HKTL_DOOMWORM
Windows


Threat Type: Hacking Tool
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This mew malware is related to the release of the Njw0rm malware source code found in early January 2015.
To get a one-glance comprehensive view of the behavior of this Hacking Tool, refer to the Threat Diagram shown below.

This hacking tool may be manually installed by a user.
TECHNICAL DETAILS
Arrival Details
This hacking tool may be manually installed by a user.
NOTES:
This hacking tool listens on a user-specified port. It monitors the following information:
- Computer Name
- Country
- Firewall
- Hack date
- Installed antivirus
- Installed CPU and GPU
- IP address
- Malware version
- Operating system version
- Presence of removable drives
- Processor ID
- Product name, ID, and key
- RAM
- User name
- Victim's infection ID
It may perform the following actions:
- DDoS attack
- Computer shutdown, restart, log off
- Message via message box
- Bitcoin-mining
- Open http://www.{BLOCKED}equran.org
- Uninstall worm (Built by this hacking tool builder)
- Build .vbs worm malware
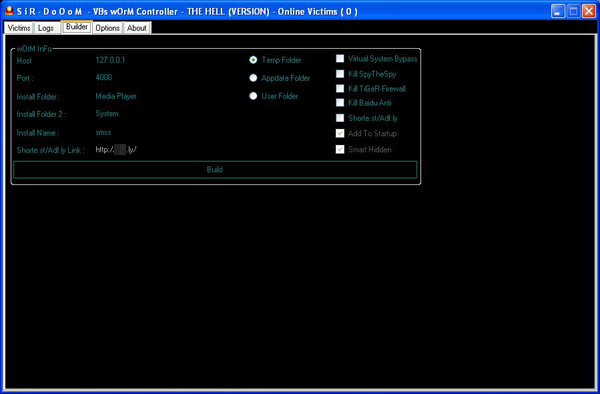
The behavior of the built malware depends on the specified option of the builder:
It connects to the specified IP and port. It may drop a shortcut file that points to a copy of itself in any of the following:
- %User Temp%\{Install Folder}\{Install Name}-DoOoM.lnk
- %Application Data%\{Install Folder}\{Install Name}-DoOoM.lnk
- %User Profile%\{Install Folder}\{Install Name}-DoOoM.lnk
It may drop a copy of itself in any of the following locations:
- %User Temp%\{Install Folder 2}\{Install Name}-DoOoM.vbs
- %Application Data%\{Install Folder 2}\{Install Name}-DoOoM.vbs
- %User Profile%\{Install Folder 2}\{Install Name}-DoOoM.vbs
The built malware may perform the following actions on the affected system.
- Force terminate the following Processes:
- SpyTheSpy.exe
- TiGeR-Firewall.exe
- bavtray.exe
- Check if running under virtual machine
- Create a shortcut that will go to a specified url at every system startup
- Hide itself
- Propagate via Removable
SOLUTION
Step 1
Before doing any scans, Windows XP, Windows Vista, and Windows 7 users must disable System Restore to allow full scanning of their computers.
Step 2
Note that not all files, folders, and registry keys and entries are installed on your computer during this malware's/spyware's/grayware's execution. This may be due to incomplete installation or other operating system conditions. If you do not find the same files/folders/registry information, please proceed to the next step.
Step 3
Scan your computer with your Trend Micro product to delete files detected as HKTL_DOOMWORM. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.


