The Reality of Cross-Platform Mobile Threats
July 15, 2014

Besides having malware created specifically to take advantage of its ballooning user base, there’s another sign that mobile devices will soon be taking over the computing scene – mobile devices are being included in cross-platform threats.
What Are Cross-Platform Threats?
Cross-platform threats are malicious attacks that involve multiple platforms in their attack pattern or routine. Examples of cross-platform threats include (but are not limited to):
- Threats that attack the same way in different platforms
- Threats that have specialized payloads for each platform they target
- Threats that have components that allow it to run on different platforms
- Threats that begin their attack routine on one platform to lead to more malicious routines on another platform
By definition, if a single identifiable threat involves multiple platforms in its attack routines, then it is a cross-platform threat. And ever since the mobile boom, cybercriminals have started developing this type of attack to also include (or sometimes even focus on) mobile devices.
Some notable and recent examples of cross-platform mobile threats include:
ANDROIDOS_USBATTACK.A, a malicious app that pretends to be a cleaning utility for Android devices. It acts as an information stealer, but also downloads an autorun malware onto the affected mobile device’s SD card. Should the user connect his mobile device to a Windows PC, the malware would then automatically run, infecting the aforementioned PC. The malware itself records the user’s voice with the PC’s microphone feature.
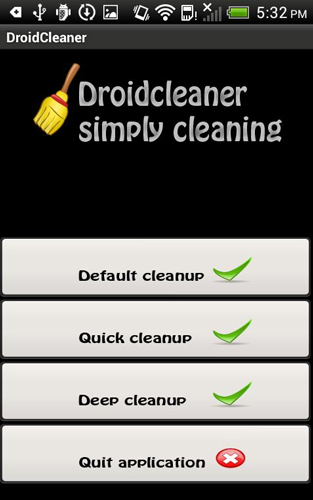
Figure 1. ANDROIDOS_USBATTACK.A as a fake device utility
TROJ_DROIDPAK.A, a PC Trojan that downloads and installs a malicious .APK file onto any Android mobile device connected to the infected PC. The malicious .APK file then searches for online banking apps on the infected mobile device and, if any are found, prompts the user to replace them with malicious versions.
A spam campaign involving WhatsApp, a popular free mobile messaging app. The spam notified the reader that they have WhatsApp voicemails pending, and to listen to them, they would have to click on a link that triggers a malicious file download. The malware downloaded would change depending on the platform used to access the link. Clicking from a PC downloads a malicious Java file, while accessing it from either an iOS or Android device downloads a malicious app (the latter’s payload is detected asANDROIDOS_OPFAKE.CTD.
What Makes Cross-Platform Threats Possible?
Multiple factors make cross-platform mobile threats like this possible. One of them is the tried-and-tested effectiveness of social engineering, as exemplified in the WhatsApp spam mentioned earlier that leveraged the app's popularity. Used increasingly often in many cybercriminal attacks, with the subjects ranging from highly-anticipated product releases to celebrity deaths and even sporting events (the World Cup is currently a very popular social engineering lure), the public’s obsession with anything contemporary, newsworthy and popular allows cross-platform attacks to appear and take victims.
Another factor is the popularity of inter-connectivity between mobile devices and laptops/desktops. With mobile devices no longer being just phones and serve as computer substitutes in their own right, users are often connecting their mobile devices to their home/work systems to sync their files and documents. This link between the devices is what threats use to jump across.
The ever-increasing popularity of mobile devices should also be considered a factor, with cybercriminals continuing to look at the platform as a very viable source of revenue. As such, cybercriminals will continue to develop threats specifically for it and/or include it in their attacks.
While the cross-platform mobile threats detected thus far have not yet utilized a mobile vulnerability, we can’t ignore that the Android fragmentation problem could also contribute to their existence. Google has definitely exerted efforts trying to resolve this particular issue, but much of its device ecosystem is still unable to update to later, more secure versions of the OS. As a result, vulnerabilities are left unpatched, and cybercriminals may soon add these still-existent vulnerabilities to their cross-platform mobile threat repertoire.
What Could We Expect from Cross-Platform Threats?
Based on what we’ve seen, it’s likely that we'll be seeing more and more cross-platfom threats in the future – especially those that start on mobiles and make the jump to desktops. We’ve seen this already happen with ANDROIDOS_USBATTACK.A – and while it may not have caused too much damage on the desktop side, an enterprising cybercriminal could easily replace the wire-tapping malware with something else, such as bitcoin miners or backdoors. We believe that more of these types of cross-platform threats will surface.
Cybercriminals may also use mobile devices as a sort of ‘carrier’ for malware that could facilitate targeted attacks against big and powerful targets, like companies or government agencies.
The infected mobile device, once connected or synched with a business system, could then spread and infect the network from within, stealing business-critical information. The reverse can also happen – where a targeted attack that has already penetrated a business network can target the mobile devices that connect to the network.
The latter scenario already a reality – with our monitoring of a LuckyCat C&C server (LuckyCat being an infamous targeted attack campaign), we found two malicious Android apps coded to steal critical information from infected mobiles stored in the server itself. We believe that the cybercriminals responsible for LuckyCat were planning to spread these malicious apps into the networks of the organizations they’ve already infiltrated, to infect the mobile devices of the organizations’ employees (to steal their personal information).
The apps in question were also discovered to have remote access tool (RAT) capabilities, allowing them to download and install other malware, making them that much more dangerous.
Lastly, cybercriminals may also try to hack into home automation systems by way of mobile-to-PC threats. An example scenario: when a user connects their infected mobile device to the home network or to a PC connected to the said network, the malware could spread through this connection and take control of the home automation. This not only exposes the family and their devices/desktops to malware, but may also allow cybercriminals to wreak havoc upon their home and safety.
An infected home automation system could potentially be manipulated to record the goings-on inside the house, compromising the family’s privacy. Cybercriminals may also manipulate the system to disengage any security measures inside the house – allowing burglars or robbers to enter the house easily. The danger is there, and it is real.
What Can Be Done?
Cross-platform threats, whether they include mobiles in their range of attack or not, are more dangerous because they can ‘hop’ from platform to platform, increasing their potential to do more damage. Not only can they affect their original victim, but also the victim’s other devices, or even the network that they connect to (in turn, making victims of the other systems in the network). The damage would be exponential if left unchecked.
And all it takes is one infected device or system to get the chain reaction going.
While we cannot do anything about the factors that make cross-platform threats effective, we can secure the points that the cross-platform threats themselves attack – namely, our mobile devices and our desktops.
Whether in a work or home environment, devices must be hardened, security-wise, in order to protect against threats that can jump from one platform to the next. Security solutions exist for nearly every platform that the cybercriminals can potentially attack, and to go without them is to invite cybercriminal activity to happen.
Their users must also be educated with these threats, how to recognize them, how to avoid them, and what to do if they suspect that they've been affected. By securing the endpoints, the chain of infection be broken.
HIDE
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Posted in Mobile Safety, Mobile Malware
 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report The Road to Agentic AI: Navigating Architecture, Threats, and Solutions
The Road to Agentic AI: Navigating Architecture, Threats, and Solutions