The mobile threat landscape is quickly resembling today’s PC threat landscape wherein vulnerabilities are discovered one after another. Each new bug is more damaging than the one before it. And a lot of these bugs could lead to data theft or device infection if exploited.
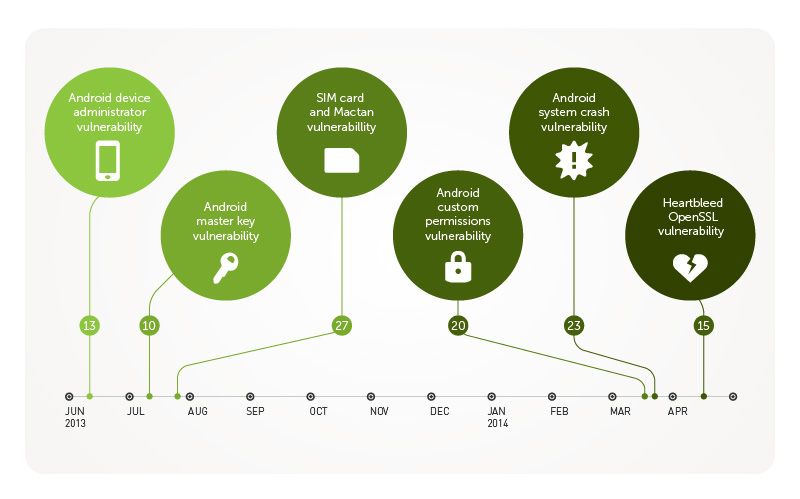
Vulnerabilities have been cropping up since June 2013. The Android™ “master key” vulnerability, which affected almost all devices, could make any mobile malware “legitimate.”
Vulnerabilities in device accessories like SIM cards and fake iPhone® chargers also came to the fore. A platform bug that could also trap a device in an endless reboot loop and another that could leak user data soon followed. And who could forget the most recent bug—the Heartbleed vulnerability—which could affect mobile devices as badly as it could computers.
Android Vulnerability Timeline
Bugs, Bugs, and More Bugs
Device Administrator Vulnerability
ANDROIDOS_OBAD, which was discovered in the early part of June last year, exploits a bug in Android’s Device Administrator feature. When installed, OBAD could continuously pester affected users to activate the Device Administrator feature on their phones. Once done, OBAD allows attackers to gain root privileges on affected devices to get these to follow malicious commands.
Master Key Vulnerability
Found in the early part of July last year, the master key vulnerability had to do with the way Android apps were “signed” by developers to prove they were legitimate. Exploitation allowed cybercriminals to push out malicious updates to legitimate apps, turning them bad.
A month after its discovery, cybercriminals abused the bug to turn NH Bank’s online banking app bad.
SIM Card and Mactan Vulnerabilities
The SIM card and fake iPhone charger (dubbed “Mactan”) bugs were discussed in Black Hat U.S. 2013. The SIM card bug had to do with using an old encryption system. To exploit it, attackers can send a specially crafted text message to cause an error in the target SIM card.
The affected SIM card responds with an error code that contains a 56-bit security key. Attackers could use this key to send messages to affected devices to trigger the download of malicious Java™ applets. These applets could perform malicious routines like send text messages and allow attackers to know where the users are.
The Mactan vulnerability, meanwhile, could allow mini-computers installed on fake chargers to initiate malicious USB commands. Apple has since issued apatch for this.
Custom Permissions Vulnerability
The custom permissions bug, which was found this March. Custom permissions, which developers create, prevent users from changing how apps work. Custom permissions run on devices, depending on when the apps they are tied to were installed.
Enterprising cybercriminals could make sure that their malicious creations run custom permissions before any other app does. Once their malicious custom permissions run, they could make them run on legitimate apps, in a way “Trojanizing” them. That way, apps that contain personal data could be forced to share that information with the malicious app that was installed before it. Google, after being notified of this bug, has since issued a patch.
Reboot Loop Vulnerability
At around the same time, the reboot loop vulnerability was discovered. It not only affected Google Bouncer—the vendor’s response to malicious apps found in Google Play™—but also all devices that ran Android 4.0 and above. If exploited, the bug could render devices unusable via “bricking”—being forced to endlessly reboot.
The bug affects the WindowManager service, which handles how windows appear on a device’s screen. If it crashes, the platform crashes, forcing affected phones to reboot.
Cybercriminals can set off a chain reaction by creating an app that opens a window specifically designed to crash WindowManager, specifically a window with a title too large for the service to handle. Once opened, the service and OS crash. If the malicious app runs every time a phone is booted up, the device will be bricked.
To stop the endless cycle of reboots, you can use a boot loader recovery fix or reset your phone. Note that these will wipe out all of the data stored on your device though.
Heartbleed Vulnerability
We extensively reported on the Heartbleed vulnerability this year as well because it could affect not just computers but mobile devices as well. All devices, regardless of platform, may be affected if apps that access vulnerable HTTP servers are installed on them. Accessing servers is necessary for activities like making in-app purchases.
The Heartbleed vulnerability especially affected Android version 4.1.1. As such, all apps that run on affected devices could be vulnerable to data theft. Credit card information and login credentials stored on affected devices could end up in cybercriminals’ hands.
Note that devices that run other Android versions could be vulnerable, too. In fact, we found 273 apps in Google Play alone that came bundled with the vulnerable version of the OpenSSL library. If installed, these made any device vulnerable to the Heartbleed bug.
Live and Let Live or Upgrade?
Mobile vulnerabilities are even more dangerous than mobile malware. Not only does exploitation expose users to even graver threats; those affected only has two options—live with the vulnerabilities or buy a new device that runs the latest OS, especially if you use an Android device because the platform suffers fromfragmentation.
Fragmentation occurs when certain devices in an ecosystem are stuck with a particular OS version. The OS can’t be updated because the device manufacturer has not yet optimized or released an update for a specific device. This renders affected devices vulnerable unless their manufacturers roll out updates, which could take a long time. It doesn’t help that most manufacturers don’t release updates at all.
You can live with some vulnerabilities if buying a new device is not an option. Just remember to adhere to mobile device best practices. Follow your company’s regulations if you use company-sponsored mobile devices so you don’t leak confidential corporate information.
Platform developers release updates or patches more so keeping an eye out for security news could be very helpful. Stay in the know to stay safe. Purchasingsecurity apps to help keep your devices safe from threats is a very big help as well. They won’t cost as much as a new device but can help keep your device bug and malware free.

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One