Adobe Reader and Acrobat CVE-2009-4324 Vulnerability
Background of the Attack
A series of attacks that exploited critical vulnerabilities identified in Adobe Reader and Acrobat recently surfaced at around the same time HYDRAQ was discovered. The widespread use of Adobe software, particularly Adobe PDF Reader, has led to increased concern. The attack leverages the CVE-2009-4324 vulnerability Adobe announced in December 2009, which enables malicious .PDF files to load an obfuscated JavaScript code if users are tricked into opening them in a JavaScript-enabled system.
What happens in this attack?
Users may either receive spammed message or unknowingly download a specially crafted .PDF file from a malicious site. Cybercriminals could then exploit the CVE-2009-4324 vulnerability in their Adobe Reader and Acrobat software, which may allow remote users to execute a malicious code embedded in specially crafted .PDF files on their systems. This also uses the vulnerability to drop other malware onto the affected system, which connect to a remote URL.
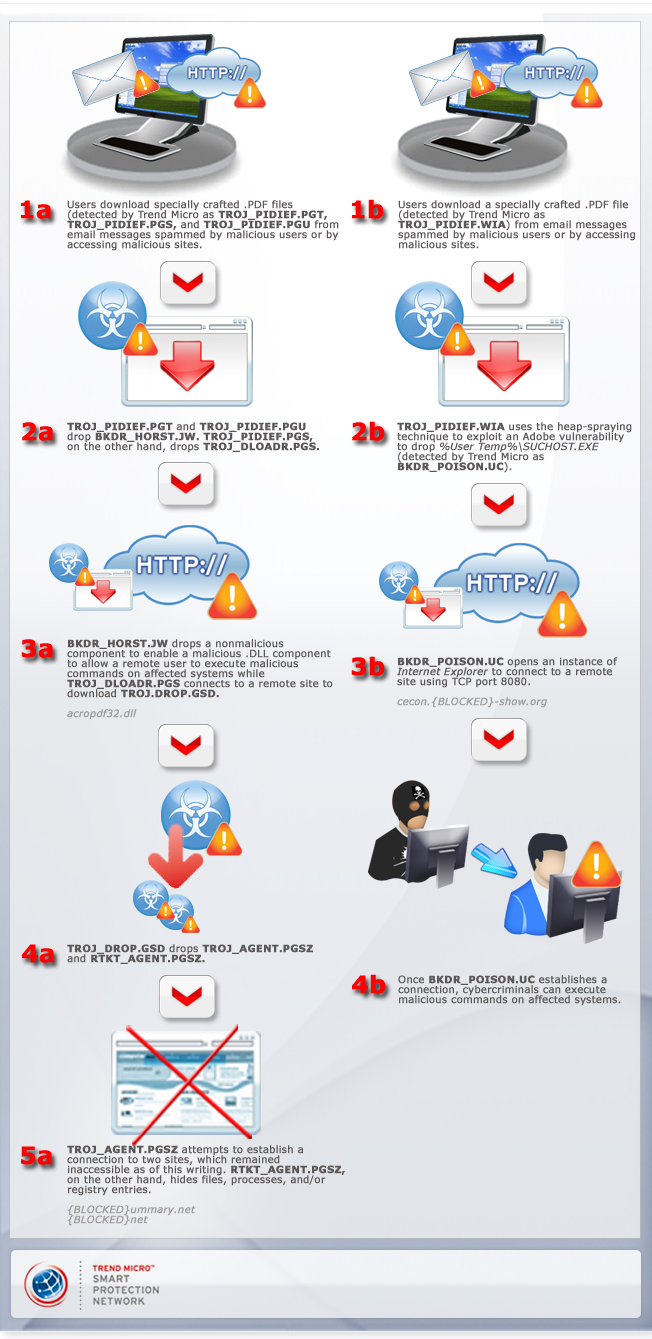
The diagram above illustrates two recent versions of this attack, both of which appeared after Adobe released a security bulletin in January. This is a developing story. These exploit codes take advantage of CVE-2009-4324 to connect to URLs to download other Trojans onto affected systems.
What are the known detections in this attack?
The first two rounds of vulnerability attacks occurred in December and in the early part of January before Adobe the released the update. The first zero-day attack led to the detection of TROJ_PIDIEF.PGT, TROJ_PIDIEF.PGS, and TROJ_PIDIEF.PGU. The second attack, which occurred a few days before the update's release, led to the detection of TROJ_PIDIEF.WIA, which dropped BKDR_POISON.UC. The most recent attack ensued after the update's release, which led to two separate infection chains, each beginning with TROJ_PIDIEFX.F and TROJ_PIDIEF.SHK.
Why is this attack noteworthy?
Adobe already released an update on January 12 to resolve a use-after-free vulnerability in Multimedia.api that could lead to remote code execution. However, it remains highly probable that a significant number of user systems remain vulnerable to these exploits until they update their systems with Adobe's latest patch. It is also worth noting that this attack used a more sophisticated method of embedding an obfuscated JavaScript code into the .PDF files. The relatively small size of the code made detection difficult and increased the probability of system infection.
Am I at risk?
Considering the increasing use of malicious .PDF files to spread infection, particularly in the Web, everyone who uses systems with unpatched Adobe Reader 9.2 and Acrobat 9.2 and earlier versions is at risk. Furthermore, since malicious JavaScript code plays another crucial role in this attack, JavaScript-enabled systems may be fully exploited.
So what can I do to protect my computer?
An important first step is to download the appropriate Adobe Reader and Acrobat updates to prevent exploit attacks. This would also prevent other applications on user systems from being exploited. Adobe also plans to release an automatic/silent updater that will automatically patch systems even without user intervention to hopefully lessen the number of users who can be victimized by attacks employing exploits for already patched vulnerabilities.
It is also important to constantly exercise caution when opening .PDF files, particularly those attached to email messages from unknown sources or those downloaded from the Web.
Trend Micro has seen a significant increase in the number of malware that arrive as specially crafted .PDF files. Users should likewise consider disabling their browsers' JavaScript feature to avoid any form of obfuscated JavaScript code from running on their systems. Trend Micro product users can further protect their systems by applying IDF Pattern 9037.