Ransom_CERBER.SM3B
Ransom:Win32/Cerber (Microsoft); Ransom.Cerber (Malwarebytes)
Windows


Threat Type: Ransomware
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
This Ransomware arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
It connects to certain websites to send and receive information.
It encrypts files with specific file extensions. It drops files as ransom note.
TECHNICAL DETAILS
Arrival Details
This Ransomware arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Installation
This Ransomware drops the following files:
- %User Temp%\{random characters}\{random characters}.tmp
- %User Temp%\tmp{random}.bmp ← Ransom note wallpaper
(Note: %User Temp% is the user's temporary folder, where it usually is C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000, Windows Server 2003, and Windows XP (32- and 64-bit); C:\Users\{user name}\AppData\Local\Temp on Windows Vista (32- and 64-bit), Windows 7 (32- and 64-bit), Windows 8 (32- and 64-bit), Windows 8.1 (32- and 64-bit), Windows Server 2008, and Windows Server 2012.)
Other System Modifications
This Ransomware changes the desktop wallpaper by modifying the following registry entries:
HKEY_CURRENT_USER\Control Panel\Desktop
Wallpaper = %User Temp%\tmp{random}.bmp
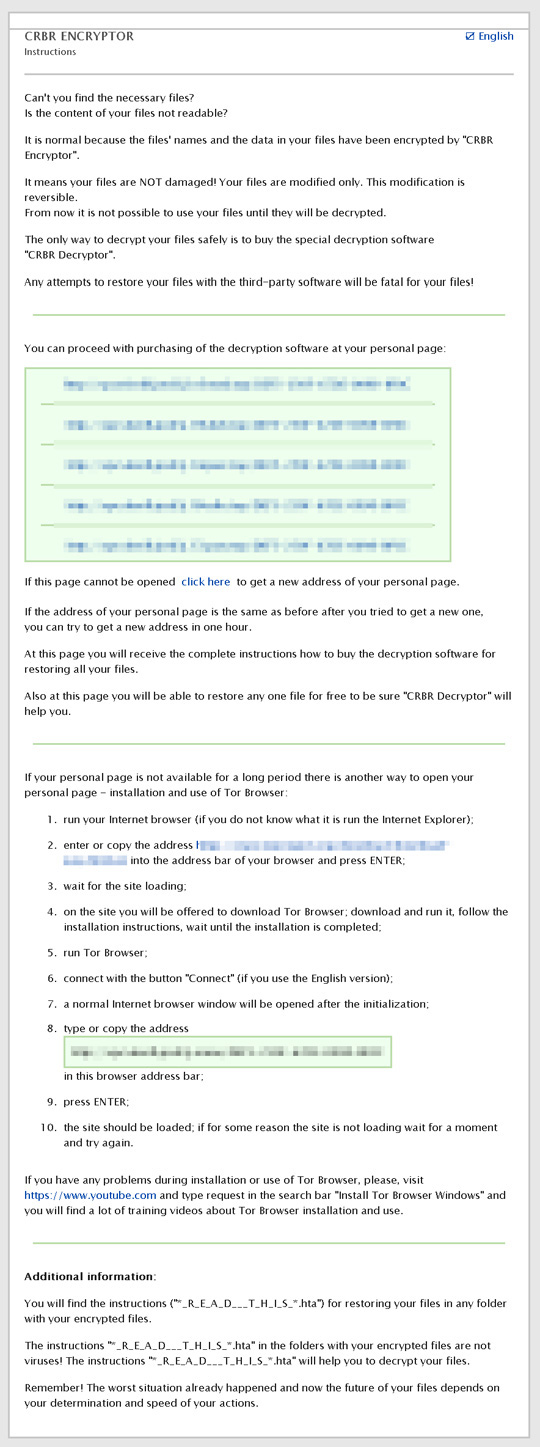
It sets the system's desktop wallpaper to the following image:
Other Details
This Ransomware connects to the following website to send and receive information:
- hxxp://xpcx6erilkjced3j.{BLOCKED}k.top/
- {BLOCKED}.{BLOCKED}.57.0/27:6893
- {BLOCKED}.{BLOCKED}.17.0/27:6893
- {BLOCKED}.{BLOCKED}.176.0/22:6893
It does the following:
- It avoids infecting system with the following OS Language Code:
- 1049 - Russian
- 1058 - Ukrainian
- 1059 - Belarusian
- 1064 - Tajik (Cyrillic)
- 1067 - Armenian
- 1068 - Azeri (Latin)
- 1079 - Georgian
- 1087 - Kazakh
- 1088 - Kyrgyz
- 1090 - Turkmen
- 1091 - Uzbek (Latin)
- 1092 - Tatar
- 2072 - Romanian (Moldova)
- 2073 - Romanian (Romania)
- 2092 - Azeri (Cyrillic)
- 2115 - Uzbek (Cyrillic)
- It is configured to target related files under the following folders:
- \bitcoin\
- \excel\
- \microsoft sql server\
- \microsoft\excel\
- \microsoft\microsoft sql server\
- \microsoft\office\
- \microsoft\onenote\
- \microsoft\outlook\
- \microsoft\powerpoint\
- \microsoft\word\
- \office\
- \onenote\
- \outlook\
- \powerpoint\
- \steam\
- \the bat!\
- \thunderbird\
- \word\
Ransomware Routine
This Ransomware encrypts files with the following extensions:
- .123
- .1cd
- .3dm
- .3ds
- .3fr
- .3g2
- .3gp
- .3pr
- .602
- .7z
- .7zip
- .aac
- .ab4
- .abd
- .acc
- .accdb
- .accde
- .accdr
- .accdt
- .ach
- .acr
- .act
- .adb
- .adp
- .ads
- .aes
- .agdl
- .ai
- .aiff
- .ait
- .al
- .aoi
- .apj
- .apk
- .arc
- .arw
- .ascx
- .asf
- .asm
- .asp
- .aspx
- .asset
- .asx
- .atb
- .avi
- .awg
- .back
- .backup
- .backupdb
- .bak
- .bank
- .bat
- .bay
- .bdb
- .bgt
- .bik
- .bin
- .bkp
- .blend
- .bmp
- .bpw
- .brd
- .bsa
- .bz2
- .c
- .cash
- .cdb
- .cdf
- .cdr
- .cdr3
- .cdr4
- .cdr5
- .cdr6
- .cdrw
- .cdx
- .ce1
- .ce2
- .cer
- .cfg
- .cfn
- .cgm
- .cib
- .class
- .cls
- .cmd
- .cmt
- .config
- .contact
- .cpi
- .cpp
- .cr2
- .craw
- .crt
- .crw
- .cry
- .cs
- .csh
- .csl
- .csr
- .css
- .csv
- .d3dbsp
- .dac
- .das
- .dat
- .db
- .db3
- .db_journal
- .dbf
- .dbx
- .dc2
- .dch
- .dcr
- .dcs
- .ddd
- .ddoc
- .ddrw
- .dds
- .def
- .der
- .des
- .design
- .dgc
- .dgn
- .dif
- .dip
- .dit
- .djv
- .djvu
- .dng
- .doc
- .docb
- .docm
- .docx
- .dot
- .dotm
- .dotx
- .drf
- .drw
- .dtd
- .dwg
- .dxb
- .dxf
- .dxg
- .edb
- .eml
- .eps
- .erbsql
- .erf
- .exf
- .fdb
- .ffd
- .fff
- .fh
- .fhd
- .fla
- .flac
- .flb
- .flf
- .flv
- .forge
- .fpx
- .frm
- .fxg
- .gbr
- .gho
- .gif
- .gpg
- .gray
- .grey
- .groups
- .gry
- .gz
- .h
- .hbk
- .hdd
- .hpp
- .html
- .hwp
- .ibank
- .ibd
- .ibz
- .idx
- .iif
- .iiq
- .incpas
- .indd
- .info
- .info_
- .iwi
- .jar
- .java
- .jnt
- .jpe
- .jpeg
- .jpg
- .js
- .json
- .k2p
- .kc2
- .kdbx
- .kdc
- .key
- .kpdx
- .kwm
- .laccdb
- .lay
- .lay6
- .lbf
- .lck
- .ldf
- .lit
- .litemod
- .litesql
- .lock
- .ltx
- .lua
- .m
- .m2ts
- .m3u
- .m4a
- .m4p
- .m4u
- .m4v
- .ma
- .mab
- .mapimail
- .max
- .mbx
- .md
- .mdb
- .mdc
- .mdf
- .mef
- .mfw
- .mid
- .mkv
- .mlb
- .mml
- .mmw
- .mny
- .money
- .moneywell
- .mos
- .mov
- .mp3
- .mp4
- .mpeg
- .mpg
- .mrw
- .ms11
- .msf
- .msg
- .mts
- .myd
- .myi
- .nd
- .ndd
- .ndf
- .nef
- .nk2
- .nop
- .nrw
- .ns2
- .ns3
- .ns4
- .nsd
- .nsf
- .nsg
- .nsh
- .nvram
- .nwb
- .nx2
- .nxl
- .nyf
- .oab
- .obj
- .odb
- .odc
- .odf
- .odg
- .odm
- .odp
- .ods
- .odt
- .ogg
- .oil
- .omg
- .one
- .onenotec2
- .orf
- .ost
- .otg
- .oth
- .otp
- .ots
- .ott
- .p12
- .p7b
- .p7c
- .pab
- .pages
- .paq
- .pas
- .pat
- .pbf
- .pcd
- .pct
- .pdb
- .pdd
- .pef
- .pem
- .pfx
- .php
- .pif
- .pl
- .plc
- .plus_muhd
- .pm
- .pm!
- .pmi
- .pmj
- .pml
- .pmm
- .pmo
- .pmr
- .pnc
- .pnd
- .png
- .pnx
- .pot
- .potm
- .potx
- .ppam
- .pps
- .ppsm
- .ppsx
- .ppt
- .pptm
- .pptx
- .prf
- .private
- .ps
- .psafe3
- .psd
- .pspimage
- .pst
- .ptx
- .pub
- .pwm
- .py
- .qba
- .qbb
- .qbm
- .qbr
- .qbw
- .qbx
- .qby
- .qcow
- .qcow2
- .qed
- .qtb
- .r3d
- .raf
- .rar
- .rat
- .raw
- .rb
- .rdb
- .re4
- .rm
- .rtf
- .rvt
- .rw2
- .rwl
- .rwz
- .s3db
- .safe
- .sas7bdat
- .sav
- .save
- .say
- .sch
- .sd0
- .sda
- .sdb
- .sdf
- .secret
- .sh
- .sldm
- .sldx
- .slk
- .slm
- .sql
- .sqlite
- .sqlite-shm
- .sqlite-wal
- .sqlite3
- .sqlitedb
- .sr2
- .srb
- .srf
- .srs
- .srt
- .srw
- .st4
- .st5
- .st6
- .st7
- .st8
- .stc
- .std
- .sti
- .stl
- .stm
- .stw
- .stx
- .svg
- .swf
- .sxc
- .sxd
- .sxg
- .sxi
- .sxm
- .sxw
- .tar
- .tax
- .tbb
- .tbk
- .tbn
- .tex
- .tga
- .tgz
- .thm
- .tif
- .tiff
- .tlg
- .tlx
- .txt
- .uop
- .uot
- .upk
- .usr
- .vb
- .vbox
- .vbs
- .vdi
- .vhd
- .vhdx
- .vmdk
- .vmsd
- .vmx
- .vmxf
- .vob
- .vpd
- .vsd
- .wab
- .wad
- .wallet
- .war
- .wav
- .wb2
- .wk1
- .wks
- .wma
- .wmf
- .wmv
- .wpd
- .wps
- .x11
- .x3f
- .xis
- .xla
- .xlam
- .xlc
- .xlk
- .xlm
- .xlr
- .xls
- .xlsb
- .xlsm
- .xlsx
- .xlt
- .xltm
- .xltx
- .xlw
- .xml
- .xps
- .xxx
- .ycbcra
- .yuv
- .zip
It avoids encrypting files with the following strings in their file name:
- bootsect.bak
- iconcache.db
- ntuser.dat
- thumbs.db
- .bat
- .cmd
- .com
- .cpl
- .dll
- .exe
- .hta
- .msc
- .msi
- .msp
- .pif
- .scf
- .scr
- .sys
It avoids encrypting files with the following strings in their file path:
- :\$getcurrent\
- :\$recycle.bin\
- :\$windows.~bt\
- :\$windows.~ws\
- :\boot\
- :\documents and settings\all users\
- :\documents and settings\default user\
- :\documents and settings\localservice\
- :\documents and settings\networkservice\
- :\intel\
- :\msocache\
- :\perflogs\
- :\program files (x86)\
- :\program files\
- :\programdata\
- :\recovery\
- :\recycled\
- :\recycler\
- :\system volume information\
- :\temp\
- :\windows.old\
- :\windows10upgrade\
- :\windows\
- :\winnt\
- \appdata\local\
- \appdata\locallow\
- \appdata\roaming\
- \local settings\
- \public\music\sample music\
- \public\pictures\sample pictures\
- \public\videos\sample videos\
- \tor browser\
It renames encrypted files using the following names:
- {10 Random Characters}.{4 Random Characters}
It drops the following file(s) as ransom note:
- {folder of encrypted files}\_R_E_A_D___T_H_I_S___{random}_.txt
- {folder of encrypted files}\_R_E_A_D___T_H_I_S___{random}_.hta
- %Desktop%\_R_E_A_D___T_H_I_S___{random}_.txt
- %Desktop%\_R_E_A_D___T_H_I_S___{random}_.hta
(Note: %Desktop% is the desktop folder, where it usually is C:\Documents and Settings\{user name}\Desktop in Windows 2000, Windows Server 2003, and Windows XP (32- and 64-bit); C:\Users\{user name}\Desktop in Windows Vista (32- and 64-bit), Windows 7 (32- and 64-bit), Windows 8 (32- and 64-bit), Windows 8.1 (32- and 64-bit), Windows Server 2008, and Windows Server 2012.)
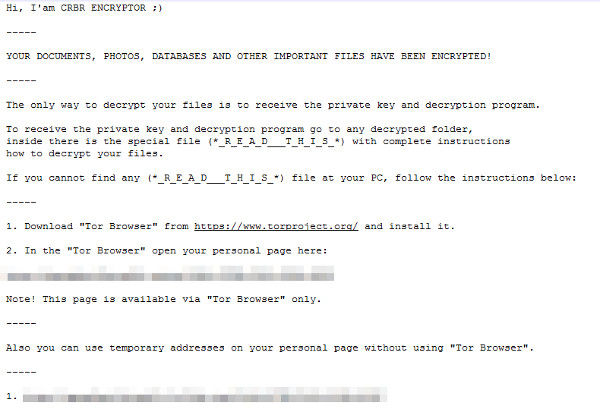
It leaves text files that serve as ransom notes containing the following text:
NOTES:
The _R_E_A_D___T_H_I_S___{random}_.hta contains the following information: