Ransomware Recap: Dec. 5 - Dec. 16, 2016
 At the tail end of 2016, ransomware operators were still hard at work. Distributors probed targets with new spam campaigns, while others experimented with unorthodox business strategies that involved selling ransomware products with "features" and add-ons that were marketed and sold separately. Operators also played around with alternative payment options that involved their victims in distribution. And, we saw malware authors fine-tuning their tools while again misusing ‘educational’ open-source ransomware.
At the tail end of 2016, ransomware operators were still hard at work. Distributors probed targets with new spam campaigns, while others experimented with unorthodox business strategies that involved selling ransomware products with "features" and add-ons that were marketed and sold separately. Operators also played around with alternative payment options that involved their victims in distribution. And, we saw malware authors fine-tuning their tools while again misusing ‘educational’ open-source ransomware.
One of the more interesting developments from these two weeks was a unique payment scheme pioneered by the creators of the new malware Popcorn Time (detected by Trend Micro as RANSOM_POPCORNTYM.A), which has no relation to the multi-platform media service of the same name. Aside from accepting payments in Bitcoin, the creators also provided an alternative payment option: pass on a malicious URL provided by the operators and try to infect others with the ransomware. If two of the ‘referred’ victims pay up, a decryptor tool is given for free.
Popcorn Time targets files found in My Documents, My Pictures, My Music, and the desktop. When unpacked, it pretends to be installing something and keeps the victim occupied as the files are encrypted using AES-256 encryption. The files are labeled with a .filock extension and the ransomware proceeds with outlining the payment plans for the victims. As justification for their criminal activity, the ransomware authors claim that the money they collect will be given to Syrians in need. It’s not a unique statement; previous ransomware operators have also made similar altruistic claims.
Figure 1. Popcorn Time “installation” screen distracts victims as files are encrypted
Unfinished code in the ransomware indicates that if a user enters the wrong decryption key four times, the malware will start deleting files.
Here are other notable ransomware stories that have surfaced over the past two weeks:
GoldenEye
Clinging to the James Bond theme, the authors behind the Petya-Mischa ransomware have made a comeback with GoldenEye (detected by Trend Micro as RANSOM_GOLDENEYE.B), the latest version of their product. This re-branded Petya-Mischa hybrid is being distributed via spam campaigns that, at the moment, seem to be targeting German-speaking users.
[READ: PETYA and Mischa: Ransomware Twins Spell Double the Trouble]
GoldenEye, like Petya, typically arrives as a legitimate-looking job application email with malicious attachments—a fake resume PDF and an excel spreadsheet which has a malicious macro embedded. The email suggests that you enable the content in the excel sheet to view important data about the “applicant”. If the file is enabled, a VBA script runs, drops the executable file, and starts the encryption process. The ransomware appends the first 8 characters of the victims personal decrypt code onto each encrypted file.
After GoldenEye encrypts files on the infected computer, it attempts to modify the Master Boot Record (MBR) and deny access to the user, preventing them from reversing the encryption process. 
Figure 2. Boxed in red, the extension name is part of the victim’s unique decryption code
The ransomware then reboots the system and displays the ransom note. A fake CHDSK screen pretends to repair issues with the hard drive, and then a skull and crossbones boot screen appears, prompting the victim to press any key. To recover files the victim is directed to a portal, asked to input their unique identifier, and then pay the ransom of 1.3 Bitcoin, or around US$1,300.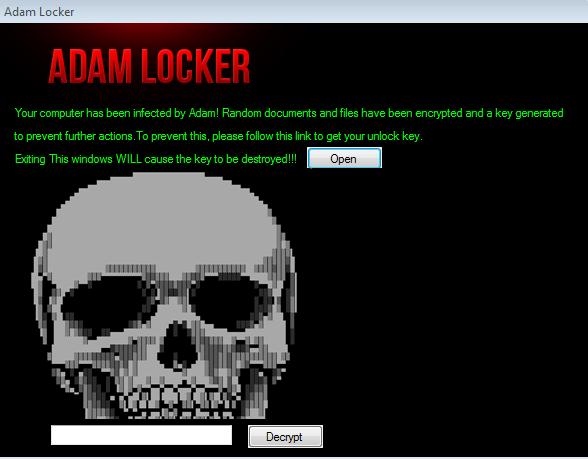
Figure 3. The CHDSK screen conceals the encryption process from the user

Figure 4. GoldenEye has a gold skull on screen, which is almost identical to Petya’s red skull and Petya/Mischa’s green skull
Cerber
Around the beginning of the holiday sale season, Cerber operators capitalized on distracted shoppers. Microsoft detected a spam campaign that uses fake credit card reports to trick users into opening a malicious Word document. The file is infected with a macro script that, when enabled, infects the user with Cerber. Trend Micro also detected a Cerber campaign in Germany where operators use fake emails disguised as fraud reports from the police’s cyber department in Cologne. Potential victims are urged to open a .ZIP file, which again contains a malicious Word document that hosts and helps execute Cerber.
Cerber has since been continuously updated over the past few weeks. The latest update is detected by Trend Micro as Ransom_CERBER.RED. These particular ransomware authors are quite persistent, and regularly tweak Cerber to improve its effectivity.
Locky
Locky has switched to another extension, this time using a character from Egyptian mythology. This latest variant (detected by Trend Micro as Ransom_LOCKY.EXE) uses .osiris and comes only a few weeks after the .aesir extension. The authors have a habit of paying homage to mythological narratives with their extension names (past examples include Odin and Thor).
This particular variant uses malicious excel documents to distribute the payload. They contain macros that, when enabled, download the malware onto the computer. The behavior parallels previous versions of Locky, and the ransom note is also similar.
Figure 5. New Locky ransom note
Here is a quick comparison of the previous versions of Locky:
|
|
AESIR |
ZZZZZ |
OSIRIS |
|
C&C |
/information[.]cgi |
/information[.]cgi |
/checkupdate |
|
Ransom Note |
_{random number}-INSTRUCTION.html |
_{ransom number}-INSTRUCTION.html |
OSIRIS-{4-alphanumeric chars}.htm |
EDA2 Locky
EDA2 Locky (Trend Micro detects it as Ransom_EDA2LOCKY.A.) is a new ransomware based on the open-source EDA2. It is simple and straightforward, with similar behavior to the previous strains based on EDA2. It gets its name from attaching the extension .locky on the files it encrypts. The ransomware is sold from a detailed product site, which divides the features and prices them individually so that attackers can opt to purchase specific additions. It’s a new pricing model as well, but this time on the operator’s side.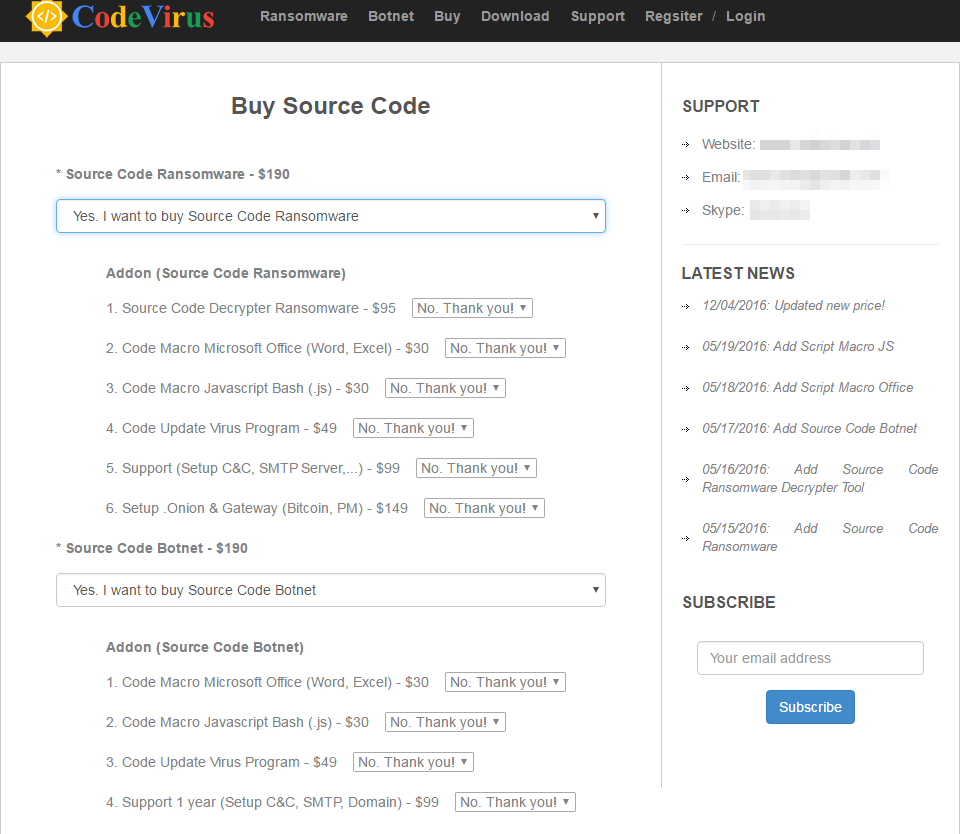
Figure 6. The product page for the EDA2 Locky ransomware
Ultralocker
Another off-shoot of open source ransomware has also been making waves. Ultralocker (detected by Trend Micro as Ransom_CryptoWire.C) comes from the open-source ransomware project CryptoWire, which was uploaded onto GitHub this past May. Though the original authors of CryptoWire intended it to be used for ‘educational’ purposes, ransomware operators have so far used it in the traditional fashion. Cybercriminals can't be expected to respect author requests for their source code. They see an opportunity—free ransomware, and practically ready for distribution. It’s quite easy to use it maliciously, as we saw previously with Hidden Tear.
You can see the similarities between Ultralocker and the Lomix ransomware, particularly in the style of the ransom note, which includes a screen displaying the encrypted files and instructions for the payment. However, after encryption Ultralocker uses the extension .locked, which is appended after the filename. Ultralocker also demands a higher ransom: the equivalent of US$1,000 in Bitcoin.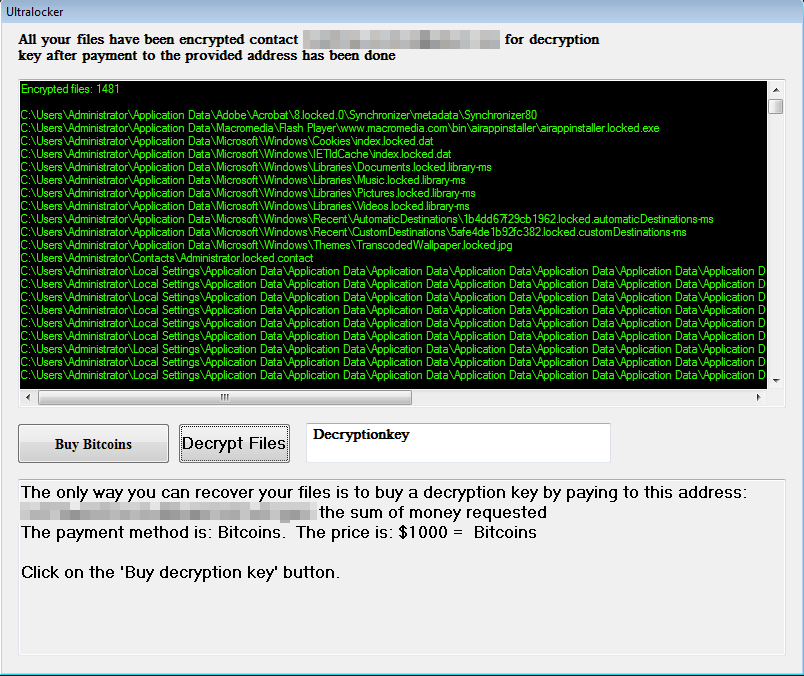
Figure 7. Ultralocker has a straightforward ransom note showing the encrypted files, similar to the Lomix note
Unlike the first two variants CryptoWire and Lomix, during distribution Ultralocker uses a document icon and executes a decoy document "Quotation{number}.doc" which is an added layer of fraud for confusing potential victims.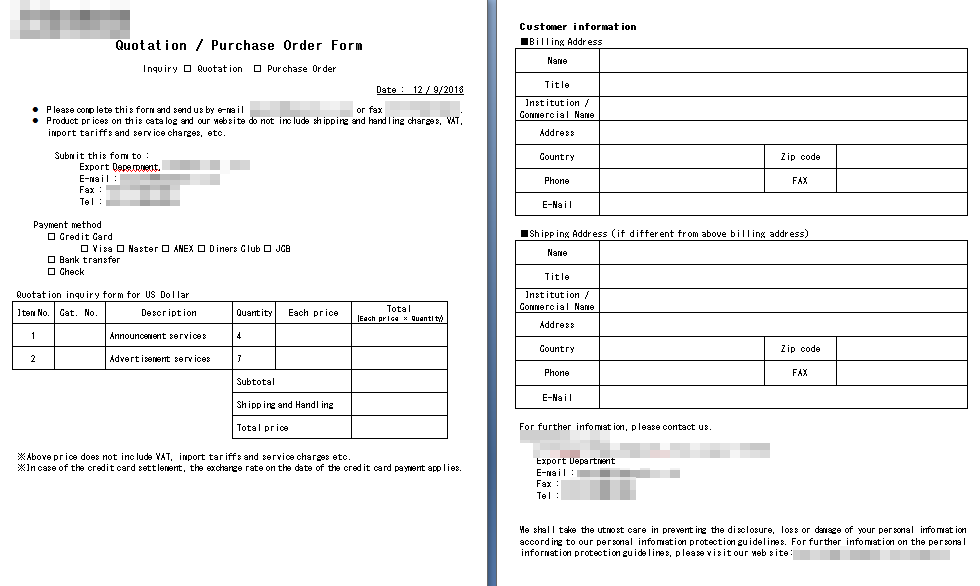
Sage
The CryLocker ransomware has a new variant called Sage (detected by Trend Micro as Ransom_MILICRY.B). The behavior is typical: after the malware is installed, files are encrypted, and the extension .sage is added to the files. The malware also creates two files (!Recovery_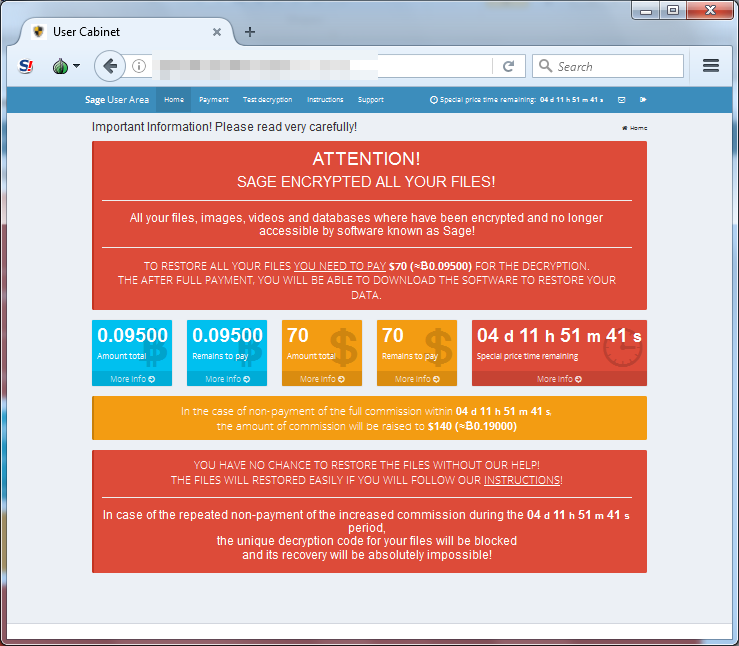
Figure 9. The Sage ransom payment page
A multi-layered approach is key to defending all possible gateways from malware. IT administrators in organizations should empower the workforce with necessary education to keep employees abreast of attack tactics. On the other hand, a solid back-up of important files can mitigate damages brought by a ransomware infection.
Ransomware solutions:
Trend Micro offers different solutions to protect enterprises, small businesses, and home users to help minimize the risk of getting infected by ransomware:
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevents ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Users can likewise take advantage of our free tools such as the Trend Micro Lock Screen Ransomware Tool, which is designed to detect and remove screen-locker ransomware; as well as Trend Micro Crypto-Ransomware File Decryptor Tool, which can decrypt certain variants of crypto-ransomware without paying the ransom or the use of the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report The Road to Agentic AI: Navigating Architecture, Threats, and Solutions
The Road to Agentic AI: Navigating Architecture, Threats, and Solutions