We have been following an evolving phishing campaign that targets high-ranking company executives since May 2020. The attackers reuse compromised hosts for the phishing pages targeting organizations in the manufacturing, real estate, finance, government, and technological industries in several countries such as Japan, the United States, UK, Canada, Australia, and Europe. As of this writing, we found over 300 unique compromised URLs and 70 email addresses from eight compromised sites, including 40 legitimate emails of company CEOs, directors, owners, and founders, among other enterprise employee targets. We are now working with the respective authorities for further investigation.
Luring victims with compromised infrastructure
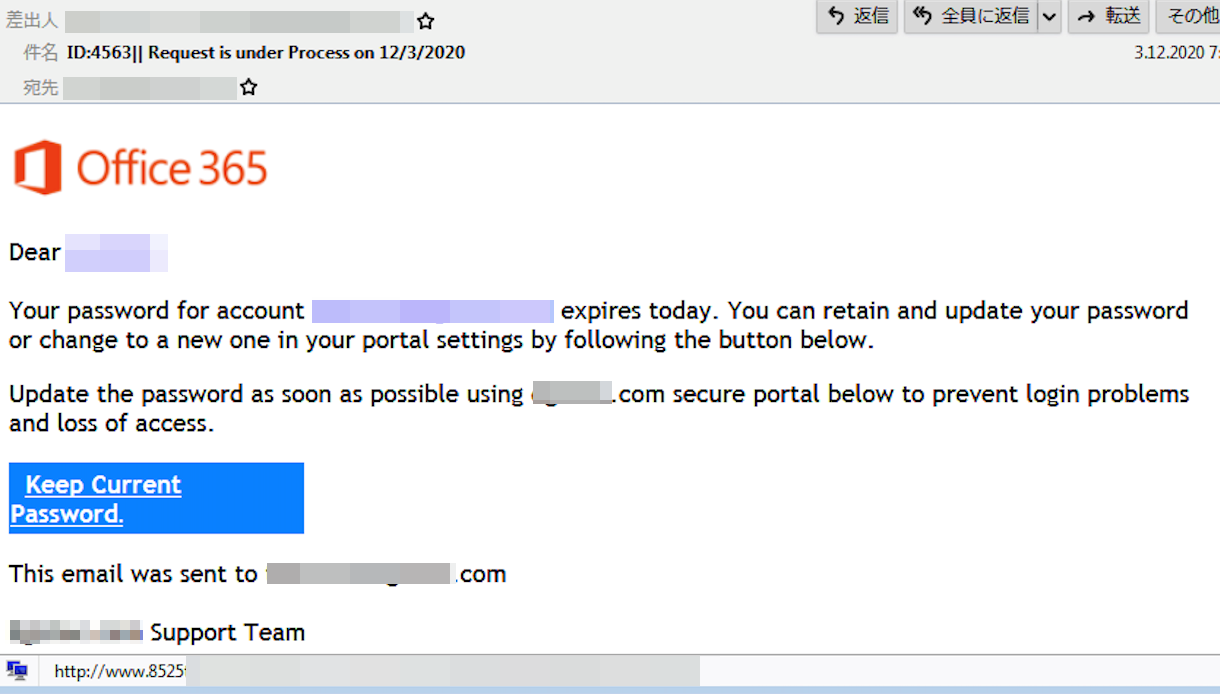
We observed the attackers targeting potential victims with emails containing fake Office 365 password expiration reports as lures. They prompt the targets to click the embedded link in the email if they want to continue using the same password; choosing the “Keep Password” option leads the user to the phishing page.

The attackers are reusing compromised infrastructure and victims’ account credentials to host phishing pages and gain more victims, as briefly reported last year. The kit, which is available for sale, can validate the credentials’ details and accuracy once the victim interacts with the embedded link.
Related to this, during examination of underground activities we identified several advertisements by cybercriminals selling account credentials of CEOs, chief financial officers (CFOs), and finance department members, among others. Those posts were seen in multiple English- and Russian-speaking forums, including an underground forum that seemingly matched with another user’s advertisement. Notably, all posts on the Russian-speaking forums were done in English and using recently registered accounts. We observed these users offering compromised MS Office 365 account credentials and the employees’ respective company positions.
Phishing kit
The campaign orchestrators used the same phishing kit during the campaigns. We observed that some of the sites that hosted the phishing kit were not configured properly. This exposed content of the directory, allowing the download of the phishing kit and associated log files without authentication. This also allowed us to get additional insights on the campaign and find evidence for potential attribution of the kits in their different deployment locations.
This discovery led us to believe that the kit developer’s previous projects served as precursor features that contributed to the Office 365 phishing kit versions subsequently sold in the underground. However, as we further examined the developer’s profile, we found odd behaviors that may warrant further technical and legal investigation.
Emailing using third-party RDP
We looked at the email headers of the lure email samples, examined the SMTP headers, and found an interesting detail: most of the phishing emails were sent using a virtual private server (VPS) from FireVPS.
from FireVPS-RDP (XX.X.XXX.XX) by from FireVPS-RDP (XXX.XXX.XX.XXX) by from FireVPS-RDP (XX.XXX.XXX.XX) by OL1P279CA0064.NORP279.PROD.OUTLOOK.COM (2603:10a6:e10:15::15) with Microsoft SMTP |
FireVPS is a virtual private server (VPS) offering a range of Windows remote desktop protocol (RDP) plans for their respective customers. The emails sent to the victims are sent from the RDP service. We have alerted FireVPS of this and have yet to hear from them.
While scanning other email samples for emails sent from a FireVPS-RDP machine, we found similar phishing email templates and the URL that was sent to a financial department member also contained the recipient’s information and credentials. An online search revealed that the recipient’s profile and email address matched the accurate information listed on his LinkedIn account.
Phishing kit blocklist
We think the phishing kit developer spent considerable time compiling the blocklist included in the kit. It uses an extensive list of domain names and IP address ranges to ensure that access is blocked when accessed by security companies or large cloud providers. We assume the intention is to evade detection by security vendors as the list includes a number of antivirus companies; Google, Microsoft, VirusTotal, and a long list of other cybersecurity and technology companies, as well as public blocklisting sites.

Keeping this in mind, we find it ironic that the kit developer would take this much time to create a blocklist while actively marketing the kit on social network site(s).
Previous versions of the phishing kit
The phishing kit we observed in this campaign is the fourth iteration of the toolkit. Previous versions were noticed and are known to the cybersecurity community, since it was widely advertised in the underground and on social media.
According to the malware developer’s “business” Facebook page, the first version of the phishing kit was released on July 4, 2019, shortly followed by the second version (V2) 15 days after. The third version (V3) was not officially announced on the Facebook page but was observed to be in circulation and could be found through a simple online search.
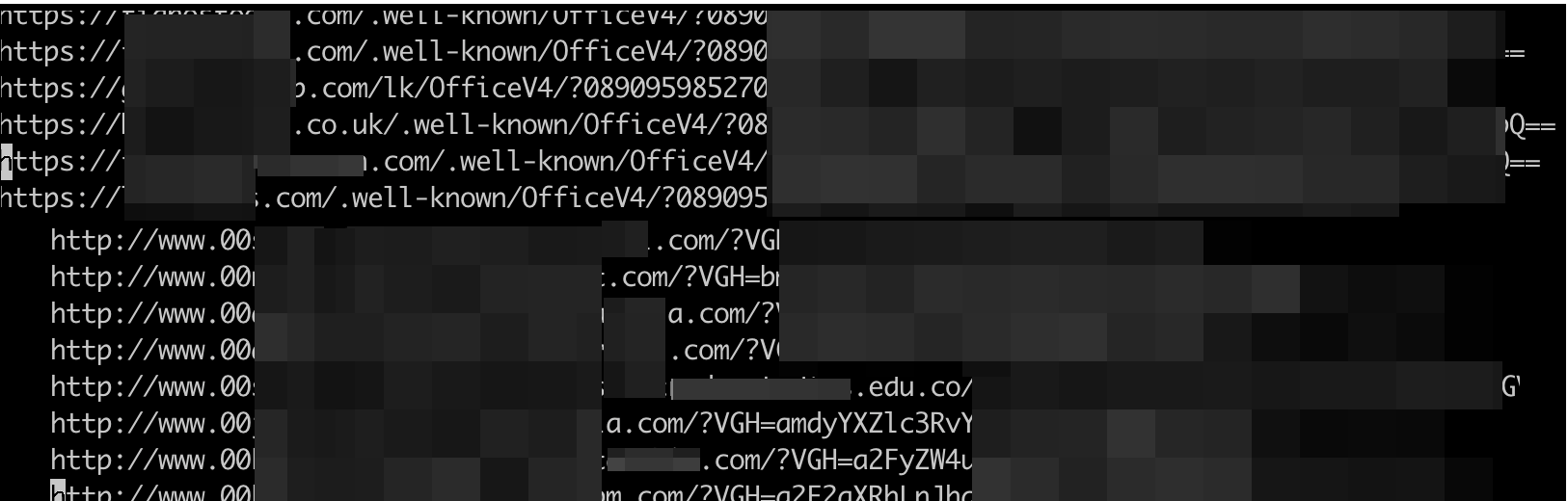
Most of the lure’s content theme focuses on prompting the victims to keep their current passwords. A look at the campaigns' pattern shows that the first layer of the phishing link includes the recipient’s email domain in the compromised URLs' subdomain, followed by the Base64 encoded string of the recipient’s email. (The email does not always have to be base64 encoded, we also have seen landing pages with email being included in plaintext).
As the user chooses the link to keep their password, they are redirected to the phishing pages. We noticed that the current version the compromised URLs’ landing pages started including the keyword “OfficeV4” in August.
By September, the victims’ domain names were still included, but the prefixes were changed from “sg” to “pl,” “00,” and/or “ag.” In another development in October, the victim’s names were being included in the subdomain instead of the respective domain names.
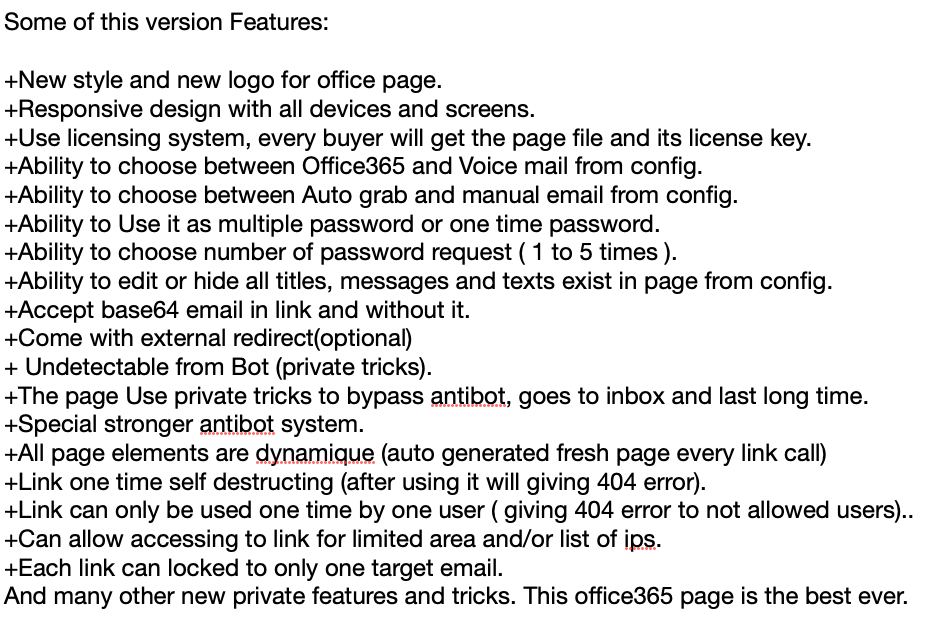
Notable features of the latest phishing kit
Aside from the blocklist, V4’s other features supposedly make the detection of this kit harder. Among them the capability to detect bot scanning or crawling attempts, and provide alternative content when bots are detected. Below are some of the features of V4 as listed by the kit developer on his Facebook page.
Furthermore, the phishing kit is sold with a license, and the obfuscated PHP script calls back to the developer’s system to verify the license’s validity. The phishing page calls back to the license server to check the license key's availability, and a URL/IP to access the license server is seen in config.PHP. Interestingly, config.PHP file is readable on an actual phishing site and contains the license key and the email address in it.
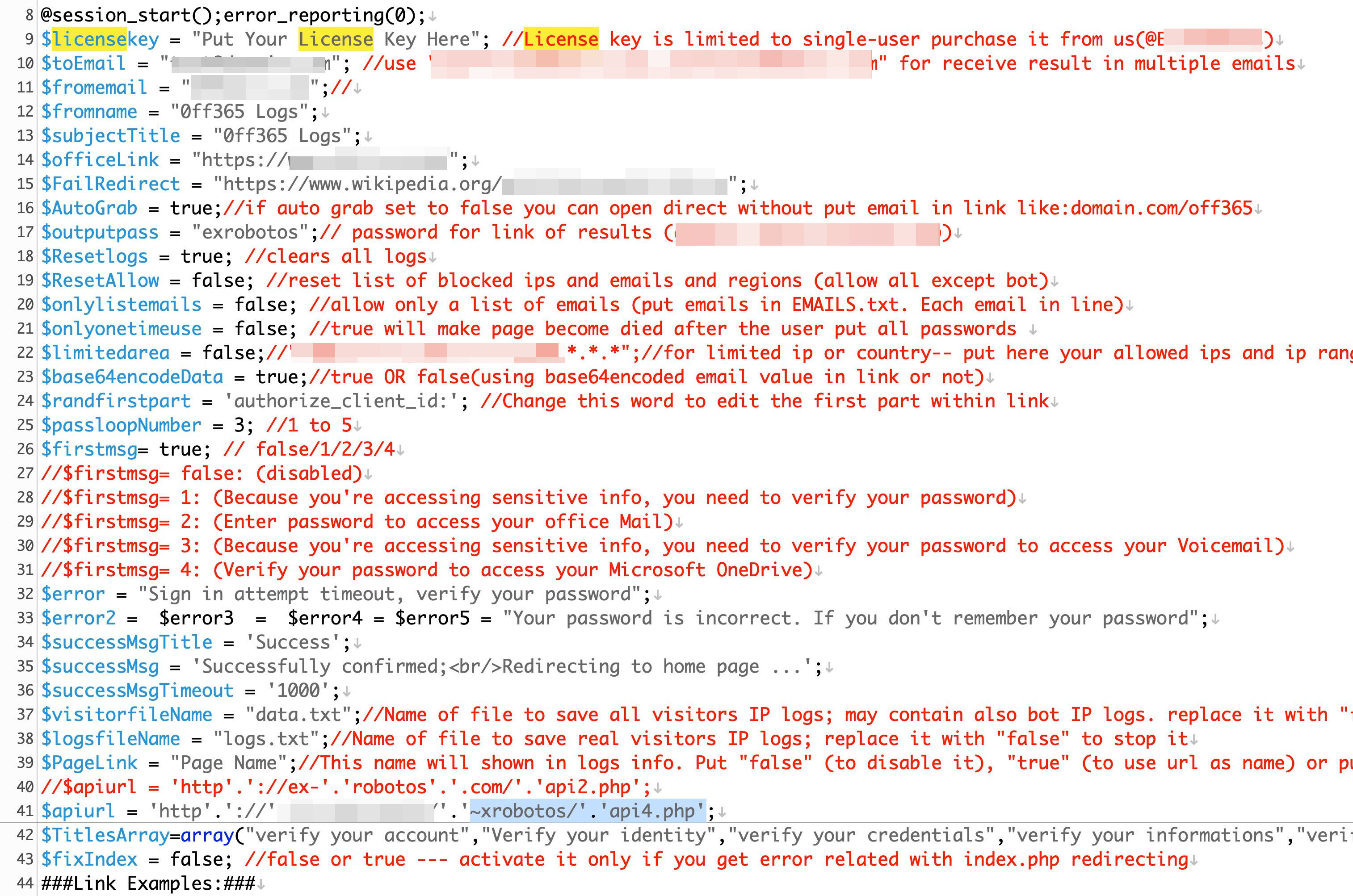
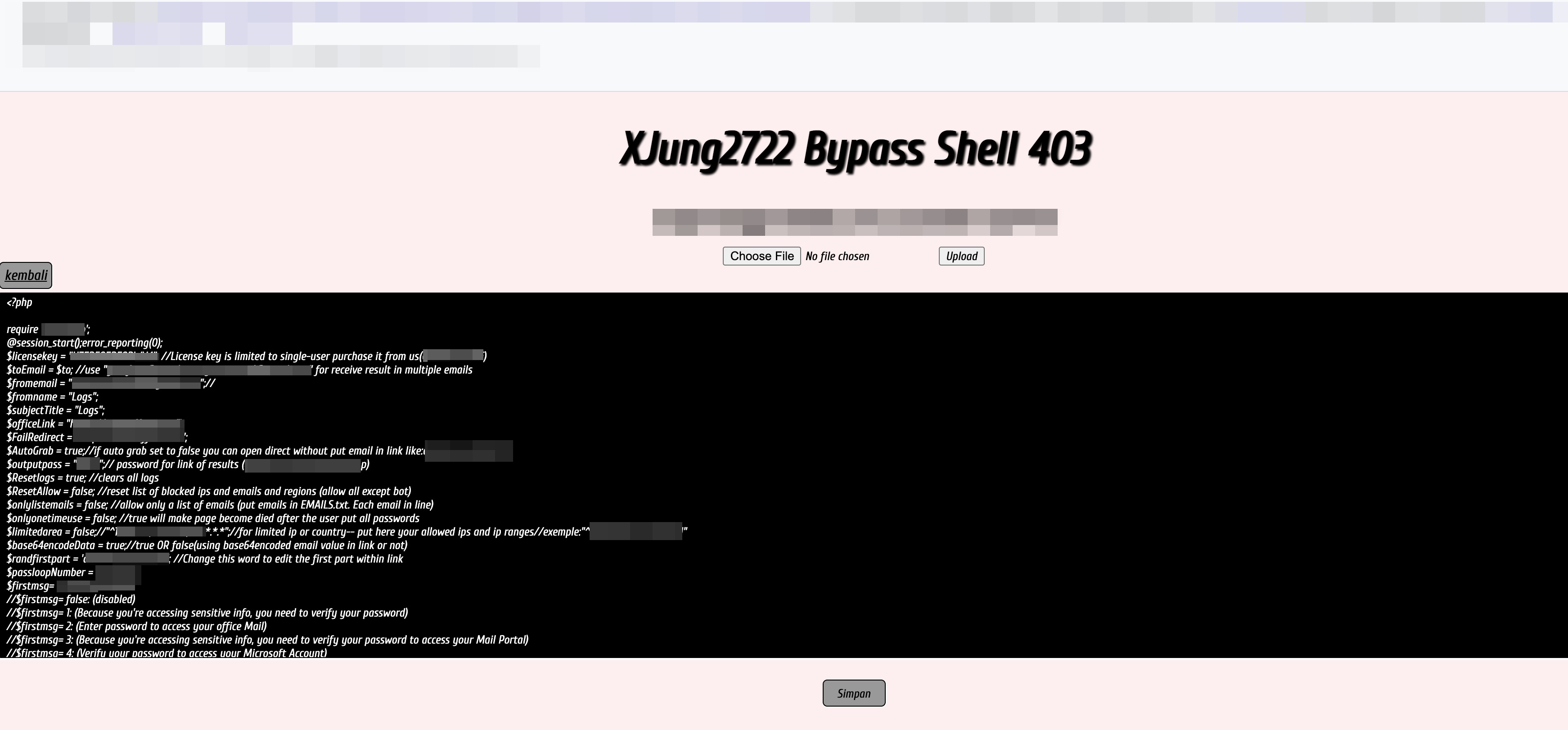
We continue to study the features of this phishing campaign to track the current and potential developments this routine may further include, and to anticipate the changes in its evasion techniques.
Tracking the kit developer
The alleged developer of Office365 announced the V4 phishing kit’s availability on their “business” Facebook page in mid-2020.
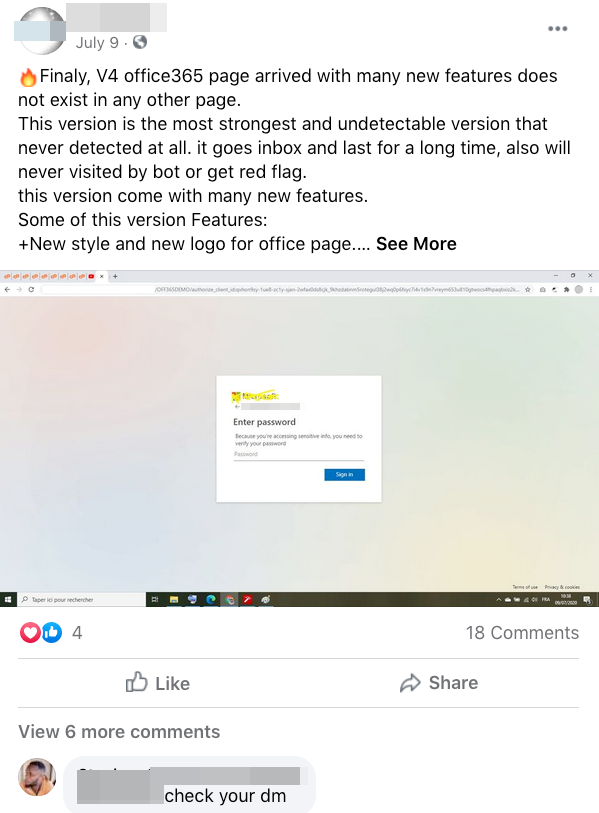
We also observed logs of test traffic from the phishing kit one day before the announcement of V4, wherein almost all logs recorded were from different IP addresses from Morocco.

Several days after the announcement of the V4’s availability, we found an email lure sample; a look at the details of the header revealed that it matched the phishing samples we saw in November and December.
Subject: ID:4563|| Request is under Process on Friday, July 17, 2020 Received: FireVPS-RDP (XX.X.XXX.XX) by VI1PR08CA0138.eurprd08.prod.outlook.com (2603:10a6:800:d5::16) with Microsoft SMTP Server (version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384) id XX.XX.XXXX.XX via Frontend Transport; Fri, 17 Jul 2020 16:46:44 +0000…… |
Looking further at the previous posts in the account also revealed announcements that claimed the user responsible for the fake Office 365 versions as the developer of other credential harvesting kits. While no longer available, the latter kit was capable of rapidly verifying the validity of email addresses; it could have been a predecessor project that potentially contributed to the features of the phishing kit versions sold. Based on other posts on the actor’s social media page, this user also continues to sell harvested credentials aside from the phishing kit itself.
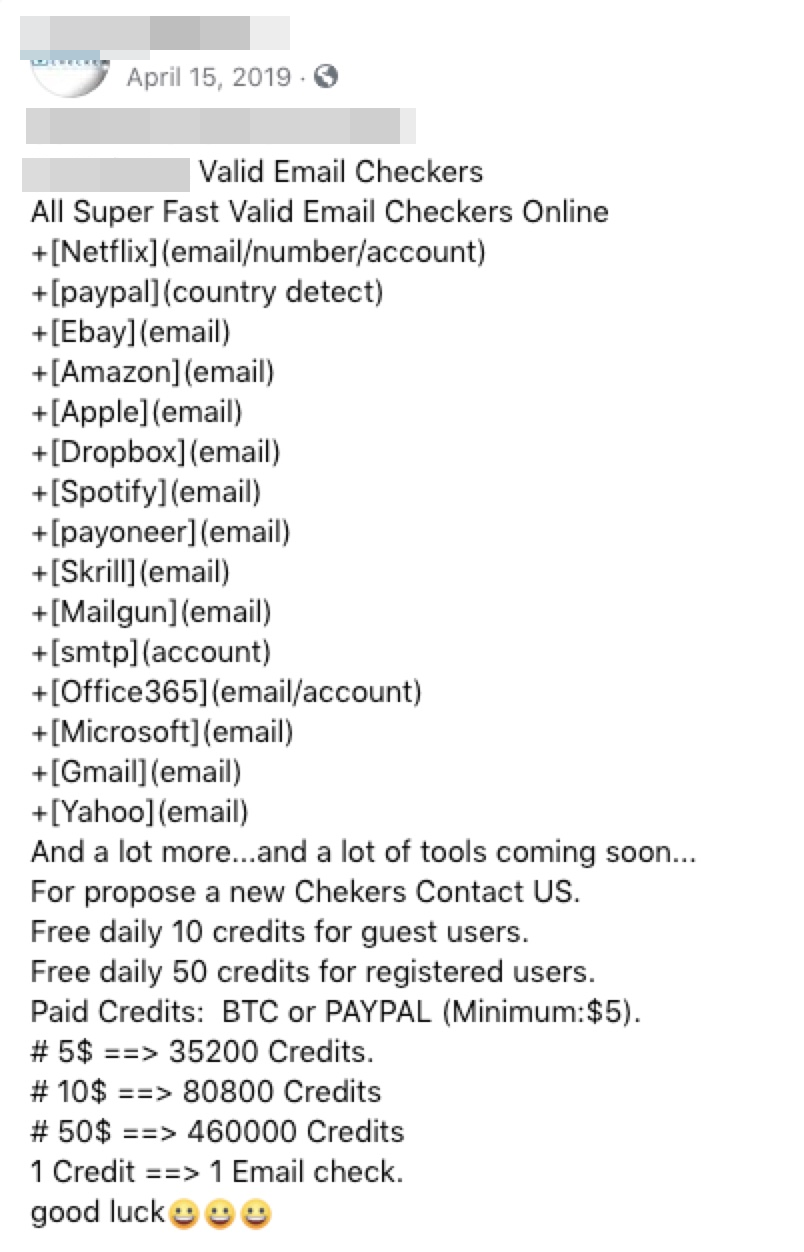
We were able to match the cybercriminal’s business Facebook page to personal pages while scanning for information online. We have informed the appropriate authorities of these details for this investigation.
Possible link to online sellers of C-level accounts
There are numerous users in underground forums selling C-Level accounts. We identified these user handles as sellers of some relevant C-level accounts across different forums, pricing these credentials ranging from $250 to $500.
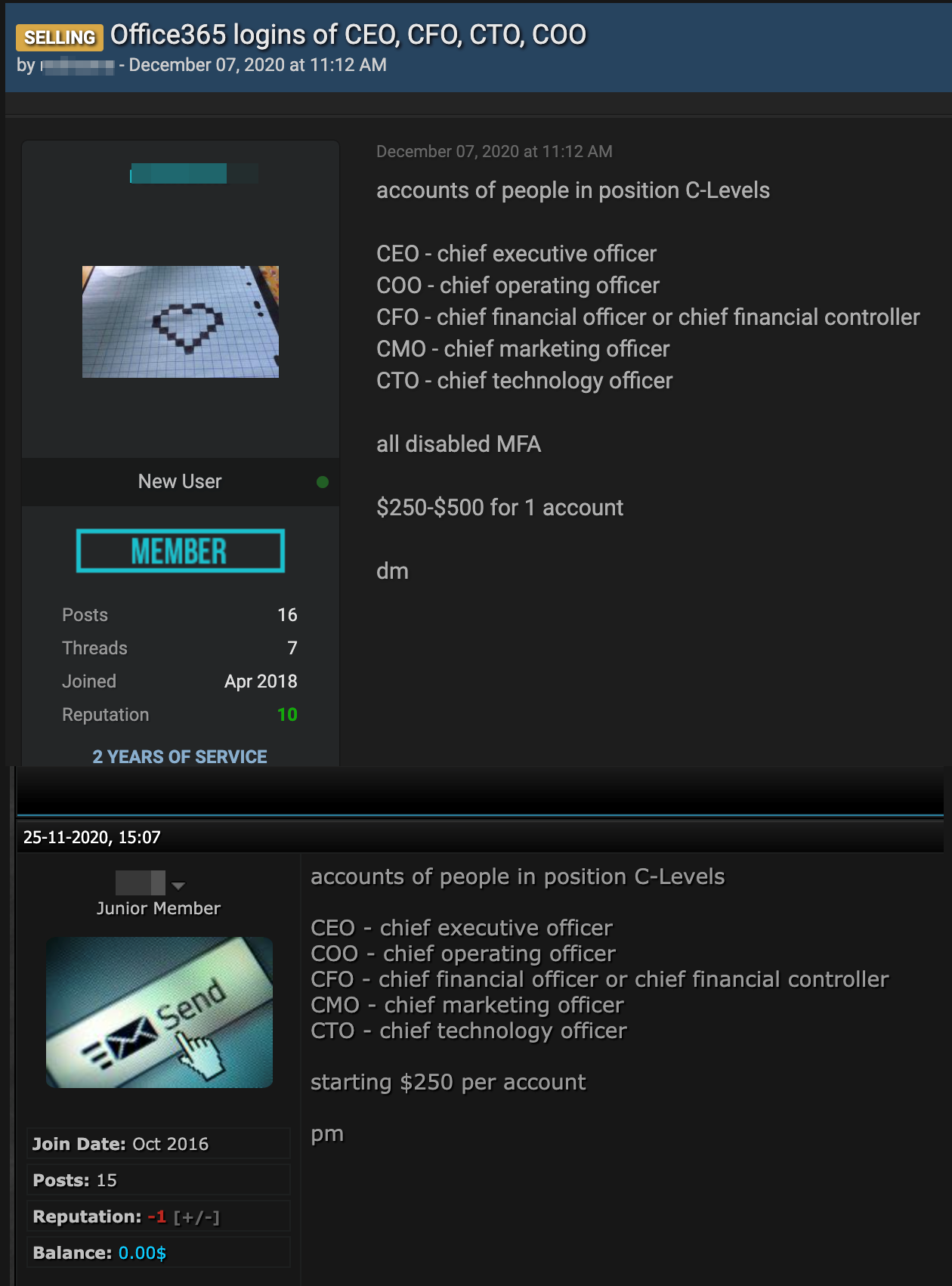
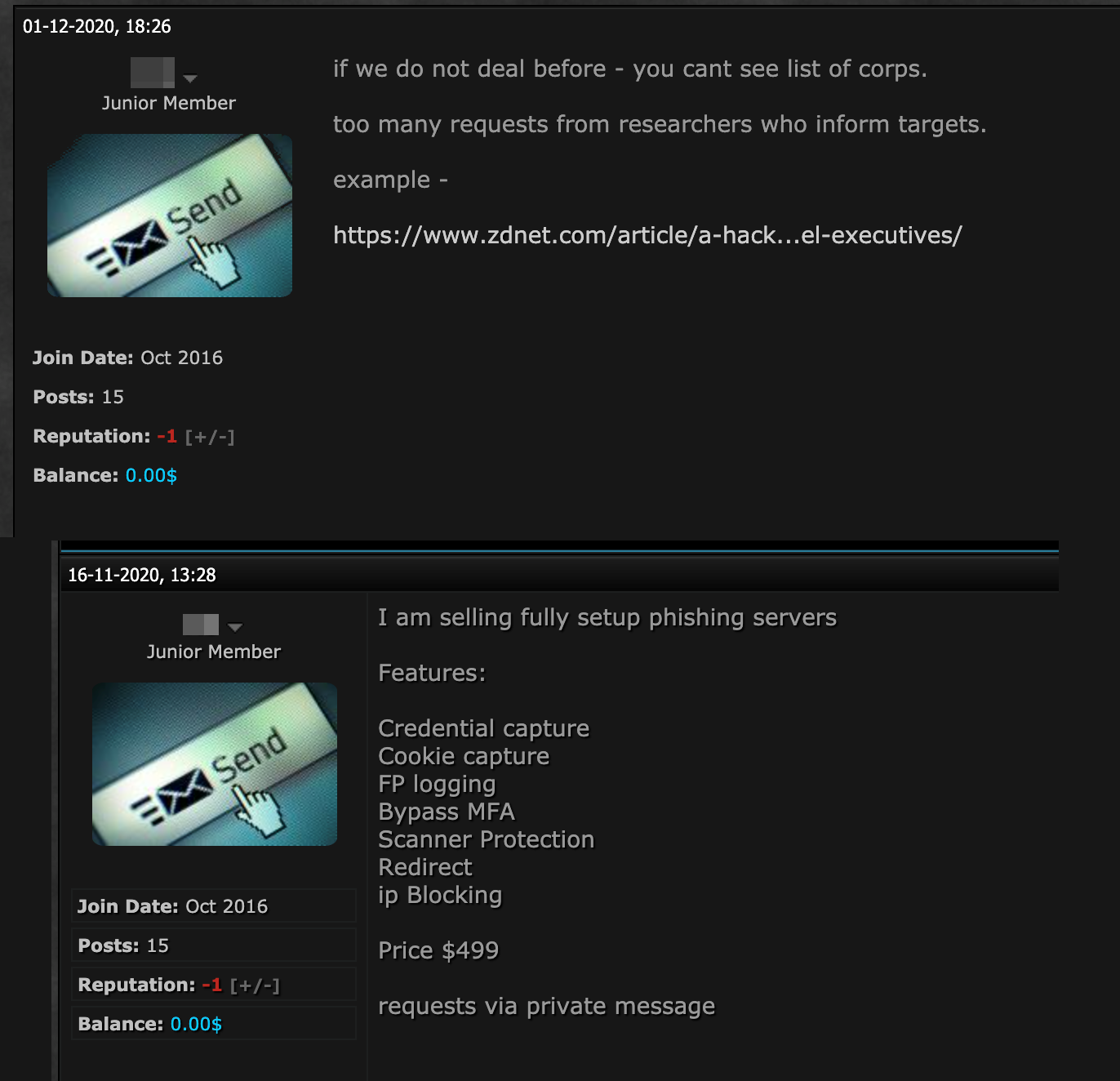
We found it interesting that the user mentioned the published article regarding selling C-level credentials and requests to deal only with users or customers he had previous transactions with. New customers are automatically prohibited from viewing the list of affected companies and credentials. The user also sells a phishing routine targeting servers and identifies its features such as cookie capture and multi-factor authentication bypass. Interestingly, the same handle sells both; the tool for credential harvesting and (two) collected accounts are priced approximately the same, similar to the alleged phishing kit developer’s offers on social media.
Potential targets and victims’ data
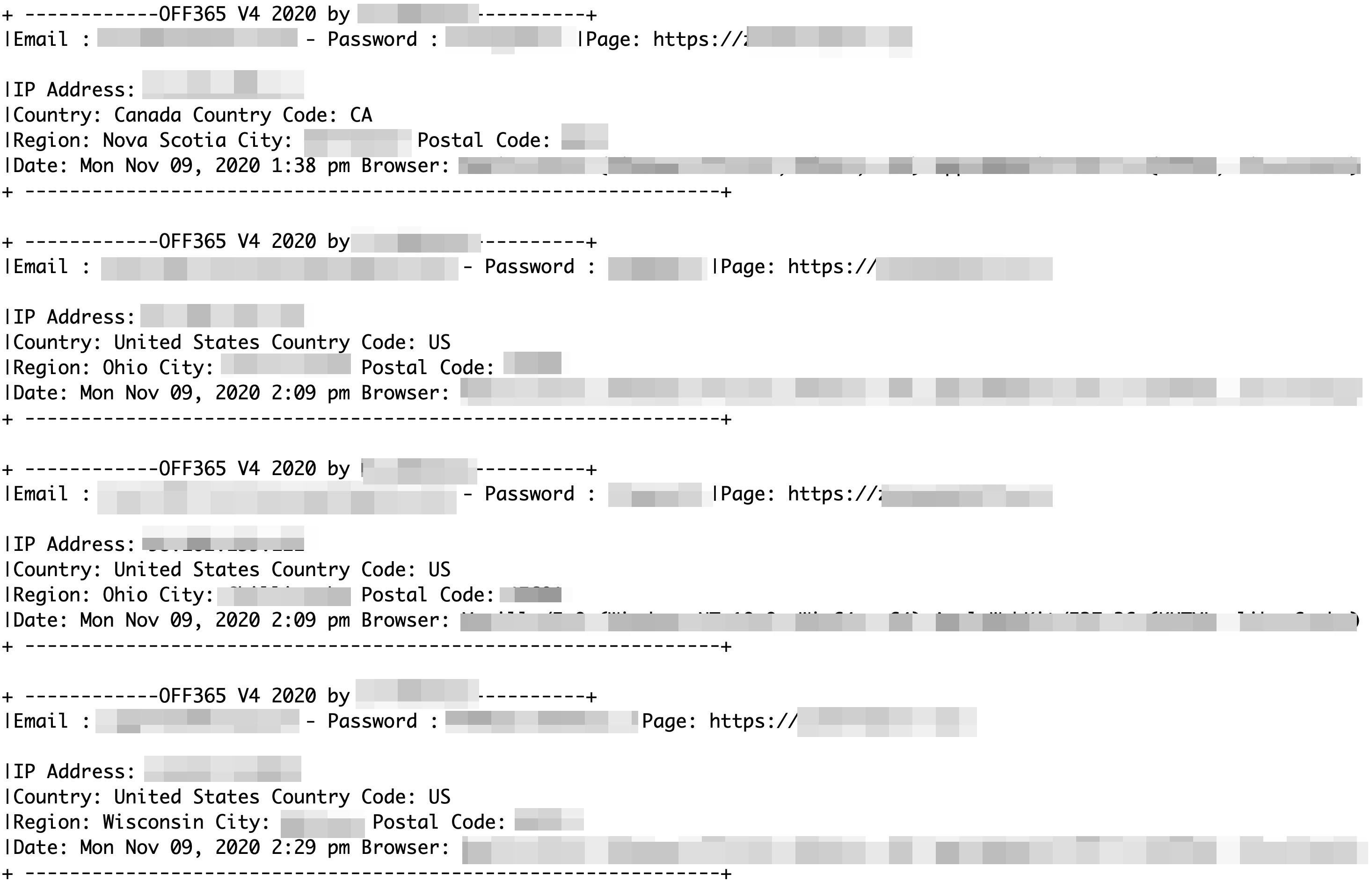
Analysis of the data from the misconfigured sites’ collected log files revealed that the stolen credentials came from eight compromised phishing sites hosting the malicious Office 365 V4 kit as of this writing. We found each site to be possibly made by different phishers for different phishing campaigns of varying scale and scope. One campaign targeted only company CEOs, presidents, and founders in the US, while another campaign targeted directors and managers from various countries such as the US, UK, Canada, Hungary, the Netherlands, and Israel. In addition, it appeared that the phishers mostly collected targeted email addresses from LinkedIn.
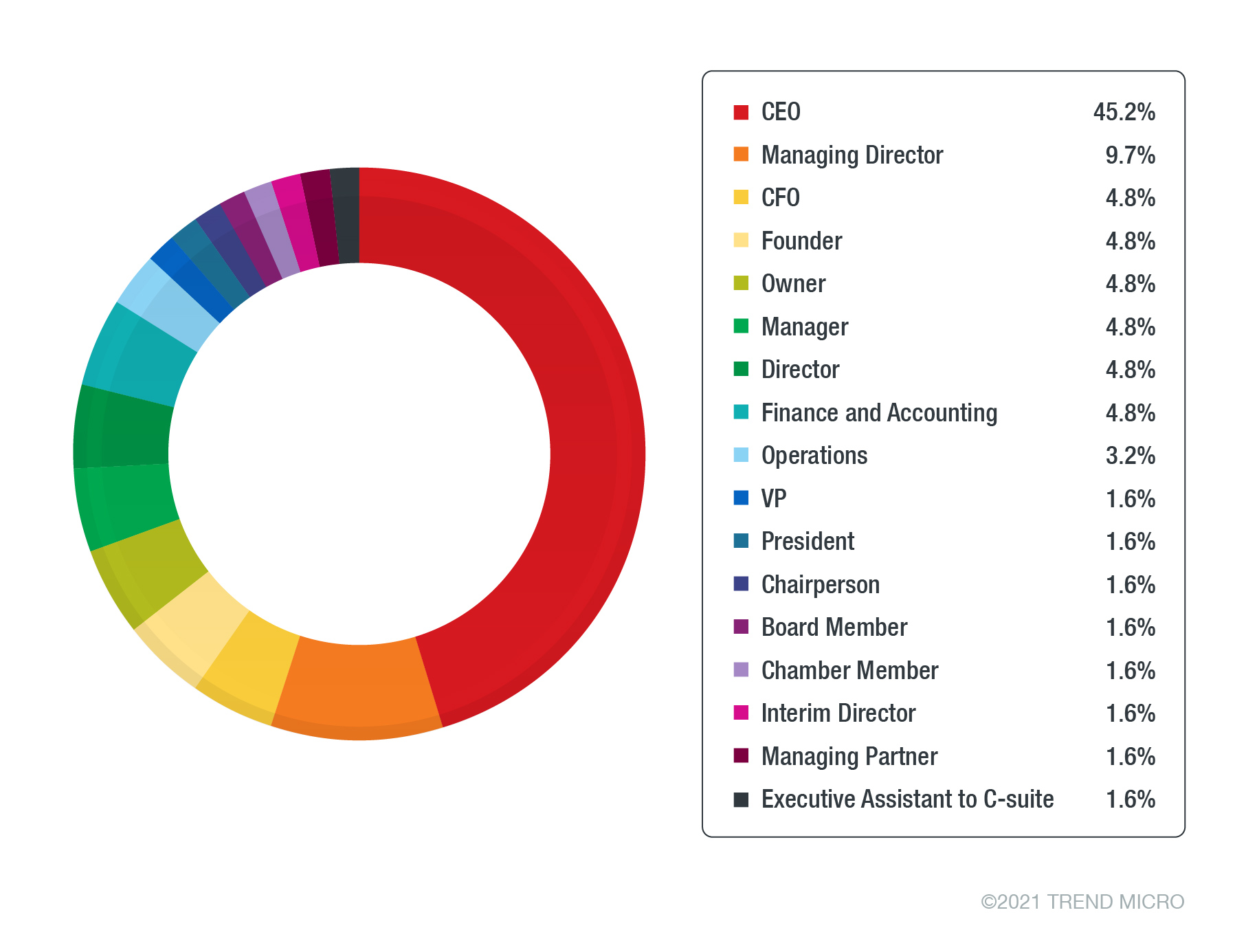
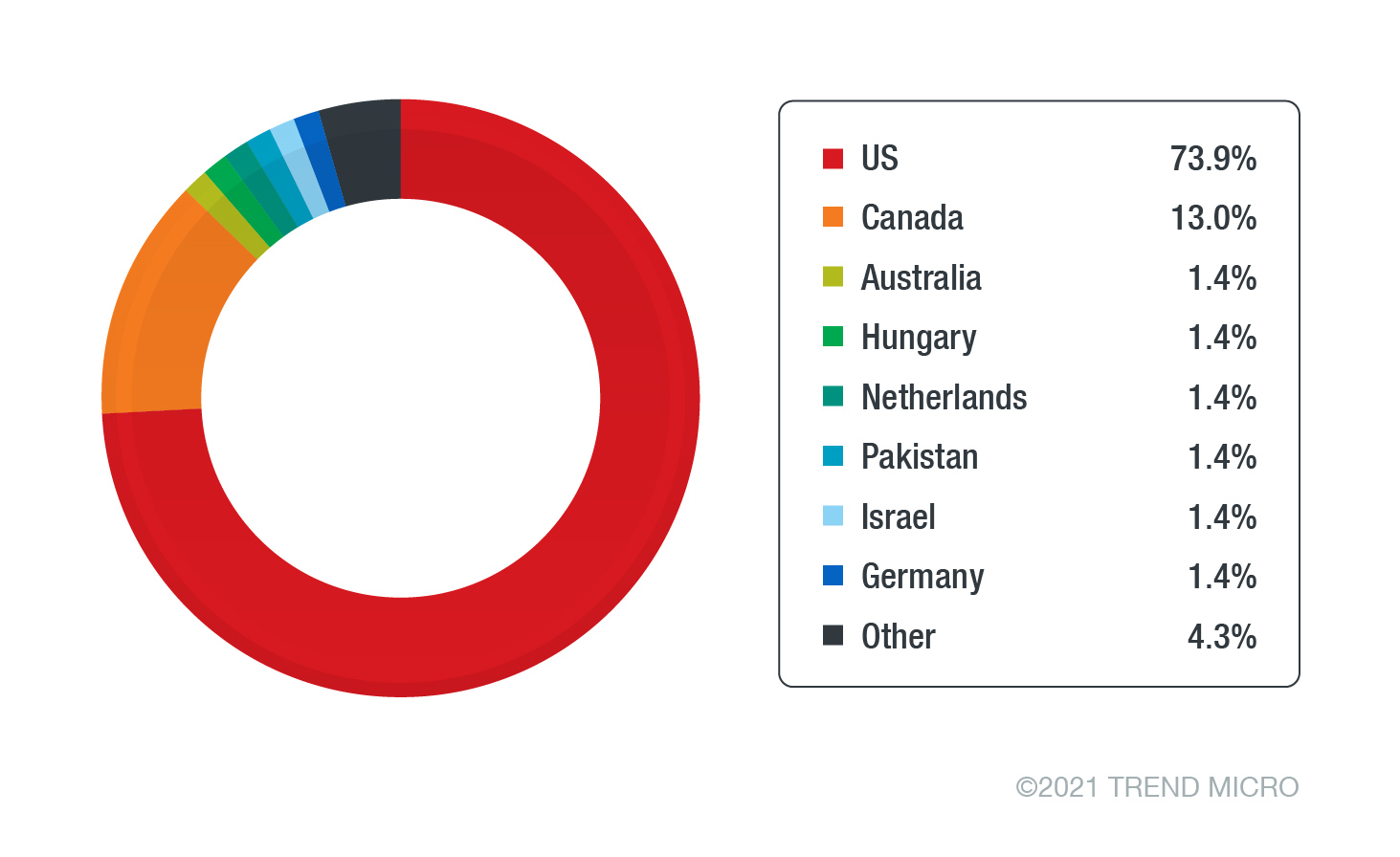
Based on the data distribution, CEOs in the US are obviously the main targets of the threat actors that use the Office 365 V4 phishing kit. In the underground markets, CEO email address lists are often sold and bought for the purpose of conducting additional phishing attacks, gaining access to sensitive information or conducting other social engineering attacks, such as business email compromise (BEC) and impersonation.
A look at different underground forums and pages also revealed specific offers for compromised credentials which are categorized according to year, industry, company position, and social media platform credentials. In addition, the forum messages were written in English, even in non-English forums such as those catering to Russian-speaking users and groups. While not uncommon, the accounts were notably created to post those specific messages selling the data and phishing kit to potential customers. This is emphasized in one forum where the actor bought an account for use in one of the forums just to sell data.
To start a target list, there are a number of platforms available that sell lists of CFO/CEO emails, Facebook profiles and more, categorized by region and country. The attackers could have purchased target lists from one of these websites.
Conclusion
Phishing attacks and attackers often target employees — usually the weakest link in an organization’s security chain. As seen in this particular campaign, the attackers target high profile employees who may not be as technically or cybersecurity savvy, and may be more likely to be deceived into clicking on malicious links. By selectively targeting C-level employees, the attacker significantly increases the value of obtained credentials as they could lead to further access to sensitive personal and organizational information, and used in other attacks.
The scale and accuracy of the emails and credentials show that the attacker possesses an accurate dataset of victims and potential targets. While the attacker could have simply compiled the emails from the targeted organizations’ websites, they went a step further to validate these to make sure it complements data collected from the public domain.
While organizations are aware and wary of the information they include in public-facing websites and platforms, their respective employees should be constantly reminded to be mindful of the details they disclose on personal pages. These can be easily used against them for attacks using social engineering techniques. All employees, regardless of company rank, should exercise caution when reviewing and acting on email prompts for specific actions, especially from unknown sources.
Considering this, legitimate service providers and vendors will never ask individual consumers and enterprise users for details such as account access credentials, and especially not to retain dated passwords. These details are susceptible to abuse among unauthorized and malicious individuals and are left for customization by vendors to respective security and IT teams following organizational policies.
Indicators of Compromise (IoCs)
Please click on the link to find our list of IoCs.

