
Ryuk is ransomware version attributed to the hacker group WIZARD SPIDER that has compromised governments, academia, healthcare, manufacturing, and technology organizations. In 2019, Ryuk had the highest ransom demand at USD $12.5 million, and likely netted a total of USD $150 million by the end of 2020.
Table of Contents
Ryuk ransomware attack
Ryuk, pronounced ree-yook, is a family of ransomware that first appeared in mid-to-late 2018. In December 2018, the New York Times reported that Tribune Publishing had been infected by Ryuk, disrupting printing in San Diego and Florida. The New York Times and the Wall Street Journal shared a printing facility in Los Angeles. They were also impacted by the attack, which caused distribution issues for the Saturday editions of the newspapers.
A variant of the older Hermes ransomware, Ryuk tops the list of the most dangerous ransomware attacks. In the CrowdStrike 2020 Global Threat Report, Ryuk accounts for three of the top 10 largest ransom demands of the year: USD $5.3 million, $9.9 million, and $12.5 million. Ryuk has successfully attacked industries and companies around the globe. Hackers call the practice of targeting large companies “big game hunting” (BGH).
Interestingly, this ransomware family carries a Japanese name from the anime movie Death Note. The name means “gift of god.” It seems an odd choice for ransomware since the targets lose data or money. From the hacker's perspective, however, it could be considered a gift of god.
A Russian cybercriminal group known as WIZARD SPIDER is believed to operate Ryuk ransomware. UNC1878, an Eastern European threat actor, has been behind some healthcare-specific attacks. The deployment of this ransomware is not direct; hackers download other malware onto a computer first.
When Ryuk infects a system, it first shuts down 180 services and 40 processes. These services and processes could prevent Ryuk from doing its work, or they are needed to facilitate the attack.
At that point, the encryption can occur. Ryuk encrypts files such as photos, videos, databases, and documents – all the data you care about – using AES-256 encryption. The symmetric encryption keys are then encrypted using asymmetric RSA-4096.
Ryuk is able to encrypt remotely, including remote administrative shares. In addition, it can perform Wake-On-Lan, waking computers for encryption. These abilities contribute to the effectiveness and reach of its encryption and the damage it can cause.
The hackers leave ransom notes in the system as RyukReadMe.txt and UNIQUE_ID_DO_NOT_REMOVE.txt that read something like the following screenshot.
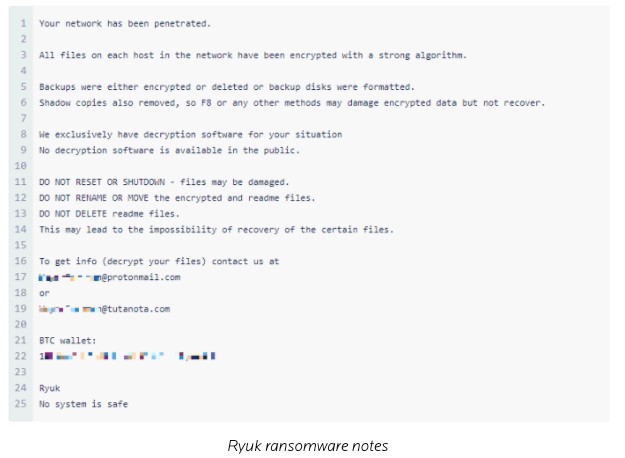
Source: Malwarebytes
Ryuk attack vector
Ryuk can use download as a service (DaaS) to infect targeted systems. DaaS is a service one hacker offers to another. If a hacker develops ransomware but doesn’t know how to distribute it, other hackers with those skills help distribute it.
Often, unwitting users fall prey to phishing attacks that facilitate the initial infection. AdvIntel reports that 91% of attacks begin with phishing emails. It is extremely important to train users to spot phishing emails. Training dramatically reduces the chance of infection. See Phishing Insights.
Ryuk is one of the most notorious and well-known ransomware as a service (RaaS) programs in terms of infection scope. Ransomware as a service (RaaS) is a model in which developers of ransomware offer it for the use of other hackers. The developer receives a percentage of successful ransom payments. RaaS is an adaptation of the software as a service (SaaS) model.
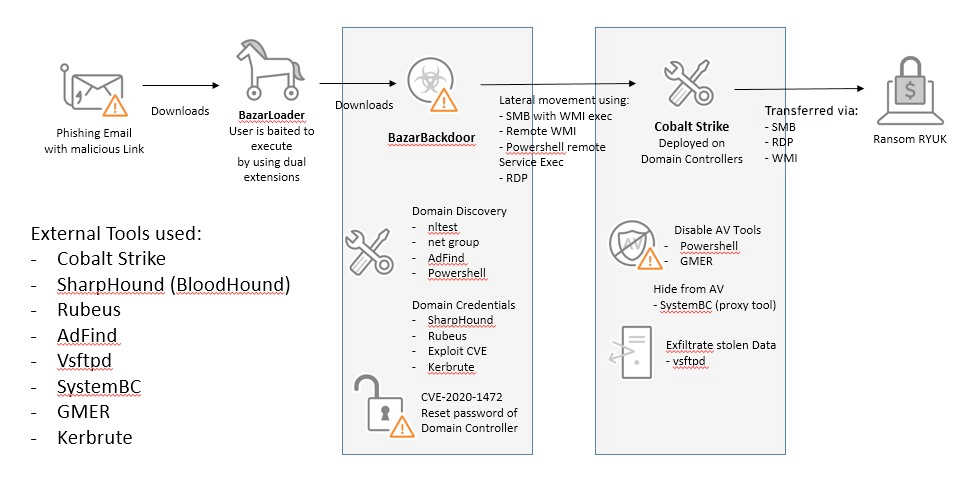
Once the user clicks on the phishing email, Ryuk downloads additional malware elements called droppers. The additional malware includes Trickbot, Zloader, BazarBackdoor, and others. These droppers might install Ryuk directly.
They could also install another piece of malware such as Cobalt Strike Beacon to communicate with a command and control (C2) network. Ryuk downloads once the malware is installed. Ryuk has also taken advantage of exploits such as the ZeroLogon vulnerability in Windows servers.
The diagram below shows Ryuk’s infection path or attack kill chain.
Sophos Group, a British security company, identified Ryuk’s attack flow, which is also called the attack kill chain. See the diagram below.
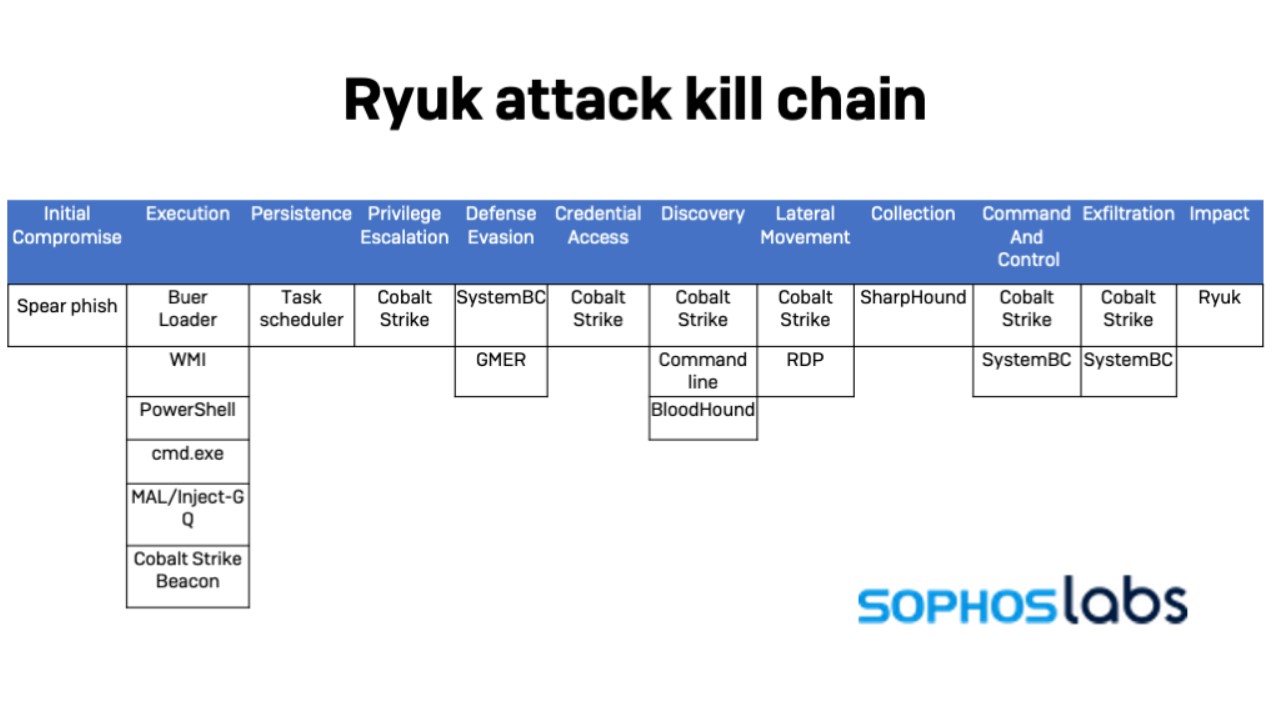
Source: Sophos
Trickbot
Trickbot emerged in 2016, and is believed to be run by WIZARD SPIDER, the same hacking group that operates Ryuk. This malware has been used as a banking trojan to steal user credentials, personally identifiable information, and bitcoins.
Skilled hackers designed Trickbot. They designed it to be used for additional purposes, such as searching for files on an infected system. It can also move laterally through a network from one machine to another. Trickbot’s capabilities now include credential harvesting, cryptomining, and more, but its most important function is to deploy Ryuk ransomware.
Ryuk indications of compromise
The devastation ransomware causes can be dramatic, so it is best to prevent an infection before it occurs. That is not always possible, so operations staff must watch for the beginnings of an attack and take immediate action to prevent further damage.
Since Ryuk can infect a system by many different attack vectors, the work to detect it is complicated. There are many indications of compromise (IOCs) that allow network and security administrators to see the precursors to a Ryuk infection.
BazarLoader, a dropper, is a common entry point for Ryuk. A dropper, or DaaS, is malware that downloads other malware. Here are some BazarLoader IOCs to watch out for:
- A scheduled task named “StartAd-Ad” appears in the Windows registry with autorun entries added next
- Executable dual-extension files such as Report.DOC.exe
TrickBot is another common entry for Ryuk, as mentioned above. Its IOC is an executable file that has a 12-character, randomly-generated file name. Once TrickBot creates the file, mnfjdieks.exe for example, it would be in one of these directories:
- C:\Windows\
- C:\Windows\SysWOW64
- C:\Users\[Username]\AppData\Roaming
For a complete list of TrickBot IOCs, please see the alert on the U.S. Cybersecurity & Infrastructure Security Agency (CISA) website.
Many times, the first IOC a company sees is the following screenshot. This screenshot indicates that Ryuk has infected the organization and encrypted sensitive data. Recovery is much faster if the company is ready with good incident response teams and playbooks, and has backed up data offline.

Source: 2SPYWARE
2020 Ryuk ransomware attacks
As Ryuk is used as a BGH, it has been used to attack governments, technology companies, and school systems. Sopra Steria, a French IT services firm with a cybersecurity brand, suffered a Ryuk infection in 2020. They believed it would take them weeks to completely recover.
Ryuk is one of the biggest threats against healthcare, and it seems Covid-19 was a contributing factor in an attack on healthcare in general. Universal Health Services (UHS) is a fortune 500 healthcare company with hospitals in the U.S. and U.K. The company suffered a Ryuk ransomware attack on September 27, 2020.
BleepingComputer reported that the most likely infection point for UHS was a phishing email. The phishing email would have contained Emotet, a piece of trojan. Emotet would have installed Trickbot, which then enabled the hacker group, WIZARD SPIDER, to manually install Ryuk through a reverse shell.
In October 2020, hackers infected two more medical centers with Ryuk. One was in Oregon – the Sky Lakes Medical Center – and the other was in New York – the Lawrence Health System. The attacks took computer systems offline, making electronic health records unavailable. The hospitals were already stressed with COVID-19 patient care, and the attack just made matters worse. Most of these hospital attacks lasted for weeks.
Ransomware best practices
There are many things companies and individuals can do to protect themselves from malware, and ransomware in particular. Here are a few top examples:
- Ensure patches are applied for OS, software, and firmware
- Use multi-factor authentication everywhere possible, with strong second factors. An example is 2FA. The U.S. National Institute of Standards and Technology (NIST) recommends not using SMS as a second factor
- Frequently audit accounts, access, logs, and anything else you can to verify configurations and activity
- Create data backups regularly and store them offline, especially for critical systems
- Educate users, especially about phishing emails. Users are on the front line receiving, reading, and responding to emails
Trend Micro Cyber Risk Report - 2025
Ransomware is a form of cyber extortion where attackers encrypt critical data and demand payment for its release. As highlighted in the Trend Micro 2025 Cyber Risk Report, ransomware remains one of the most visible and financially damaging threats to organizations worldwide.
Ransomware operators are no longer relying solely on traditional entry points like phishing emails or exposed RDP ports. Instead, they are exploiting overlooked and emerging vulnerabilities across an organization's digital ecosystem—what cybersecurity experts call the attack surface.
Discover how ransomware threats are evolving and what proactive strategies can help mitigate risk in Trend Micro’s 2025 Cyber Risk Report
How Trend Micro Helps You Stay Ahead of Ransomware Threats
As ransomware continues to be one of the most disruptive threats facing organizations today, the need for a unified, intelligent defense has never been greater. Trend Vision One™ offers a powerful solution that goes beyond traditional security tools—providing extended detection and response (XDR), attack surface risk management, and automated threat mitigation in a single, integrated platform.
With Trend Vision One™, security teams gain centralized visibility across endpoints, email, cloud, and network layers, enabling faster detection and response to ransomware activity. Backed by decades of threat intelligence and powered by Trend Micro’s Cybersecurity AI, the platform helps organizations proactively identify vulnerabilities, reduce exposure, and stop ransomware before it can cause damage.