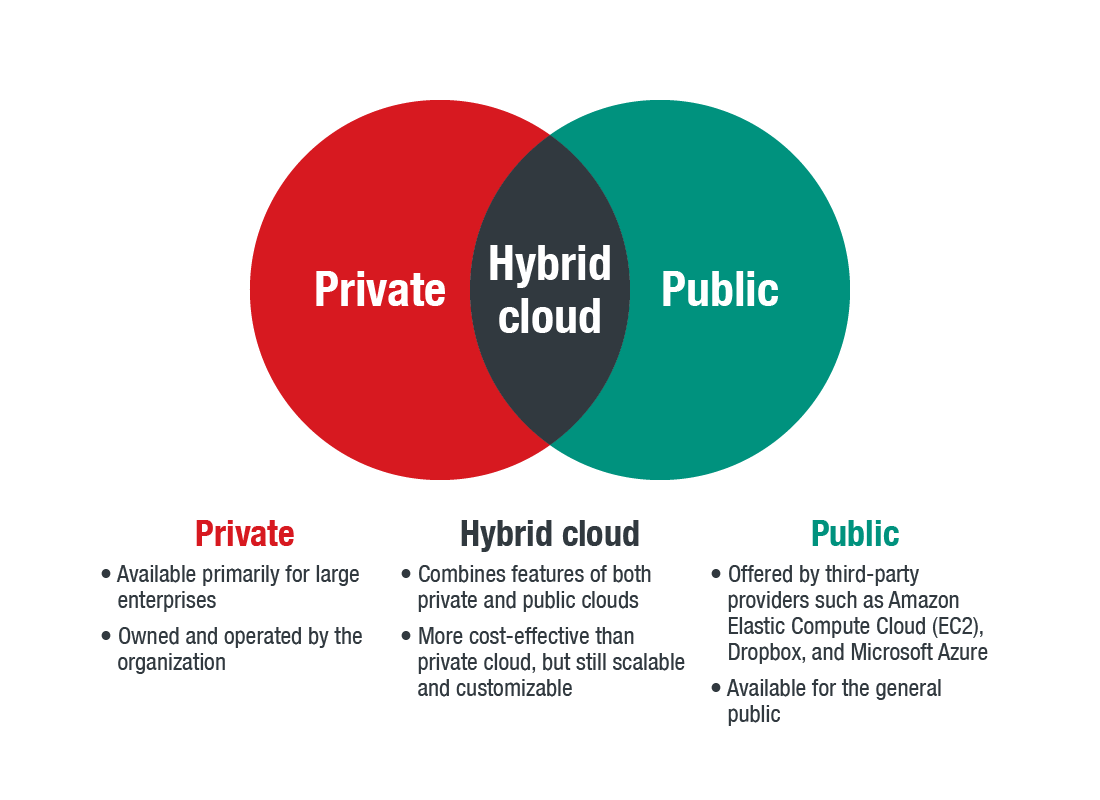
Hybrid clouds are as customizable as required, so the security requirements that an organization needs are variable as well. For example, some companies may opt for minimal interaction with the data center portion of their cloud solutions, while others may use it for most of their operation, using only the public cloud for storing nonessential data. When it comes to hybrid clouds, information technology (IT) personnel should know exactly what type of setup their organization uses, and where the data is located — whether hosted on public cloud networks or stored in data centers.
Threats to the cloud
With regard to the cloud, it is important to understand that threats are often not cloud-specific. Threats such as ransomware, business email compromise (BEC) attacks, and especially data breaches can occur in cloud environments as well as traditional ones. For example, organizations that use cloud-based email services can be susceptible to everything from simple spam and phishing attacks to BEC scams. Also, data breaches can happen because of malware attachments, or they can be the result of man-in-the-middle attacks on the cloud. Organizations, therefore, should implement proper security measures to protect their networks and systems, regardless of what type of setup is used.
Securing the hybrid cloud as a shared responsibility
No matter what kind of setup they employ, organizations need to adhere to a very important principle of cloud security: shared responsibility.
Organizations sometimes make the mistake of assuming that their service provider will handle all aspects of cloud security and that once the service is in play, they will no longer have any need to secure their cloud. The truth is that cloud security is a shared responsibility: While the service provider offers security for the underlying infrastructure, the organization is responsible for securing the data itself. This further means implementing access policies, ensuring proper encryption, and managing the overall configuration of the cloud service to fit the needs of the organization. This also extends to other security aspects such as updating and patching machines within the organization and monitoring the software installed on these machines.
An organization should consider all its requirements when choosing a third-party provider for its cloud service — not only in terms of features but also in terms of security and access control. Depending on the cloud service used, service providers will also have access to organizational data, which may not be feasible for some organizations.
Despite the large variance in hybrid cloud setups, there are certain security principles that apply to all forms of hybrid clouds, which can be summarized in four points:
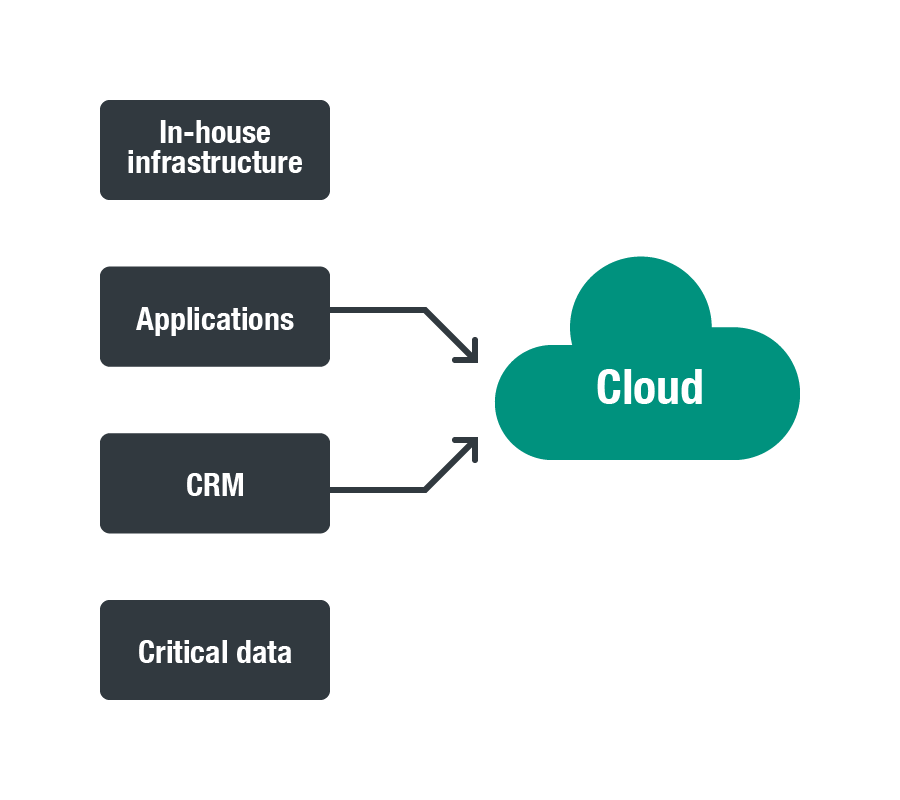
- Adherence to a single process regardless of environment will make the whole system run much more smoothly. Mixed processes for both the cloud and traditional environments do not mesh well together. Organizations need to create an environment that takes into account the requirements for both cloud and traditional systems. A traditional infrastructure typically includes applications and platforms as well as business processes. Hybrid cloud can integrate into the existing infrastructure of an organization and provide flexibility and scalability. For example, an organization can retain its critical workloads, such as data, on its on-site or traditional servers, while moving applications, emails, and customer relationship management (CRM) into the cloud.
- Tools that scale automatically will help organizations maximize both their manpower and their resources, allowing for greater focus on the core areas of operations. This is one of the major advantages of a hybrid cloud. On-premise infrastructure can be expensive to upgrade: There are hardware costs, maintenance costs, and even application development and deployment costs that can quickly add up as the operations begin to scale. Hybrid clouds can be customized to a company’s needs without its having to shoulder the costs that are associated with scaling up an operation.
- Customizable tools that are programmable will allow organizations to tailor them according to the organizations’ respective specific requirements. Most hybrid cloud providers offer a range of options to organizations that can be customized to fit their requirements.
- The security solutions deployed have a degree of “decision-making,” that is, they are smart enough to make security decisions on behalf of the organizations. Like the second point, it allows for less manpower and resources to maximize security. This is especially important for organizations, given that a large portion of their operations may be hosted on the cloud. Considering the sophistication of modern-day threats, it might not be enough for hybrid cloud providers to offer only rudimentary security solutions with their products and services; the security technology should also be smart enough to adapt and learn even without human intervention.
Best practices for securing the cloud
No matter what type of cloud structure an organization uses, these best practices will help maximize its cloud security.
Employ the principle of least privilege.
All cloud environments should implement the principle of least privilege, which states that access to specific portions of the system should be given only to users who need it. This was already covered in the private cloud portion, but since it is a very crucial part of cloud security that extends to all kinds of cloud environments, it needs to be emphasized.
Secure all endpoints in the network.
The use of cloud infrastructure does not rule out the need for stronger endpoint security. Many attacks start at the endpoint level, and this is no different when it comes to cloud-based systems. Accordingly, organizations should implement proper endpoint protection, which includes using comprehensive security solutions that provide features such as browser exploit protection and application whitelisting, as well as providing proper user education on security.
Isolate the most critical infrastructure.
For organizations that store important data on the cloud, the idea is that fewer is more: The fewer the people who have access to important data, the more secure it is from potential attacks.
Encrypt data passing through the cloud.
This is also one way to isolate the most critical infrastructure. Data — both in transit and at rest — should be encrypted as a general security measure. Many cloud service providers already offer encryption of data as part of their security measures, but organizations that want to take their cloud security further can look into solutions that include data encryption.
Back up critical data on external storage devices.
The use of cloud infrastructure does not guarantee the safety of organizations’ data, since an attack or system failure can mean temporary or even permanent loss of data. For a more comprehensive approach to security, organizations should back up their data both physically and virtually, as doing so ensures that data is accessible at all times.
Create a business continuity and disaster recovery plan.
Organizations should have a backup plan that ensures that operations will still run smoothly in case of emergencies, such as the disruption of services or power outages in data centers. This includes the implementation of image-based backups that can create copies of computers or virtual machines (VMs) that in turn can be used to restore or recover data.
Choose the right cloud security solution.
Organizations should choose the right cloud security solution for their organizations based on what can give them the most protection. The Trend Micro™ Deep Security™ solution for the cloud can provide proactive detection and prevention of threats, while the Trend Micro Hybrid Cloud Security solution, powered by XGen™ security, provides optimal security for hybrid environments that incorporate physical, virtual, and cloud workloads.
A hybrid cloud environment requires hybrid security solutions. Organizations can secure critical data and applications across their cloud and virtualized environments with effective server protection that maximizes their operational and economic benefits. The Trend Micro Hybrid Cloud Security solution protects applications and data from critical modern threats, such as ransomware, that can cause significant business disruptions, while helping to accelerate regulatory compliance.
Whether organizations are focused on securing physical, virtual, cloud, or hybrid environments, the Trend Micro Deep Security solution can provide the advanced server security organizations need.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One