Developing Story: COVID-19 Used in Malicious Campaigns
 Latest update on November 11, 2020. Originally published on March 06, 2020. Former Title: Coronavirus Used in Spam, Malware File Names, and Malicious Domains
Latest update on November 11, 2020. Originally published on March 06, 2020. Former Title: Coronavirus Used in Spam, Malware File Names, and Malicious Domains
COVID-19 is being used in a variety of malicious campaigns including email spam, BEC, malware, ransomware, and malicious domains. As the number of those afflicted continue to surge by thousands, campaigns that use the disease as a lure likewise increase. Trend Micro researchers are periodically sourcing for samples on COVID-19 related malicious campaigns. This report also includes detections from other researchers.
The mention of current events for malicious attacks is nothing new for threat actors, who time and again use the timeliness of hot topics, occasions, and popular personalities in their social engineering strategies.
Update as of November 11
Covid-19 still filled the headlines in the third quarter of 2020, and Trend Micro’s monitoring showed that cyberthreats that used the virus as a lure increased exponentially in September. This spike in malicious activity coincided with a shift in social engineering tactics — instead of using Covid-19 information to trick users, criminals used coronavirus-related school updates and job listings. For example, many schools required more information about students’ health as part of their safety protocols for combating the virus. In late October, security firm MalwareBytes Lab found ransomware hidden in a fake health survey targeting staff at the University of British Columbia (UBC).
Headers used in phishing emails have also changed. Instead of using Covid-19 as the subject, malicious actors are using titles related to job opportunities to trick users into opening spam mail. Many people are out of work due to the economic downturn caused by the pandemic, and are eager to find job openings. Threat actors are aware of what users click on and use the most obvious bait to make their schemes more effective.

Types of Threats Using COVID-19
Spam
Many aspects of daily work, from meetings to presentations and collaborative tasks, have moved online because of quarantine restrictions affecting offices across the globe. As users adapt to new methods of working, they should be wary of cybercriminals using popular online tools, sharing software, and file attachments in their scams. Trend Micro Research found coronavirus-related emails with malicious attachments sent to users as early as February 2020.
Early COVID-19 related malicious email
Now there are ongoing business email compromise (BEC) scams that use the disease as a hook. BEC schemes usually work by tricking targets into transferring money to a criminal posing as someone from within the same company. The email below uses the ongoing health crisis to push for urgent action.
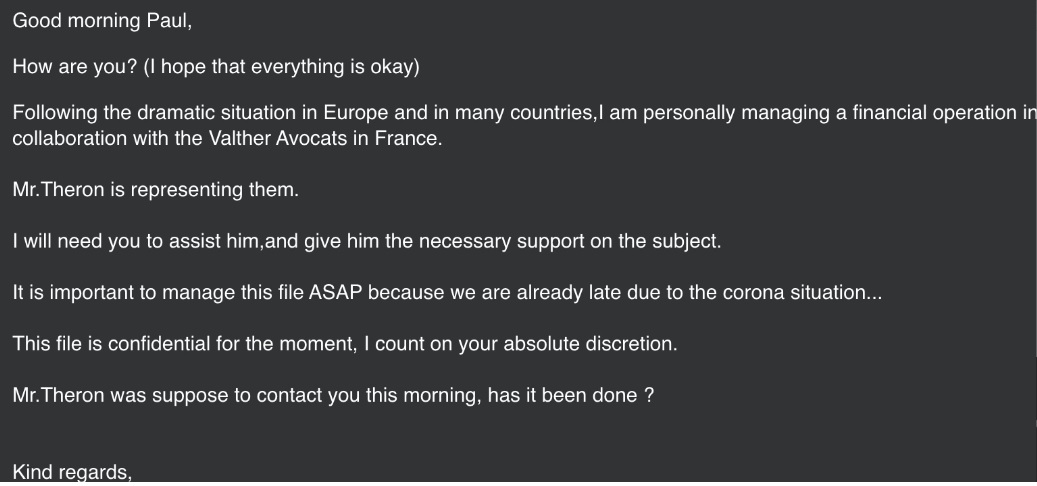
Example of a BEC email using COVID-19
We also have detected emails claiming to be relief or health organizations asking for donations in bitcoin. The emails were sent by a group claiming to be “COVID19Fund,” which is supposedly associated with legitimate health organizations. They ask for aid and provide a cryptocurrency wallet where people can donate.
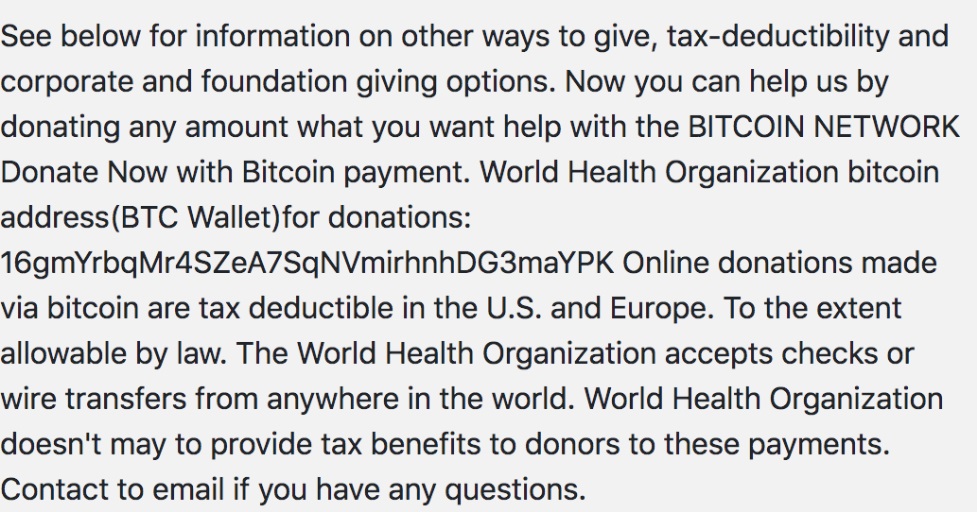
Text from scam email asking for aid for the World Health Organization
Trend Micro researchers also acquired email samples sent to and received from all over the globe, including countries such as the U.S., Japan, Russia, and China. Many of the emails, purportedly from official organizations, contain updates and recommendations connected to the disease. Like most email spam attacks, they also include malicious attachments.
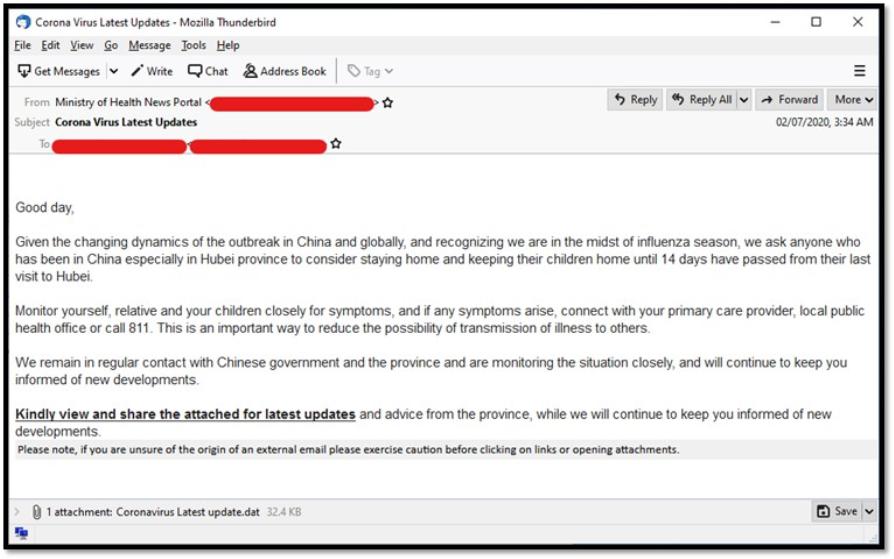
One of the samples used the email subject “Corona Virus Latest Updates” and claimed to come from the Ministry of Health. It contained recommendations on how to prevent infection and came with an attachment that supposedly contains the latest updates on COVID-19 but actually carried malware.
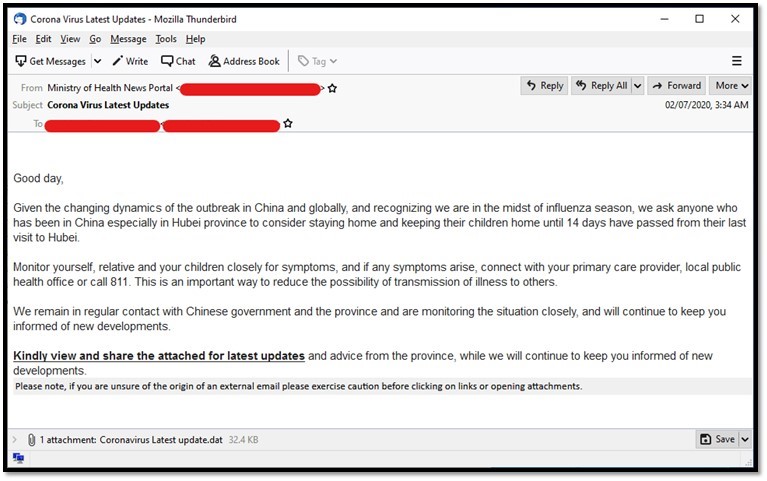
COVID-19 related email spam purportedly from the Ministry of Health
Many of the spam emails were related to shipping transactions, either postponement due to the spread of the disease or one that provides a shipping update. One email informed about shipping postponement. The attachment, supposedly containing the details of the new shipping schedule, bears malware. The email is assumed to come from Japan, and included details written in Japanese (masked in the screenshot).
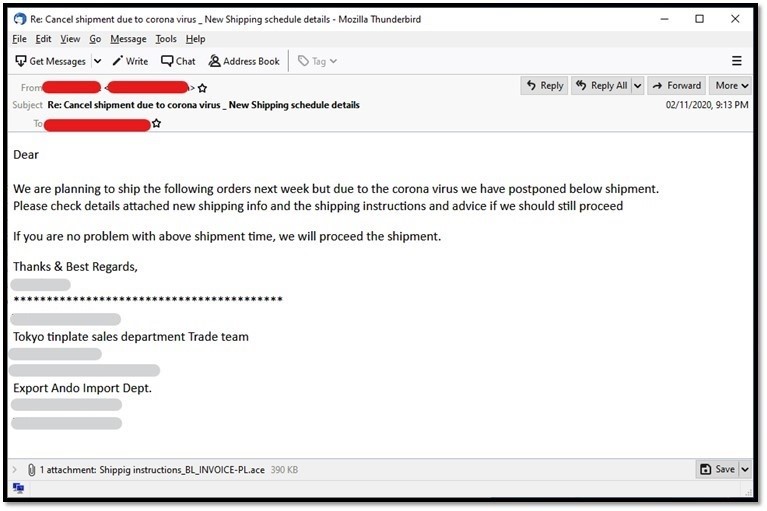
COVID-19 related email spam about a shipping postponement
There were also other samples detected in foreign languages such as Italian and Portuguese. The email in Italian was about important information about the virus, while the email in Portuguese discussed a supposed vaccine for COVID-19.
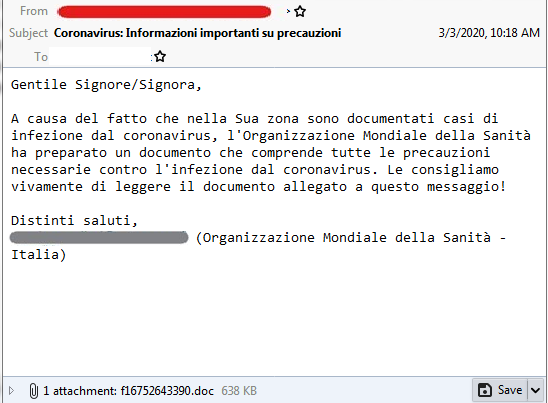
COVID-19 related email spam in Italian
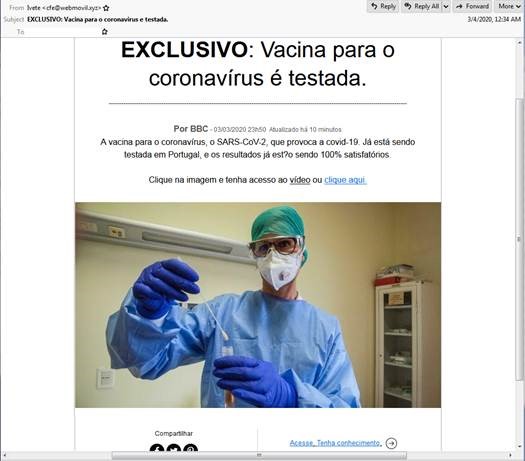
COVID-19 related email spam in Portuguese
Trend Micro researchers encountered an email spam sample targeting China and Italy that mentioned a cure for COVID-19 in the email subject as a lure for downloading the malicious attachment. Further inspection revealed that the payload sample from the attachment is HawkEye Reborn, a newer variant of the information-stealing HawkEye trojan. The file is a heavily obfuscated AutoIT script compiled into an executable. This script will then inject malicious code to RegSvcs.exe. Dumping the injected code will yield a .NET executable that is also packed using ConfuserEx. Part of the decrypted configuration of the HawkEye sample includes the email address and mail server where it will send its exfiltrated data.
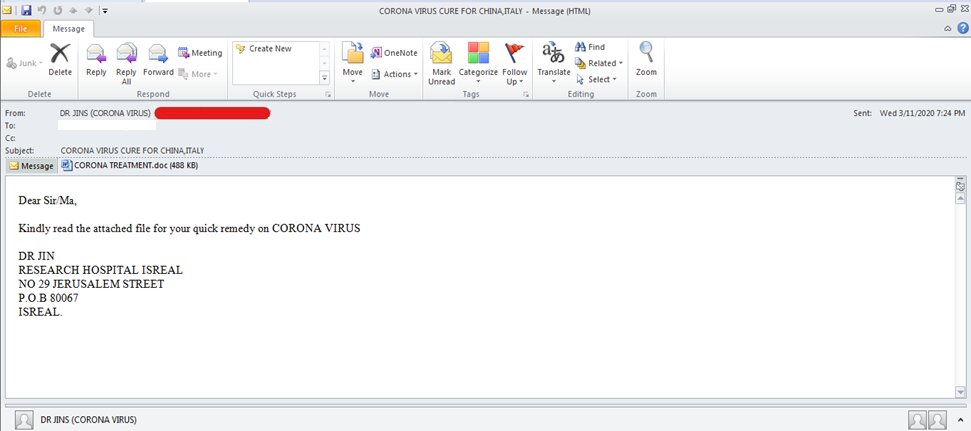
HawkEye Reborn COVID-19 email spam
Other samples of email spam targeting Italy were also detected by Trend Micro researchers. This time, mentions of the disease were not found in the email subjects, but in the URL. The subject instead contained the word “Fattura” (Italian for “invoice”), the invoice number, and its supposed date. The emails had attachments that contain malware, which executes a PowerShell command that will download a file from a URL related to COVID-19. The URL is hxxps://recoverrryasitalycovid-19.xyz/over
Upon further investigation, it was found that the malware used Evil Clippy, a tool for creating malicious MS Office Documents, to hide its macro.
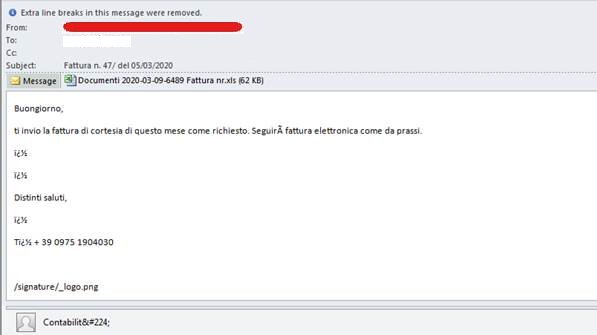
Italian email spam connected to a URL related to COVID-19
And as Italy remains one of the countries most affected by the COVID-19, threat actors also continued to attack users with another spam campaign that we detected on March 20, 2020. Trend Micro researchers detected over 6,000 events of the spam.
Both the email subject and body are written in Italian. The subject translates to “Coronavirus: Important info on precautions.” In the email body, the sender claims that the attachment is a document prepared by the World Health Organization (WHO), and strongly advises the readers to download the attached compromised Microsoft Word file. The malicious file contains a trojan.
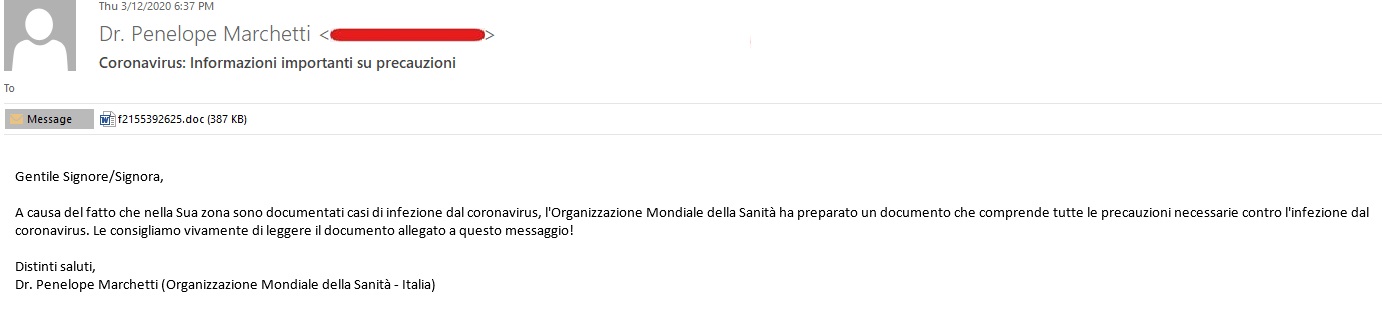
Sample of spam targeting users in Italy
The document contains the following message details luring users to enable macro content:

Attachment sample
Malware that Overrides Master Boot Record (MBR)
Trend Micro Research recently analyzed a coronavirus-themed malware that overrides a systems’ master boot record (MBR), making it unbootable. The malware was detailed in a public report published by the Czech cybersecurity agency (NUKIB). The malware file has "Coronavirus Installer" in the description.
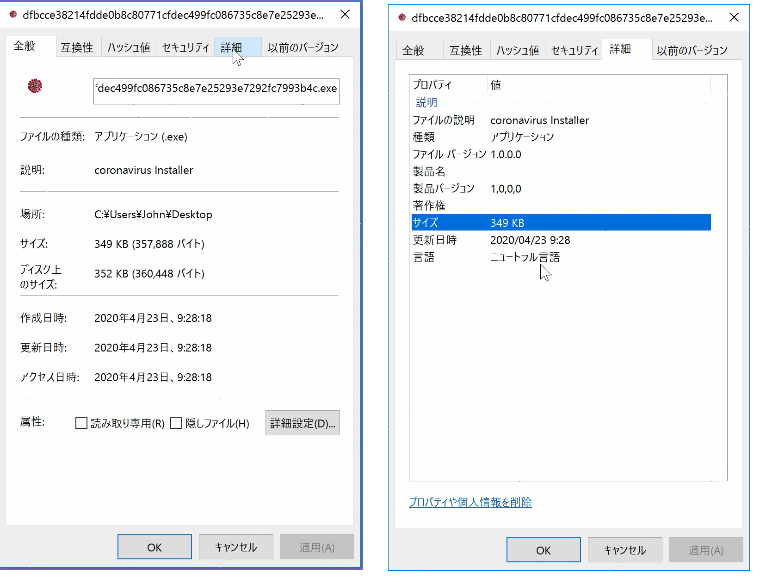
Malware file details
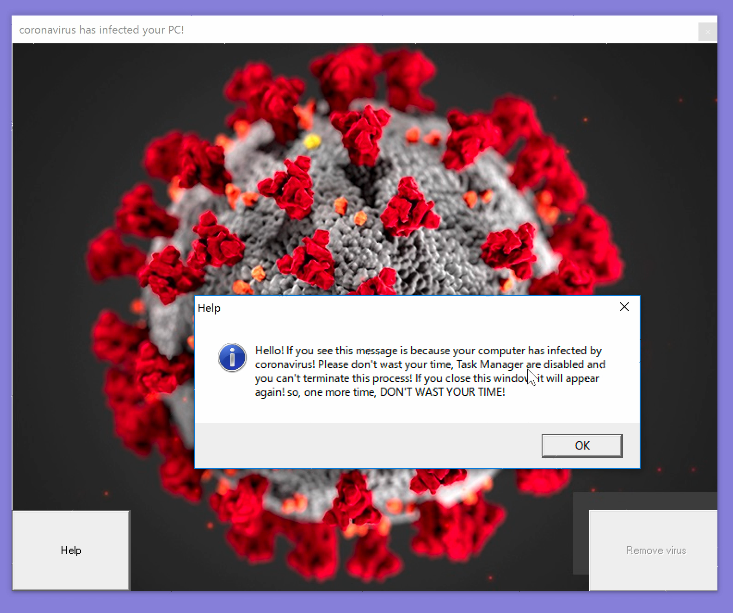
Lockscreen of the malware
When the malware executes, it will automatically restart the machine and then display a virus-themed window that cannot be closed. The usual exit button on the top right side of the window does not function.
Clicking on the “Help” button on the bottom left will bring up a pop-up message notifying that the user cannot start the Task Manager. The “Remove virus” button on the bottom right seems to offer a solution, but it is grayed out and unclickable. The button remains unclickable even when connected to the internet.
The malware also creates a hidden folder named “COVID-19,” which contains several secondary modules. Manually restarting the system will execute another binary file and display the grey screen shown below.
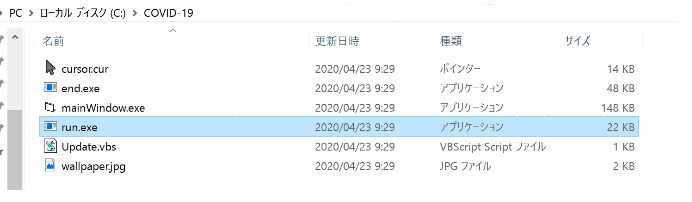
Contents of Covid-19 Folder
Gray screen that shows after a manual reboot
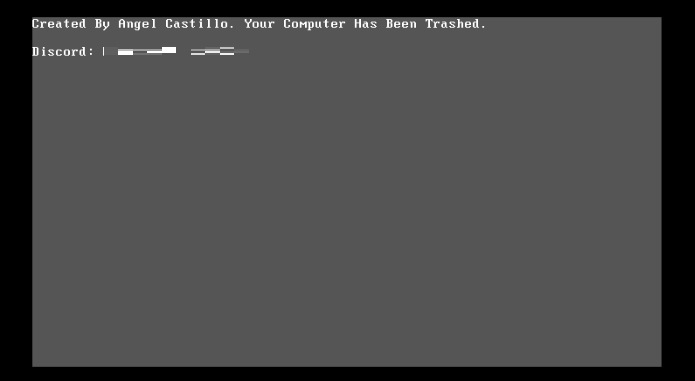
The malware backs up the original MBR and places the text “Created by Angel Castillo. Your Computer Has Been Trashed” on the device screen. It also leaves Discord contact information, implying that the victim needs to communicate with the hacker to find a solution.
Ransomware typically provides victims with fund transfer details, with a specific amount and cryptocurrency wallet to which the victim deposits money. However, recent case studies have found that many malware distributors have taken to using Discord to provide victims specific instructions.
Many attackers simply wipe the MBR at the beginning of the process, so this method seems overly complicated. The file “Update.vbs,” which the secondary module drops, provides a clue as to why its creator designed the process this way. This VBS file will display a message box indicating that the user will need an internet connection (likely displayed two minutes after the grey screen appears).
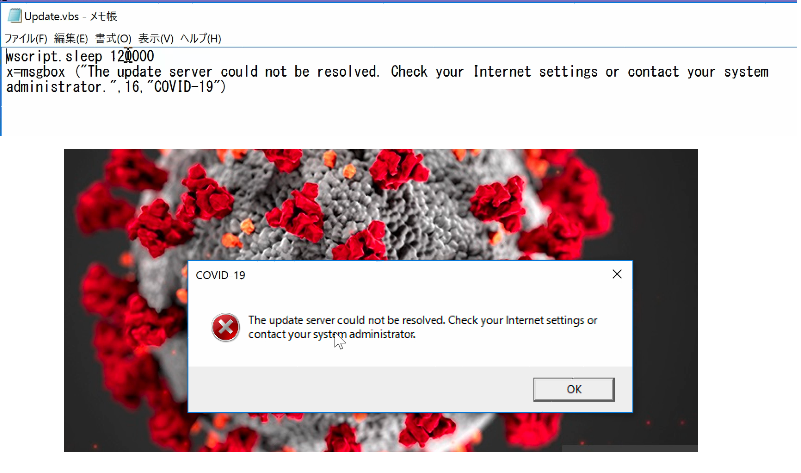
Screen pushing users to connect to the internet
More steps were likely added to get the user to connect to the internet, possibly because the victim needs to be online for the MBR to be overwritten. The MBR was not overwritten during manual rebooting when tested in a closed, offline environment.
Trend Micro Research also analyzed a coronavirus-themed malicious HTA file, possibly from the SideWinder APT group. Based on the command and control infrastructure and its connection to the Pakistani army, it is likely that SideWinder is using the coronavirus as a lure. SideWinder is an active group known for targeting military entities; their last notable activity was in January when we found evidence that they were behind malicious apps found on Google Play.
This HTA file contained a pop-up PDF lure displaying clickbait titles and images of the Pakistan army. It was connected with to these malicious URLs (blocked by Trend Micro):
- hxxp[://www.d01fa[.net/plugins/16364/11542/true/true/
- hxxp[://www.d01fa[.net/cgi/8ee4d36866/16364/11542/58a3a04b/file.hta
- hxxps[://cloud-apt[.net/202/6eX0Z6GW9pNVk25yO0x7DqKJzaNm6LIRaR0GCukX/16364/11542/2a441439

Screenshot of the lure
Malicious websites
Researchers reported two websites (antivirus-covid19[.]site and corona-antivirus[.]com) promoting an app that can supposedly protect users from COVID-19. The website antivirus-covid19[.]site, reported via the Malwarebytes’ blog, is now inaccessible. However, the website corona-antivirus[.]com, reported via the MalwareHunterTeam’s twitter account, is still active up to now.
The websites claim that their app, named “Corona Antivirus,” is a result of the work of scientists from Harvard University. Installing the app will infect the system with BlackNET RAT malware, which will then add the infected devices to a botnet. Through the botnet, threat actors can launch DDoS attacks, upload files to the device, execute scripts, take screenshots, harvest keystrokes, steal bitcoin wallets, and collect browser cookies and passwords.
The US Department of Justice (DOJ) filed a temporary restraining order against the fraudulent website, coronavirusmedicalkit[.]com. The website is supposedly selling COVID-19 vaccine kits approved by WHO. However, there are no WHO-approved legitimate COVID-19 vaccines available in the market yet.
The bogus website requests US$4.95 for shipping. Users were requested to enter their credit card information to proceed with the transaction. The websites have since been taken down.
There has been a notable increase in domain names using the word “corona” has also been observed by Bit Discovery. Trend Micro researchers confirmed the following domains as malicious:
- acccorona[.]com
- alphacoronavirusvaccine[.]com
- anticoronaproducts[.]com
- beatingcorona[.]com
- beatingcoronavirus[.]com
- bestcorona[.]com
- betacoronavirusvaccine[.]com
- buycoronavirusfacemasks[.]com
- byebyecoronavirus[.]com
- cdc-coronavirus[.]com
- combatcorona[.]com
- contra-coronavirus[.]com
- corona-armored[.]com
- corona-crisis[.]com
- corona-emergency[.]com
- corona-explained[.]com
- corona-iran[.]com
- corona-ratgeber[.]com
- coronadatabase[.]com
- coronadeathpool[.]com
- coronadetect[.]com
- coronadetection[.]com
A fake government website has been spotted luring users with the promise of aid or relief. The image below shows the domain uk-covid-19-relieve[.]com imitating legitimate "gov.uk" sites. It will ask for personal information and collect users’ bank account credentials if they enter a correct postcode.
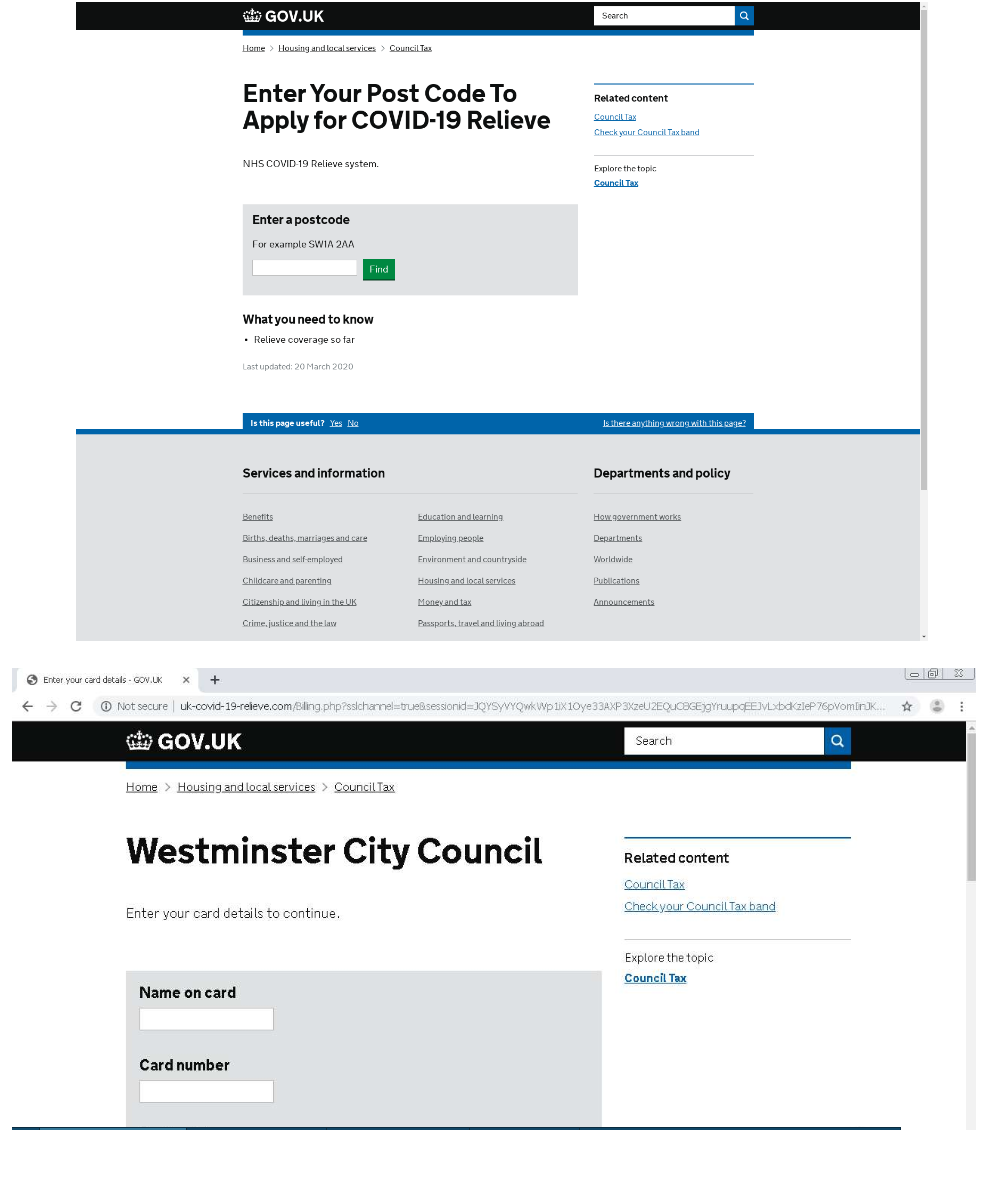
Fake UK government relief sites
Virus-related domains hosting malicious files are also still active. The site hxxps://corona-map-data[.]com/bin/regsrtjser346.exe loads the DanaBot banking trojan, which is capable of stealing credentials and hijacking infected systems.
Another recent example is hxxp://coronaviruscovid19-information[.]com/en. The site encourages you to download a mobile application called “Ways To Get Rid of Coronavirus,” promising a cure.
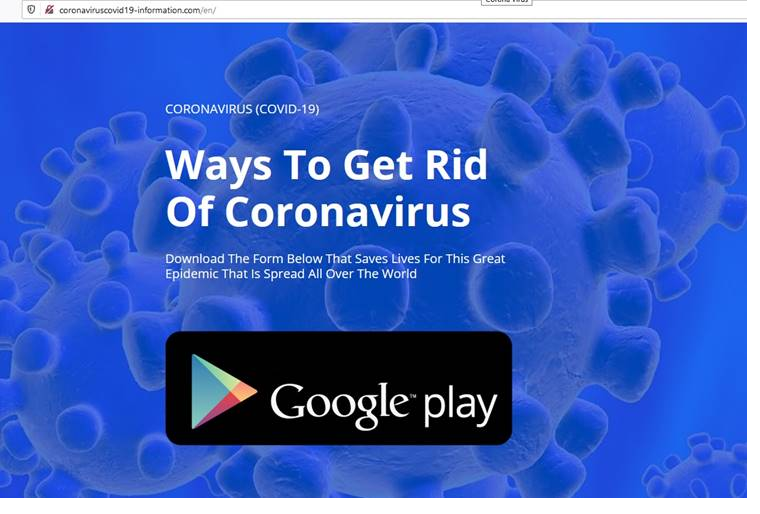
Website promoting fake app
Malicious actors are also aware that many users across the globe are quarantined and spending more time looking for entertainment online. They use fake streaming sites, or sites offering entertainment promotions to appeal to users. We spotted the domain hxxps://promo-covid19-neftlix[.]ml, which is actually a phishing site that steals Netflix account credentials. As always, users should always be mindful of websites they regularly use, and to keep credentials to online accounts as private as possible.
Another domain we noted was hxxps://paypaluk-coronavirussupport.com, a fake website that possibly targets UK PayPal users’ credentials. The site’s URL format is a red flag that it’s potentially malicious, with a hint that the domain does not legitimately belong to PayPal. Users should also check such sites by looking at the company’s official sites or social media for any evidence that they have new domains up and running.
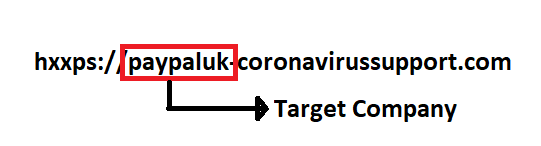
Based on the URL’s construction, the target company’s name is appended with a non-legitimate PayPal domain to make it appear more convincing. This is the same technique that was used for hxxps://promo-covid19-neftlix[.]ml.
In the beginnine of April, Trend Micro Research continued to find more phishing websites using the terms “coronavirus” or “COVID- 19” to trap users. Malicious actors are pretending to be legitimate organizations in an effort to collect valuable personal information. Here are a few examples of the different guises malicious sites take on to phish for data:
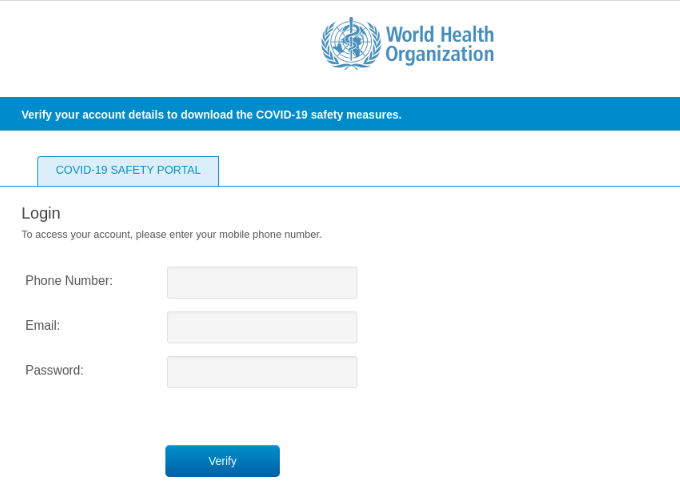
Fake COVID-19 safety portal from the World Health Organization (WHO)
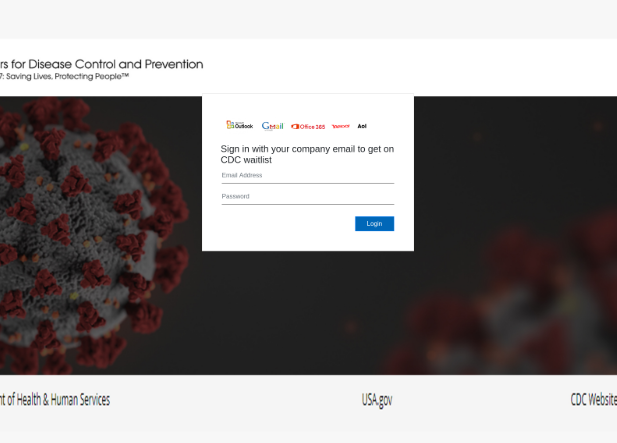
Fake Center for Disease and Prevention waitlist

Fake Canada/COVID-19 Emergency fund
The following have already been blocked and categorized as phishing sites.
- adaminpomes[.]com/em/COVID-19/index-2[.]php
- mersrekdocuments[.]ir/Covid/COVID-19/index[.]php
- bookdocument[.]ir/Covid-19/COVID-19/index[.]php
- laciewinking[.]com/Vivek/COVID-19/
- teetronics[.]club/vv/COVID-19/
- glofinance[.]com/continue-saved-app/COVID-19/index[.]php
- starilionpla[.]website/do
- ayyappantat[.]com/img/view/COVID-19/index[.]php
- mortgageks[.]com/covid-19/
- cdc[.]gov.coronavirus.secure.portal.dog-office.online/auth/auth/login2.html
Malicious actors are also using COVID-19 or coronavirus-related names in the titles of malicious files to try and trick users into opening them. One example is Eeskiri-COVID-19.chm (“eeskiri” is Estonian for rule), which is actually a keylogger disguised as a COVID-19 help site. If unpacked, it will gather a target’s credentials, set up the keylogger, and then send any gathered information to maildrive[.]icu.
A disguised file that unloads a keylogger onto a victim’s system
Malicious Social Media Messaging
Trend Micro Research investigated a scam and phishing tactic circulating online via Facebook Messenger. Below is a sample of the messages that use the promise of two months free premium Netflix subscription as a lure:
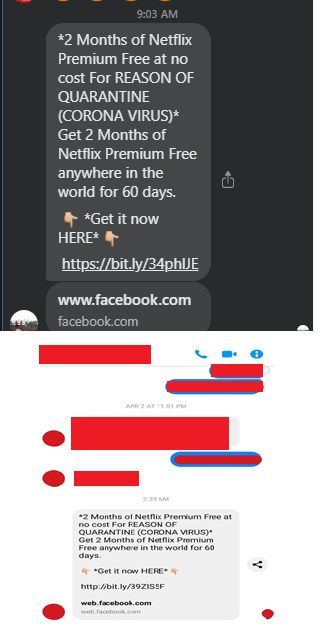
Captured images of SMS scam
The URL sent through Facebook Messenger is in the form of Short URL, hxxps://bit[.]ly/34phlJE which then redirects to two possible pages. The scenarios are detailed below:
First Scenario
If the user is already logged in to their Facebook account, it will simply continue and redirect to a fake Netflix page (seen below).
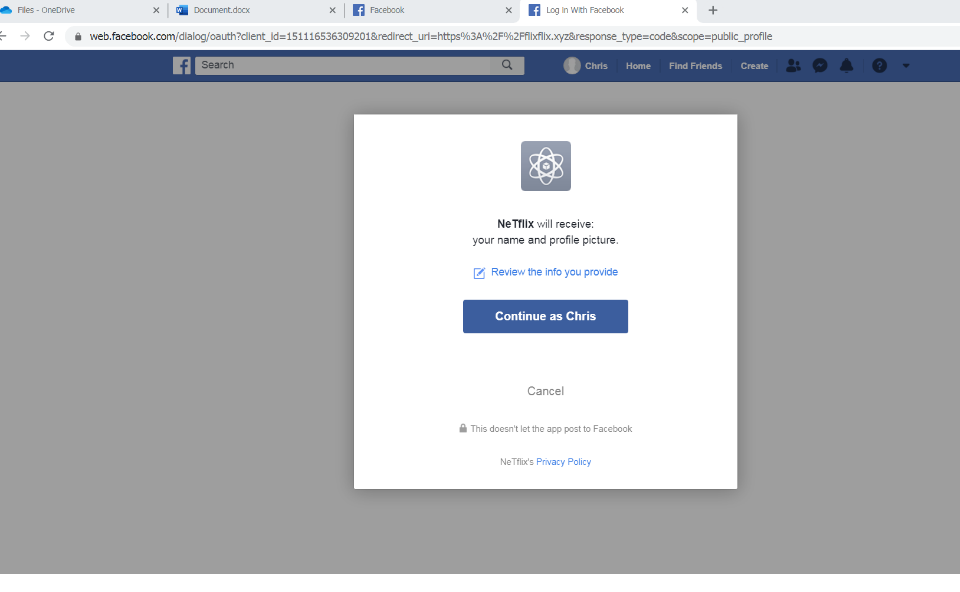
Fraudulent Netflix page
This page captures the victim’s Facebook login credentials and creates an active subscription to an app in Facebook named “NeTflix.” The app is simply an indicator that the user has already been compromised. If a user already subscribed to the fake app and clicks on the malicious link again, they will be redirected to a second page, detailed in the next section.
Subscribers who click on the link again will be redirected to this page
Second Scenario
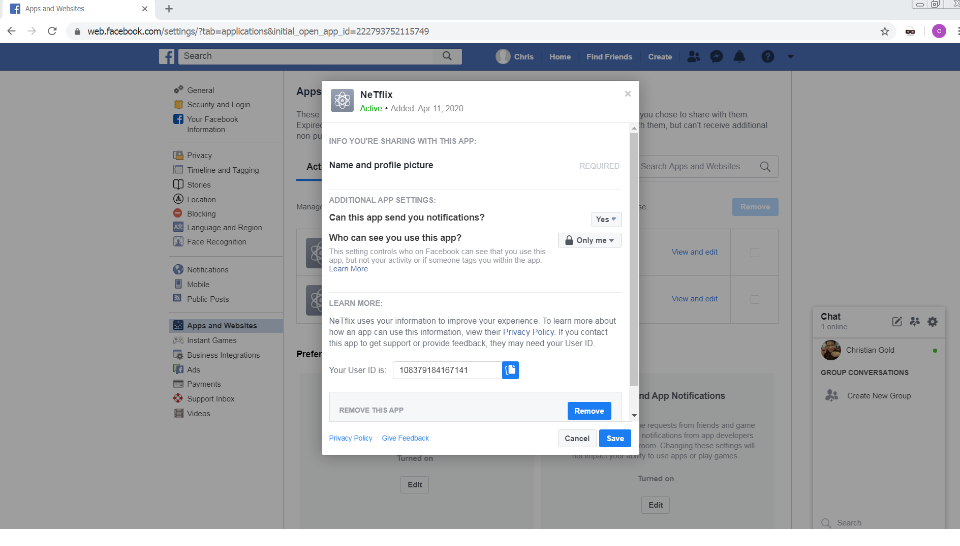
This is the second possibility for would-be victims. Users who have not logged in to their Facebook accounts will be redirected to the Facebook login page.
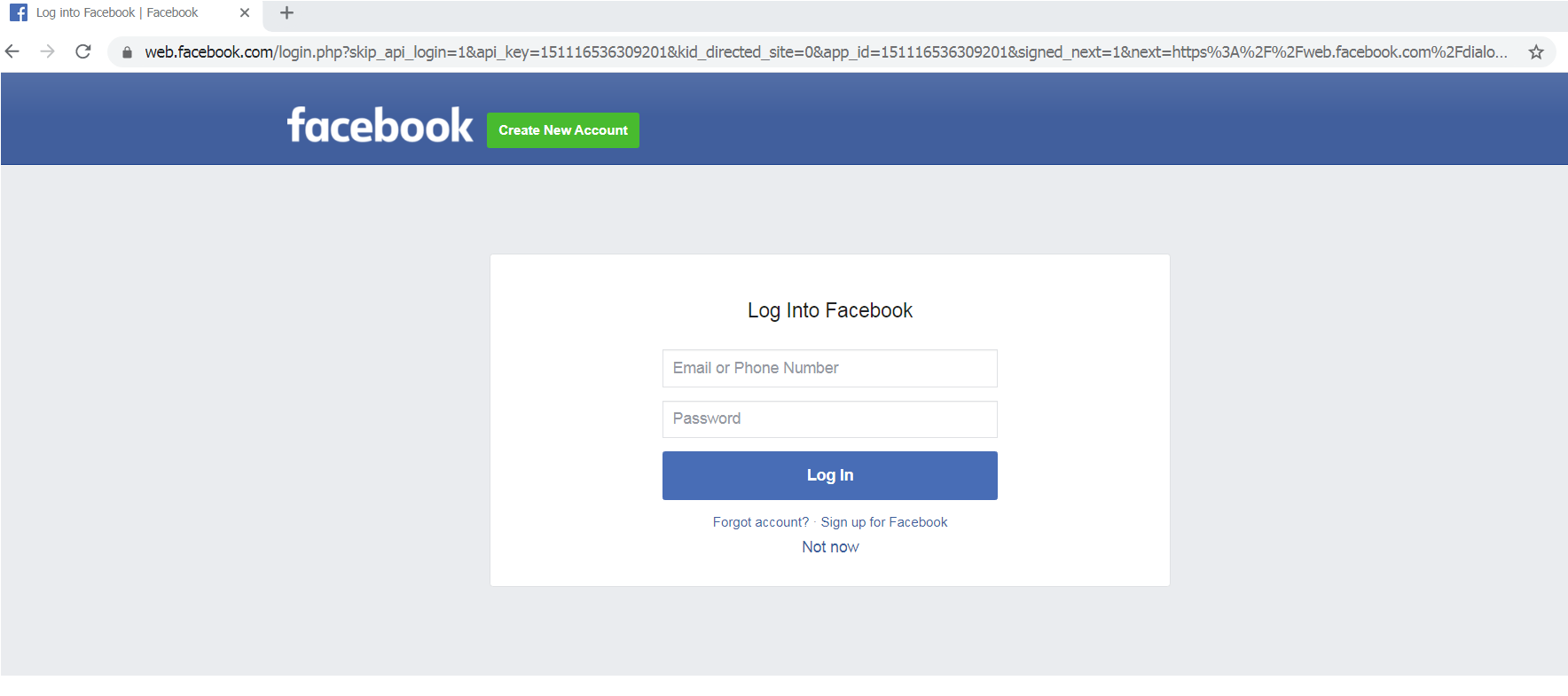
Redirects to Facebook login page
If the user enters their account credentials, it will redirect to the fraud page seen in the first scenario. If the user clicks the “Not now” button, it will redirect to the fake Netflix page, as seen below. The page contains a fake Netflix offer and a survey on the right side with questions about COVID-19 and cleanliness habits. The scammers used free, newly created domains unrelated to Netflix.
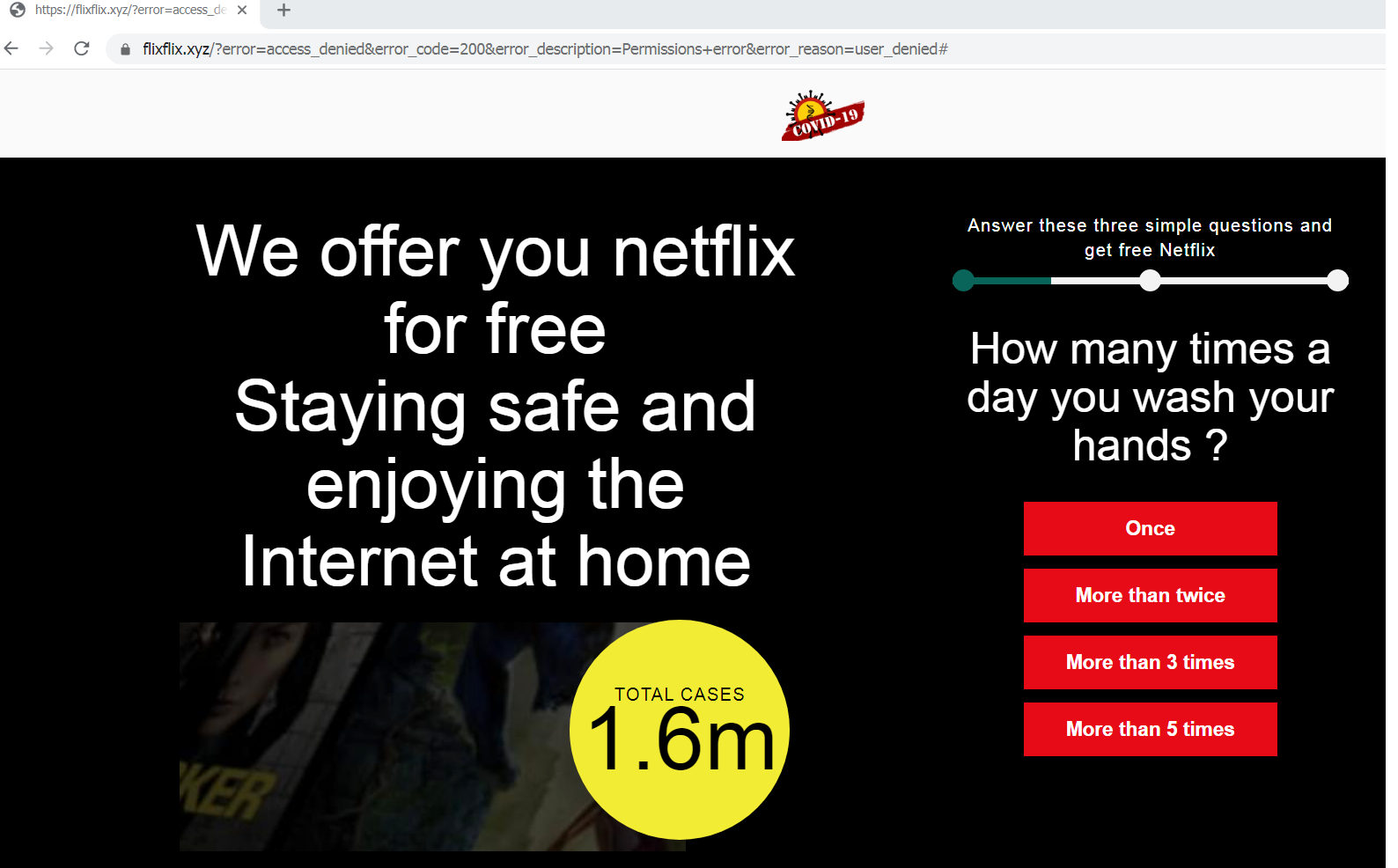
Fake Netflix offer
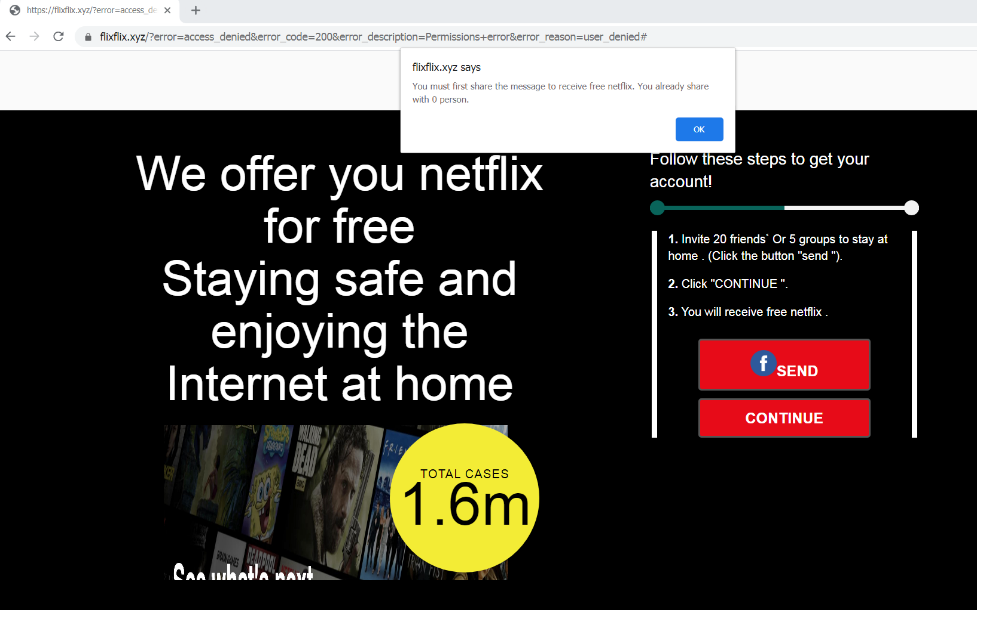
The victim is urged to spread the offer
At the end of the survey, it will ask the user to share or invite twenty friends or five groups to complete the survey before the user can continue and receive their fake free Netflix subscription (Figure 6). The survey has random questions and accepts any answer that the user types. It is an additional tactic to make the user continue to the next step.
Regardless if users click the ‘Send’ or ‘Continue’ button at the end of the survey, it will redirect users to the same page — a Facebook share prompt. In this next step, users are urged again to spread malicious links by clicking a “Share” button for Facebook contacts. Then the user will be prompted to log in to Facebook.
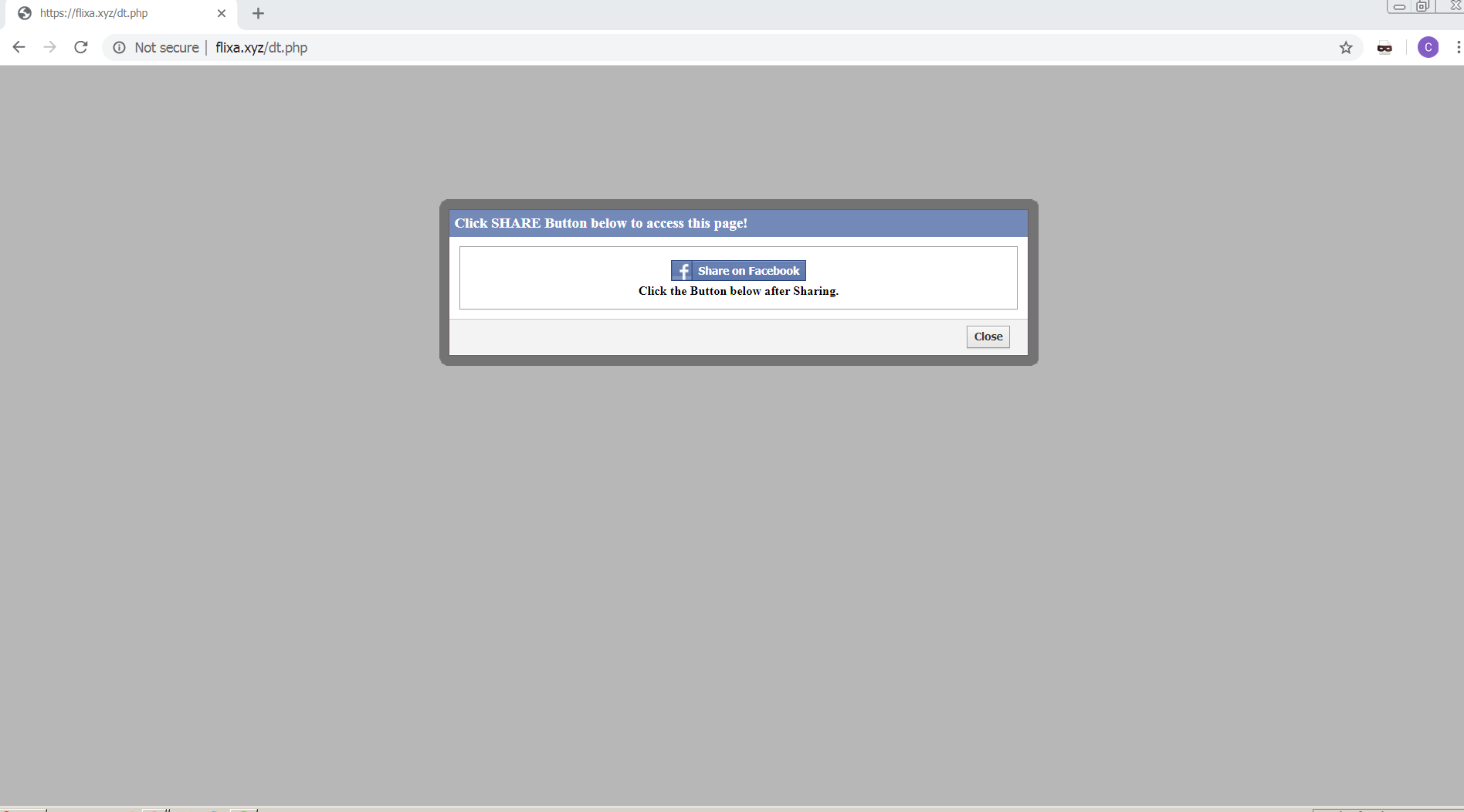
Users are asked to log in to Facebook
Users that enter their Facebook login credentials will be taken to an automatically generated post. Clicking on the “Post” button will post a status about the malicious link on the user’s Facebook page.
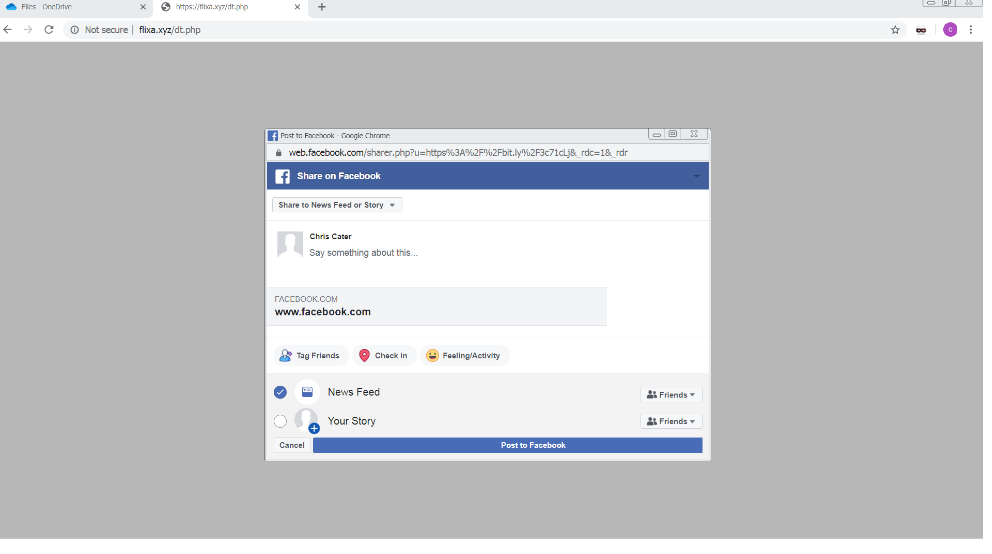
Users will be asked to post a link on their Facebook page
These two scenarios show that whether the user is already logged in or refuses to give their credentials, they will be pressured into sharing fraudulent links. The following URLs were identified as malicious and are already blocked by Trend Micro:
- hxxp://bit[.]ly/3ec3SsW -- flixx.xyz
- hxxp://bit[.]ly/2x0fzlU -- smoothdrive.xyz
- hxxp://bit[.]ly/39ZIS5F -- flixa.xyz
- Do not click on links or shared files from an unknown sender.
- Check if the information being shared comes from a legitimate source.
- Check the URLs of websites that ask for your information.
- Do not give personal information or credentials to unverified sites.
With people around the world staying and working from home, most users are vulnerable to simple attacks like the one detailed above. Social media plays a critical role in keeping users updated on the latest information, but at the same time can be used for cyberattacks. Everyone should try to stay safe not only from the pandemic but also from digital threats.
Malware
An interactive COVID-19 map was used to spread information-stealing malware, as revealed by Brian Krebs. The map, which was created by Johns Hopkins University, is an interactive dashboard showing infections and deaths. Several members of Russian underground forums took advantage of this and sold a digital COVID-19 infection kit that deploys Java-based malware. Victims are lured to open the map and even share it.
Also, Trend Micro Research analyzed a coronavirus-themed Winlocker that can lock users out of affected machines. When executed, the malware drops files and modifies system registries. It then displays a message, plays sinister sounds through Windows, and requires a password to unlock the machine. Based on this video sample, the ransomware variant seems to be a modified and repurposed malware from 2019. At the time of writing, this malware has not been seen in the wild.
Upon execution, the malware drops a number of files; and also creates a copy of the following files:
- C:\wh\speakh.vbs
- C:\wh\antiwh.vbs
- C:\wh\diex.bat
- C:\awh\anti-exe
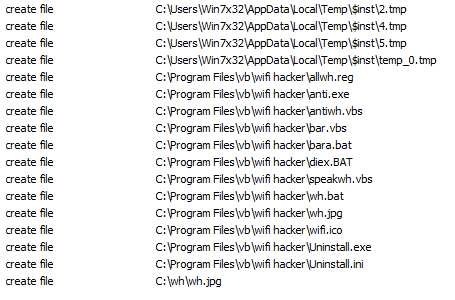
List of dropped files
It also modifies registry entries. The modified registry entries create autorun entries for the following components:
- C:\wh\speakh.vbs
- C:\wh\antiwh.vbs
- C:\wh\diex.bat
It then disables Explorer policies for certain essential functions, making the affected Windows system almost impossible to navigate. It modifies the legal notice caption, and the user sees the image below.
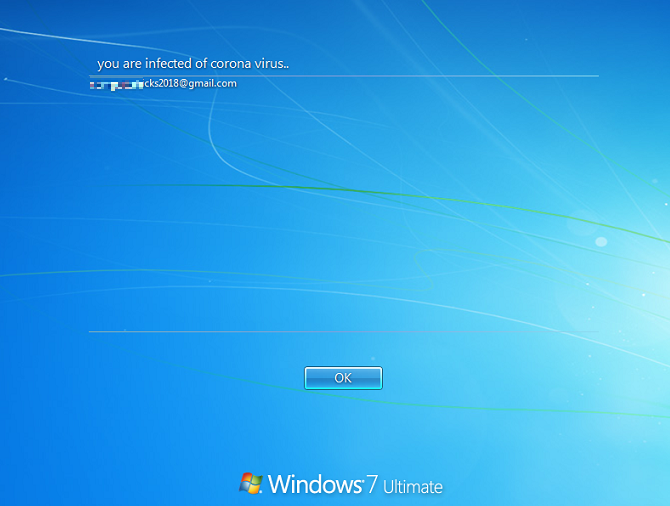
Modified notice
After the welcome message, the affected machine’s wallpaper is replaced with a “coronavirus” image. The screen also displays a box that informs the user that the machine has been locked, and file recovery needs a decryption code.
This screen is from the dropped file antiwh.vbs, which is executed every time the system starts. Based on the analyzed malware script, the correct code needed to load explorer.exe is “vb”.
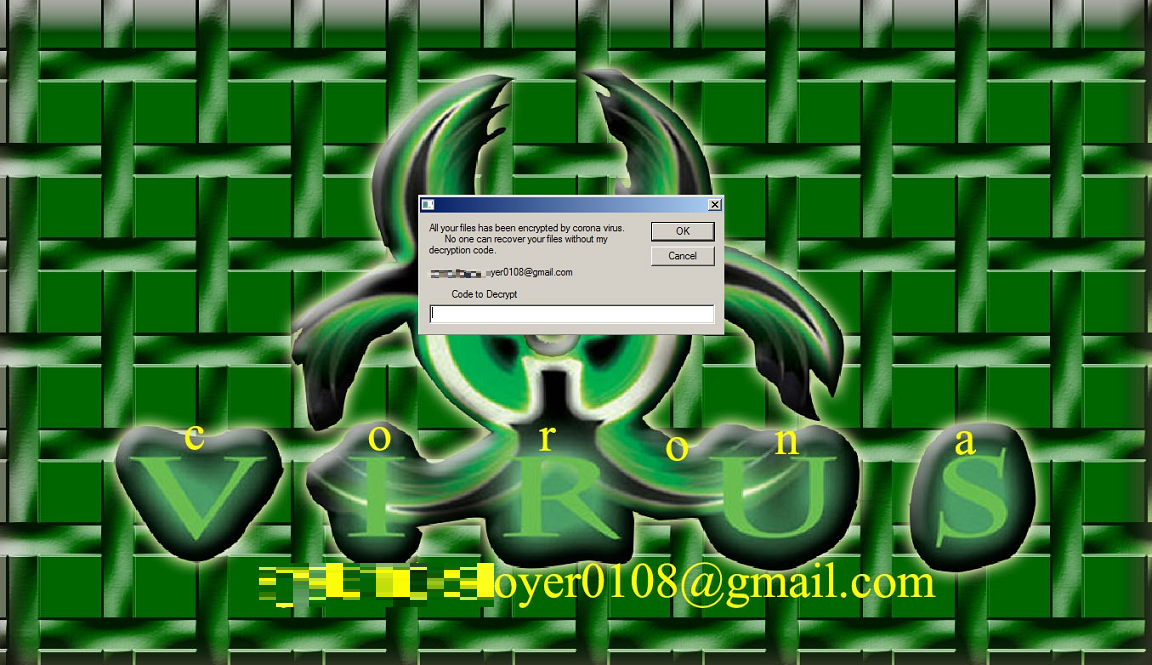
Lockscreen image
Another script (C:\wh\antiwh.vbs) is executed at every startup to make use of the Windows speech feature to say “coronavirus” in a loop.
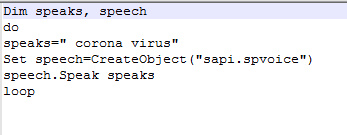
Windows speech feature used to loop “Coronavirus”
The file, C:\wh\diex.bat, terminates explorer.exe upon startup. Additional analysis of the other dropped binary file (“C:\awh\anti-exe”) shows that it is a password-protected unlocker for this malware. Upon execution, it asks for a password. We tried the same password “vb” from the previous script.
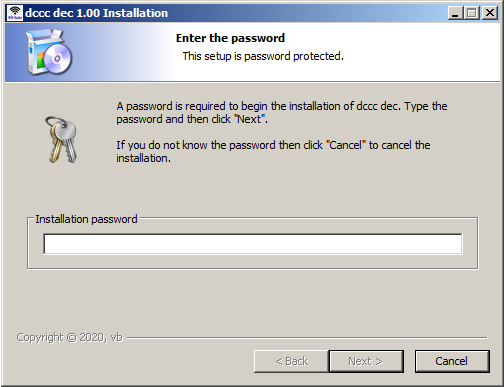
The password-protected unlocker installer
After successful installation, the unlocker drops the following files:
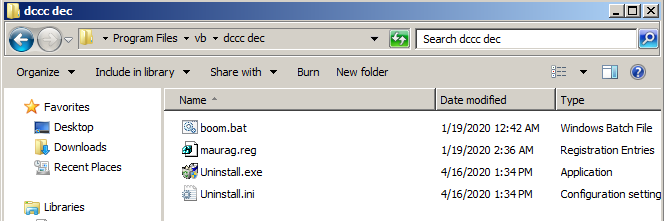
Files installed by the unlocker
Based on the content of maurag.reg, it restores the registry entries to make the system usable again. The file “boom.bat” deletes the dropped files in c:\wh\ and displays the following message:
Malware note
BEC
A Business Email Compromise (BEC) attack mentioning COVID-19 was reported by Agari Cyber Intelligence Division (ACID). The attack, a continuation of an earlier BEC campaign, came from Ancient Tortoise, a cybercrime group behind multiple BEC cases in the past.
The threat actors first target accounts receivables into forwarding aging reports (accounts receivable reports). Then, while posing as legitimate companies, they use customer information in these reports to send emails to inform customers of a change in banks and payment methods due to COVID-19.
Ransomware
A new ransomware variant called CoronaVirus was spread through a fake Wise Cleaner site, a website that supposedly promoted system optimization, as reported by MalwareHunterTeam. Victims unknowingly download the file WSGSetup.exe from the fake site. The said file acts as a downloader for two types of malware: The CoronaVirus ransomware and password-stealing trojan named Kpot. This campaign follows the trend of recent ransomware attacks that go beyond encrypting data and steal information as well.
Another attack that is presumed to be caused by ransomware has hit a University Hospital Brno in the Czech Republic, a COVID-19 testing center. The hospital’s computer systems had been shut down due to the attack, delaying the release of COVID-19 test results.
Threat actors also launched a new phishing campaign that spreads the Netwalker ransomware, according to MalwareHunterTeam from reports on Bleeping Computer. The campaign uses an attachment named “CORONAVIRUS.COVID-19.vbs” that contains an embedded Netwalker ransomware executable.
Upon execution of the script, the EXE file will be saved to %Temp%\qeSw.exe. Launching this file will lead to the encryption of other files on the computer. Victims will then find a ransom note with instructions on how to pay the ransom via a Tor payment site.
Mobile Threats
A mobile ransomware named CovidLock comes from a malicious Android app that supposedly helps track cases of COVID-19. The ransomware locks the phones of victims, who are given 48 hours to pay US$100 in bitcoin to regain access to their phone. Threats include the deletion of data stored in the phone and the leak of social media account details. A look at their cryptocurrency wallet shows that some victims have already paid the ransom on March 20. The final balance at the time of writing is 0.00018096 BTC.
There are also reports of malicious Android apps offering safety masks to targets worried about COVID-19. Unfortunately the malicious app actually delivers an SMSTrojan that collects the victim's contact list and sends SMS messages to spread itself. So far, the app seems to be in the early stages of development and is simply trying to compromise as many users as possible.
Browser Apps
A new cyberattack has been found propagating a fake COVID-19 information app that is allegedly from the World Health Organization (WHO). Bleeping Computer reports that the campaign involves hacking routers’ Domain Name System (DNS) settings in D-Link or Linksys routers to prompt web browsers to display alerts from the said apps.
Users reported that their web browsers automatically open without prompting, only to display a message requesting them to click on a button to download a “COVID-19 Inform App.” Clicking on the button will download and install the Oski info stealer on the device. This malware variant can steal browser cookies, browser history, browser payment information, saved login credentials, cryptocurrency wallets, and more.
Sextortion Scam
A sextortion scheme reported by Sophos demands US$4,000 in bitcoin, or else, they threaten to infect the victim’s family with COVID-19. The victims receive emails informing them that the threat actors know all their passwords, their whereabouts, and other details relating to their personal activities. The email senders threaten to release the data if the victim doesn’t make the payment in 24 hours. There is no indication that the threat actors actually have access to the data, or if they can actually follow through with their threats.
Trend Micro Research detected an extortion scam similar to the type security firm Sophos found on March 19. It seems that cybercriminals have now begun threatening targets with exposure to COVID-19 if their demands are not met.
The image below shows the scammer using scare tactics in an attempt to manipulate the user. The hackers claim that they have somehow infiltrated the user's system and can send email from the user's own account. In reality, the spam email is drafted so that the "From," or sender, is the same as the recipient of the email, so if the target replies they get the same email again. This adds to the fear that the hacker has somehow broken into their system and has personal information about their whereabouts. The hacker then demands US$500 or he will expose the target to the virus.
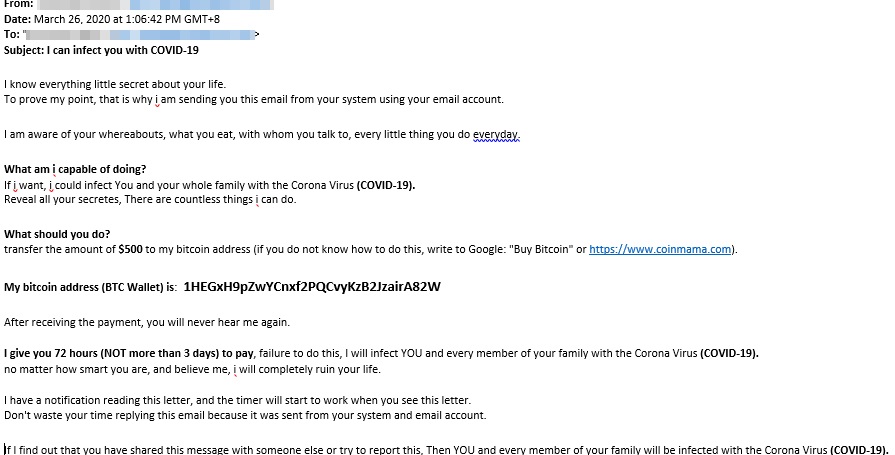
COVID-19 being used for extortion
COVID-19 in the Underground
Underground forums and cybercriminal marketplaces operate in the same way legitimate selling spaces operate: Suppliers pay attention to world news and markets, and make money by catering to market demand.
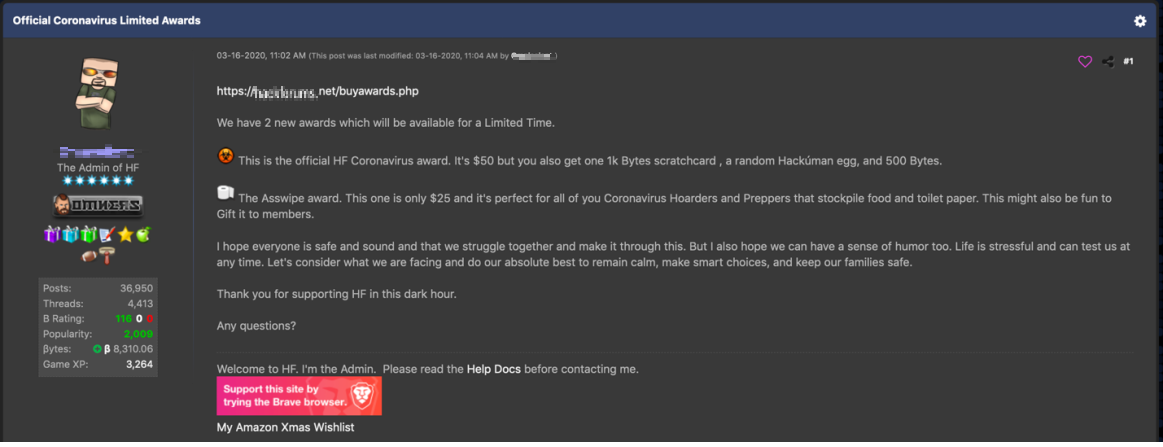
A popular underground forum created limited coronavirus awards where people can purchase a toilet paper or “coronavirus” icon to add to the user’s profile
We usually see themed malware after natural disasters or major world events, and it’s no different for the current coronavirus (COVID-19) pandemic. We’re seeing multiple listings for phishing, exploits, and malware linked to the virus in underground forums. One user (pictured below) is asking for US$200 for a private build of a coronavirus-themed phishing exploit and an additional US$700 for a Code Sign certificate.
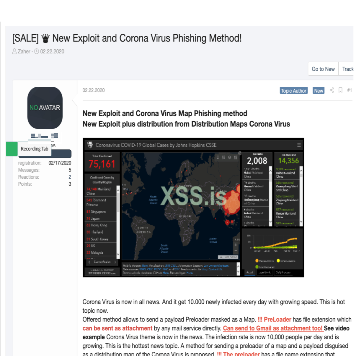
Coronavirus-themed phishing exploit sold on a Russian underground forum
The pandemic has changed consumer habits rapidly. People in multiple countries are struggling to find essential supplies, and toilet paper and face masks are in high demand. Trend Micro Research found that numerous underground forums are now selling items such as N95 masks, toilet paper, ventilators, thermometers, and patient monitors. We have seen posts offering N95 masks for US$5 each and toilet paper rolls for US$10. As stocks plunge, underground forum users have also been discussing if now is a good time to invest in bitcoins. The value of bitcoins have dropped from US$8914 (February 27) to US$6620 (March 27) in a month.
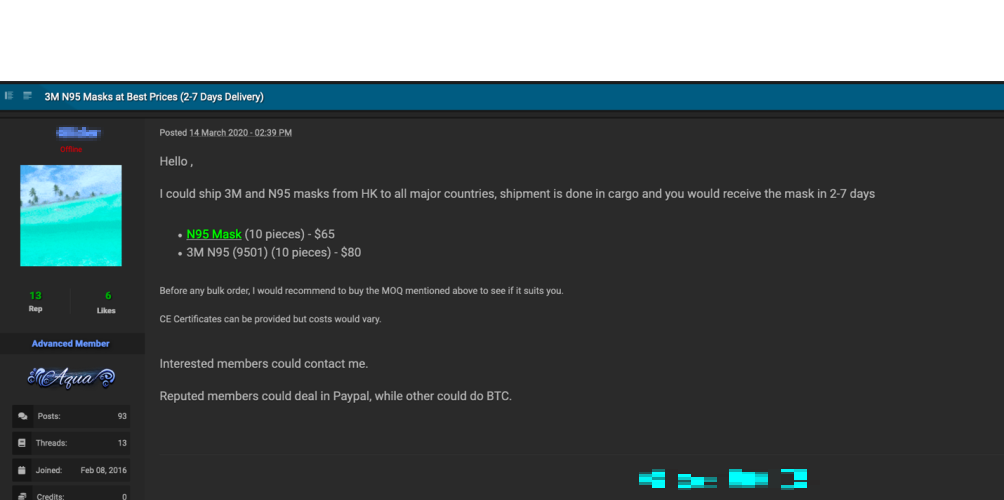
Underground seller offering 3M N95 masks
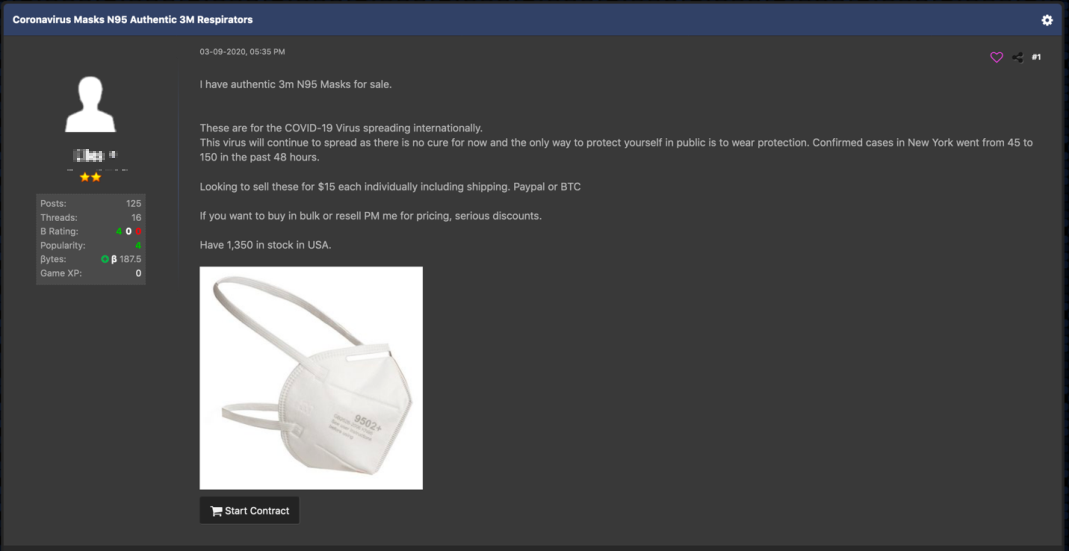
Forum post offering N95 masks
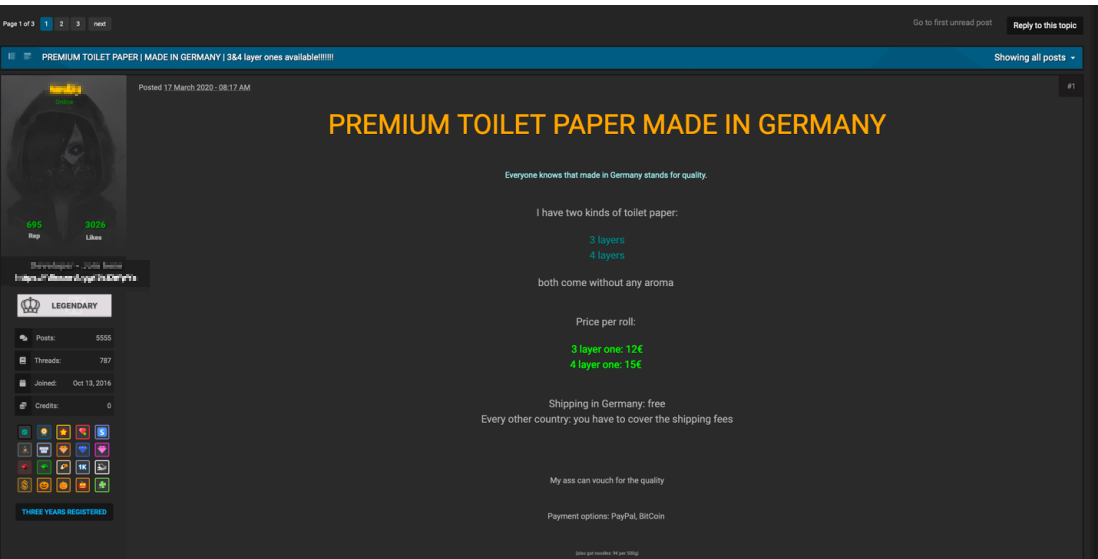
Forum post offering toilet paper rolls
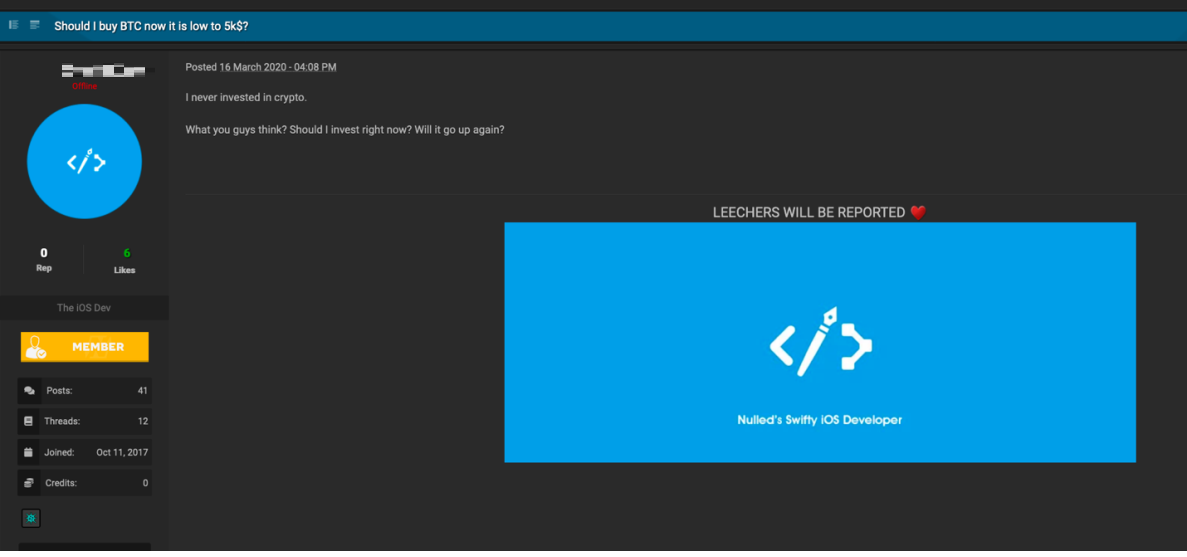
Thread on whether this is a good time to invest in cryptocurrency
Some sellers are using “coronavirus” as a keyword in the title or body of their advertisements to increase sales. They are offering virus-themed sales or even looking for partners for joint ventures. We even found some users discussing how to use the virus to their advantage for social engineering scams. For example, to get around verification requests for large transactions, the user would mention that the money being transferred was for a family member affected by the virus or that a lockdown prevented them from completing the transaction in person.
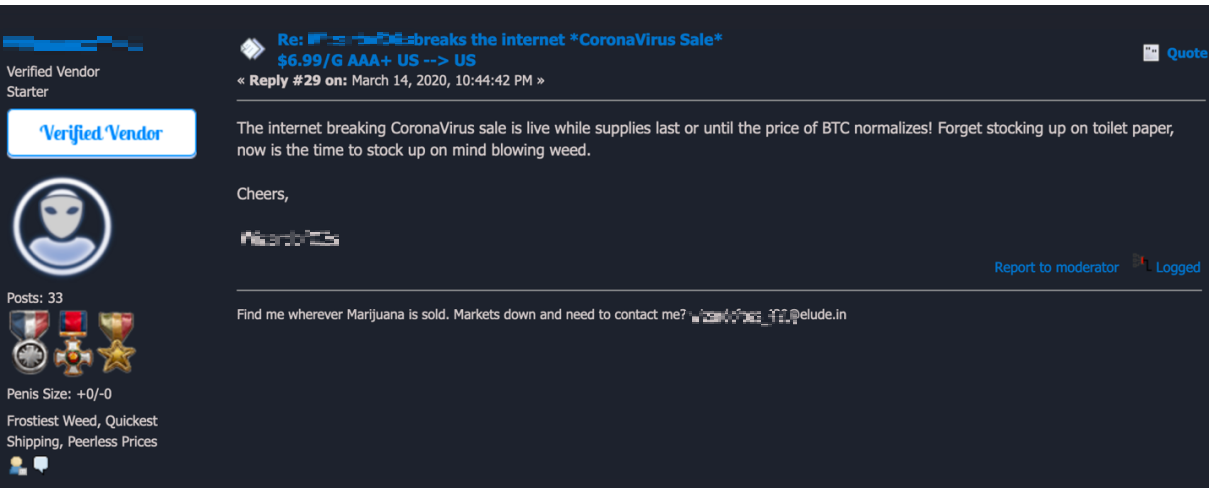
Darkweb marketplace offering a “coronavirus sale” on marijuana
Seller looking for a joint venture related to Coronavirus
In many countries, people have been asked to stay home, businesses have closed, and unemployment has increased. Like everyone else, underground sellers have seen their revenues drop since fewer people are spending money. Sellers on forums are complaining that exit scams have increased too. Underground businesses depending on money mules and dropshipping have also been affected as the “mules” are unavailable or afraid of catching the virus. A search on multiple forums returned many threads of people discussing how to prevent getting COVID-19, how to make hand sanitizer, how forum users are coping with city lockdowns, as well as general concerns about the virus.
Scope of COVID-19 Threats
Data from our Smart Protection Network indicates that there are millions of threats across email, URL, and file. The data below represents information collected in the third quarter of 2020.

Map of threats using COVID-19
Malicious URLs span the range of phishing-related sites, scams, and domains that dump malware (adware, ransomware to name a few). In the chart below we list the top ten countries where users have inadvertently accessed malicious URLs with covid, covid-19, coronavirus, or ncov in its strings. Our midyear roundup shows that the number of times users tried to access malicious Covid-19-related URLs peaked in April, while May and June saw sustained activity. However, in Q3 we see that activity is rising again, notably in August and September.
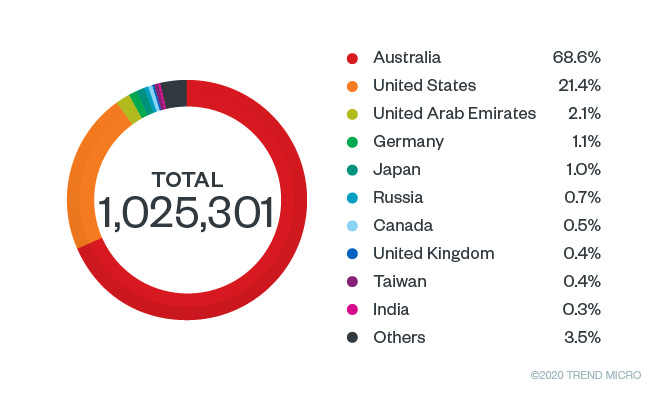
Top countries with users accessing malicious COVID-related URLs in Q3 of 2020
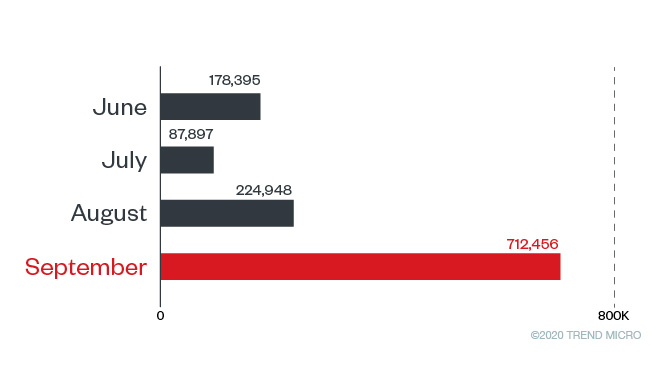
Instances that malicious COVID-19 related URLs were accessed
A large portion of these threats are related to spam email, as indicated by our threat samples detailed above. As we noted in our midyear roundup, email threats made up 91.5% of all Covid-19 related threats in the first half of 2020 and was the most commonly used entry point for malicious actors. In the third quarter of the year, users should still be on guard since malicious activity is continuing at a relatively high rate.
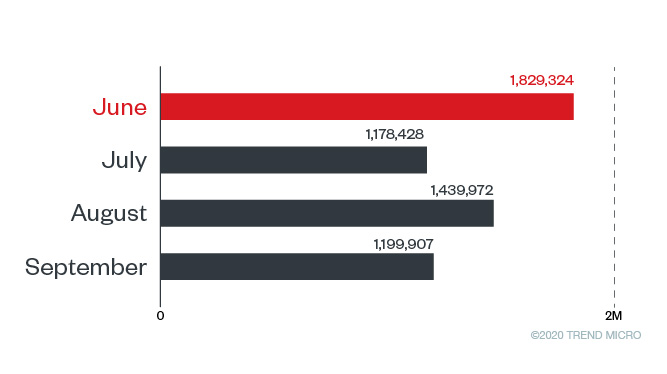
Spam email detections June to September 2020
Our team has also been tracking malicious files that use covid, covid-19, coronavirus, or ncov in the filename. As of this writing, these files belong to various malware families. Most are Trojans, and a handful are ransomware-related files. Our researchers also saw Covid-19 themed tools and malware variants being sold on forums catering to malicious online activities. This may be one of the factors that contributed to the malware activity seen in Q3. There was a steep increase in malware files detections, with a surprisingly high number seen in September.
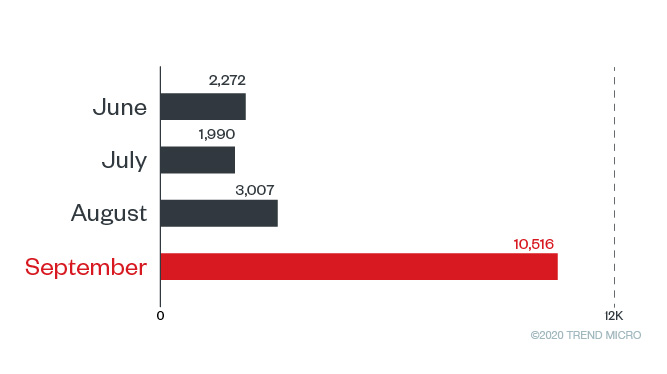
Monthly detctions for malware related to COVID-19
*Note: The detection numbers are based on the coverage of our Smart Protection Network, which has limited global distribution. It was previously stated that the data represents countries hosting these malicious URLs. The correct statement is that this data represents countries where users have accessed malicious URLs.
Defense Against these Threats
Trend Micro endpoint solutions such as the Smart Protection Suites and Worry-Free™? Business Security detect and block the malware and the malicious domains it connects to.
As an added layer of defense, Trend Micro™ Email Security thwarts spam and other email attacks. The protection it provides is constantly updated, ensuring that the system is safeguarded from both old and new attacks involving spam, BEC, and ransomware. Trend Micro's Cloud App Security finds unknown malware using machine learning. The document exploit detection engine uncovers threats hidden in office files while artifical intelligence checks email behaviour, intention, and authorship to identify BEC attacks.
A multilayered protection is also recommended for protecting all fronts and preventing users from accessing malicious domains that could deliver malware.
Indicators of Compromise for Malware Files
Trend Micro researchers were also able to detect malware with “corona virus” in their filename, listed below:
| File Name | SHA 256 | Trend Micro Pattern Detection | Trend Micro Predictive Machine Learning Detection |
| CORONA VIRUS AFFECTED CREW AND VESSEL.xlsm | ab533d6ca0c2be8860a0f7fbfc7820ffd 595edc63e540ff4c5991808da6a257d | Trojan.X97M.CVE201711882.THCOCBO | N/A |
| CORONA VIRUS AFFECTED CREW AND VESSEL.xlsm | 17161e0ab3907f637c2202a384de67fca 49171c79b1b24db7c78a4680637e3d5 | Trojan.X97M.CVE201711882.THCOCBO | Downloader.VBA.TRX.XXVBAF01FF006 |
| CORONA VIRUS AFFECTED CREW AND VESSEL.xlsm | 315e297ac510f3f2a60176f9c12fcf9 2681bbad758135767ba805cdea830b9ee | Trojan.X97M.CVE201711882.THCOCBO | Downloader.VBA.TRX.XXVBAF01FF006 |
| CoronaVirusSafetyMeasures_pdf.exe | c9c0180eba2a712f1aba1303b90cbf12c11 17451ce13b68715931abc437b10cd | TrojanSpy.Win32.FAREIT.UHBAZCLIZ | Troj.Win32.TRX.XXPE50FFF034 |
| CoronaVirusSafetyMeasures_xls.exe | 29367502e16bf1e2b788705014d0142 d8bcb7fcc6a47d56fb82d7e333454e923 | TrojanSpy.Win32.FAREIT.SMTHC.hp | N/A |
| LIST OF CORONA VIRUS VICTIM.exe | 3f40d4a0d0fe1eea58fa1c71308431b5c2c e6e381cacc7291e501f4eed57bfd2 | Trojan.MSIL.AGENTTESLA.THCOCBO | N/A |
| POEA HEALTH ADVISORY re-2020 Novel Corona Virus.pdf.exe | 3e6166a6961bc7c23d316ea9bca87d82 87a4044865c3e73064054e805ef5ca1a | Backdoor.Win32.REMCOS.USMANEAGFG | Troj.Win32.TRX.XXPE50FFF034 |
| POEA Advisories re-2020 Novel Corona Virus.2.pdf.exe | b78a3d21325d3db7470fbf1a6d254e23d34 9531fca4d7f458b33ca93c91e61cd | Backdoor.Win32.REMCOS.USMANEAGFE | Troj.Win32.TRX.XXPE50FFF034 |
Other researchers are seeing cybercriminals take advantage of coronovirus maps and dashboards. Researchers from Reason Labs have found fake websites that lead the download and installation of malware. The downloaded malware are detected by Trend Micro as the following:
| SHA 256 | Trend Micro Pattern Detection | Trend Micro Predictive Machine Learning Detection |
| 2b35aa9c70ef66197abfb9bc409952897f 9f70818633ab43da85b3825b256307 | TrojanSpy.Win32.AZORULT.UJL | Troj.Win32.TRX.XXPE50FFF034 |
| 0b3e7faa3ad28853bb2b2ef188b310a676 63a96544076cd71c32ac088f9af74d | TrojanSpy.Win32.CLIPBANKER.BK | Troj.Win32.TRX.XXPE50FFF034 |
| 13c0165703482dd521e1c1185838a6a12e d5e980e7951a130444cf2feed1102e | Trojan.Win32.CRYPTINJECT.SMB | Troj.Win32.TRX.XXPE50FFF034 |
| fda64c0ac9be3d10c28035d12ac0f63d85 bb0733e78fe634a51474c83d0a0df8 | TrojanSpy.Win32.CLIPBANKER.SMMR | Troj.Win32.TRX.XXPE50FFF034 |
| 126569286f8a4caeeaba372c0bdba93a9b0 639beaad9c250b8223f8ecc1e8040 | Trojan.Win32.CRYPTINJECT.SMB | Troj.Win32.TRX.XXPE50FFF034 |
Indicators of Compromise for HawkEye Reborn spam
| SHA-256 | Trend Micro Pattern Detection |
| 0b9e5849d3ad904d0a8532a886bd3630c4eec3a6faf0cc68658f5ee4a5e803be | Trojan.W97M.POWLOAD.THBBHBO |
Indicators of Compromise for spam targeting Italy
| SHA-256 | Trend Micro Pattern Detection |
| 6cc5e1e72411c4f4b2033ddafe61fdb567cb0e17ba7a3247acd60cbd4bc57bfb | Trojan.X97M.POWLOAD.THCAOBO |
| 7c12951672fb903f520136d191f3537bc74f832c5fc573909df4c7fa85c15105 | Trojan.PS1.POWLOAD.JKP |
Indicators of Compromise of spam targeting Italy (March 20)
| SHA-256 | Trend Micro Pattern Detection |
| dd6cf8e8a31f67101f974151333be2f0d674e170edd624ef9b850e3ee8698fa2 | Trojan.W97M.JASCREX.BSUB |
Indicators of Compromise for Netwalker ransomware campaign
| Attachment Filename | SHA-256 | Trend Micro Pattern Detection |
| CORONAVIRUS.COVID-19.vbs | 9f9027b5db5c408ee43ef2a7c7dd1aecbdb244ef6b16d9aafb599e8c40368967 | Ransom.VBS.MAILTO.AA |
Indicators of Compromise for DanaBot banking trojan
| Attachment Filename | SHA-256 | Trend Micro Pattern Detection |
| regsrtjser346.exe | 44c7ef261a066790a4ce332afc634fb5f89f3273c0c908ec02ab666088b27757 | TrojanSpy.Win32.DANABOT.LR |
Indicators of Compromise for keylogger files
| Attachment Filename | SHA-256 | Trend Micro Pattern Detection |
| Eeskiri-COVID-19.chm | 6117a9636e2983fb087c9c9eec2a3d2fbadb344a931e804b2c459a42db6d2a68 | Trojan.HTML.INFOSTEALER.THDOABO |
| ~tmp6.cab | e02aedeea6c8dc50a5ff95d37210690daeeef172b2245e12fcf0913a492fd0ac | Trojan.HTML.INFOSTEALER.THDOABO |
Indicators of Compromise for Winlocker
| Attachment Filename | SHA-256 | Trend Micro Pattern Detection |
| diex.BAT | 827cca9b9c4489495429a3ff0b204dcf46812d10 | Ransom.Win32.CORONAWINLOCKER.A |
| Uninstall.ini | 013e89d9bc9a402fbb929c92446d7cb3069f4820 | Ransom.Win32.CORONAWINLOCKER.A |
| bar.vbs | b797c987a004d6ddd72c126b8ee3f695a6179891 | Ransom.Win32.CORONAWINLOCKER.A |
| wh.bat | 796acc76dfdaf7b532c32481d814c6d935827439 | Ransom.Win32.CORONAWINLOCKER.A |
| anti.exe/antiwh.vbs | 0add3747bd143687865b26a0abca99a2f44b0585 | PUA.Win32.CORONAWINLOCKER.A |
| speakwh.vbs | cb3d4522f1185adc587fabfa3f6feabf1d33ed1a | Ransom.Win32.CORONAWINLOCKER.A |
| allwh.reg | 525caebb2ab47893c9241e0193ee6dcd92659729 | Ransom.Win32.CORONAWINLOCKER.A |
| bara.bat | dcd3297d494b338eb71f7d4d5691290f474d2e18 | Ransom.Win32.CORONAWINLOCKER.A |
| antiwh.vbs | 50968a42da31fed47fc67914b8948500d93e468b | Ransom.Win32.CORONAWINLOCKER.A |
| 39a58879b0327145f5eb94caa83227564b11abde | Ransom.Win32.ONALOCKER.A |
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One