BKDR_ZACCESS.TU
Mal/ZAccess-BL (Sophos), Backdoor.Win32.ZAccess.etgx (Kaspersky), TrojanDropper:Win32/Sirefef (Microsoft), Win32/Sirefef.FY trojan (NOD32), Trojan.Zeroaccess.C (Norton)
Windows 2000, Windows Server 2003, Windows XP (32-bit, 64-bit), Windows Vista (32-bit, 64-bit), Windows 7 (32-bit, 64-bit)


Threat Type: Backdoor
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
This backdoor arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
It deletes the initially executed copy of itself.
TECHNICAL DETAILS
Arrival Details
This backdoor arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Installation
This backdoor drops the following copies of itself into the affected system and executes them:
- %AppDataLocal%\Google\Desktop\Install\{GUID}\{unprintable characters 1}\{unprintable characters 2}\{RLO Unicode}{unprintable characters 3}\{GUID}\GoogleUpdate.exe
- %Program Files%\Google\Desktop\Install\{GUID}\{unprintable characters 1}\{unprintable characters 2}\{RLO Unicode}{unprintable characters 3}\{GUID}\GoogleUpdate.exe
(Note: %AppDataLocal% is the Local Application Data folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Application Data on Windows 2000, XP, and Server 2003, or C:\Users\{user name}\AppData\Local on Windows Vista and 7.. %Program Files% is the default Program Files folder, usually C:\Program Files in Windows 2000, Server 2003, and XP (32-bit), Vista (32-bit), and 7 (32-bit), or C:\Program Files (x86) in Windows XP (64-bit), Vista (64-bit), and 7 (64-bit).)
It drops the following component file(s):
- %AppDataLocal%\Google\Desktop\Install\{GUID}\{unprintable characters 1}\{unprintable characters 2}\{RLO Unicode}{unprintable characters 3}\{GUID}\@ - configuration file
- %Program Files%\Google\Desktop\Install\{GUID}\{unprintable characters 1}\{unprintable characters 2}\{RLO Unicode}{unprintable characters 3}\{GUID}\@ - configuration file
(Note: %AppDataLocal% is the Local Application Data folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Application Data on Windows 2000, XP, and Server 2003, or C:\Users\{user name}\AppData\Local on Windows Vista and 7.. %Program Files% is the default Program Files folder, usually C:\Program Files in Windows 2000, Server 2003, and XP (32-bit), Vista (32-bit), and 7 (32-bit), or C:\Program Files (x86) in Windows XP (64-bit), Vista (64-bit), and 7 (64-bit).)
Autostart Technique
This backdoor adds the following registry entries to enable its automatic execution at every system startup:
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Run
Google Update = ""%AppDataLocal%\Google\Desktop\Install\{GUID}\{unprintable characters 1}\{unprintable characters 2}\{RLO Unicode}{unprintable characters 3}\{GUID}\GoogleUpdate.exe" >"
It registers as a system service to ensure its automatic execution at every system startup by adding the following registry keys:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\{RLO Unicode}etadpug
Start = "2"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\{RLO Unicode}etadpug
Type = "10"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\{RLO Unicode}etadpug
ErrorControl = "0"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\{RLO Unicode}etadpug
ImagePath = "%Program Files%\Google\Desktop\Install\{GUID}\{unprintable characters 1}\{unprintable characters 2}\{RLO Unicode}{unprintable characters 3}\{GUID}\GoogleUpdate.exe"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\{RLO Unicode}etadpug
Description = "Keeps your Google software up to date. If this service is disabled or stopped, your Google software will not be kept up to date, meaning security vulnerabilities that may arise cannot be fixed and features may not work. This service uninstalls itself when there is no Google software using it."
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\{RLO Unicode}etadpug
DisplayName = Google Update Service (gupdate)
Other System Modifications
This backdoor deletes the following registry keys:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\wscsvc
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\wuauserv
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\BITS
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\SharedAccess
Other Details
This backdoor connects to the following possibly malicious URL:
- http://{BLOCKED}.{BLOCKED}.184.199
- http://j.{BLOCKED}d.com/app/geoip.js
- http://e526.d.{BLOCKED}edge.net/get/flashplayer/update/current/install/install_all_win_cab_ax_sgn.z
It deletes the initially executed copy of itself
SOLUTION
NOTES:
Step 1
Before doing any scans, Windows XP, Windows Vista, and Windows 7 users must disable System Restore to allow full scanning of their computers.Step 2
Backup Autorun Registry Key
- Open the Registry Editor by pressing Windows Key + R , type regedit into the Run input box, and then pressing ENTER.
- Locate and click the key:
HKEY_CURRENT_USER\Software\Microsoft\Windows\Current Version\Run - Click the File menu, and then click Export.
- In the Save in box, select the location where you want to save the backup copy, and then type a name for the backup file in the File name box.
- Click Save.
- Press delete key then Press the 'yes' button to confirm deletion.
Step 3
Disable Service Registry
- Open the Registry Editor by pressing Windows Key + R , type regedit into the Run input box, and then pressing ENTER.
- In the left panel, double-click the following: HKEY_LOCAL_MACHINE>SYSTEM>CurrentControlSet>services>gupdate
- In the right panel, locate the registry value:
ImagePath = "%Program Files%\Google\Desktop\Install\{GUID}\{unprintable characters1}\{unprintable characters2}\{RLO + unprintable characters3}\{GUID}\GoogleUpdate.exe" - Right-click on the value name and choose Modify. Change the value data of this entry to:
ImagePath = "" - In the right panel, locate the registry value:
Start = "2" - Right-click on the value name and choose Modify. Change the value data of this entry to:
Start = "4"
Step 4
For Windows Vista and later versions, you may skip steps 1 and 2 and just add permission by pressing 'yes' button on the permission pop-up. For other operating system versions, you need to assign owner for the malware folder in order to access/delete it. To do this you need the following step:
- Open the folder %AppDataLocal%\Google\Desktop\Install\{GUID}\{unprintable characters1}\{unprintable characters2}\{RLO + unprintable characters3}
(Note: %AppDataLocal% is the Local Application Data folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Application Data on Windows 2000, XP, and Server 2003, or C:\Users\{user name}\AppData\Local on Windows Vista and 7. %Program Files% is the default Program Files folder, usually C:\Program Files in Windows 2000, Server 2003, and XP (32-bit), Vista (32-bit), and 7 (32-bit), or C:\Program Files (x86) in Windows XP (64-bit), Vista (64-bit), and 7 (64-bit).)
- In the menu bar above click Tools>Folder Options>View Tab
- Then uncheck use simple file sharing (Recommended) then press apply.
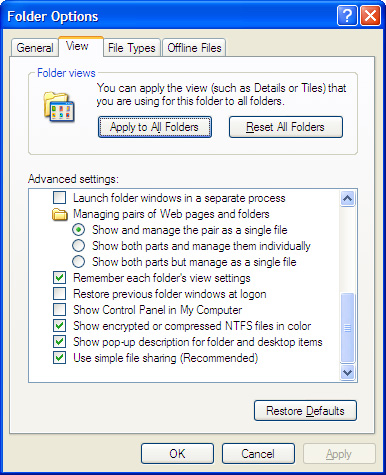
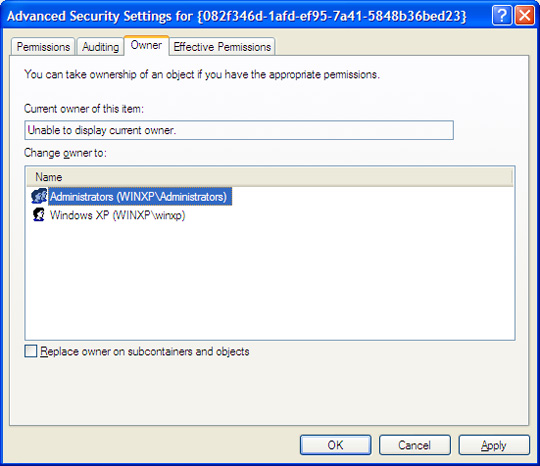
- Right Click the {GUID} folder and click Properties. Click Security Tab>Advanced button>Owner.
- Choose any owner then press 'Apply' button.
- Re-open folder Properties then on Security Tab. Checked the Full Control Box (Allow) then click 'Apply' button.
- Delete the folder to remove the malware.
- Open the folder %Program Files%\Google\Desktop\Install\{GUID}\{unprintable characters1}\{unprintable characters2}\{RLO + unprintable characters3}
- In the menu bar above click Tools>Folder Options>View Tab. Uncheck use simple file sharing (Recommended) then press apply.
- Right Click the {GUID} folder and click Properties. Click Security Tab>Advanced button>Owner.
- Choose any owner then press 'Apply' button.
- Re-open folder Properties then on Security Tab. Checked the Full Control Box (Allow) then click 'Apply' button.
- Delete the contents of the folder exlucind '@' file. (This is non-malicious but can be deleted upon restart)
- Restore the registry entries backup in Step 2 by executing the .reg file in saved folder and file name you specified.
Step 5
Restart in normal mode and scan your computer with your Trend Micro product for files detected as BKDR_ZACCESS.TU. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files.
Did this description help? Tell us how we did.



