Email is a perennial tool for businesses, enabling effective communication between colleagues, clients, and vendors. Due to its functionality and the overall system that it runs on, it can serve as a pipeline for important elements that fuel the engine of a business operation. To no one’s surprise, it has also become cybercriminals’ bait for their malicious quests.
Email remains a common infection vector for malware and other threats: In 2017, data from Trend Micro™ Smart Protection Network™ security infrastructure revealed that 94 percent of ransomware threats were found in email, while business email compromise (BEC) scams showed a 106 percent increase from the first half of the year to the second. Over the years, organizations worldwide have suffered through hefty payouts, paralyzed systems, and damaged reputations simply because of a malicious Microsoft Word document or PDF attachment.
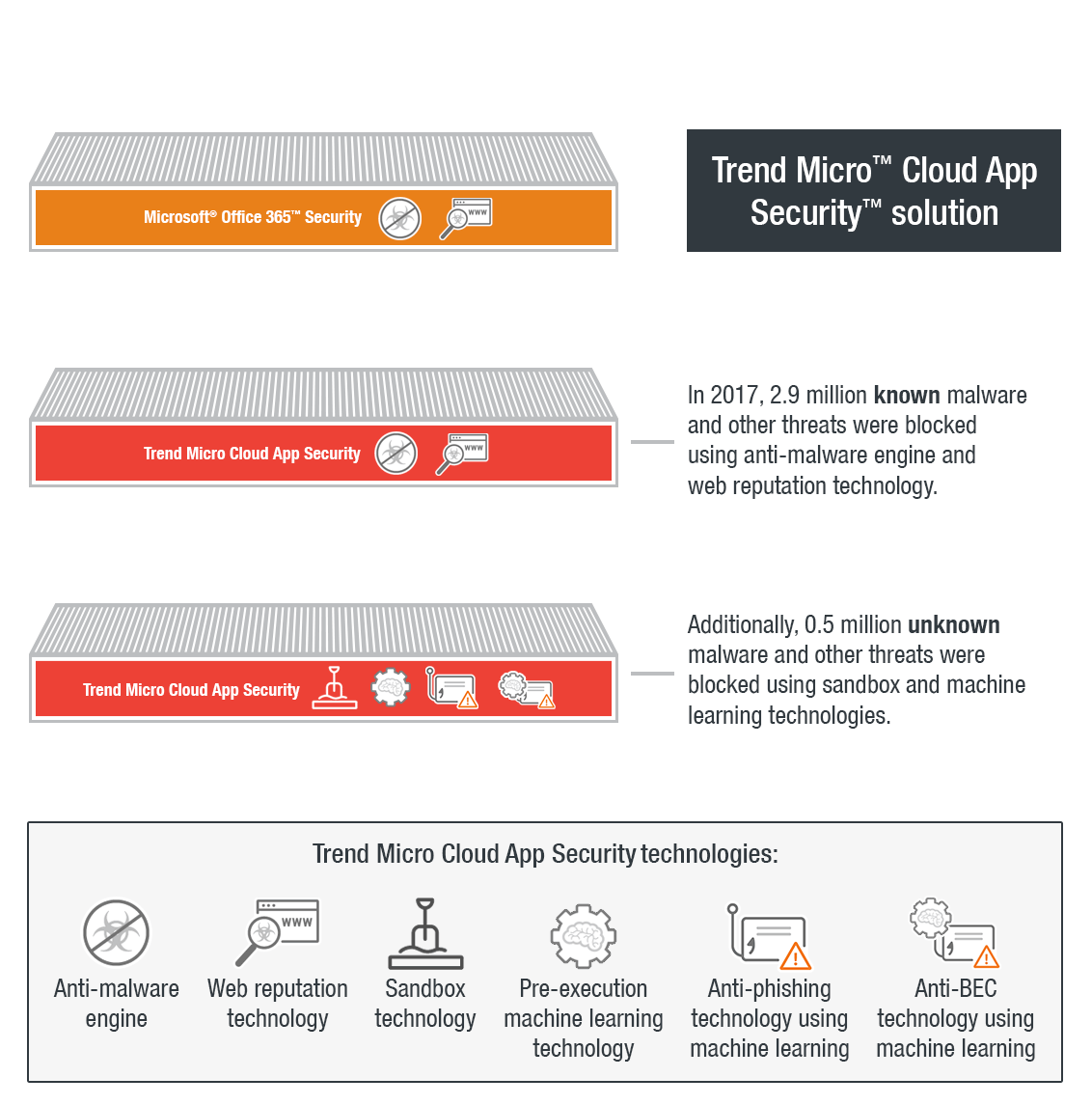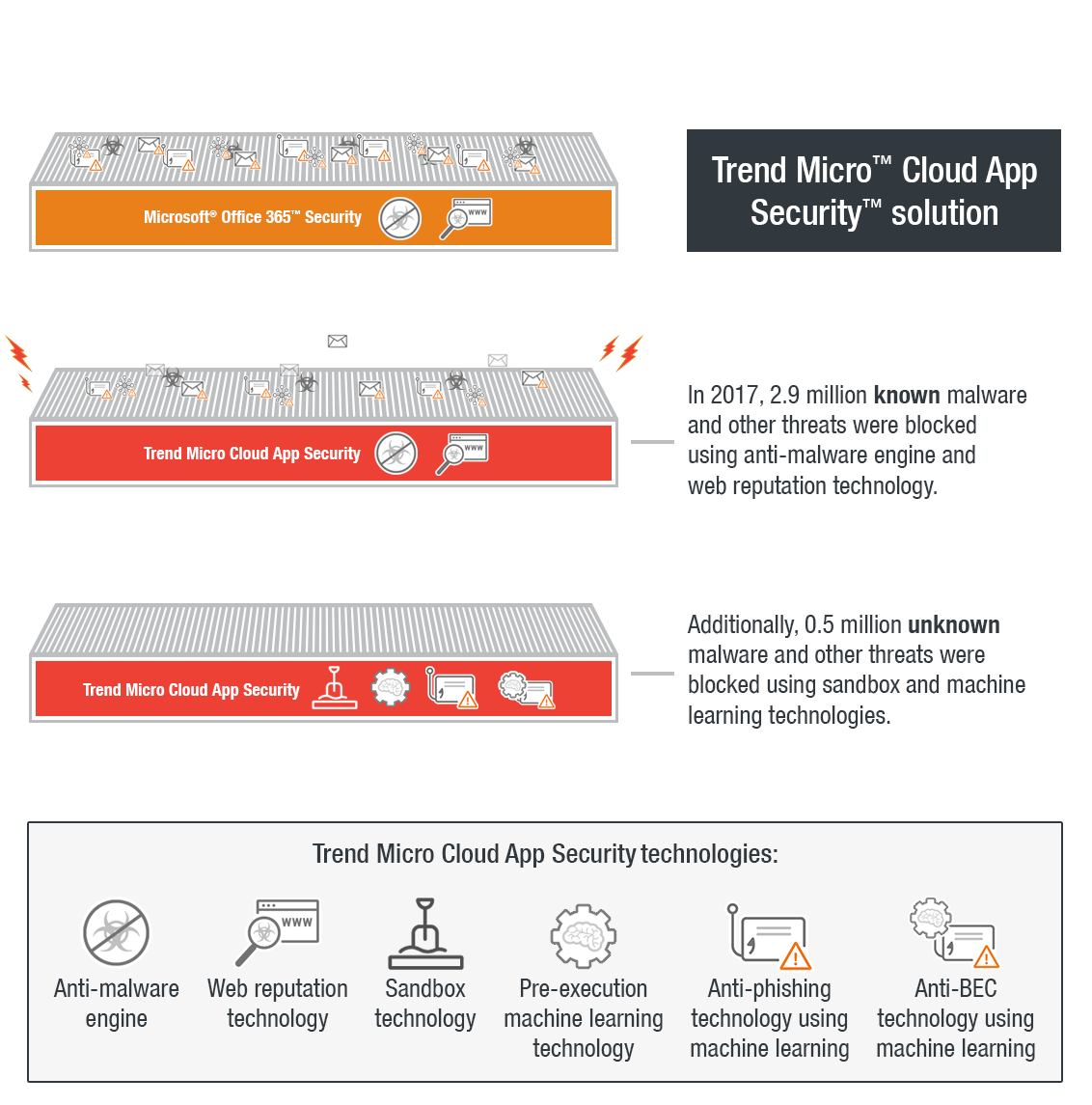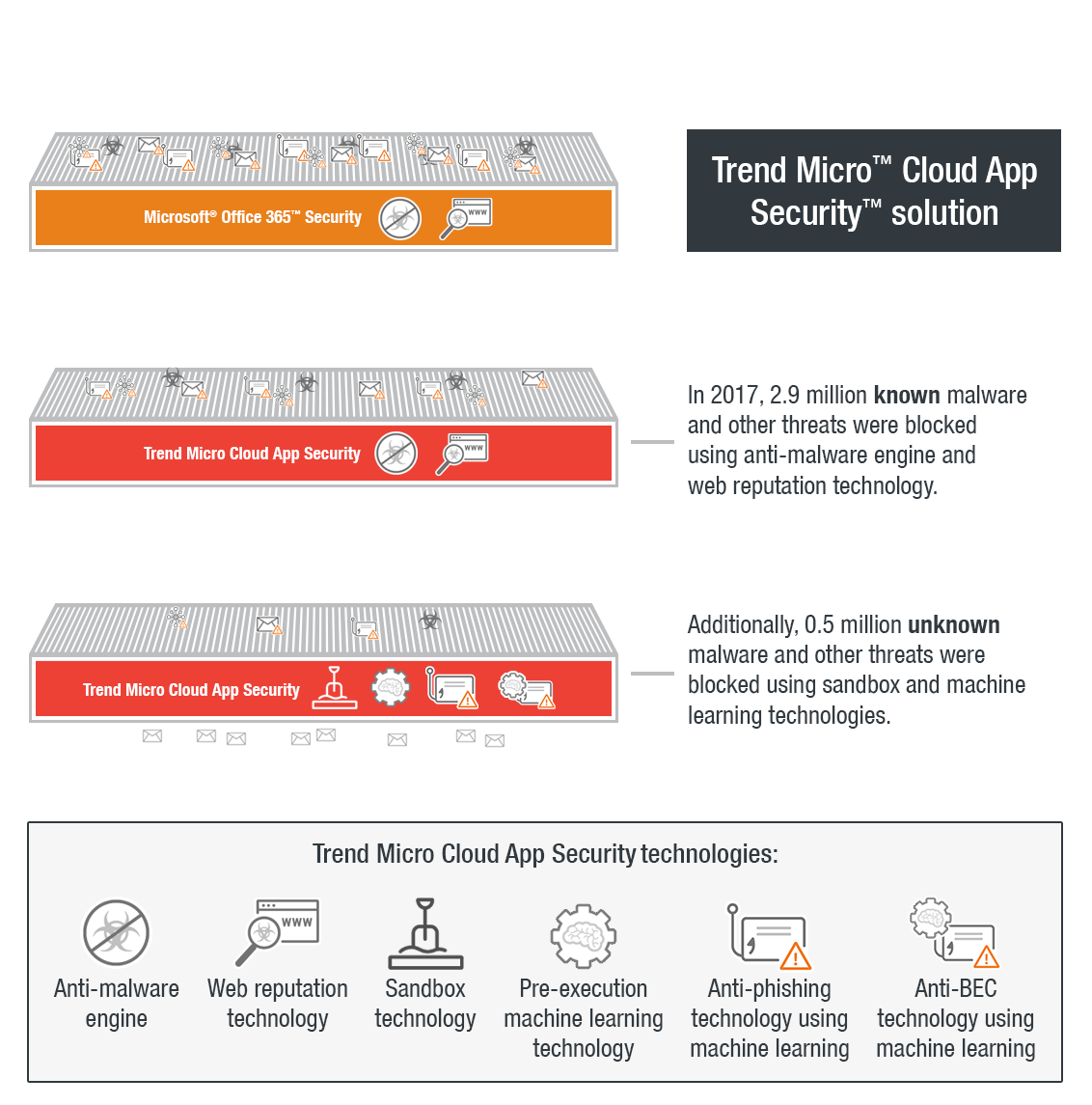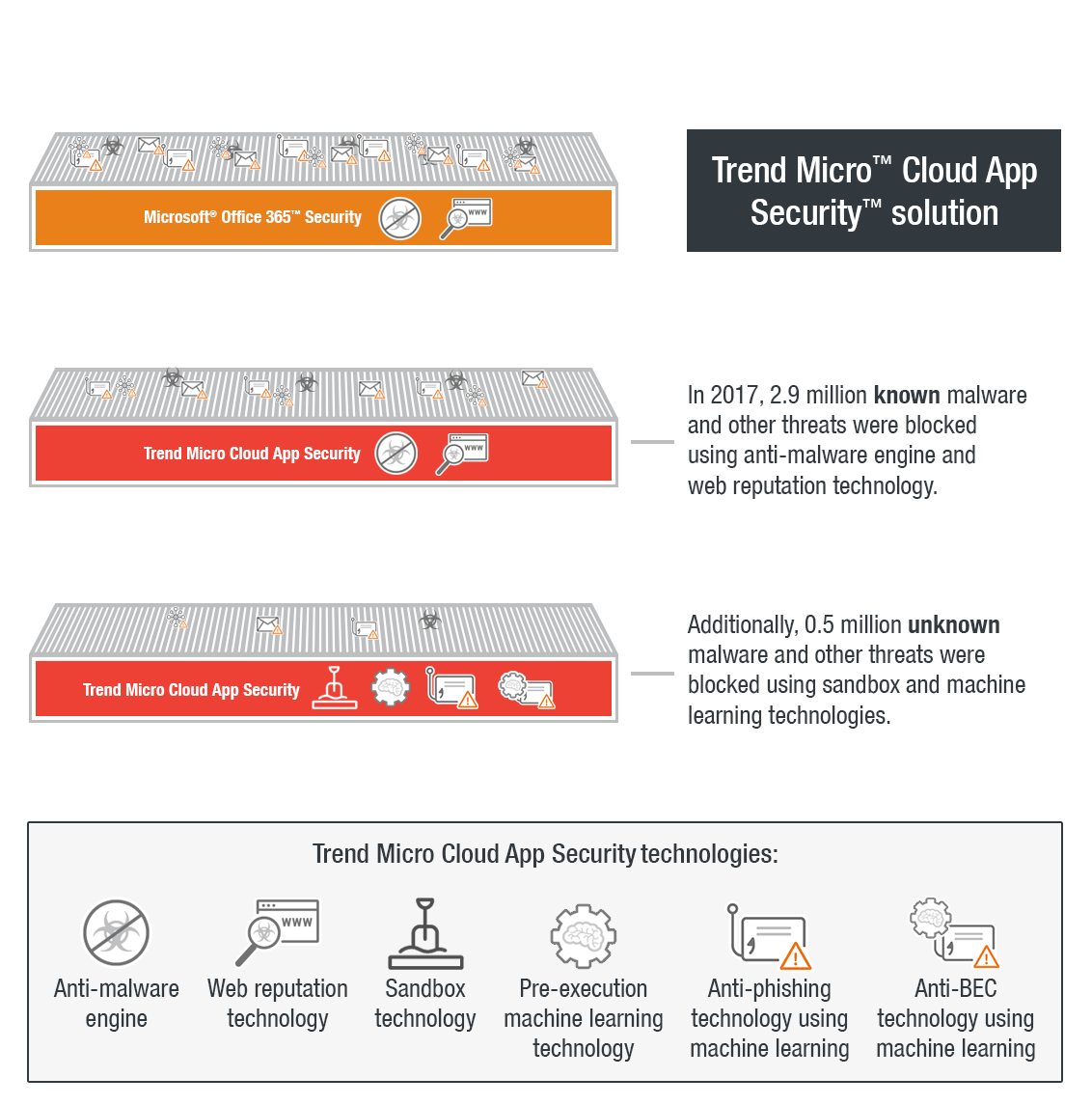
The Trend Micro™ Cloud App Security™ solution is an API-based service protecting the Microsoft® Office 365™ Exchange™ Online, OneDrive® for Business, and SharePoint® Online platforms. It acts as a second layer of protection after email and files have passed through Office 365 scanning. It aims to counter the proliferation of email threats by using machine learning and sandbox malware analysis for ransomware, BEC, and other advanced threats. Cloud App Security can detect both known and unknown email threats that attempt to infiltrate cloud services.
Cloud App Security detected 65,000 known Trojans, worms, viruses, and backdoors for the whole of 2017. With its improved classification engine in Q2, Cloud App Security managed to detect over 50,000 ransomware and 3,000 BEC threats in the last three quarters of 2017. More than 260,000 unknown email threats were also blocked by the pre-execution machine learning and sandbox engines. In the same period, 2.8 million known malicious links as well as over 190,000 phishing emails were blocked. Not counting Office 365 threat scans using its own built-in security, Cloud App Security was able to detect and block 3.4 million high-risk email threats.
We, along with businesses and the rest of the security industry, continue to up the ante in our battle against email threats. However, cybercriminals also adapt and change their methods to continue targeting users. We looked into the state of email threats and security in 2017 to provide a clearer picture of what organizations are up against — and what can protect them.
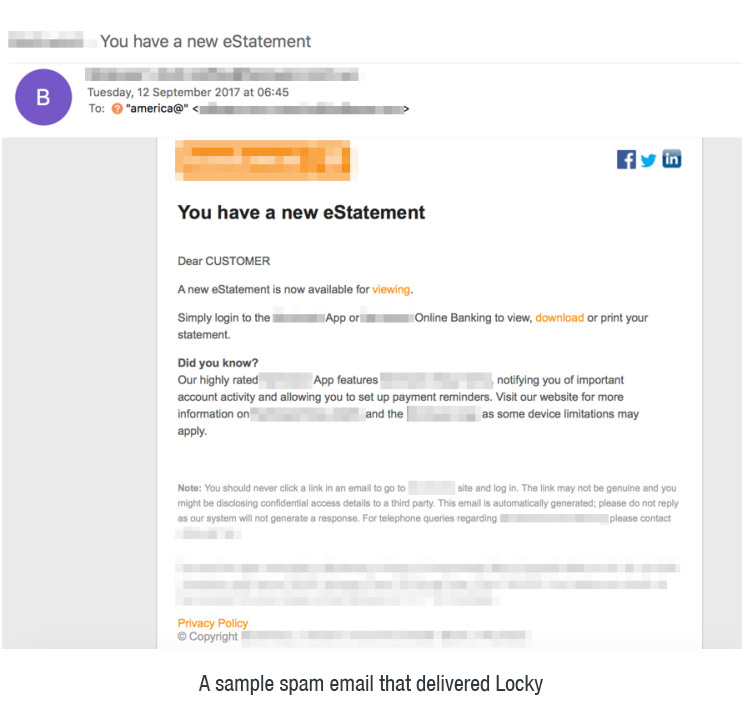
Ransomware continued to proliferate in 2017, and Locky took the spotlight with its massive spam campaigns. Locky was first detected in 2016 and has since continued to spread through different methods, particularly spam email. Kentucky-based Methodist Hospital was targeted with digital extortion via a malicious email carrying the Locky ransomware. In 2017, Locky became the most widely distributed email-borne ransomware. A large spam campaign, detected distributing Locky alongside another ransomware called FakeGlobe, launched millions of attacks in a single day. Notably, one of the latest Locky variants used Word documents with malicious macro, but coded to run and download the ransomware after the user closes the file.
The email-abusing Cerber ransomware, which was tagged as the most prolific ransomware family in the threat landscape, was notable for its evolution. At its peak in 2017, it attempted to counter the security industry’s adoption of machine learning solutions. This Cerber variant was distributed via emails that claimed to be from utility companies. To infect the system, the emails contained a link to a self-extracting archive, and the operators behind Cerber intended to trick users to download and open it. The following flowchart illustrates what happens after.
In our coverage of unique Cerber samples, we found that the U.S., Japan, Taiwan, and Australia were the most affected.
Meanwhile, a ransomware variant sporting new behaviors was also discovered in late 2017. Samples of qkG were found infecting the Microsoft Word Normal template (normal.dot template) on which all new, blank Word documents are based. qkG stands out as the first ransomware to scramble one file (and file type) and one of the rare file-encrypting malware written completely in Visual Basic for Applications (VBA) macros. It also uncommonly employs malicious macro codes, unlike the usual families that use macros mainly to download the ransomware.
In addition to the abovementioned ransomware threats, other email-borne malware families pose new threats. For example, the banking Trojan TrickBot, an iteration of the older malware DYRE/Dyreza, is equipped with new capabilities designed to steal data saved by Microsoft Outlook® by opening relevant registry keys.
The abuse of email services is also common to hacking groups like Pawn Storm, which continues to use email in its relentless campaign to target not just businesses but also governments. In the second half of 2017, Pawn Storm launched credential phishing and spear-phishing attacks against several organizations by exploiting the preview pane of Outlook Web Access (OWA).
In hindsight, it may seem easy to spot maliciously decorated emails using bare observations that don’t require complex security solutions. The truth, however, is that businesses can still be misled when tricked with sophisticated BEC scams.
BEC scams have proven to be so vicious that even software and technology companies were not spared. In early 2017, social engineering tactics were launched against Google and Facebook. The two tech titans had been reportedly defrauded of over $100 million by a man who allegedly used falsified invoices and convinced both companies that he was a member of a partner manufacturing company. Fortunately, most of the losses for both companies were recouped after the incident.
We predict that BEC incidents are on track to multiply this year, with global losses expected to reach $9 billion. The Federal Bureau of Investigation (FBI) said that BEC scams have now been reported in over a hundred countries, showing a 2,370 percent increase in identified exposed losses between January 2015 and December 2016.
Given that email is still the most common infection vector for malware threats, organizations need multiple layers of protection to combat email-borne threats that continue to evolve and spread.
Last year, we became the first email security vendor to use machine learning-based antimalware in our security products. The pre-execution machine learning finds unknown malware before sandbox analysis for added protection and a quicker decision on suspicious files. Integrated into Cloud App Security, the advanced security technology protects Office 365 users.
Cloud App Security has a document exploit detection engine that discovers malware hidden in Microsoft Office files, and an artificial intelligence feature that checks email behavior and intention to identify BEC scams. It detects incoming and internal phishing attacks by using extensive threat intelligence from Smart Protection Network to find and block links hidden in the message body and email attachments that lead to malware. Cloud App Security scans internal email and file sharing services to detect attacks already in progress and discovers criminal attempts to infiltrate organizations from compromised accounts or devices. In addition, it discovers unknown malware using pattern-less technologies by utilizing behavior analysis with sandbox technology and shares intelligence learned during analysis with other security layers.
Ransomware, BEC, and other threats will only continue to abuse email as it has proven to be one of the most easily utilized platforms to gain a foothold in an organization. Aside from using multilayered email security solutions, the workforce is key to keeping an organization safe from cybercriminals. Building a culture of security to combat email threats is imperative in protecting businesses’ most important communication tool.
Using a multilayered identification process for transferring funds can mitigate BEC scams. IT professionals and organization employees should be trained to look out for BEC indicators and practice proper email protocols such as inspecting inbound and outbound messages. Stopping email-borne ransomware from infecting endpoints and systems is also possible by adopting best practices against socially-engineered spam emails.
Moreover, cybercriminals will use different kinds of social engineering tactics to coerce potential victims into downloading files or giving out sensitive information, so it is important to educate employees on how to avoid phishing attacks. Simple steps, such as bookmarking trusted websites and never clicking on links accompanied by suspicious promises, go a long way.
Network administrators should ensure that antispam filters, including policy management and threat detection level thresholds, are properly configured. IT professionals should adopt security measures such as Sender Policy Framework (SPF), Sender ID, DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting & Conformance (DMARC) to prevent the spoofing of the company domain.
If cybercriminals have already successfully infiltrated the organization’s network, there are recovery steps that can be followed. No matter how well-implemented the company’s security policies are, there can be occasional or accidental gaps. Recoveries for such attacks depend on the scenario and on the threat’s payload. For phishing attacks, a password reset followed by proactive email deletion should be the priority. Network administrators should also notify users in advance not to click on unverified email links or executable files.
Email threats are advanced, pervasive, and costly, but with the combination of workforce cybersecurity awareness and solutions like Trend Micro Cloud App Security, they can be stopped before causing havoc.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering



 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One