Analysis: Abuse of .NET features for compiling malicious programs
By Karen Victor and Matthew Fernandez (Threat Analysts)

The .NET framework, a software development framework created by Microsoft and is now a built-in component of Windows, includes components that enable developers to compile and execute C# source code during runtime. This allows programs to update or load modules without having to restart. While the .NET framework is originally intended to help software engineers, cybercriminals have found a way to abuse its features to compile and execute malware on the fly. Recently, we discovered several kinds of malware, such as LokiBot (detected by Trend micro as Trojan.Win32.LOKI), utilizing this technique. This particular LokiBot variant disguises itself as a fake game launcher to trick users into downloading the malware into their machines and drops a compiled C# code into the system.
The infection flow below illustrates this technique in action:
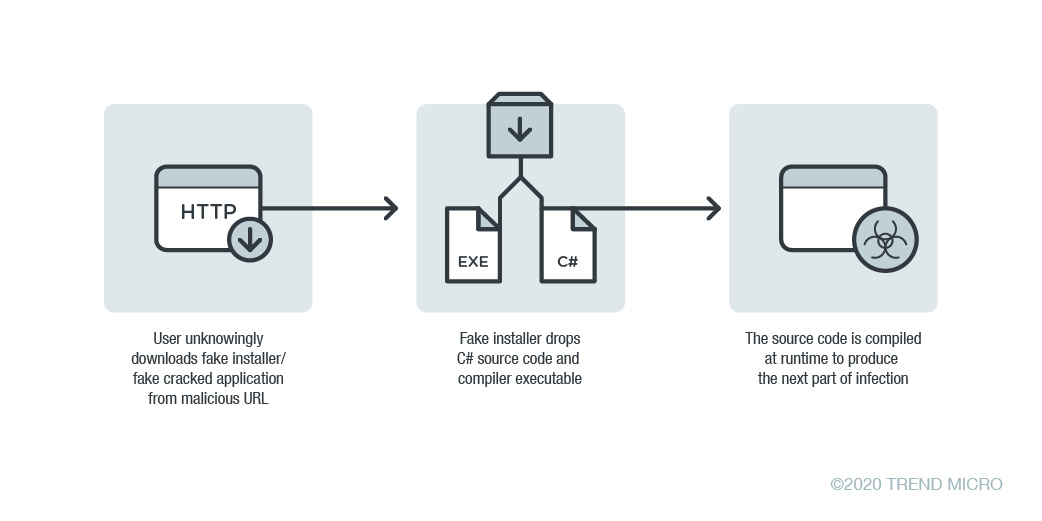
Figure 1. .NET abuse infection chain
An awareness of this unusual abuse of .NET features helps in building robust defenses against the ever-evolving threat landscape.
Technical Analysis
The infection begins when a user unknowingly downloads a malicious file masquerading as a legitimate installer, like LokiBot’s fake game launcher. Other samples we’ve analyzed use icons and metadata that mimic applications such as FileZilla, FaxTalk Communicator, OpenBullet, Facebook Messenger, Mini FTP, and many more. These fake installer files were packaged using the NSIS (Nullsoft Scriptable Install System) installer-authoring tool.
Figure 2. File icons of malicious samples impersonating legitimate applications
Upon execution, the installer will drop two files into a victim’s machine:
|
File |
Description |
|
%HOMEPATH%\pictures\{random 17 characters file name ending in “m”} |
C# source code |
|
%HOMEPATH%\pictures\{random 19 characters file name ending in “ma5.exe”} |
.NET executable |
An investigation of the dropped C# source code file reveals that the majority of its contents are obfuscated functions and encrypted machine code. In this example, the encrypted machine code is stored in the EventData variable:
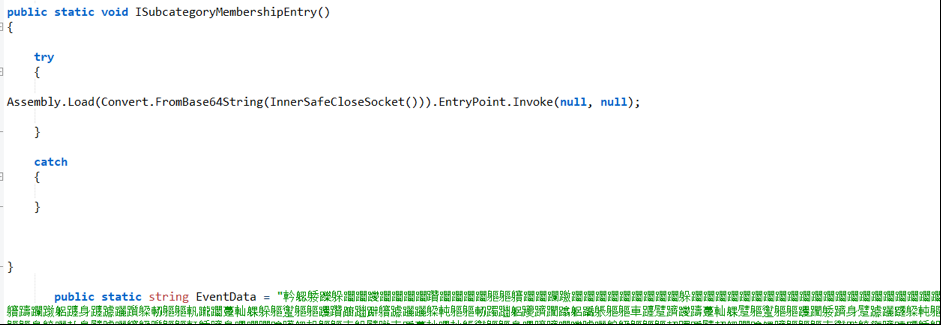
Figure 3. Screengrab of malicious C# source code
We observed that the dropped .NET executable is responsible for compiling the C# source code into executable format. It uses CSharpCodeProvider, a .NET framework class that allows programmers to access the C# language compiler. The screenshot below shows how the malware initializes its compiler.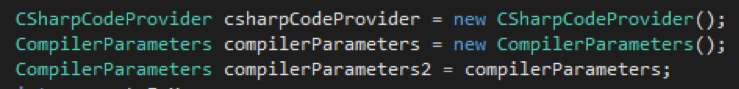
Figure 4. Screengrab of code showing the initialization of C# compiler
Afterwards, it uses the CodeDomProvider class to compile the C# code into a dynamic-link-library (DLL), which is a binary that contains functions that other executables can use.
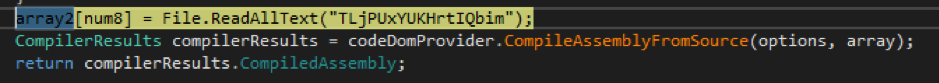
Figure 5. Screengrab of code showing the .NET executable reading and compiling the C# source code
Finally, the .NET executable uses InvokeMember to call the main function of the compiled DLL. For the analyzed sample (SHA-256: a805adf88390a05745d9cff6891e1a3b4acdb2096acf08371cc93a915523314c), the function name is “ISubCategoryMembershipEntry”. This function is seen in its source code form in figure 3.
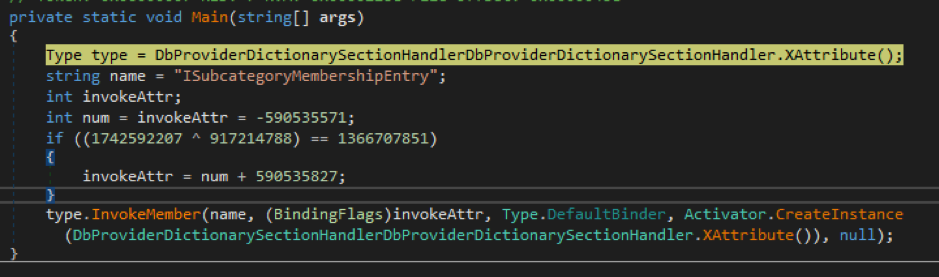
Figure 6. Screengrab showing the main function of the .NET executable
The function names that the compiled DLL uses are also names of classes found in legitimate Microsoft libraries, like “ISubCategoryMembershipEntry” or “TaskSchedulerException.” It may have been designed this way to hide the DLL execution in plain sight, as well as to deceive malware analysts and possibly stop them from fully analyzing the files.
The compiled DLL contains the instructions needed to de-obfuscate and decrypt its contents, ultimately being able to load its decrypted content as another .NET executable. This leads to the installation of the payload, which is the next stage of the infection chain.
The following screenshot shows the “ingodwetrust*.exe” running process, which is a backdoor payload of one of the samples we’ve analyzed: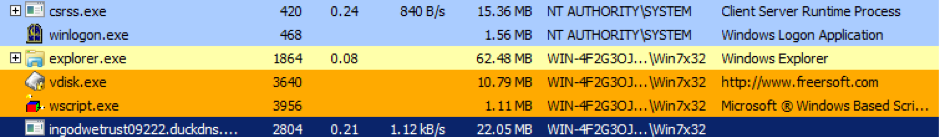
Figure 7. Screengrab showing the execution of “ingodwetrust*” backdoor and wscript execution of the malicious script
This executable runs alongside wscript.exe that in turn runs a script that prevents the system from entering sleep mode. This script and backdoor combination makes the system available to the malicious actor at all times.
Other samples we’ve investigated had a trojan spy payload, which runs silently in the background of an infected machine. The trojan spy continuously gathers victim information, which it sends over a command and control (C&C) server.
Conclusion
Cybercriminals are continuously beefing up their defense evasion techniques. Using malware in its source code form helps in their attempt to avoid detection by modern security controls. By abusing built-in functions of the .NET framework, they are able to compile and execute malicious C# source code — an unconventional way of completing the infection chain.
Seeing this technique in the wild suggests that more malicious actors are using similar techniques, abusing legitimate programs that are native to the system to carry out their attacks.
Recommendations and Trend Micro solutions
The compile-after-delivery technique cannot be easily mitigated through preventive controls since it is based on the abuse of a feature that is built into Microsoft Windows.
Users can defend against this threat as well as similar types of malware by following these security recommendations:
- Avoid accessing suspicious or unknown URLs.
- Avoid downloading cracked applications, as these may be bundled with malware.
- Unless you are certain of the creator of a software or application, do not authorize the download or installation of software. Only download software or applications from official websites.
- Be wary of socially engineered threats.
Additionally, users and organizations can benefit from employing security solutions that proactively blocks emerging and unknown security risks, like Trend Micro’s Predictive Machine Learning module.
Trend Micro™ Deep Discovery™ provides detection, in-depth analysis, and proactive response to attacks using exploits and similar threats through specialized engines, custom sandboxing, and seamless correlation across the entire attack life cycle, allowing it to detect these kinds of attacks even without engine or pattern updates. These solutions are powered by XGen™ security, which provides a cross-generational blend of threat defense techniques against a full range of threats for data centers, cloud environments, networks, and endpoints. Smart, optimized, and connected, XGen powers Trend Micro’s suite of security solutions: Hybrid Cloud Security, User Protection, and Network Defense.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report The Road to Agentic AI: Navigating Architecture, Threats, and Solutions
The Road to Agentic AI: Navigating Architecture, Threats, and Solutions