How Vetting Mobile Apps Works for App Stores and Its Users
These days, when you see someone staring intently or tapping at their mobile phones, chances are that they’re busy using an app. In the United States, for instance, a massive majority or 80% of consumers’ time on a mobile is spent on apps for gaming, news, productivity, utility, social networking, and more (the remaining 20% is spent on the web).
Indeed, mobile app adoption continues to flourish, as shown by the growing number of mobile app downloads worldwide. By the end of this year, there would have already been roughly 180 million mobile app downloads, and the yearly number is projected to total 270 million app downloads per year by 2017. Meanwhile, some say that the days of the so-called “bulky square” mobile apps are not going to last forever.
Why do people like their apps so much?
Research indicates that changes in mobile computing behavior—what consumers like to do when they’re on their phones—is driving this growth. For instance, there are certain app categories that people now like to engage more time in than others. Music apps showed the largest growth; over an hour, 64 minutes, were added to the total time people spend on them every month. This may be a result of more people opting for their music apps for commutes or downtime. Meanwhile, when it comes to which apps people open or launch the most, social media apps still dominate.
App stores also serve as catalysts for mobile usage. Each OS and device creator features an official app store, where either pre-approved or curated apps are available as direct downloads. However, from what we found, mobile users also tend to download apps from third-party stores.
Looking at the samples gathered as of October, we found that the number of downloaded apps from third-party app stores (4.17 million) is more than the number downloaded from Google Play (2.58 million) or than those downloaded from all other app stores (4.13 million).
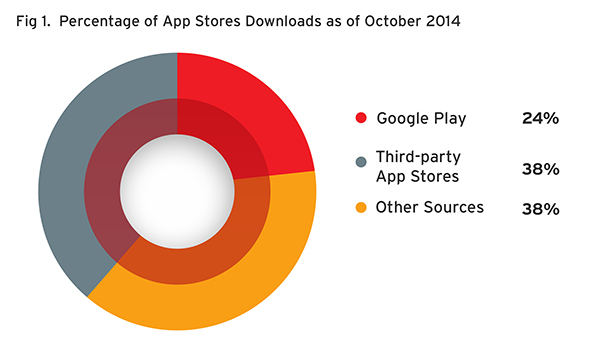 Percentage of App Stores Downloads as of October 2014
Percentage of App Stores Downloads as of October 2014
Third-party app stores are quite popular to mobile users for a number of reasons. For one, they allow users the option to download and install apps in APK format, which is perfect especially for apps that are already taken out of official app stores. Third-party app stores also often offer trial or discounted versions of apps that are otherwise priced higher on official ones. Lastly, downloading apps from third-party stores is the only option for select countries where the official app stores are either blocked or feature apps that are too expensive.
Notably, the more lenient approval process for these app stores also invites more developers to create and distribute more apps there. As a result, they create niche marketplaces that cater to very specific but demanding markets.
Apps and risky taps
If the mobile world were a high-class hotel, apps are clients who get the VIP pass. They are the highest grossers. No wonder developers like to create them; they offer an effective way to generate more revenue.
However, not all apps are created because of this. Some apps are made with the intention to either steal, spy, or destroy. As of October, we reached a total of almost 11 million unique apps in our sample collection, 3.8 million of which we detect as Android threats. More threats originally created for computers are also jumping into mobile devices, and vice versa. The USBATTACK malware for Android, for one, is installed as an Android device cleaner but can actually steal information, download AUTORUN on the SD card, and then run itself on a connected PC and use its microphone to record.
For the month of October, of the 532 thousand new Android samples we received, we counted 317 thousand Android threats that comprise at least seven different types of apps, including malicious and high-risk or potentially unwanted apps (PUA) like adware, as shown below: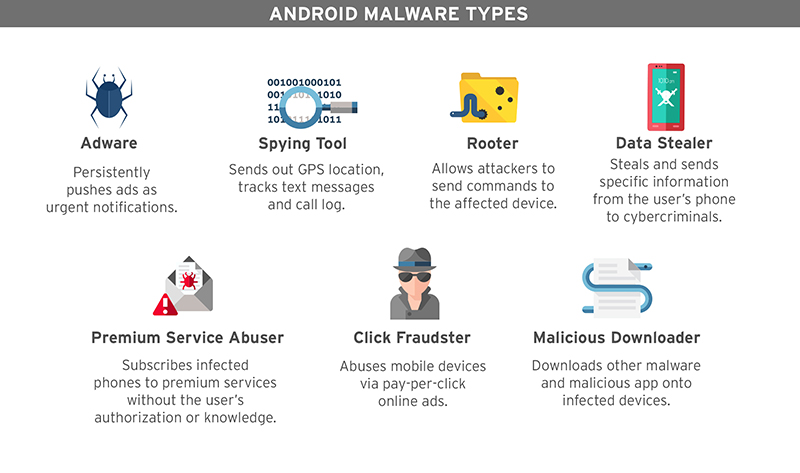
Android Malware Types
How app store vetting processes work to ensure safety
Similar to high-class hotels, app stores don't just let anyone in. Of course, they have to guard their premises to ensure that the environment is safe. Security standards differ depending on the hotel, and it's the same as the processes used to keep app stores safe. The standards depend on the app store owners.
In the technology industry, the process of vetting apps is a valid option to ensure the safety of app stores. This validation process is a broadsword that helps both the consumers and organizations in the business of creating and regulating app stores.
The diagram below shows how the vendor Blackberry, for instance, makes use of technology to screen mobile apps:
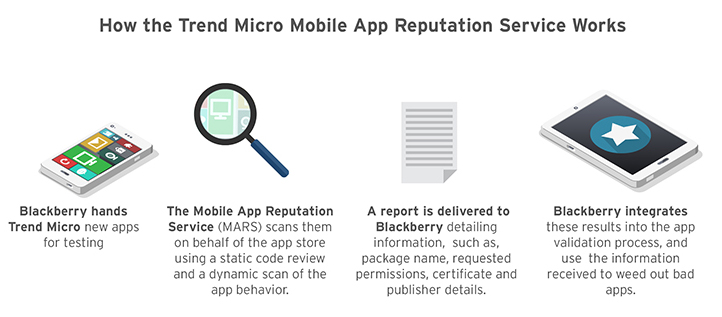
How the Trend Micro Mobile App Reputation Service Works
Vetting mobile apps has been proven to aid organizations in evaluating apps and catching malicious ones before they are released in the app stores. Using this process, Blackberry has been noted to block malicious apps from their store. Known technology breakthroughs can do this without hardware and headcount increase.
The following app categories are typically used to vet apps: 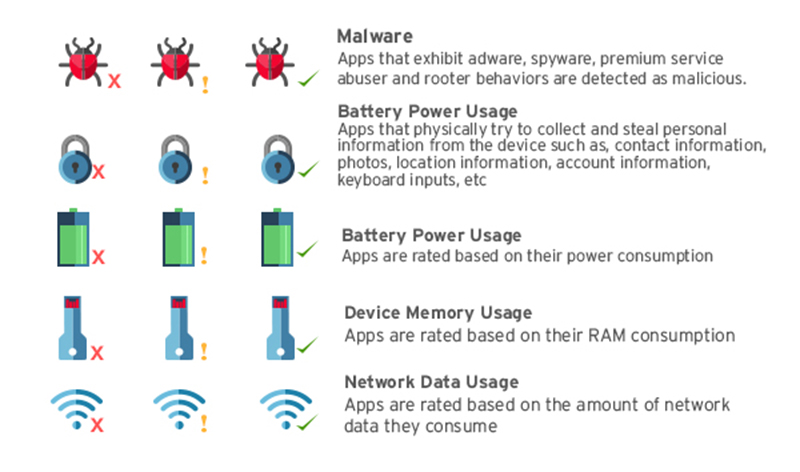
Security and Resource Ratings
These categories are especially helpful for mobile users who wish to maximize their device’s potential while ensuring that their data and resources are protected. Given the ratings provided for each app, it will be easier and more accurate to decide on which hogs resources, consumes battery fast, takes up a lot of memory, or consume too much data.
Mobile Threats in October
Given the sheer number of malware samples collected daily, the screening process for apps serve as the security personnel in an otherwise bustling and confusing app store environment. From what we have seen, legitimate and third-party app stores were filled with threats that are either safe, ad-heavy (high-risk/ adware), or outright malicious (malware).
Adware apps display ad content, often at the expense of network or device performance. Meanwhile, the malicious ones may pretend not to be malicious, but actually exhibit bad routines when already in the device.
The pie chart below shows the malware detections based on unique samples since we started scanning app stores. Nearly a quarter, 23%, are malware while 13% are adware. The rest of the apps, 64%, were considered safe.
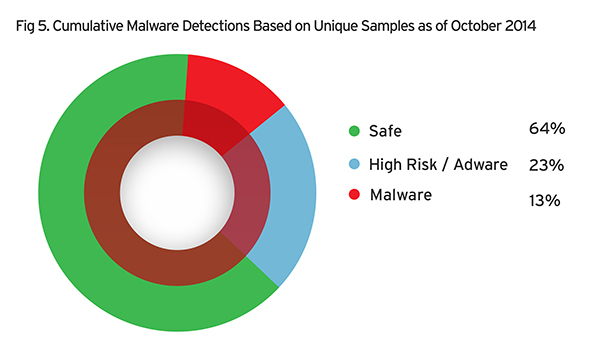 Cumulative Malware Detections Based on Unique Samples as of October 2014
Cumulative Malware Detections Based on Unique Samples as of October 2014
For the month of October, almost a third, 29%, are malware, while a third, 30%, are adware. Less than half, 41%, of the apps checked were considered safe.
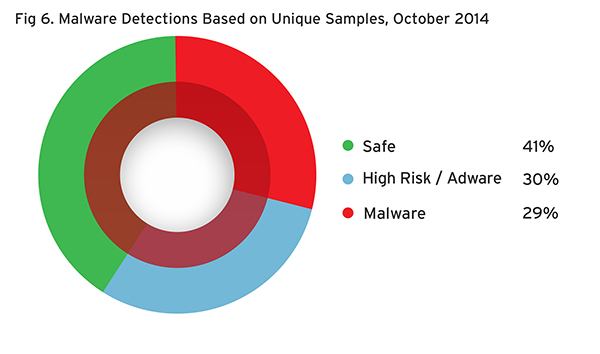 Malware Detections Based on Unique Samples, October 2014
Malware Detections Based on Unique Samples, October 2014
Roughly half of the malicious apps are from the OPFAKE (27.35%) and FAKEINST (26.74%) families combined. Both these malware families belong to the premium service abusers threat type, which typically subscribe users to costly premium services without their consent. OPFAKE variants are usually linked to malware apps that pretend to be legitimate ones, like fake World Cup 2014 apps and Flappy bird clones. Similarly, FAKEINST variants are linked to fake apps like the rogue version of a Bad Piggies app.
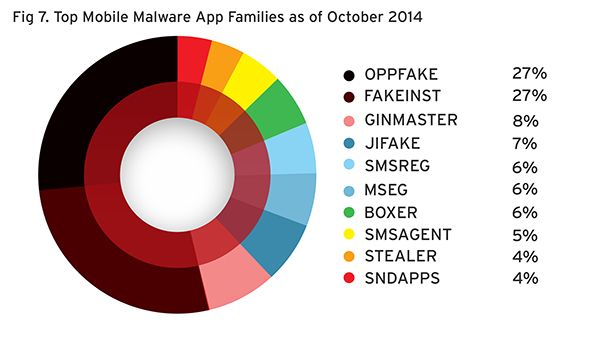 Top Mobile Malware App Families as of October 2014
Top Mobile Malware App Families as of October 2014
For adware, a significant cut of the pie, 30%, were detected to come from the GOYEAR app family. The AIRPUSH (10%) and DOWGIN (8%) ad services also remain among the top adware families this month.
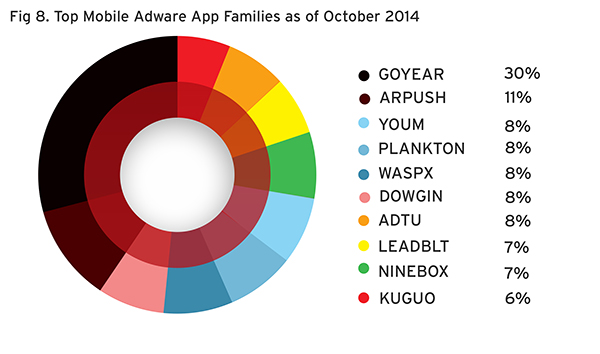 Top Mobile Adware App Families as of October 2014
Top Mobile Adware App Families as of October 2014
These rogue apps and adware apps are socially engineered threats that target the general public. Using popular apps they know most people like to download, they are assured of a large number of victims. Given that these apps can do a lot of things, depending on the permissions they’re given, it is especially dangerous to have them on mobile devices. Now that the holiday shopping season is near, we expect the emergence of more mobile threats that target online banking users and, very soon, mobile payment users as well.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One