
Log4Shell (CVE-2021-44228, CVE-2021-45046 and CVE-2021-45105) is a remote code execution (RCE) vulnerability that enables malicious actors to execute arbitrary Java code, taking control of a target server.
Table of Contents
Log4Shell vulnerability overview
2021 was a busy year for zero-day vulnerabilities capped off by Log4Shell, a critical flaw found in the widely used Java-based logging library, Apache Log4j. Officially identified as CVE-2021-44228, it carries a severity score of 10 out of 10 (CVSS v3.1) from the Common Vulnerability Scoring System (CVSS).
The vulnerability was first privately reported to Apache on Nov. 24, 2021. On Dec. 9, 2021 Log4Shell was publicly disclosed and initially patched with version 2.15.0 of Apache Log4j.
Subsequent news of observed attacks in the wild triggered several national cybersecurity agencies to issue warnings, including the US Cybersecurity and Infrastructure Security Agency (CISA), UK National Cyber Security Center (NCSC), and Canadian Center for Cyber Security. Due to the popularity of Apache Log4j, hundreds of millions of devices could be impacted.
How Log4Shell works
Log4Shell is a Java Naming and Directory Interface™ (JNDI) injection vulnerability which can allow remote code execution (RCE). By including untrusted data (such as malicious payloads) in the logged message in an affected Apache Log4j version, an attacker can establish a connection to a malicious server via JNDI lookup. The result: full access to your system from anywhere in the world.
Since JNDI lookup supports different types of directories such as Domain Name Service (DNS), Lightweight Directory Access Protocol (LDAP) which provide valuable information as the organisation’s network devices, remote method invocation (RMI), and Inter-ORB Protocol (IIOP), Log4Shell can lead to other threats such as:
- Coinmining: Attackers can use your resources to mine cryptocurrency. This threat can be quite costly, given vast amount of computing power required to run services and applications in the cloud.
- Network denial of service (DoS): This threat allows attackers to shut down and/or disable a network, website, or service so it is inaccessible to the targeted organisation.
- Ransomware: After RCE is achieved, attackers can collect and encrypt data for ransom purposes.
Below is a possible infection chain:
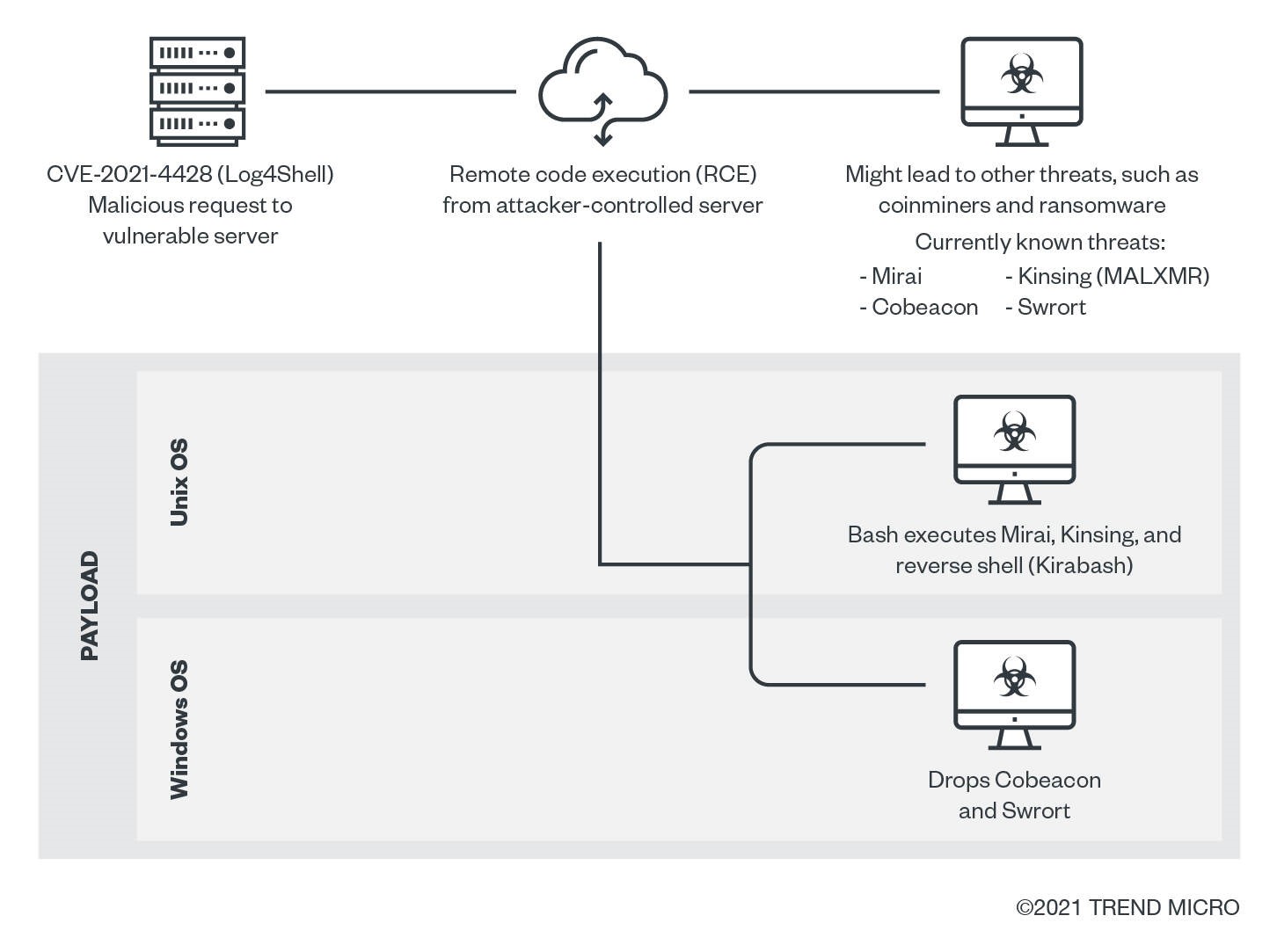
Vulnerable products, applications, and plug-ins
Essentially, any internet-facing device running Apache Log4j versions 2.0 to 2.14.1. The affected versions are included in Apache Struts, Apache Solr, Apache Druid, Elasticsearch, Apache Dubbo, and VMware vCenter.
Patch and mitigation
Apache initially released Apache Log4j version 2.15.0 to patch the vulnerability. However, this version only worked with Java 8. Users of earlier versions needed to apply and re-apply temporary mitigations. At the time of publication, Apache released version 2.16.0 and advised users to update their potentially affected library as quickly as possible.
Other mitigation strategies such as virtual patching and utilising an intrusion detection/prevention system (IDS/IPS) are strongly encouraged. Virtual patching shields the vulnerability from further exploitation, while IDS/IPS inspects ingress and egress traffic for suspicious behavior.
Log4Shell and the Hackers
Initial access
This vulnerability is caused by the “lookup” mechanism in log4j 2.x. It checks for the characters ${ in logs and triggers the “lookup” function, allowing forms like JNDI lookups (e.g., ${jndi:logging/context-name}), which support protocols like LDAP and RMI. An attacker can use an LDAP server with a malicious Java class to execute remote code.
Execution
If the exploit works, the server interprets the lookup string, potentially executing arbitrary commands in Java, JavaScript, or Unix shell formats.
Lateral movement
Cobeacon components, known for aiding lateral movement and linked to ransomware, may be downloaded.
Credential access
Malware like Kirabash may steal credentials by exfiltrating /etc/passwd and /etc/shadow.
Impact
Observed payloads include the Mirai botnet and Kinsing coinminer. Impacts include:
Resource hijacking: Coinminers consume system resources; Mirai can use infected systems for botnets.
Network DoS: Mirai may launch DDoS/DoS attacks using compromised systems.
The Impact of Log4Shell
Discovered by Alibaba researchers on November 24, 2021, Log4Shell was rated a critical vulnerability with a perfect CVSS score of 10.0. As a zero-day flaw in the widely used Log4J logging library, it posed an immediate and severe risk before a patch was available.
Log4J's broad adoption across web apps, cloud services, and consumer systems meant that over 90% of cloud environments were vulnerable. Many organizations didn’t even know they were exposed due to Log4J being used as an indirect dependency.
What made Log4Shell especially dangerous was its ease of exploitation—no special access was needed. Attackers could inject malicious code through simple user inputs like chat boxes or login forms. Once triggered, it could pass payloads to other parts of the system.
By December 9, public exploit code emerged, and major companies like Minecraft, Twitter, and Cisco were affected. At its peak, over 100 attacks per minute were recorded globally.
Attackers used the flaw to deploy botnets, cryptominers, and ransomware (e.g., Khonsari, Night Sky), and even state-backed groups from countries like China and North Korea were seen exploiting it.
Trend Micro Vision One
Stopping adversaries faster and taking control of cyber risk demands a unified approach. The widespread Log4J vulnerability exposed how easily attackers can exploit even simple components—making proactive, integrated defense essential.
Trend Vision One equips you with AI-driven prevention, detection, and response capabilities, backed by leading threat intelligence. It supports hybrid IT environments, automates security workflows, and simplifies operations—so you can reduce complexity, close gaps, and stay ahead of evolving threats.
Fernando Cardoso is the Vice President of Product Management at Trend Micro, focusing on the ever-evolving world of AI and cloud. His career began as a Network and Sales Engineer, where he honed his skills in datacenters, cloud, DevOps, and cybersecurity—areas that continue to fuel his passion.
Frequently Asked Questions (FAQs)
What is the Apache Log4j vulnerability?
The Apache Log4j vulnerability, known as Log4Shell, allows remote code execution, exposing systems to severe cybersecurity risks globally.
What is Apache Log4j?
Apache Log4j is a popular Java-based logging framework used widely for application event logging and system monitoring.
What is the fix for Log4j vulnerability?
The fix involves upgrading to Log4j version 2.17.1 or later, applying security patches, and disabling risky JNDI lookups.
Has Log4j been fixed?
Yes, Apache released patched versions addressing Log4Shell, but organizations must update promptly to prevent exploitation and maintain security.
Is Log4j deprecated?
No, Log4j is not deprecated; it remains widely used, but updated versions are essential for secure application logging.
What companies were affected by Log4j?
Major companies like Amazon, Microsoft, Apple, and numerous enterprises faced exposure due to widespread Log4j integration in software systems.

