HTML_FBSPAM.ASM
Windows 2000, Windows XP, Windows Server 2003


Threat Type: Trojan
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
This HTML script uses social engineering methods to lure users into performing certain actions that may, directly or indirectly, cause malicious routines to be performed. Specifically, it poses as a Facebook stalker finder to be able to infect Facebook user accounts.
To get a one-glance comprehensive view of the behavior of this Trojan, refer to the Threat Diagram shown below.
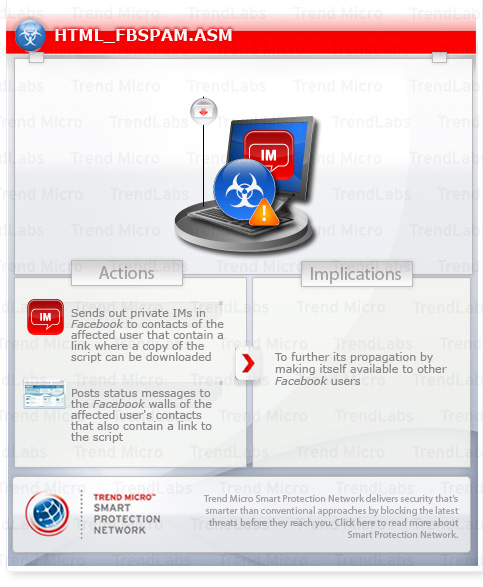
It may be hosted on websites that run a malicious script when accessed by unsuspecting users.
It poses as a legitimate Facebook application. It propagates by sending IMs and status messages with links to websites where it can be downloaded.
This Trojan executes when a user accesses certain websites where it is hosted.
TECHNICAL DETAILS
18,033 bytes
Script
21 Feb 2011
Arrival Details
This Trojan executes when a user accesses certain websites where it is hosted.
Other Details
This Trojan does the following:
- Poses as a Facebook application that finds stalkers. It sends private messages to the affected user's contacts containing a shortened URL where a copy of itself can be downloaded. It also posts status messages to the wall of the affected user's contacts that contain the shortened URL. Status message may be any of the following:
- Wow! Seems like lots of people stalk me - {link}
- New FB tool shows who stalks your profile-- {link}
- Secret tool shows who stalks your pics {link}
- Insane! Awesome tool to see who looks at your pics{link}
- According to {link} you're my top stalker. Creep.
- Secret tool shows who stalks your pics - {link}
- Check this out!
- Hey, whats happening?
- Hey! This is awesome
- http://{BLOCKED}l.com/5sec2j8
- http://{BLOCKED}o.gl/nxSGH
- http://{BLOCKED}s.gd/nOojFu
- http://{BLOCKED}l.com/fbcreeper
- http://{BLOCKED}o.gl/SDFu7
- http://{BLOCKED}o.gl/ngHGR
- Adds the following email addresses to the contacts of the affected user's account:
- {BLOCKED}ersenoocz@hotmail.com
- {BLOCKED}lossonmist@hotmail.com
NOTES:
This malware may be hosted to any of the following sites:
- http://{BLOCKED}eper.info
- http://{BLOCKED}ep.info
- http://{BLOCKED}eview.info
- http://{BLOCKED}eepers.co.cc
- http://{BLOCKED}eeper.tk
SOLUTION
8.900
7.850.03
21 Feb 2011
7.851.00
21 Feb 2011
Step 1
For Windows XP and Windows Server 2003 users, before doing any scans, please make sure you disable System Restore to allow full scanning of your computer.
Step 2
Close all opened browser windows
Step 3
Scan your computer with your Trend Micro product to delete files detected as HTML_FBSPAM.ASM. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.


