Navigating Gray Clouds: The Importance of Visibility in Cloud Security
The cloud is the digital world’s ground zero for transformation, innovation, and agility. Its vastness and power enable enterprises and organizations to keep up with high-resource demands and allow them to access mission-critical data anytime, anywhere.
With 85% of businesses worldwide using the cloud to store large amounts of information, it has proven its imperative value, especially during the onslaught of the Covid-19 pandemic. 87% of global IT decision makers attribute the speedy shift to the cloud to the unforeseen global health crisis: a move that proves helpful with economic resiliency. Because of the cloud, enterprises and organizations are able to keep the bulk of their employees working from home. Indeed, even after the pandemic, it is expected that the number of employees working from home (which has already quadrupled compared to before the pandemic started) will still be higher than the number in previous years. Today, organizations are already gearing up for a cloud-first world. In fact, banks and financial institutions are now working toward becoming fully cloud-powered by 2025.
Meanwhile, the big move to the cloud has already happened for majority of enterprises and organizations who are invested in providing unhampered, future-proof services. With a considerable number of people working remotely and accessing the cloud from different parts of the globe, however, the issue of visibility in enterprise cybersecurity has become more evident. In this context, how can enterprises prioritize visibility in a cloud-first world?
Post-migration threats and security risks in the cloud
Those who have already migrated to the cloud are by now enjoying increased connectivity, productivity, and efficiency. Still, there are many things that can be done on the cloud — such as data storage, big data analysis, app and software development, and video- and audio-streaming functionalities — which could cause a lot of moving parts and gaps that would need to be secured. In order to keep security strong, enterprises need to be aware of everything that they need to protect. After all, protecting what cannot be seen is difficult, if not impossible.
After seamlessly and securely migrating to the cloud, enterprises need to be aware of the visibility-related challenges and security risks associated with operating on it.
One of the challenges that affect visibility is having disparate buckets of compute resources. Most organizations make use of varying cloud providers, accounts, and services on top of their on-premises data centers. In fact, four out of five companies have two or more infrastructure-as-a-service (IaaS) or platform-as-a-service (PaaS) providers.
To add, in a 2019 survey, over 51% of IT security practitioners shared that their organizations have separate identity and access management (IAM) interfaces for their cloud and on-premises environments. Having separate IAMs can be difficult to oversee, as it could allow unauthorized individuals to gain access to critical or sensitive information.
Meanwhile, 86% of companies make use of 11 different software-as-a-service (SaaS) providers, which include cloud-based apps like Gmail or Microsoft 365. The use of a variety of cloud services and apps is double-edged: While it is beneficial to productivity and efficiency, it also creates a complex web of cloud-powered services that is difficult to oversee without the proper tools and workforce.
Despite what they can bring with respect to streamlining operations, not all cloud apps are created equal. According to Netskope data from 2018, almost 93% of cloud applications that businesses use are not enterprise-ready. This means that they do not meet the standards specified in the Cloud Security Alliance’s Cloud Controls Matrix, which includes parameters for data security, access control, and privacy.
The spawning of multiple unsecured services (also referred to as shadow IT) is another security risk that affects visibility. In 2019, before the Covid-19 pandemic hit, a report from software company Igloo stated that 50% of employees use apps and infrastructures that are not approved by their companies to accomplish work-related tasks. As large numbers of employees started shifting to work-from-home (WFH) setups due to the pandemic in 2020, many of them resorted to using personal devices such as their own laptops, computers, or mobile phones for work.
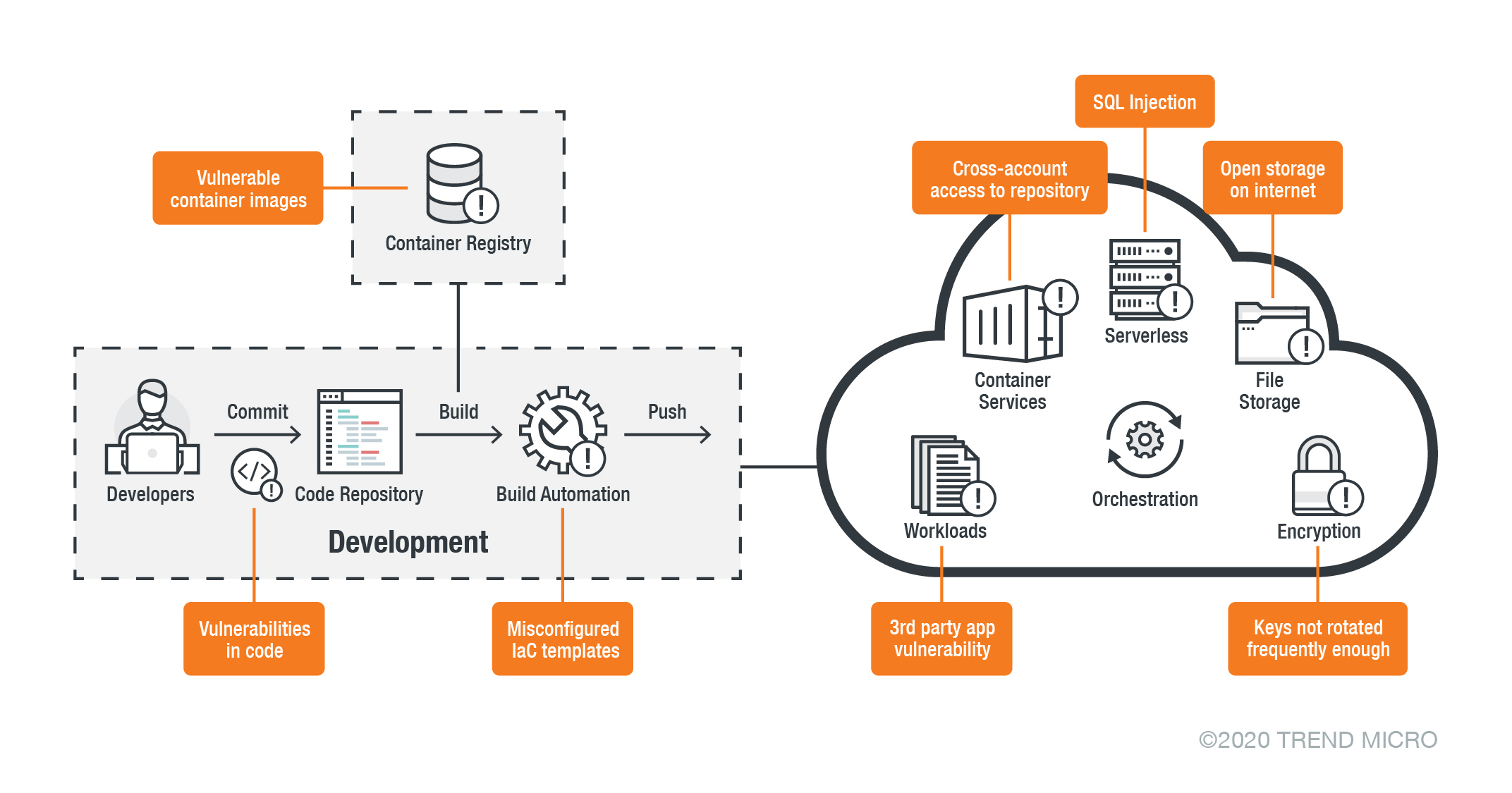
Figure 1. Some potential risks in cloud environments
Because the cloud enables speedy access to dynamic resources, developers are able to deploy new servers without having to bother with the hassles that are usually associated with deployment in an on-premises environment, such as provisioning and budgeting. On the other hand, security teams might also be unaware of all the virtual environments that are being spawned. As a result, they might not be able to apply all the necessary protections. Out of haste and in the aim of ensuring that services are able to communicate with one another seamlessly, these quickly deployed virtual private clouds (VPCs), virtual networks, and containers might be configured to have lax security provisions or none at all. It cannot be stressed enough that this is an unsecure practice that could lead to exposed public-facing services.
Because of very permissive configurations and bad coding practices, APIs that might contain sensitive data could become exposed for malicious actors to prey on. Exposed APIs, for instance, could be abused by cybercriminals to conduct remote code execution (RCE) and distributed denial of service (DDoS) attacks. Exposed containers could also lead to cryptocurrency mining, something that we recently observed with cryptocurrency-mining malware targeting both Linux systems and exposed Docker environments.
Cloud-native app development could also cause an increase in the use of and reliance on third-party libraries. In order to match the velocity needed to power these ever-evolving apps, developers often resort to the heavy use of open-source code, libraries, components, and software. Unfortunately, these could be riddled with vulnerabilities — ones that are actively targeted by malicious actors. In particular, Snyk research has determined that vulnerabilities in open-source components have increased in the past three years. It should be emphasized that the exploitation of these vulnerabilities could lead to compliance and security issues.
Clear clouds ahead: How to gain visibility and security in a cloud-first world
The cloud is an extremely advantageous technological advancement. However, it also comes with complexities and security considerations — especially at a time when remote work is rampant and reliance on the cloud for automation and scalability is the norm. Regardless of where employees and systems are located during the pandemic, enterprises need to have visibility over their employees and environments to keep them as secure as possible.
To make the most of what the cloud can offer, here are some security recommendations. By following these closely, enterprises and organizations can keep visibility a priority within their systems and environments. They can also protect themselves from a wide range of evolutionary threats and misconfigurations.
Employ the principle of least privilege. Users should only have the minimum necessary access right or permission that is required for their tasks. Not all users need to have admin access or root privileges, and thus should not be given such.
Adhere to the shared responsibility model. Data hosted on the cloud shouldn’t be perceived as automatically protected from threats and risks. The major cloud service providers (CSPs), namely Amazon Web Services (AWS), Google Cloud Platform GCP), and Microsoft Azure, have their own resources that highlight the importance of shared responsibility. AWS’ shared responsibility model outlines the clear areas of responsibility for both the CSP and the user with regard to the use of the cloud. AWS is responsible for the “security of the cloud” or the overall cloud infrastructure where services are hosted. Users, meanwhile, are responsible for the “security in the cloud,” which is determined by the type of service that they will use, such as IaaS, PaaS, and SaaS. Google Cloud Platform (GCP), which follows the Payment Card Industry Data Security Standard (PCI DSS), also provides the requirements that Google complies with on behalf of its clients. Additionally, GCP outlines the shared responsibilities between both parties. Similarly, Microsoft Azure also shares some areas of responsibility between Microsoft and its customers, depending on the type of stack deployment that their customers have. Regardless of stack, however, Microsoft provides guidance on some areas that customers are always responsible for, such as their data, endpoints, accounts, and access management.
Strengthen email, gateway, server, and network security. Vulnerabilities in applications, operating systems, and platforms can be exploited via unsecure networks. Virtual patching can help defend networks, workloads, servers, and containers against zero-day attacks, data breaches, and ransomware attacks.
Secure endpoints, internet of things (IoT) devices, and home networks. As employees work remotely, it’s important for companies to ensure that the use secure machines, devices, and networks for all work-related tasks. We detail important security considerations in the new norm for both employers and employees in our article “Working From Home? Here’s What You Need For A Secure Setup.”
Set up a continuous monitoring program. Organizations need to select a security methodology that best suits their online architecture’s demands. This will help organizations systemically analyze their system and infrastructure’s security needs by regularly monitoring existing controls. In an interview with Mark Houpt, Chief Information Security Officer (CISO) of DataBank, he discusses the importance of continuous monitoring and how it is applied in their organization.
Employ strong, personalized WFH policies and training for employees.
Companies also need to integrate the most common employee personas based on cybersecurity behaviors when formulating their WFH policies and training activities. Since employees have different ways of thinking about and dealing with cybersecurity risks, a one-size-fits-all approach to training will not prove effective for enterprise security.
Employ the zero-trust model. The zero-trust security concept basically hinders organizations from automatically trusting or granting access to users on a perimeter-based system. It doesn’t matter whether a user is within the organization’s network perimeter or not — all users will need to be verified before they are given access to specific parts of the system.
Trend Micro’s cloud security solutions
Cloud-specific security solutions such as Trend Micro™ Hybrid Cloud Security can help protect cloud-native systems and their various layers. It is also powered by Trend Micro Cloud One™, a security services platform for cloud builders that provides automated protection for the continuous integration and continuous delivery (CI/CD) pipeline and applications. It also helps identify and resolve security issues sooner and improves delivery time for DevOps teams. Hybrid Cloud Security includes:
- Workload Security: runtime protection for workloads
- Container Security: automated container image and registry scanning
- File Storage Security: security for cloud file and object storage services
- Network Security: cloud network layer IPS security
- Application Security: security for serverless functions, APIs, and applications
- Conformity: real-time security for cloud infrastructure — secure, optimize, and comply
The Trend Micro™ Cloud App Security solution enhances the security of Microsoft 365 and other cloud services by taking advantage of sandbox malware analysis for ransomware, business email compromise (BEC), and other advanced threats. It also protects cloud file sharing from threats and data loss by controlling sensitive data usage and protecting file sharing from malware.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
- Metaverse or Metaworse? How the Apple Vision Pro Stacks Up Against Predictions
- Understanding Hacktivists: The Overlap of Ideology and Cybercrime
- Across the Span of the Spanish Cybercriminal Underground: Current Activities and Trends
- Bridging Divides, Transcending Borders: The Current State of the English Underground
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks Today’s Cloud and Container Misconfigurations Are Tomorrow’s Critical Vulnerabilities
Today’s Cloud and Container Misconfigurations Are Tomorrow’s Critical Vulnerabilities Ransomware Spotlight: Ransomhub
Ransomware Spotlight: Ransomhub CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks