3 Things We Learned About the IoE in 2014
The future is starting to take shape as the concept of the Internet of Everything (IoE) is applied to everything from smart home appliances to connected wearables. And it doesn't look like a fad that's going to pass; the market is slowly being filled with more and more smart devices as vendors come up with IoE products that focus on connectivity, convenience, security, and energy conservation. By what we have seen in the rich display of smart devices and systems at the International Consumer Electronics Show (CES) 2015, this market is strong and still growing.
IoE ecosystems operate smoothly thanks to the things, processes, and people that run it.
[Read: IoE 101: How to Explain All Things Smart, Wearable, and IoE]
“When a company creates a smart device, they not only need to create the hardware for the device, they also need to write the software for it. This is not a simple task, particularly for complex items,” says Trend Micro CTO Raimund Genes.
“All this results in a very large amount of software that needs to be written. A modern car has more than 100 million lines of code. More code not only means more features, but also more opportunities for various security flaws and vulnerabilities,” Genes adds.
In 2014, we reported about a series of scenarios by which malicious groups or individuals can attack insecure IoE systems like maritime tracking and monitoring or smart meters. During the year, we were witnesses to actual attacks that targeted these systems, such as the hacking of a road sign or a CCTV system.
Here are three important lessons we learned from IoE-related incidents in 2014:
Homes are becoming smarter
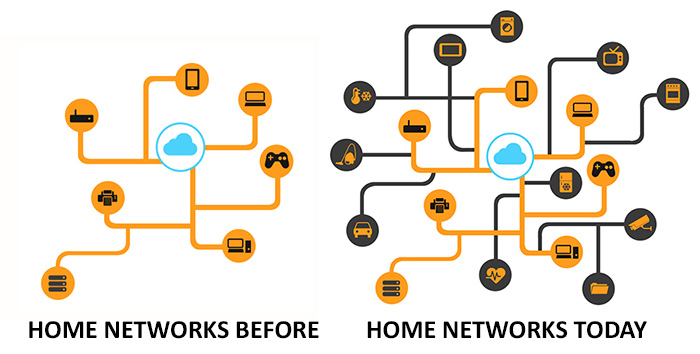
As a concept, the so-called “smartification” of the home has evolved further in 2014 as more households used intelligent devices that they can control via their mobile device. Smart meters, home security systems, thermostat controls, locks, and other technologies allow for the easy control and monitoring of the home. However, this opens up delicate concerns about the security of tomorrow’s home, where one misstep could give someone unwanted access to the home network.
[Read: The Smartification of the Home, Part 1]
[Read: The Smartification of the Home, Part 2]
Smart homes call for the “Administrator of Things.”
“Managing a household full of smart devices calls for the skills of both a multi-user IT administrator and a handyman. Let’s call this role the Administrator of Things (AoT),” remarks Geoff Grindrod, Director of Threat Intelligence Services at Trend Micro.
Internet users may find it easy to just go ahead and buy new IoE stuff, but, are they really ready to secure a network of devices filled with probable security holes? This role can exponentially get more difficult depending on how many smart devices the home has, how well these devices are used for automation, how many household members there are, and a lot of other factors. The burden is upon the home’s AoT to maintain these devices over time, though we believe that things will get better as vendors offer better support and stronger security measures for their products.
[Read: The Administrator of Things (AoT) – A Side Effect of Smartification]
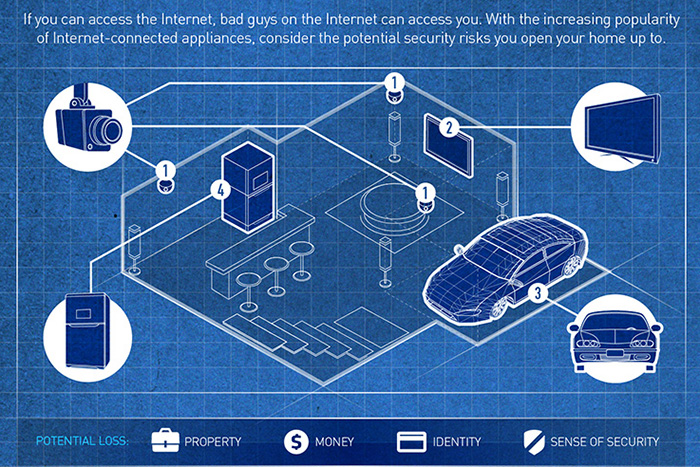
Hardware vulnerabilities endanger the IoE ecosystem.
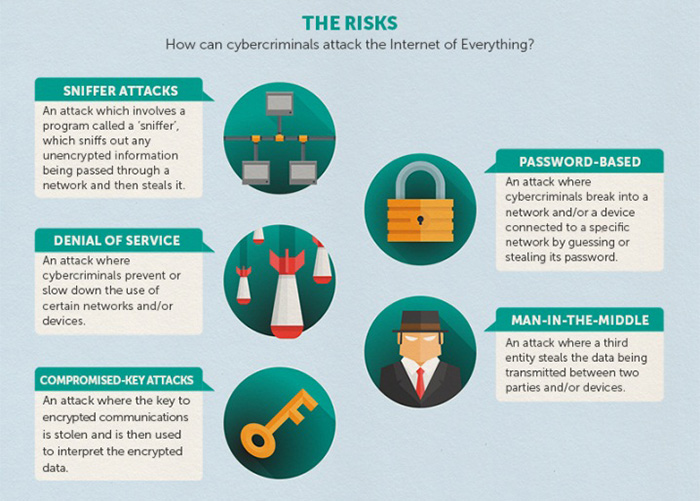
An ecosystem driven by the IoE consists of many layers and protocols, and each of these layers could have probable holes that can be exploited. One such weakness was exposed in 2014 when an easily exploitable backdoor was discovered in Netis routers, which could allow cybercriminals access to the home or office network. This can be dangerous considering that malicious actors need only attack the router to get to the smart devices connected to it. This can lead to homes being put physically at risk of hackers who can tinker with their smart locks or surveillance cameras, for instance.
[Read: The Internet of Everything: Layers, Protocols and Possible Attacks]
To 2015 and Beyond
Looking forward, securing IoE devices has to start with the vendors themselves. Federal Trade Commission Chairwoman Edith Ramirez stressed how this can be achieved "by adopting 'security by design," engaging in data minimization, and increasing transparency and providing consumers with notice and choice for unexpected data uses."
Watch the complete video to learn more about Securing the Internet of Everything:
How can one go about protecting their smart home networks from threats? Besides considering features and convenience, security should also be a primary consideration when deciding which smart devices to go for. For consumers, we have developed a comprehensive and helpful list of Security Considerations for Buying Smart Home Devices, which expounds on the importance of strong passwords, updateability, encryption, and more.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Do Security Blogs Enable Vibe-Coded Cybercrime?
- Unmasking Task Scams to Prevent Financial Fallout From Fraud
- Beware of MCP Hardcoded Credentials: A Perfect Target for Threat Actors
- Lessons in Resilience from the Race to Patch SharePoint Vulnerabilities
- LLM as a Judge: Evaluating Accuracy in LLM Security Scans
 Trend Micro State of AI Security Report 1H 2025
Trend Micro State of AI Security Report 1H 2025 AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report The Road to Agentic AI: Navigating Architecture, Threats, and Solutions
The Road to Agentic AI: Navigating Architecture, Threats, and Solutions