Secure earlier
Scan throughout your build pipeline, verifying new container images as they’re built and providing continuous zero-day protection after deployment. Automated scanning and response provides instant feedback for developers about the presence of threats and vulnerabilities.

Trusted enforcement
Make centralized container admission control part of your container security approach. Trend Micro provides policy-based management of images, allowing security teams to define the rules so only the most secure Kubernetes administered containers are deployed.

Complete protection
Automate vulnerability detection and protection of containerized applications from build to runtime. Gain in-depth security coverage built into your CI/CD processes to discover, assess and mitigate container risks. Prioritize risks and bolster security with Attack Surface Management.
WHY CONTAINER SECURITY
End-to-end container protection
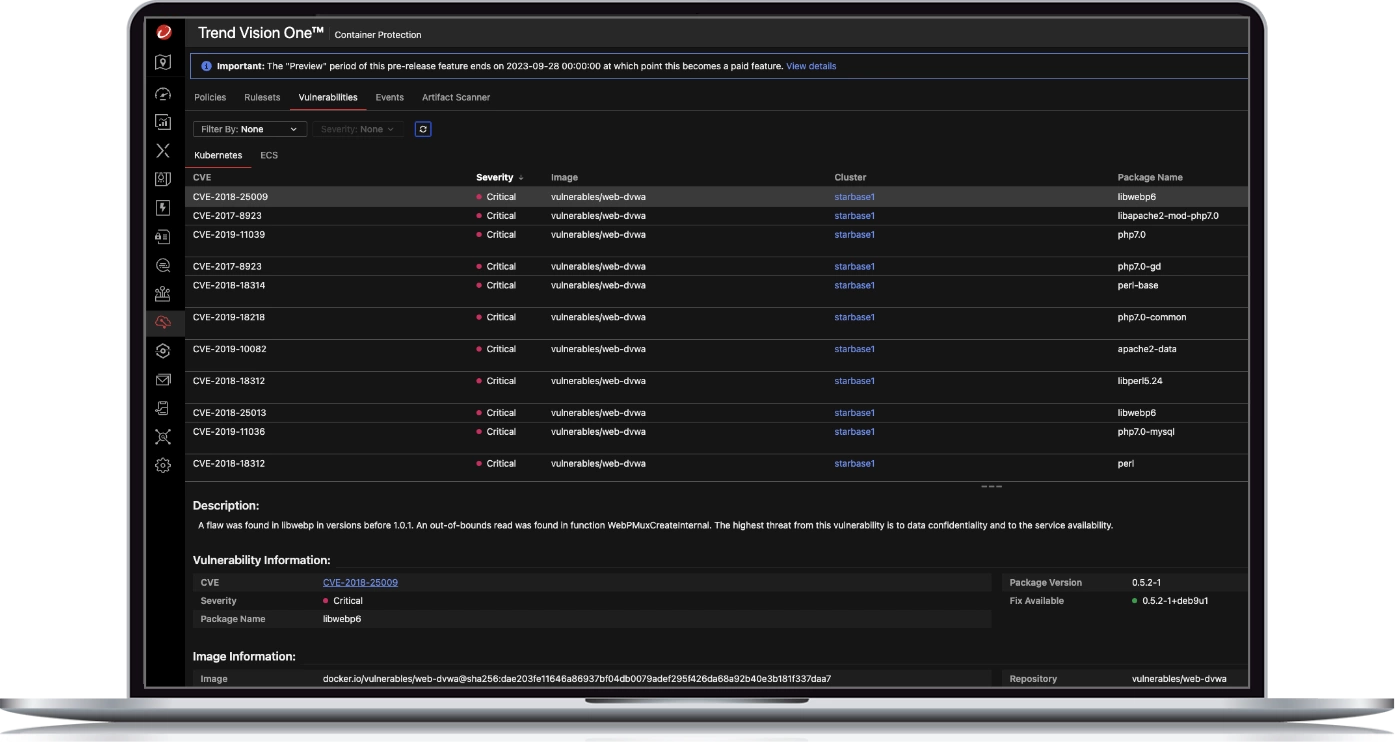
Address security issues before they can be exploited in production
- Uncover vulnerabilities, malware, and compliance violations within container images
- Detailed scans with recommended fixes anywhere in your pipeline
- Address and remediate issues before they can be exploited in production
- Minimize false positives by correlating patch layers with vulnerable packages in the same image
Fix fast with actionable insights
- Enable developers to remediate security issues before deployment via existing tools and workflows
- Share common policies across multiple pipelines while removing the need to hard-code rules for scan results
- Easily review scan results through command lines or tool suite scripting language – no security expertise required
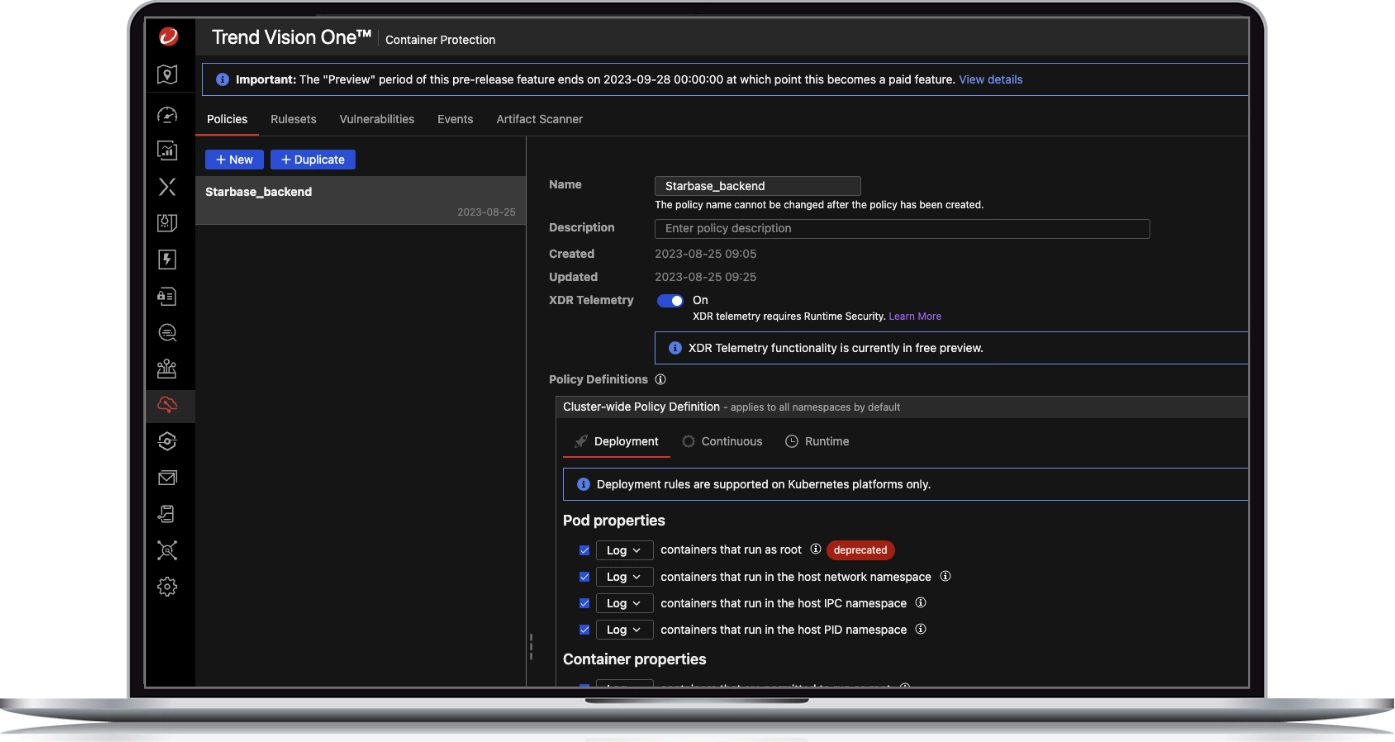
Ensure ongoing container security
- Detect security issues early, enforce admission policies, and ensure only the most secure containers run in production
- Allow images that only meet specific application or organization security policies to proceed through the pipeline
- Choose from advanced policies, such as disallowing privileged containers or allowing exceptions based on names or tags
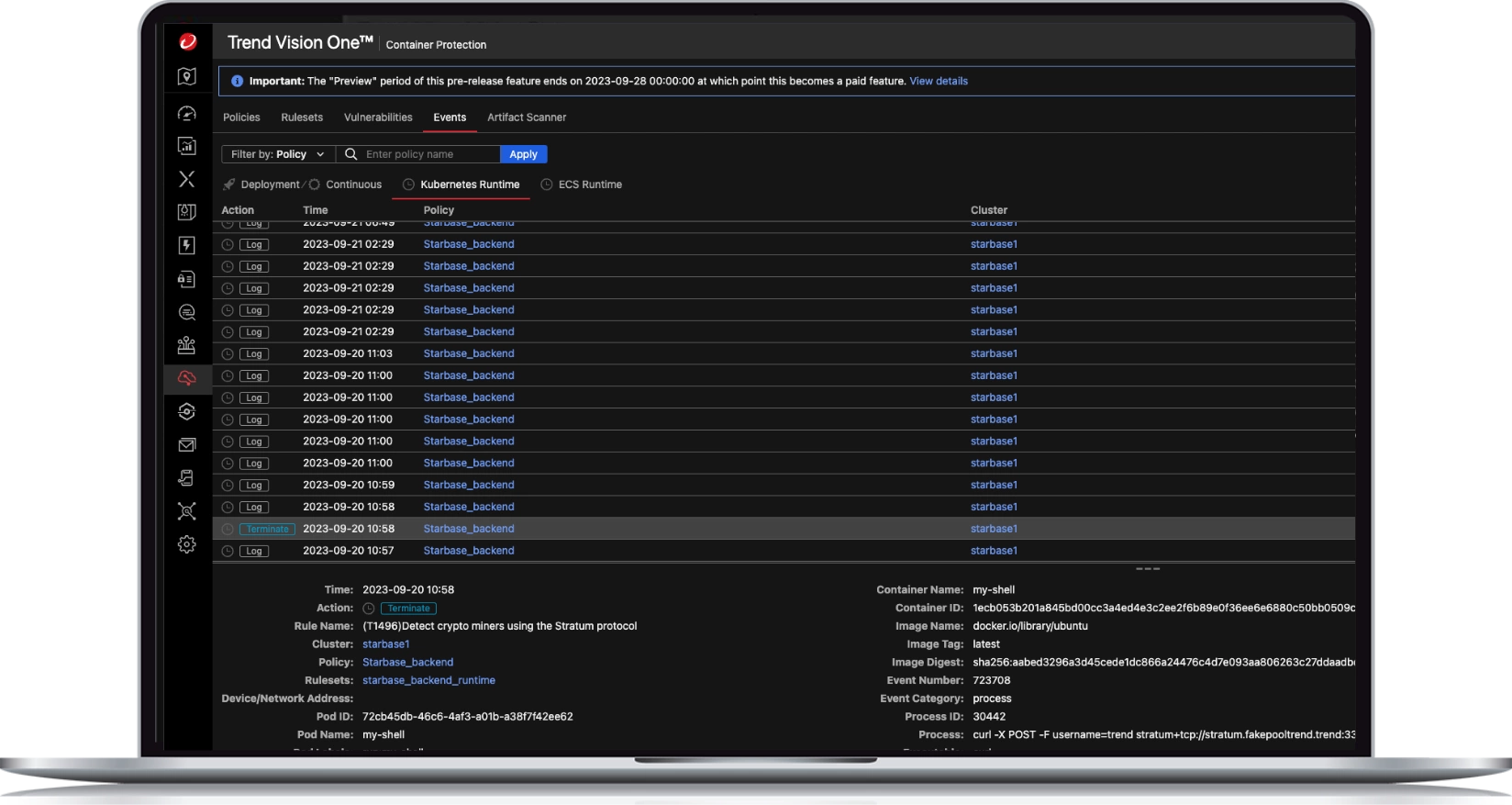
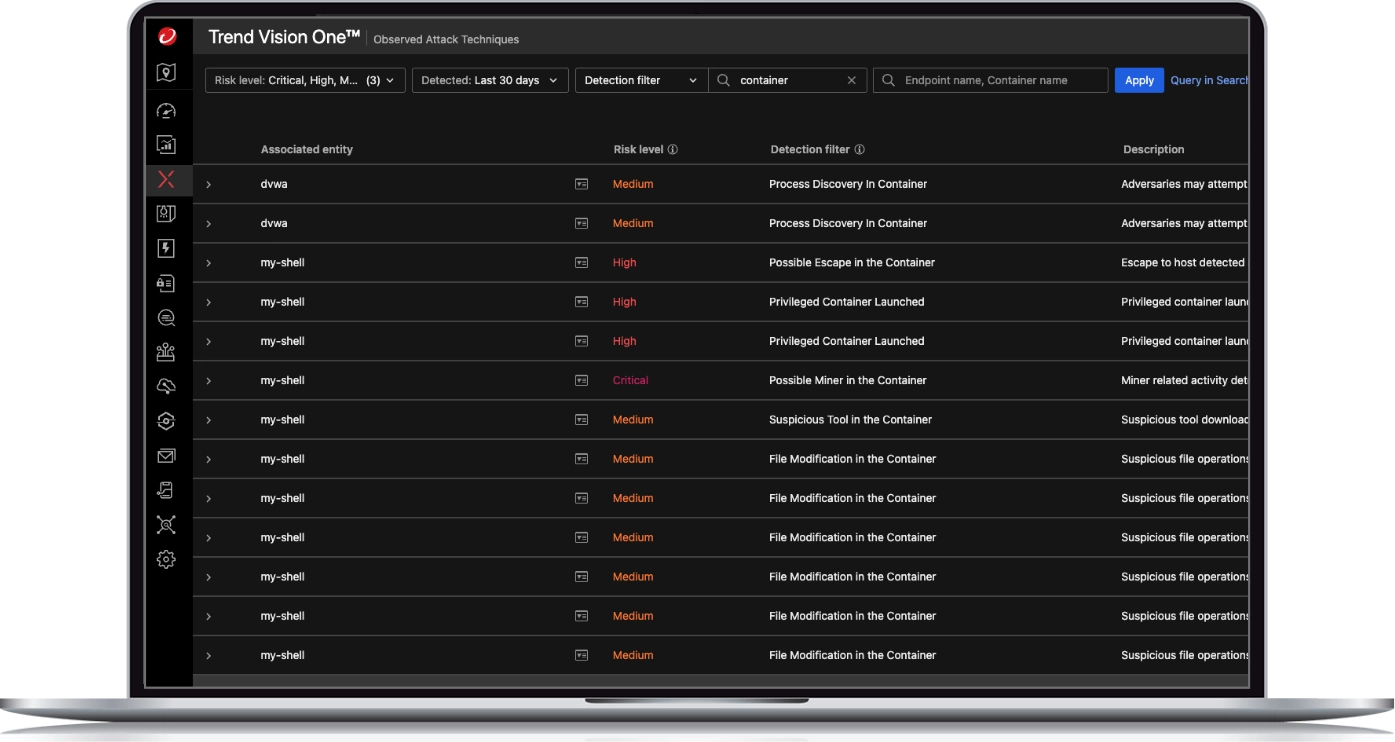
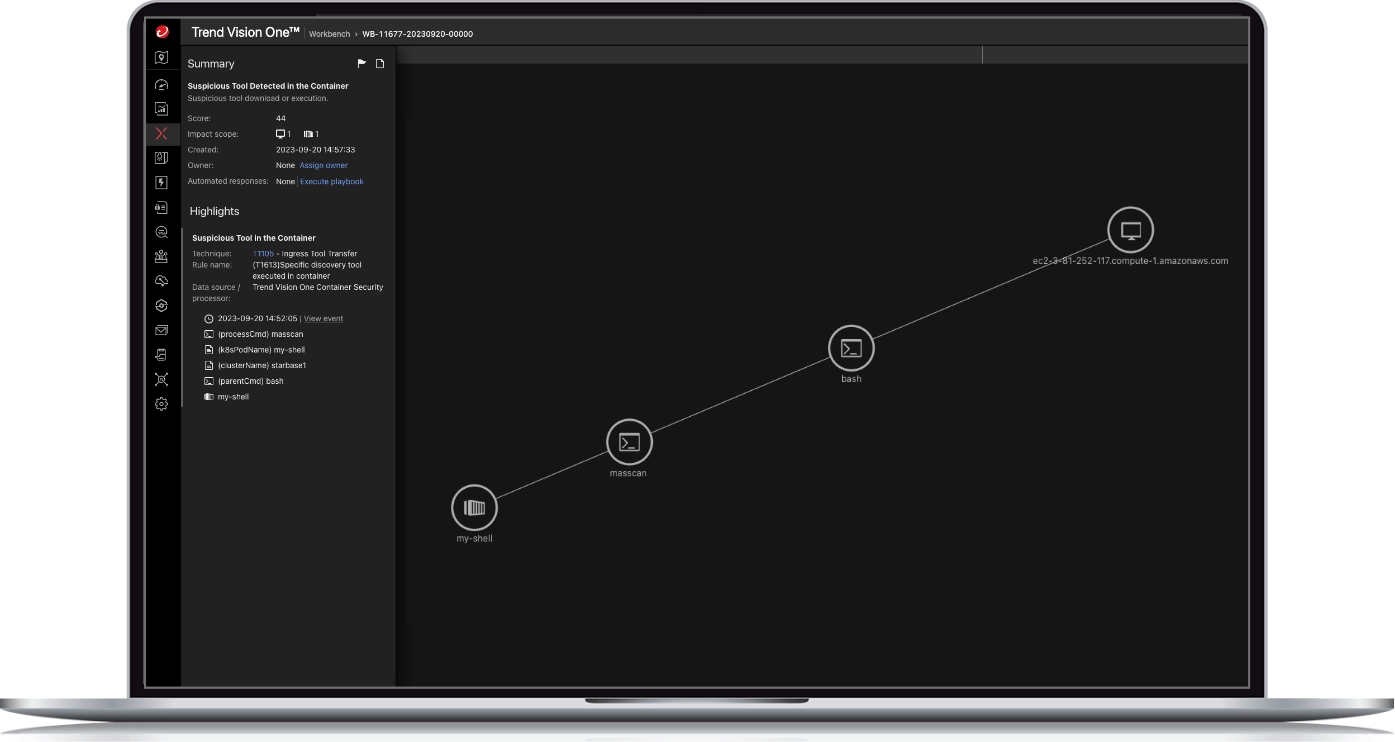
Protection with full visibility, detection, and response
- Get instant visibility of vulnerable containers and container drift with insights aligned with MITRE ATT&CK framework
- Discover and block attempts to run disallowed commands or illegally access files
- Detect, track, and investigate cross-layer threats or activities with Extended Detection and Response (XDR)
Market-leading performance
TRANSFORMING CYBERSECURITY
Get started with Trend Vision One — Container Security