Employees Are Top Targets of Phishing Emails
October 09, 2012
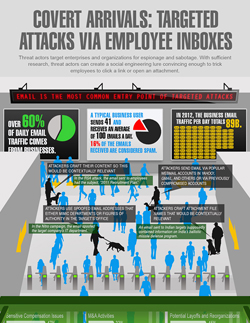 Download the infographic: Covert Arrivals: Targeted Attacks via Employee Inboxes
Download the infographic: Covert Arrivals: Targeted Attacks via Employee Inboxes
Spear phishing emails usually come posing as legitimate and basic messages employees see day after day. If sent to tired or unknowing recipients who give in to their lure, these messages can easily be the bearers of sophisticated malware designed to lay in stealth while eventually siphoning off sensitive company information.
Notably, most work emails sent daily revolve around sensitive compensation issues, merger and acquisition activities, potential layoffs and reorganizations, product road maps, and budget plans. Attackers can simply draft a message in any of these common contexts and easily gain the attention of its recipient.
It’s also common for malware in spear phishing emails to exploit a vulnerability, drop a file, download a file, or communicate with a remote server—any which way, it can then start to gather information about a company and scour the network for available information for sabotage, espionage, or monetary purposes.
See how email threats work for targeted attack campaigns on this infographic.
HIDE

Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Do Security Blogs Enable Vibe-Coded Cybercrime?
- Unmasking Task Scams to Prevent Financial Fallout From Fraud
- Beware of MCP Hardcoded Credentials: A Perfect Target for Threat Actors
- Lessons in Resilience from the Race to Patch SharePoint Vulnerabilities
- LLM as a Judge: Evaluating Accuracy in LLM Security Scans
 Trend Micro State of AI Security Report 1H 2025
Trend Micro State of AI Security Report 1H 2025 AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report The Road to Agentic AI: Navigating Architecture, Threats, and Solutions
The Road to Agentic AI: Navigating Architecture, Threats, and Solutions