Dropbox Used In Delivering UPATRE Malware
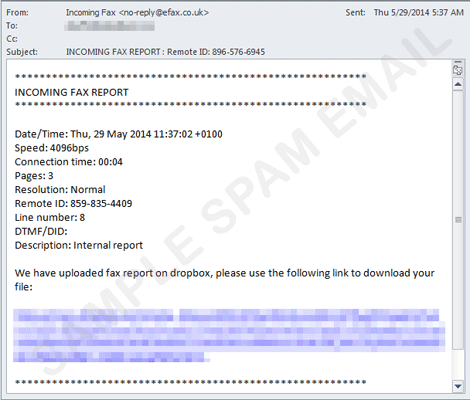
Due to the popularity of file hosting service Dropbox, it is no surprise that cybercriminals leverage this platform to proliferate their malicious activities. We recently spotted a spam run that purports as an eFax notification mail. Users are encouraged to view the fax message by clicking a link. Once clicked, the URL goes to a legitimate Dropbox site which downloads a .ZIP file, containing a malicious .EXE file detected as TROJ_UPATRE. Once users execute this malware, it downloads a variant of NECURS, which is known for disabling security software features of infected system.
UPATRE variants are known downloaders of ZeuS malware. These are commonly seen as email attachments. What is notable in this spam attack is this is the first instance we saw TROJ_UPATRE being deployed via URL found in email message. Typically, this malware arrives as attachment to spammed messages.
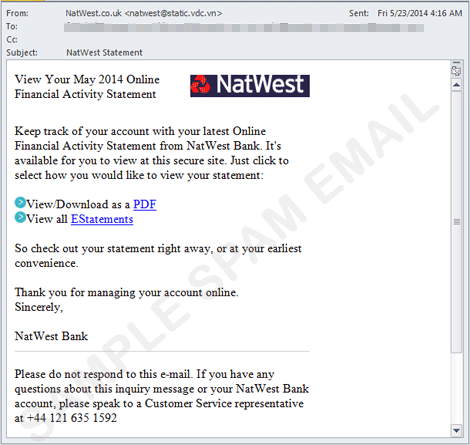
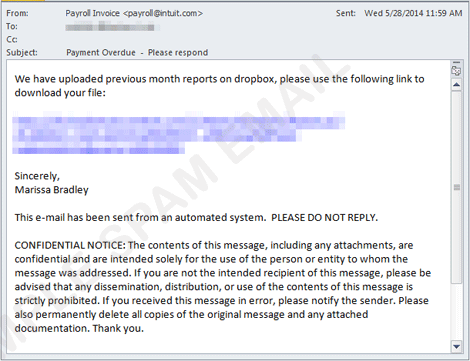
Similarly, another spam run pretends as Natwest Financial Activity Statement email containing a Dropbox link. However, instead of downloading a supposed financial file, users get a malware also detected as TROJ_UPATRE. Lastly, a spammed email contains a Dropbox link, which has an embedded link that leads to Canadian pharmacy website.
Trend Micro protects users from these several spam runs via its Smart Protection Network that detects the spam and malicious file. Users are strongly advised to check first the validity of any email they received before opening any emails from unknown sources.
- ENGINE:7.5
- PATTERN:20736