Ransom.Linux.AVOSLOCKER.YXCAKZ
Linux/Filecoder.AvosLocker.A (Nod32), Ransom:Linux/AvosLocker.A!MTB (Microsoft)
Linux


Threat Type: Ransomware
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
Downloaded from the Internet
This Ransomware arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
TECHNICAL DETAILS
1,619,392 bytes
Yes
Terminates processes, Displays message/message boxes, Encrypts files
Arrival Details
This Ransomware arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Other Details
This Ransomware does the following:
- Terminates VMware Elastic Sky X Integrated (ESXi) and Virtual Machine File System (VMFS) processes
- Displays the following if an argument is not given:
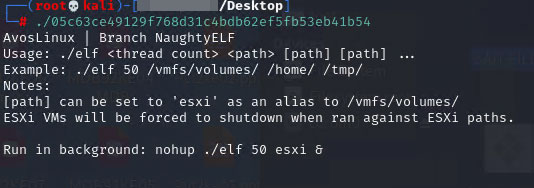
- Displays the following in the terminal while encrypting:
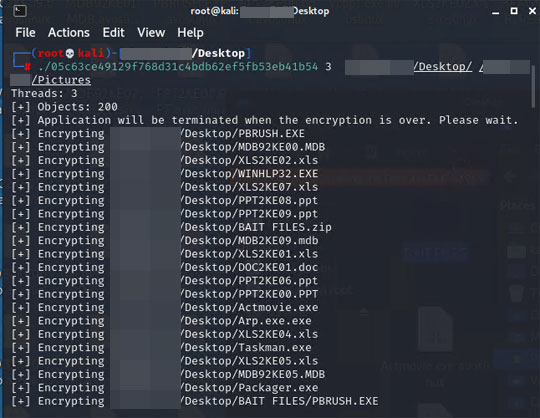
It accepts the following parameters:
- {Thread Count} {path} {path2}
- {Thread Count} - Number of threads to be used for the encrpytion routine.
- {path} - Directory to be encrypted (required)
- {path2} - Additional directory to be encrypted (optional)
Ransomware Routine
This Ransomware appends the following extension to the file name of the encrypted files:
- .avoslinux
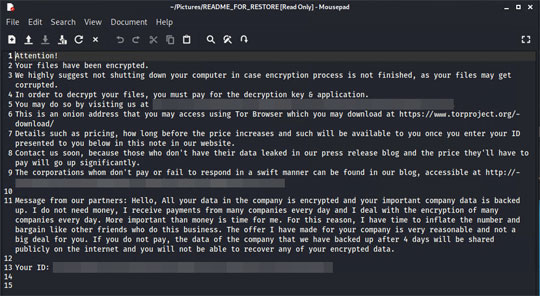
It leaves text files that serve as ransom notes containing the following text:
- {Encrypted Directory}\README_FOR_RESTORE
SOLUTION
9.800
17.307.00
10 Jan 2022
17.308.00
11 Jan 2022
Scan your computer with your Trend Micro product to delete files detected as Ransom.Linux.AVOSLOCKER.YXCAKZ. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check the following Trend Micro Support pages for more information:
Did this description help? Tell us how we did.

