TROJ_SASFIS.HS
TrojanDropper:Win32/Sirefef.B (Microsoft); Trojan.Win32.Sasfis.bvii (Kaspersky); Adware.Lop (Symantec); Trojan.Win32.Generic.pak!cobra (Sunbelt); W32/Sasfis.BVII!tr (Fortinet)
Windows 2000, Windows XP, Windows Server 2003


Threat Type: Trojan
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
TROJ_SASFIS.HS terminates and modifies the Access Control List (ACL) of processes that attempt to access it. When users attempt to execute forensic tools such as Process Explorer, it may display a popup message.
It infects system drivers (SYS) that meet certain conditions.
This Trojan may arrive bundled with malware packages as a malware component. It arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
It deletes itself after execution.
TECHNICAL DETAILS
Arrival Details
This Trojan may arrive bundled with malware packages as a malware component.
It arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Installation
This Trojan injects itself into the following processes as part of its memory residency routine:
- Explorer.exe
Other Details
This Trojan deletes itself after execution.
NOTES:
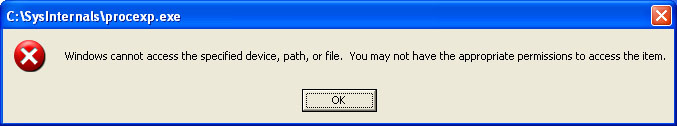
This Trojan will terminates and modify the Access Control List (ACL) of processes that attempt to access it. Infected systems are easily identified when users attempt to execute forensic tools such as Process Explorer.
For instance, it will not allow any user to execute Process Explorer and instead will display the pop-up message below:
This Trojan will enumerate all system drivers (SYS) using the following conditions:
- search for drivers between classpnp.sys and win32k.sys
- check for size must be greater than the malware code
This Trojan will then infect the SYS files by overwriting the first 53,248 bytes (D000H) of the file.
SOLUTION
Step 1
For Windows XP and Windows Server 2003 users, before doing any scans, please make sure you disable System Restore to allow full scanning of your computer.
Step 2
Using Trend Micro Rootkit Buster
RootkitBuster is a rootkit scanner that can check through hidden files, registry entries, processes, drivers, and hooked system services.
To use this tool, do the following:
- Download the tool from the following link and extract it to a temporary folder:
https://www.trendmicro.com/download/rbuster.asp - Run the RootkitBuster.exe file.
- On the upper left corner, select the types of hidden items that you wish to scan. We recommend selecting all types.
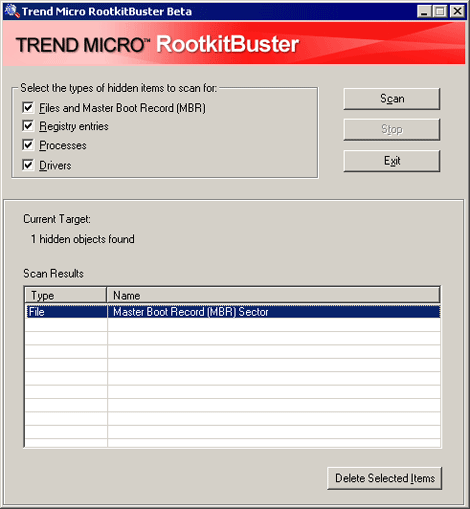
- Click the Scan button.
- The system is infected by this malware if the Scan result is similar to the image below:
Step 3
Restart in normal mode and scan your computer with your Trend Micro product for files detected as TROJ_SASFIS.HS. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
NOTES:
Step 4
In command prompt, execute the following command:
- cacls (path and filename) /G Everyone:F
Did this description help? Tell us how we did.


