Pawn Storm in iOS Apps and Other Cases of Mobile Links in Targeted Attacks

When the Pawn Storm campaign was first discovered in October last year, it had the notable bearings of a full-blown active economic and political cyber-espionage operation. Its targets range from military agencies in the US and its allies to opposition politicians and dissidents of the Russian government, and even International media.
Pawn Storm used decoys and delivered malware via a three-pronged attack vector that use spear-phishing emails, a network of phishing emails that take advantage of typographic errors, and malicious iFrames injected into legitimate sites.
[Read:Pawn Storm Espionage Attacks Use Decoys, Deliver SEDNIT]
Since the Pawn Storm operation affected only computers and servers at the time, mobile device users were spared from data theft. But that was in 2014.
What the new year ushered in was a specific, unusual, and impactful addition to how Pawn Storm attackers can try to get inside their target networks, i.e., via an iOS mobile app. Millions of iOS devices were at risk because of two spyware apps tracked back to the campaign.
[Read: Millions of iOS Devices at Risk from ‘Operation Pawn Storm’ Spyware]
“The actors of Pawn Storm tend to first move a lot of pawns in the hopes they come close to their actual, high profile targets. When they finally successfully infect a high profile target, they might decide to move their next pawn forward: advanced espionage malware. The iOS malware we found is among those advanced malware,” reports Trend Micro mobile threat analysts Lambert Sun and Brooks Hong, and senior threat researcher Feike Hacquebord in an update to the research into the Pawn Storm operation.
[Read: Detailed technical analysis of the iOS apps for researchers]
This is not the first we have seen of threat actors abusing the mobile platform to get to their targets. Take a look at how mobile devices and platforms were used or attacked in the following targeted attack campaigns:
2012 | LuckyCat
Luckycat, a targeted attack campaign linked to 90 attacks against multiple industries and/or communities in Japan and India, targeted Android users. Threat researchers uncovered evidence of mobile apps, which act like remote access tools (RAT), inside Luckycat servers. These apps can gather information about the mobile device as well as upload or download files from it via remote access.
2013 | Chuli
Targeted attacks against Tibetan and Uyghur activists were initially carried out using social engineering attacks that download files meant to exploit victims using Windows and Mac OS X platforms. It was later discovered that the same attack involved an APK attachment of a malicious Android app (detected as ANDROIDOS_Chuli.A) that was sent using the hacked email account of a targeted activist.
2014 | Xsser mRat
In the analysis of what was believed to be a targeted attack campaign by Chinese-speaking attackers against Chinese protesters, researchers found cross-platform malware Xsser mRat (detected as AndroidOS_Code4HK.A) targeting both Android and iOS devices. This malware is said to expose device information such as SMS, email, instant messages, location data, usernames and passwords, call logs, and contact information.
2014 | Regin
The Regin campaign, which targeted governments, financial institutions, telecom operators, research organizations and other industries in multiple countries, was found attacking GSM base station controllers. The attackers were able to collect credentials needed to manipulate a Middle Eastern country’s GSM network, the control of which could allow them to access to access data on calls, redirect calls, and perform other malicious routines.
Reasons and Implications of Mobile as an Attack Vector
A year ago, we predicted that boundaries will be blurred when it comes to cybercrime and targeted attacks. With the steady rise of consumerization in the workplace, we believe mobile devices will not only be attacked to target mobile banking users, but will also be abused as a means to get to target networks.
Attackers target mobile devices because they are both popular and convenient. Unsafe mobile habits that users practice in their personal lives can easily leak into the workplace, thanks to the BYOD trend.
In addition, mobile devices are ideal tools for launching phishing attacks against probable targets. “This trend in launching phishing attacks on mobile devices can be attributed to certain limitations of the platform itself. This includes the small screen size in most mobile devices, which prevents users from fully inspecting websites for any anti-phishing security element,” remarks fraud analyst Paul Pajares.
Growing Mobile Malware as Attack Motivation
The increasing number of mobile cybercrime victims may also serve as an inspiration for success for threat actors to launch targeted mobile attacks. Attackers need only take a look at the crop of mobile malware and high-risk apps that now exist to realize that the mobile landscape is a promising one.
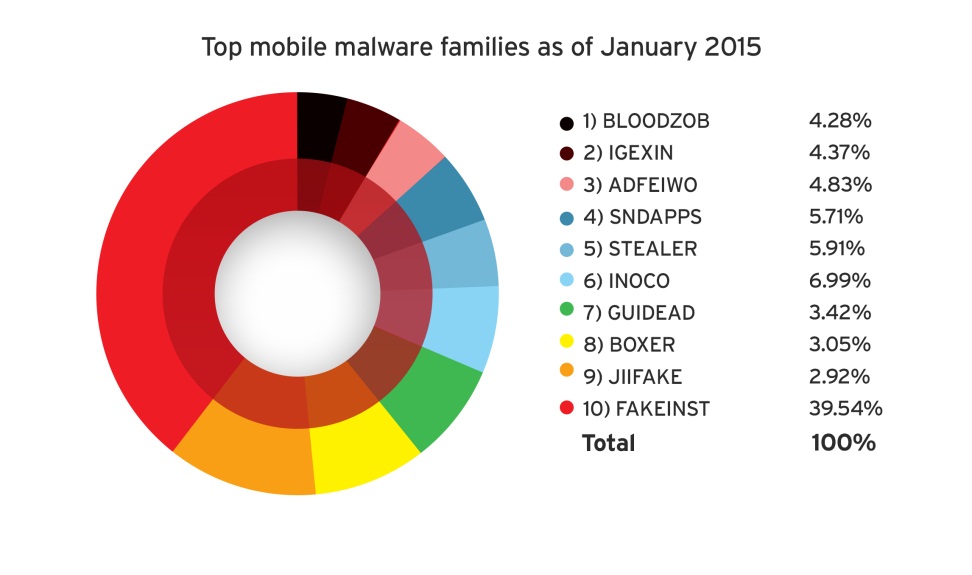
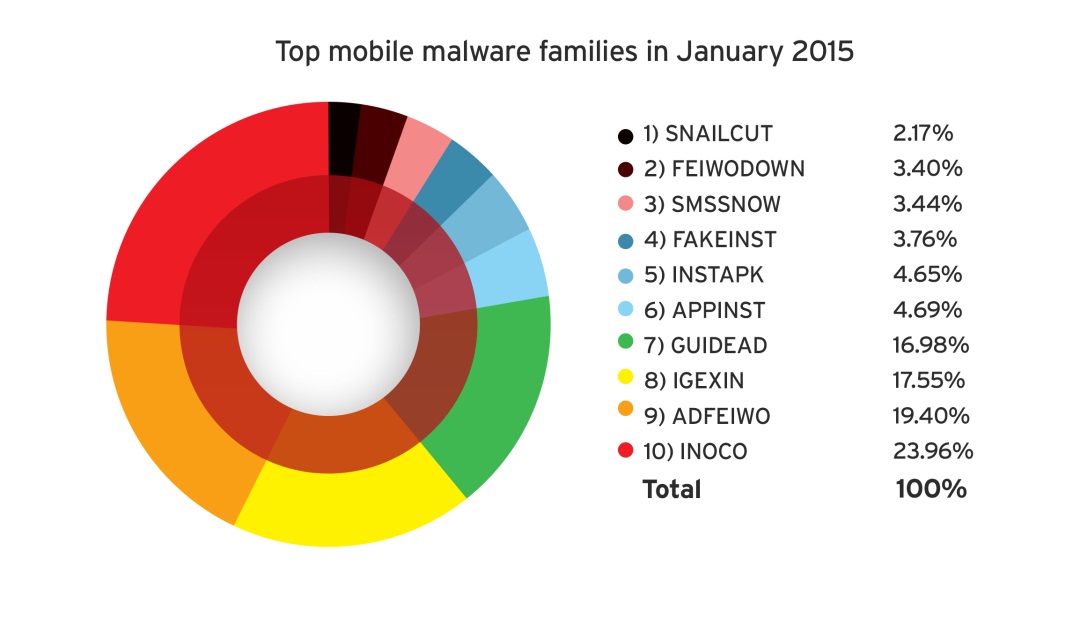
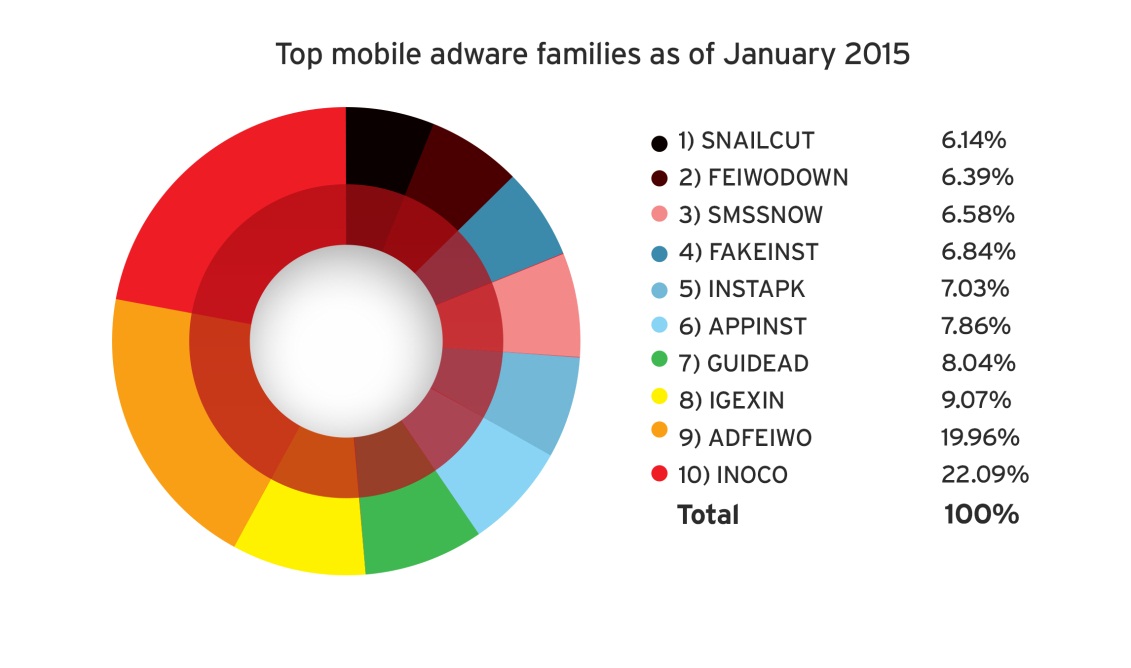
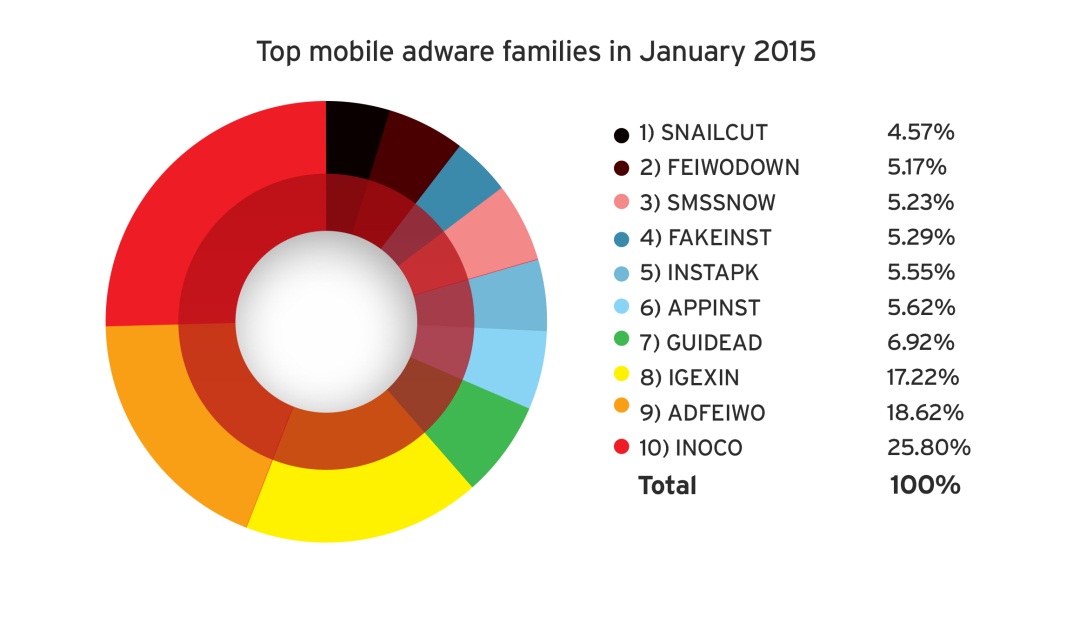
[Read:Masque, FakeID, and Other Notable Mobile Threats of 2H 2014]
Best practices
The nature of the modern workplace is to be open to technologies and habits brought about by consumerization and the IoE. For enterprises, the key to protecting from targeted attacks that abuse mobile devices is to recognize that every platform is a possible attack vector, no matter the screen size.
From what we now know, threat actors target cross-platform organizations with a sophisticated blend of threats. Their end goal is always to access confidential corporate information. As such, IT department heads and staff need to develop a defense strategy that covers mobile devices and the data stored in them. Other best practices include:
- A centralized console that makes policy enforcement easier and more consistent,
- comprehensive, reputation-based threat intelligence to spot and block emerging mobile attacks,
- data encryption and data loss prevention tools to protect critical corporate data,
- and mobile and desktop virtualization to separate personal and corporate applications or data in mobile devices.
[Read: How to Protect Multiple Devices from Cross-Platform Threats]
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One