FBot aka Satori Is Back With New Peculiar Obfuscation, Brute-force Techniques
![[TITLE]](https://documents.trendmicro.com/images/TEx/articles/20180416224808964-450-wpxrugo-800.jpg)
We have recently observed that the Mirai-variant FBot (detected by Trend Micro as IoT.Linux.MIRAI.DLET), also known as Satori, has resurfaced with a brand-new obfuscation technique and a tweaked brute-force attack routine. After analysis, we discovered that this FBot malware uses a peculiar combination of XOR encryption and a simple substitution cipher, which has not been previously used by other IoT malware variants. We have also observed that for its brute-force mechanism, the credentials this FBot sample uses are not located within the executable binary — instead, they are received from a command-and-control (C&C) server.
Our honeypots have been under attack by different IP addresses in an attempt to distribute the FBot malware since mid-November. After analyzing the FBot sample, we discovered that the malware obfuscates the strings it uses for its operation. It decrypts its payload in a host machine using the “0x59” XOR encryption.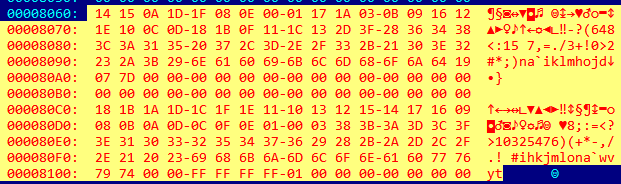
Figure 1. XOR-encrypted data embedded in the FBot sample
We have also observed that after the payload has been decrypted, there are two strings used in FBot’s simple substitution cipher:
| Cipher Alphabet | Plaintext Alphabet |
| "MLSDFQWYXNCZRPOKGIUTABVHEJtfqomaechlynudwvjrxigkzsbp7890254163=@^$" | "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789./ -" |
By replacing each character in the encrypted string with the corresponding letter in the plaintext alphabet (i.e., M=A, L=B), the following string was found:
/proc/self/exe/proc//maps/comm/cwd/var/tmp/varpizzadongshelperOfHelpingslavefartedlolfgtwolfexecbintelnetonPLSDIEPOST /cdn-cgi//proc/net/tcpGET / HTTP/1.0uc-httpd 1.0.0re the chicken and the melon tasty enough
It should be noted, though, that some of FBot’s strings were encrypted using the “0x07” XOR encryption.
We have also observed that for its brute-force attacks, this FBot variant uses credentials that are located in its C&C server (5[.]206[.]227[.]65:7685). It accesses the server, downloads a list of usernames and passwords, and attempts to gain access to vulnerable devices.
Trend Micro solutions
Trend Micro™ Smart Home Network provides an embedded network security solution that protects all devices connected to a home network against cyberattacks. Based on Trend Micro’s rich threat research experience and industry-leading deep packet inspection (DPI) technology, Trend Micro Smart Home Network offers intelligent quality of service (iQoS), parental controls, network security, and more.
The Trend Micro Deep Discovery™ solution provides detection, in-depth analysis, and proactive response to attacks using exploits and similar threats through specialized engines, custom sandboxing, and seamless correlation across the entire attack life cycle, allowing it to detect these kinds of attacks even without engine or pattern updates.
Users of the Trend Micro Smart Home Network solution are protected from particular vulnerabilities and related attacks via these rules:
- DDI rule 4227 - Port Sweep - TCP
- DDI rule 2391 - TELNET_BUSYBOXCHECK_REQUEST
These solutions are powered by XGen™ security, which provides a cross-generational blend of threat defense techniques against a full range of threats for data centers, cloud environments, networks, and endpoints. Smart, optimized, and connected, XGen powers Trend Micro’s suite of security solutions: Hybrid Cloud Security, User Protection, and Network Defense.
Indicators of Compromise
SHA-256
- 51e208e0003ebcf2225f0482865dd03896f759c170f0be84649f666c13e1130c
URLs
- Ohyaya[.]raiseyourdongers[.]pw Disease Vector
- 5[.]206[.]227[.]65[:]7685 C&C Server
With insights from Augusto Remillano II
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One