MIRAI
Linux


Threat Type: Trojan
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
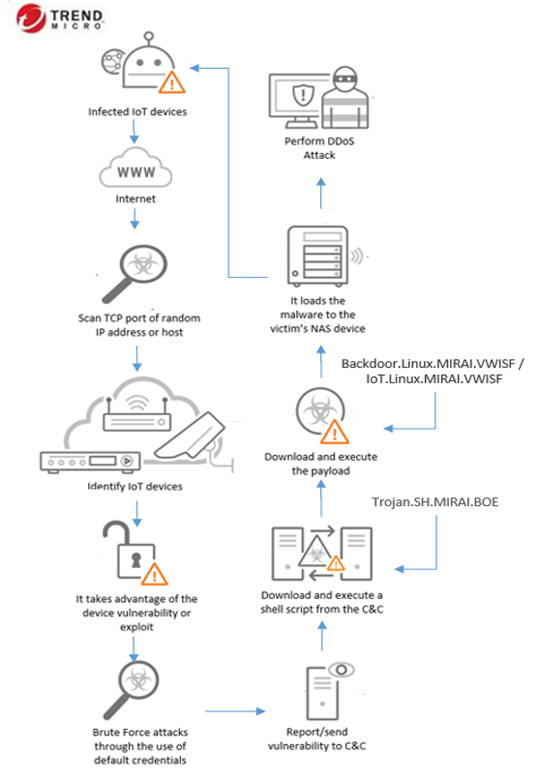
MIRAI is a malware that turns networked devices running Linux into remotely controlled bots that can be used as part of a botnet in large-scale network attacks. It primarily targets online consumer devices such as IP cameras and home routers. The MIRAI botnet was first found in August 2016 by MalwareMustDie, a whitehat malware research group. It has been used in some of the largest and most disruptive distributed denial of service (DDoS) attacks. The source code for Mirai was published on Hack Forums as open-source. Since the source code was published, the techniques have been adapted in other malware projects.
The MIRAI variant named Mukashi attacks network-attached storage (NAS) devices. Mukashi takes advantage of CVE-2020-9054, a vulnerability found in Zyxel NAS devices. Exploitation allows remote attackers to execute malicious codes into the affected system. It uses brute force attacks through default credentials to log into Zyxel NAS products. When logged in successfully, the attackers can now take control of the devices and add them to a botnet that can be used to perform distributed denial of service (DDoS) attacks. Mukashi retains the ability of communicating to a command-and-control server.
MIRAI gathers the following information and sends it to its servers:
- User/device information (IP address, port, username, password)
It is capable of the following:
- Exploits
- Information Theft
- Backdoor commands
It follows the typical infection chain below: