The Dire Implications of DYREZA
Publish Date: 2014年10月29日
DYREZA is an online banking malware that is advertised as a spinoff of the infamous ZeuS banking malware. First spotted around September 2014, it caught the security industry’s attention due to its ability to bypass SSL, a popular security measure for online banking websites.
How does DYRE arrive into users’ systems?
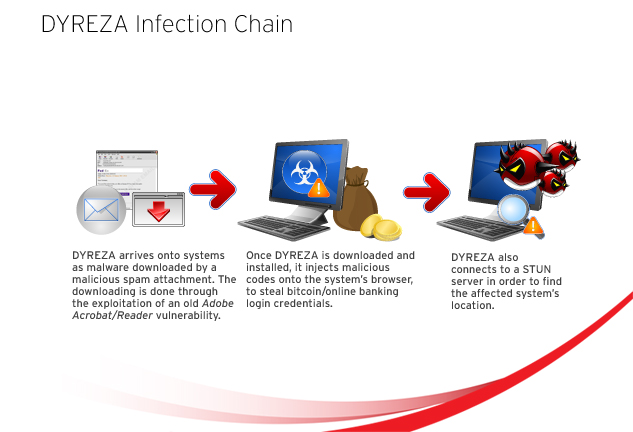
DYREZA variants arrive into users’ systems mainly through spammed mails with malicious attachments. The spammed mail itself is almost always tailored to look like an invoice notification or similar to a notification involving banks/financial institutions, while the attachment is invariably a PDF file.
Should users be taken in by this particular socially-engineered threat and open the attached malicious PDF file, then the involved DYRE variant is downloaded onto their system and then executed.
What happens when users execute this threat on their systems?
DYREZA variants are capable of the following routines once installed and executed on an affected system:
- Perform man-in-the-middle attacks via browser injections
- Monitor/take screenshots of browser activity
- Steal personal security certificates
- Steal online banking/login credentials
- Track the affected user’s location through STUN (Session Traversal Utilities for NAT).
In summary, the security of the affected system itself is compromised to such a degree that it can be viewed as a very serious privacy risk to the user, along with the compromise of any online account (banking or otherwise) accessed with the aforementioned system.
How does this threat affect users?
DYREZA affects users by stealing their personal information (online account credentials) through its many personal information theft/browser monitoring routines. It can also violate their privacy, as the login credentials stolen may also lead to the user’s social networking accounts being broken into and/or hijacked. Its ability to connect to STUN servers also allows it to locate its victims anywhere in the world, which can be construed as a form of privacy breach.
Most of all, the money stolen from the victimized users’ accounts will be used to fund more cybercriminal activities through pack mule scams (i.e. using the stolen funds to buy luxury items online, and then having those items fenced for profit).
Why is this threat notable?
DYREZA is notable as it is a banking malware that sports multiple information theft routines – nearly all of which focus on the browser being used to access online banking accounts, rather than focusing on keystrokes (which ZeuS variants are infamous of doing). Its ability to steal personal certificates also make it that much more of a dangerous threat, as this gives it the ability to bypass SSL, which is a security measure used by online banking websites to prevent online banking account hacking.
Its latest variant, TSPY_DYRE.EKW, has recently been spotted to take advantage of an old Adobe Reader/Acrobat vulnerability (CVE-2013-2729) in order to download itself onto vulnerable systems. It has also been found to be targeting Bitcoin websites besides banking organizations.
Are Trend Micro users protected from this threat?
Yes. Users with Trend Micro security solutions installed on their systems are protected from DYREZA and all malicious elements related to it.
What can users do to prevent these threats from affecting their computers? What should they do if they suspect infection?
Users can protect themselves by adhering to the following best practices:
- Know your bank’s policies. If you receive an online banking notification email and don’t have an account in said bank, delete it immediately. If you do, however, immediately get in touch with the nearest branch to verify the mail itself.
- Delete any suspicious-looking emails you receive, especially if they sport links and/or attachments. Don’t even open them, just delete them.
- Install an antimalware solution that also covers email in its protective scope. This should remove the chance of you accidentally opening malicious email/malicious attachments in the first place.
- If you suspect DYREZA infection, immediately change your online banking account passwords using a different (and hopefully uninfected) system, and touch base with your bank to alert them for any fraudulent transactions taking place. Do the same for any account that you may have accessed using your infected system.