Fileless Cryptocurrency Mining Malware Uses New Technique, Additional Variant Already Spotted
by Miguel Ang, Byron Gelera and Michael Villanueva
As ransomware continues its decline, cryptocurrency mining malware seems to be one of the threats set to take its place in terms of popularity. In addition to cryptocurrency’s increasing real-world relevancy, one of the aspects of cryptocurrency mining malware that make it appealing for cybercriminals is its stealthiness, being able to indefinitely stay in a system undetected.
In fact, many of today’s mining malware take it even further by managing to infect machines as a fileless threat. Fileless attacks allow the attackers to hide the malware in memory, making analysis and forensics difficult.
We recently discovered a fileless cryptocurrency mining malware (Fileless-DASKUS) variant back in February that uses PowerShell (PS) to perform its routine. Unlike the case of TROJ64_COINMINER.QO discovered in August 2017, this particular mining malware does not use Windows Management Instrumentation (WMI). Instead, it uses the registry technique that we’ve seen in other established fileless malware such as KOVTER and ANDROM.
The diagram below shows the mining malware's infection chain: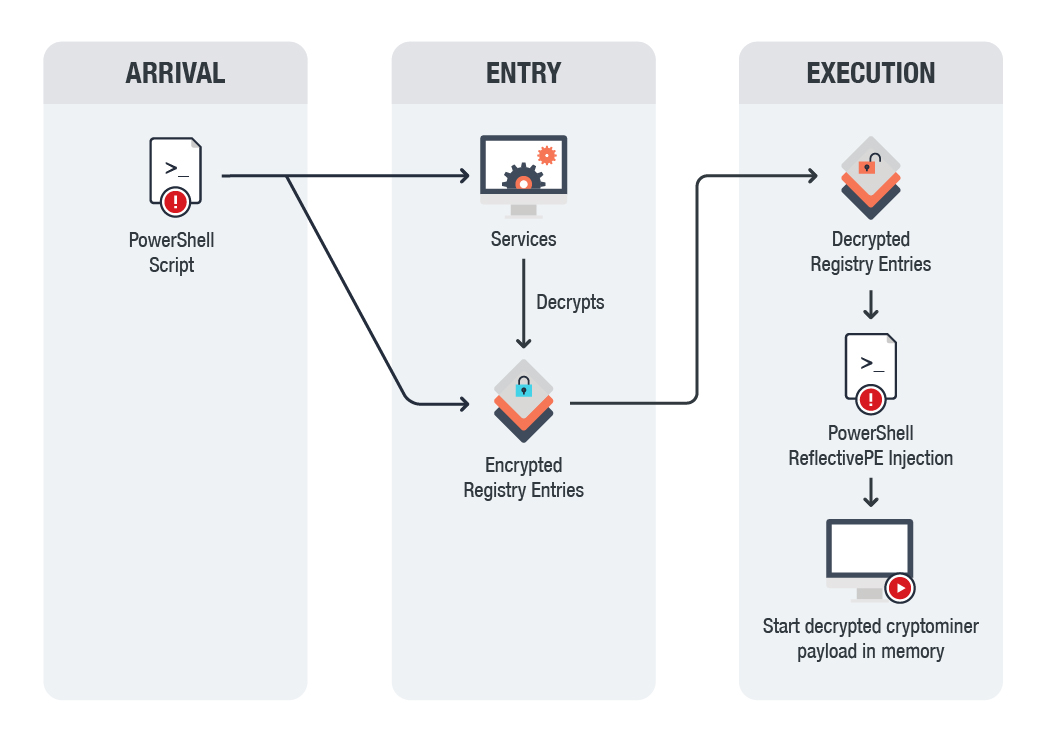
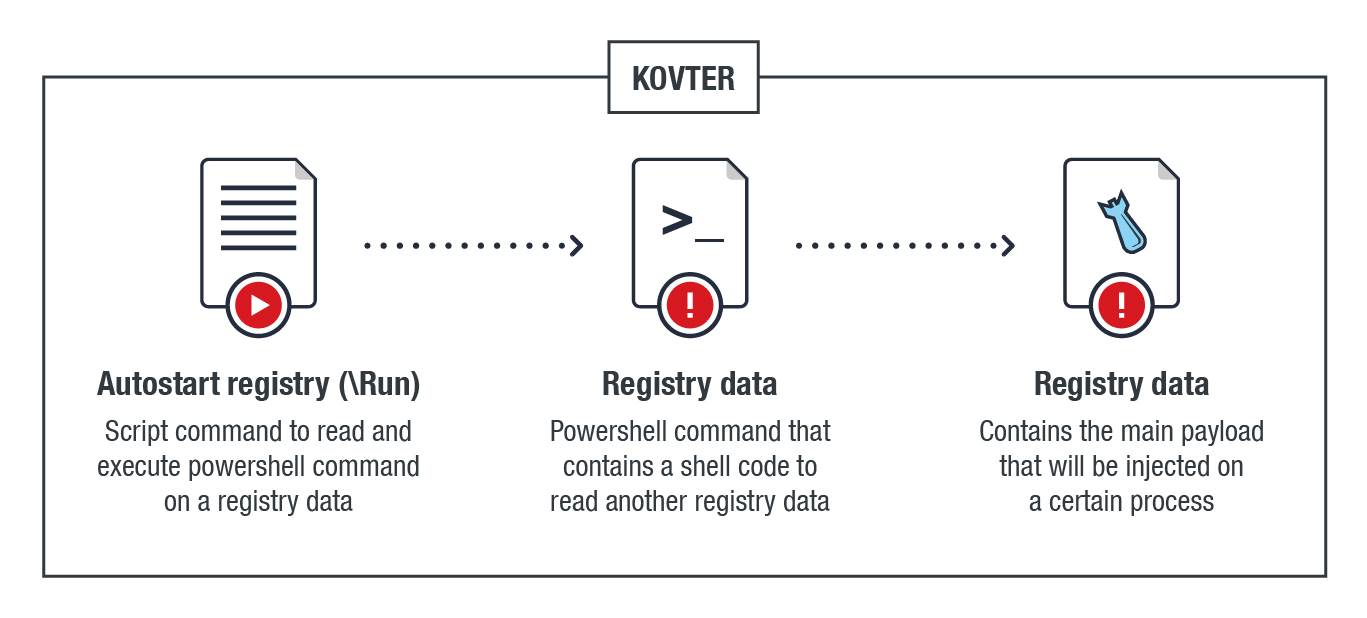
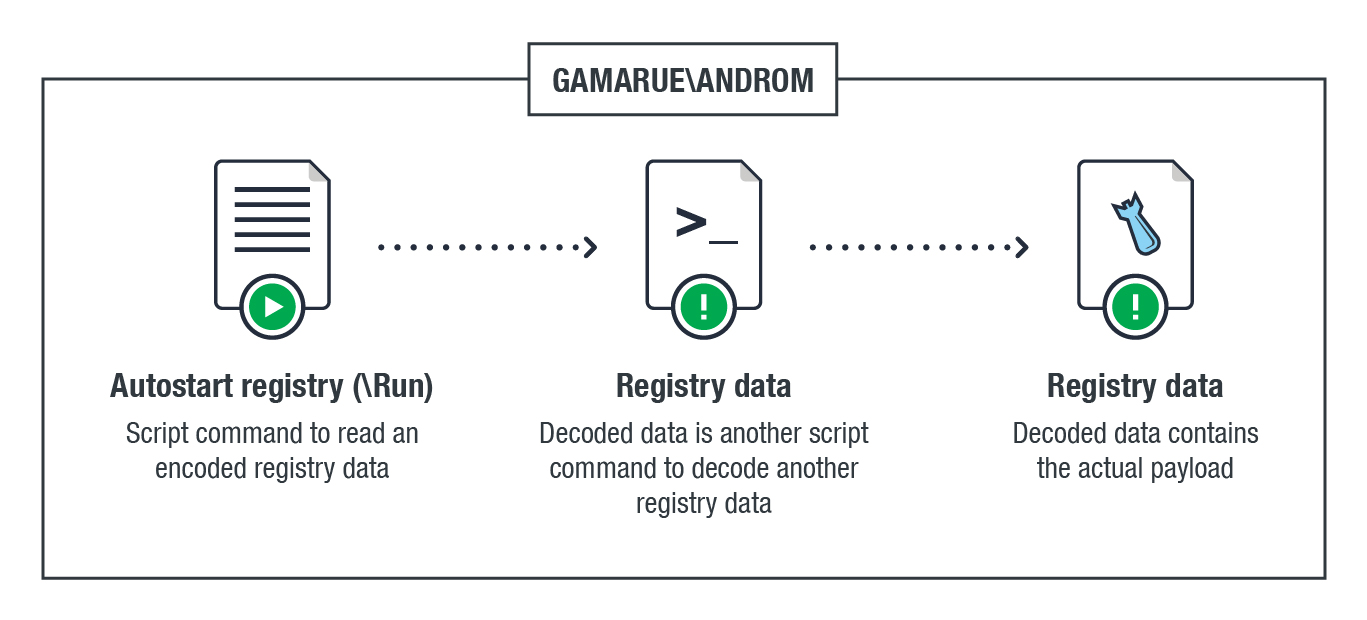
The registry technique of the malware’s routine as compared to both KOVTER and ANDROM are summarized below: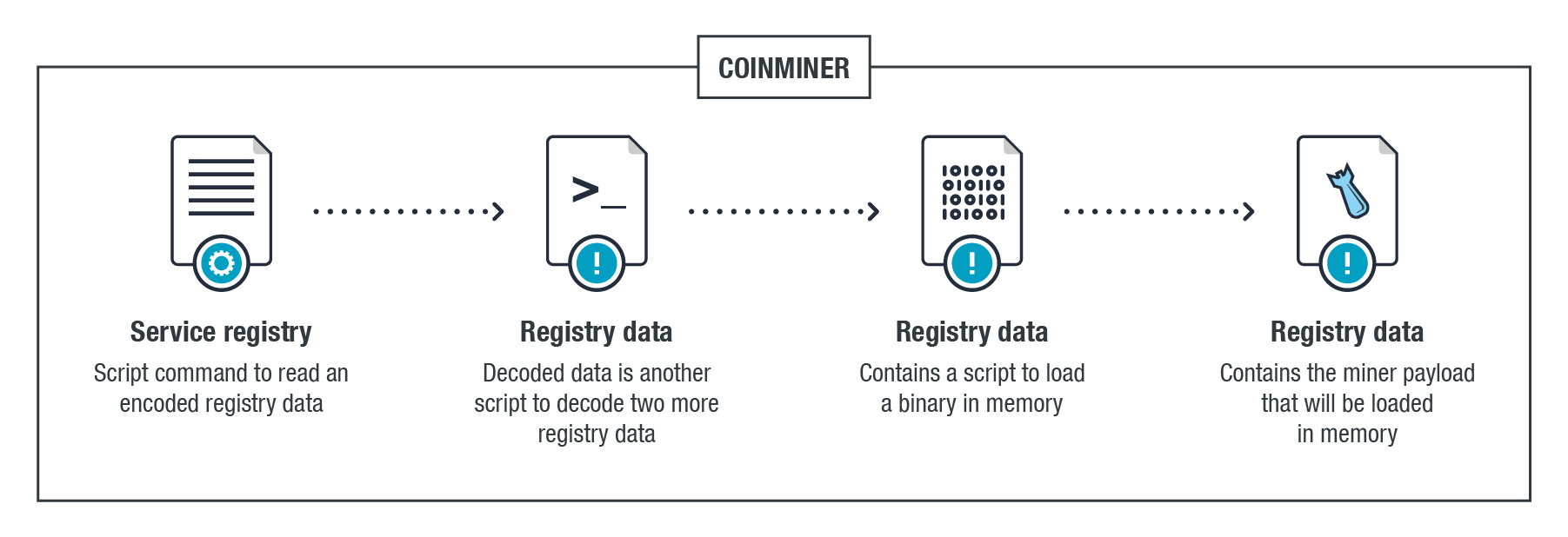
The malware comes from a malicious script (Coinminer_MALXMR.DB-PS) that creates three encrypted registries, which also includes their decryption routines, a PS reflective portable executable (PE) loader that is used for process injection, and the actual malicious code.
To execute the actual payload, the initial script creates the service that will decrypt the first registry containing the decryption code of the other registries. It then uses the decrypted reflective PE loader to load the actual coinminer in memory.
However, it should be noted that this variant looks for the coinminer malware's config file; therefore, it is not entirely fileless.
In addition to the malware we found in February, we also encountered a variant that implemented some changes to its code, making it fully fileless: in this instance, the configuration is integrated in its command line upon decryption and execution.
From what we can see with this miner, it seems to be using an older fileless infection technique, perhaps signifying that the authors are looking to the past to find more efficient methods of spreading their malware.
Defending against fileless malware
While fileless malware is difficult to detect, we still recommend that both users and organizations implement firewalls and other solutions that can monitor inbound and outbound network traffic to prevent fileless malware from infecting endpoints.
In addition, given the use of PowerShell in this scenario, consider following the proper implementation measures. Disabling PowerShell itself could also be considered if absolutely necessary.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report The Road to Agentic AI: Navigating Architecture, Threats, and Solutions
The Road to Agentic AI: Navigating Architecture, Threats, and Solutions