Targeted Attack Campaigns and Trends: 2014 Annual Report
 View Targeted Attack Campaigns and Trends: 2014 Annual Report
View Targeted Attack Campaigns and Trends: 2014 Annual Report
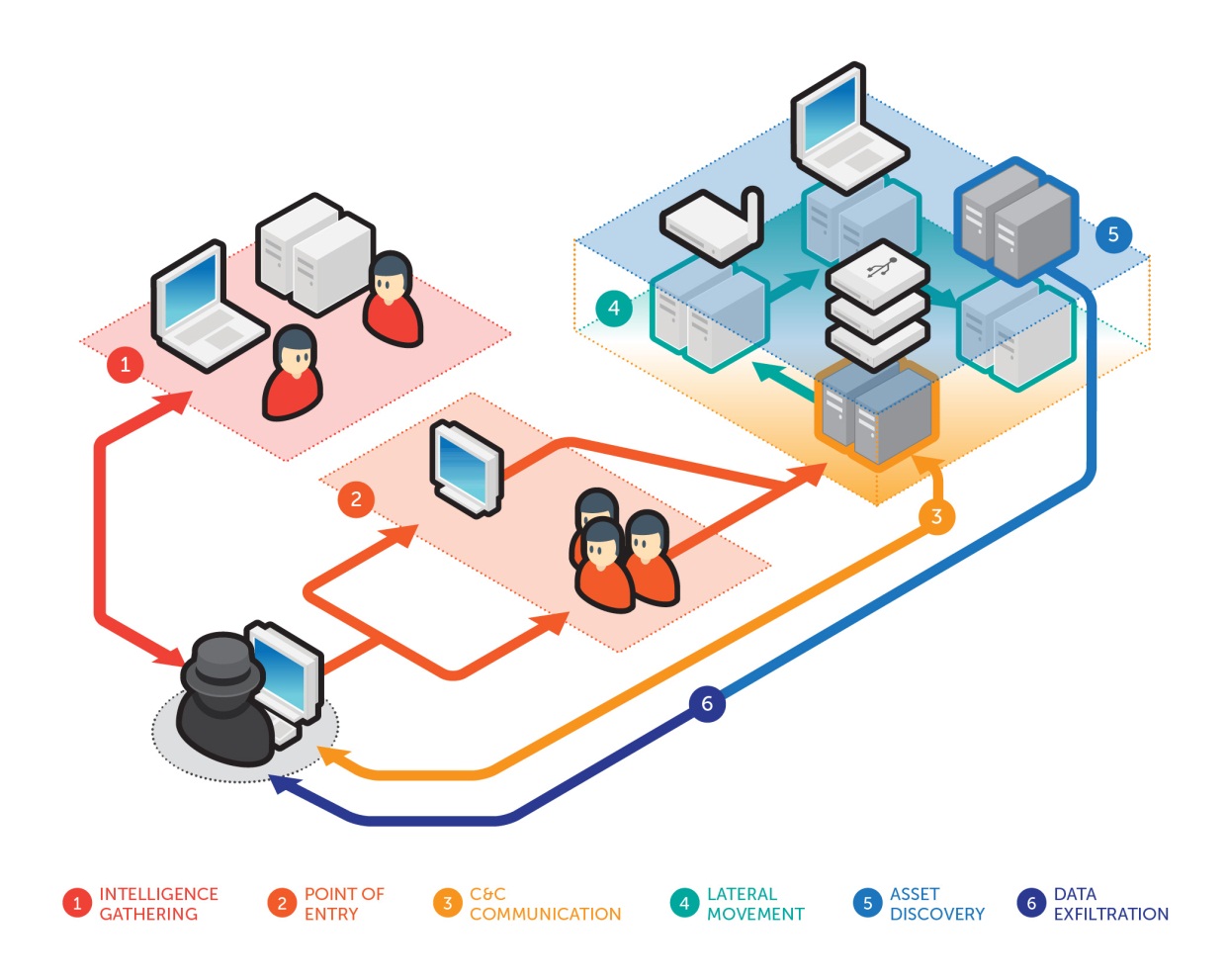
A targeted attack is a type of threat that aims to exfiltrate data from target systems. It is composed of six components: intelligence-gathering, point of entry, command and control communication, lateral movement, asset/data recovery, and data exfiltration. Contrary to some notions, targeted attacks are non-linear; as these are often cyclical in nature with overlapping stages. Data exfiltration is not a one-time event, while C&C communication and lateral movement can occur throughout a campaign. Lastly, maintenance can be considered as the final “stage” of a targeted attack, wherein attackers perform certain activities to make sure incident response or a takeover from other hackers fails.
Our 2014 annual report features the targeted attack cases that Trend Micro analyzed in 2014, including information on monitored attack-related C&C infrastructure. The report also includes details about campaigns we investigated, as well as trends and observations on targeted attack tactics, techniques, and procedures (TTPs):
- Attributing targeted attack campaigns to specific threat actors/groups remained difficult.
Threat actors made it to a point not to leave identifiable traces in target networks, thus making attribution arduous. In 2014, we saw a mix of state and nonstate-sponsored attacks. Examples of the latter include Operation Arid Viper and Pitty Tiger. According to Trend Micro cybersecurity officer Tom Kellermann, a growing number of threat actors use destructive attacks for activism or as part of counter-incident response.
Organizations also have to deal with the probability of insider threats, like in the case of Amtrak breach last year that resulted in the loss of 20 years’ worth of passengers’ personal identifiable information (PII).
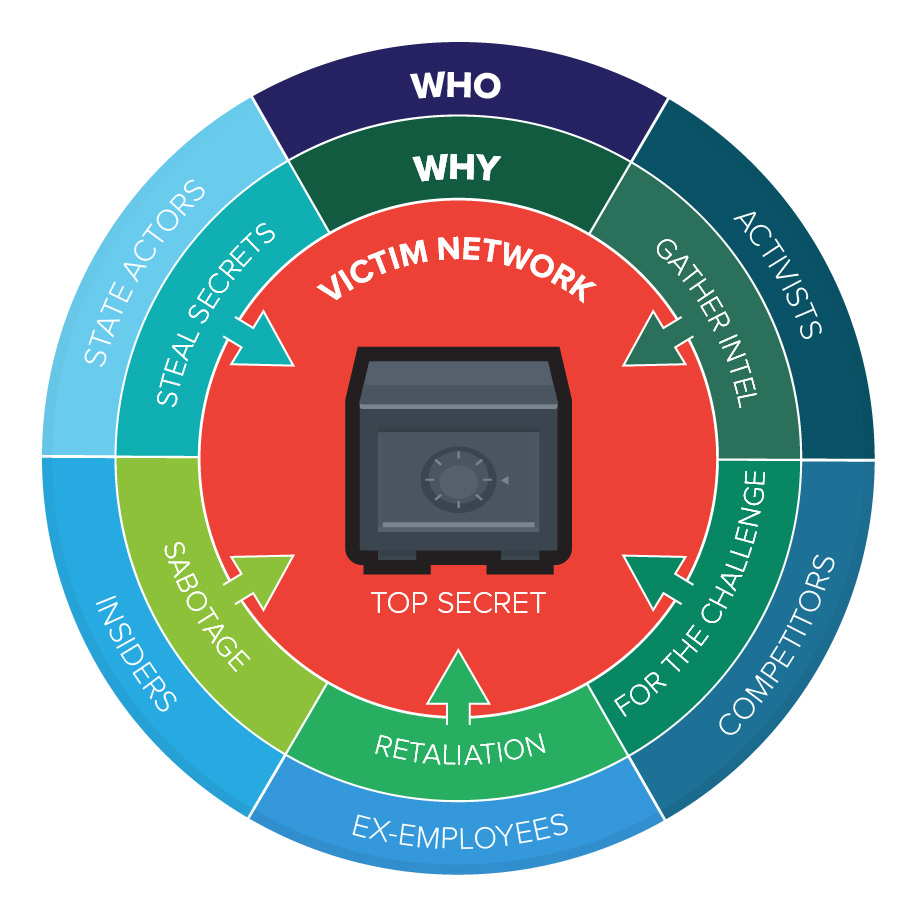
Figure 2. Threat actors’ identities and motivations
- Highly specific configurations did not necessarily stop threat actors.
Apart from targeting commercial and popular software and tools, threat actors also launched attacks using highly specific applications, programs, OSs, and setups. An example of which was the attack that employed GE intelligent Platform’s COMPLICITY. Apple devices were also targeted to infiltrate the network and further the espionage goals of threat actors as seen in Operation Pawn Storm.
- Targeted attack tactics continued to push the envelope with newly identified techniques.
New targeted attack methodologies were observed in 2014. These tactics involved the abuse of legitimate tools like Windows PowerShell and cloud storage platforms such as Dropbox. We also observed that malware that specifically runs on 64-bit systems are becoming prevalent.
[Can you defend your organization from cyber attacks? Play as the company CIO in Targeted Attack: The Game]
- Tried-and-tested and newly discovered zero-day vulnerabilities continued to be exploited in attacks.
We saw evidence of use of both zero-day exploits in targeted attacks along with exploits of older vulnerabilities that have been around for years.
- Targeted attacks remained a global problem.
Based on the cases monitored in 2014, the top countries that hosted targeted attack C&C servers are Australia, Brazil, China, Egypt, and Germany. In our threat monitoring, we also observed that many countries communicated with targeted attack C&C servers which showed that US, Russia, and China were no longer the only favored targets.
- Cybercriminal adoption of targeted attack techniques blurred the boundaries that set them apart.
Cybercriminals emulated techniques commonly seen and associated with targeted attacks because these proved effective in increasing their victim base and consequently, financial gain. For instance, the attackers behind Predator Pain and Limitless, which went after small and medium-sized businesses, were able to earn as much as US$75 million in six months.
To learn more about targeted attack trends from last year, read our full report, Targeted Attack Campaigns and Trends: 2014 Annual Report.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One