Take control of cyber risk
Cyber Risk Exposure Management (CREM), part of Trend Vision One™, proactively reduces cyber risk by discovering all assets, assessing risk in real time, and automating mitigation across any environment. Shift from reactive to proactive security – to build true risk resilience.
Why Cyber Risk Exposure Management?
See everything, secure everything
Achieve continuous, real-time visibility of your entire attack surface including unknown, unmanaged, and third-party assets. Eliminate blind spots and map exposures to business impact for better decision-making. Benchmark posture and create custom dashboards for stakeholders.
Fix what matters first
Prioritize risks with intelligent, context-driven scoring that factors in asset criticality, threat activity, and business impact. Predict moves with AI insights and focus remediation on the highest-risk vulnerabilities and exposures.
Automate to stay ahead
Accelerate threat response and remediation with AI-driven recommendations and automated security playbooks. Reduce your mean time to respond (MTTR), freeing up your teams to focus on strategic initiatives.
One solution, one risk picture
Reduce cost, complexity, and tool sprawl by consolidating critical security and risk disciplines like External Attack Surface Management (EASM), Cloud Security Posture Management (CSPM), Vulnerability Risk Management (VRM), Identity Security Posture, Security Awareness and more into one cyber risk exposure management solution. CREM simplifies security and business operations to enable faster, more strategic risk reduction by replacing fragmented point solutions across these domains.
The CREM life cycle: turning risk insight into risk reduction
Achieve continuous visibility, prioritize risks, gain predictive insights, ensure compliance, quantify impacts, and proactively mitigate threats while anticipating adversary moves.
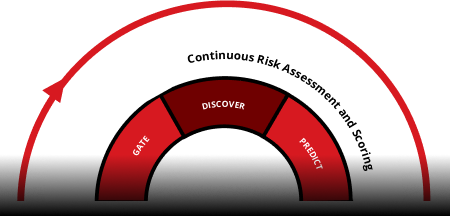
Discover
Discover every asset across your environment – from cloud services to devices and APIs. CREM uses real-time discovery and risk-based vulnerability management to eliminate blind spots. With native telemetry and third-party integrations, it builds AI-powered asset profiles, uncovering hidden risks and ensuring complete visibility and security coverage.
Map your entire attack surface to uncover hidden cyber exposures instantly.
Use AI to forecast threats and simulate likely attack paths.
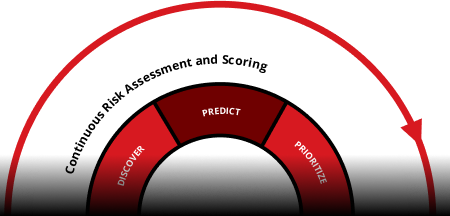
Predict
Anticipate attacks before they happen. By mapping discovered risks to critical assets and visualizing attack paths, CREM highlights choke points and potential exploitation opportunities. Advanced threat intelligence helps forecast where adversaries will strike to help teams proactively close gaps and prevent breaches.
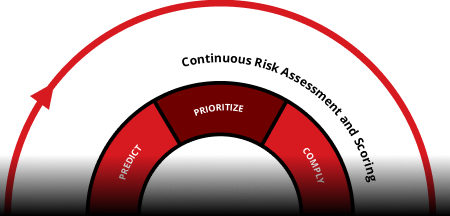
Prioritize
Focus on what matters most, fast. Intelligent, context-driven risk scoring goes beyond basic severity ratings, factoring in asset value, business criticality, and threat activity. Early indicators alert teams to emerging risks, and AI-powered guidance helps direct resources to high-impact issues first, reducing dwell time and strengthening your security posture.
Identify high-impact risks and prioritize remediation based on business context.
Continuously enforce security controls and prove compliance across all environments.
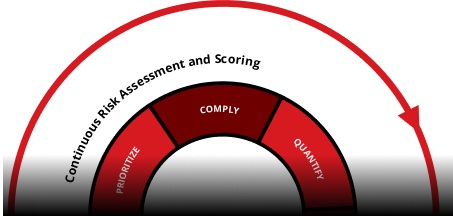
Comply
Make compliance effortless and proactive. Map security efforts to leading global standards such as NIST, FedRAMP, and GDPR. Generate audit-ready reports instantly, automate routine compliance processes, and communicate risk posture with clarity to leadership and stakeholders to reduce liability and show due diligence.
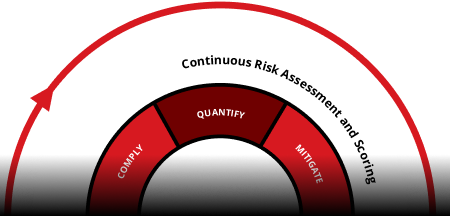
Quantify
Translate cyber risk into business terms with integrated cyber risk quantification. Clearly communicate your risk posture to stakeholders and the board, driving informed, strategic decisions and investment justification.
Translate cyber risk into financial terms to inform executive decisions.
Accelerate response with guided actions to contain and neutralize threats.

Mitigate
Remediate with foresight, speed, and precision. Automatically adjust to changes in risk posture using AI-guided playbooks and orchestrated remediation actions. Whether across cloud, endpoints, or networks, Trend Vision One empowers teams to proactively reduce risk at scale, saving time and enabling focus on strategic security initiatives.
Manage cyber risk exposure from every angle
Security Awareness
Empower employees to recognize and stop threats before they spread. Provide engaging, interactive training that builds a strong human firewall.
Cloud Risk Management
Gain full visibility into cloud assets, risks, and compliance. Proactively identify and prioritize threats to keep your cloud environments secure and resilient.
Risk-Based Vulnerability Management
Harness faster, smarter threat protection with real-time visibility, rapid response times, and the world's best threat intelligence.
Compliance Management
Automate compliance, save time, mitigate risk.
Digital Twin Innovation
Strengthen risk awareness and readiness using digital twins and agentic AI for planning and resilience.
Experience Cyber Risk Exposure Management live
Thwart attacks, assess risks in real-time, and prioritize mitigation actions – lowering risk exposure. Let's show you how live