Negasteal/Agent Tesla Now Gets Delivered via Removable Drives, Steals Credentials from Becky! Internet Mail

We have recently spotted a Negasteal/Agent Tesla variant (detected by Trend Micro as Worm.Win32.NEGASTEAL.B) that uses a new delivery vector: removable drives. The malware also now steals credentials from the applications FTPGetter and Becky! Internet Mail.
Agent Tesla, discovered back in 2014, has been known to send stolen information either through web panel, file transfer protocol (FTP), or simple mail transfer protocol (SMTP). In the following sample (see Figures 1 and 2), the Negasteal/Agent Tesla variant steals credentials from “Becky! Internet Mail,” an email client used on Microsoft Windows operating systems (OS). It is to be noted that Becky!, as a shareware email product, supports many local characters and handles region-specific languages.
![]()
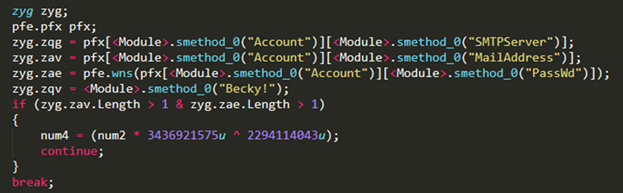
Figures 1 and 2. Credentials are gathered from Becky! Internet Mail
Additionally, the malware gathers stolen information from FTPGetter, which is used to automate FTP and SSH file transfer protocol (SFTP) uploads and task downloads. Aside from gathering credentials, Negasteal/Agent Tesla also drops .lnk files in the removable drives and uses the names of the drives’ folders/files as filenames. It then hides the original folders and files to trick unwitting users into opening the malicious file.
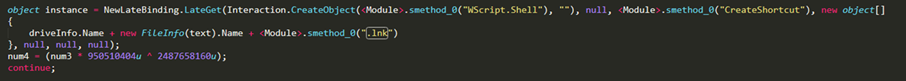
Figure 3. .lnk file is dropped in the removable drive
Interestingly, the sample was also seen being distributed via malspam, where the email gets delivered under the guise of new order notification. The content indicates that a new order has been attached for the recipient to review and respond to. The mail then goes into detail with the sender’s information and contact details such as address, mobile number, email address, and website.
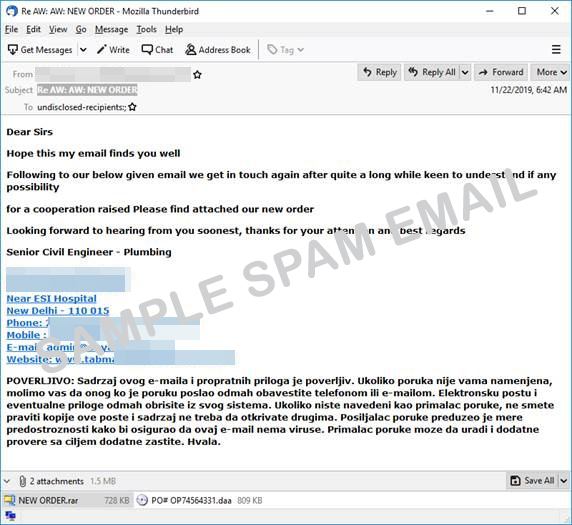
Figure 4. Sample spam email of a new order notification
[Related Research: AutoIT-compiled Negasteal/Agent Tesla, Ave Maria Delivered via Malspam]
In October 2019, Trend Micro researchers discovered that trojan spy Agent Tesla and remote access trojan (RAT) Ave Maria payloads were delivered via email to steal credentials and log keystrokes from various Windows applications. The payloads have been compiled with AutoIt, a scripting language intended to automate basic tasks in Windows GUI, to obfuscate the malware binary to bypass security detection. Upon successfully infecting machines, the malware will steal credentials from browsers and mail clients, log and monitor keystrokes, webcam and screen capture, as well as collect information saved on clipboards.
Trend Micro Solutions and Recommendations
To protect against Negasteal/Agent Tesla, we recommend updating applications and operating systems running to their latest versions. Users and organizations are also protected from threats like Negasteal/Agent Tesla through Trend Micro’s multilayered approach to cybersecurity. At the email level, the Trend Micro™ Anti-Spam Engine (TMASE)™ and Hosted Email Security (HES)™ solutions block spam emails, such as the fake new order notification in this report, from reaching users and organizations. Both solutions use machine learning technologies that include statistical analysis, advanced heuristics, whitelists and blacklists, as well as signature filtering.
Malicious files, scripts, and messages related to Negasteal/Agent Tesla are proactively detected by Trend Micro’s behavior monitoring technology, a key component in its endpoint solutions such as the Smart Protection Suites and Worry-Free™ Business Security.
The Trend Micro Deep Discovery Inspector protects customers by detecting suspicious network traffic and preventing Negasteal/Agent Tesla from connecting to C&C servers, which may lead to data exfiltration, via this DDI rule that covers the malware without TLS encryption:
- DDI Rule 4249 - NEGASTEAL - SMTP (Request)
Indicators of Compromise (IoCs)
depotipera@radianthospitals[.]org
b2d5a480a2b5ef561ded877b4259586b8c0487b27b61ac779392037c2351f99f – .daa file (detected as Worm.Win32.NEGASTEAL.B)
48339c4466a775775fbc0820dc0a66cd432df699daf6174ea6366b7273628fb1 – extracted from .daa (detected as Troj.Win32.TRX.XXPE50FFF033)
With insights from Michael Ofiaza and Jay Garcia
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One