
Ransomware is devastating for a business because it damages critical data. During an attack, ransomware scans for important files and encrypts them with strong encryption that cannot be reversed, crippling an organization faster than other malicious applications.
Table of Contents
How a ransomware threat begins
Most ransomware attacks start with a malicious email. The email often contains a link to an attacker-controlled website where the user downloads the malware. It could also contain a malicious attachment with code that downloads ransomware after the user opens the file.
Attackers usually use Microsoft Office documents as attachments. Office has a Visual Basic for Applications (VBA) interface that attackers use to program scripts. Newer Office versions disable the feature that automatically runs macro scripts when a file opens. The malware prompts the user to run the scripts, and many users do. This is why malicious macros are still dangerous.
The Office macro downloads the ransomware from an attacker’s server, and the malware runs on the local device. The ransomware scans the network and local storage for critical files and encrypts what it finds. Encryption is typically symmetric Advanced Encryption Standard (AES) cryptography using 128 or 256 bits. It makes the process resistant to brute-force attacks. Some ransomware also uses public / private key cryptography such as Rivest-Shamir-Adleman (RSA).
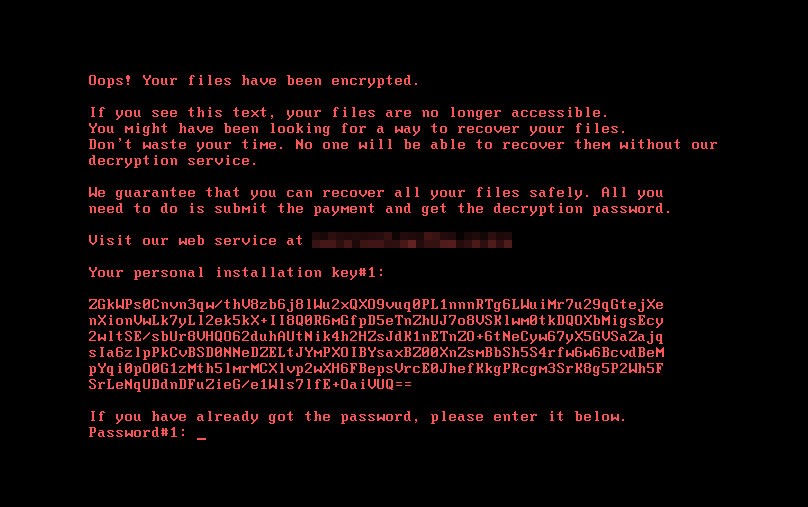
Recovering data and removing ransomware
Ransomware developers build in functionality that blocks users from removing the application without first paying the ransom. Some hackers use screen lockers so users cannot access the Windows desktop. Because the cryptography libraries used to encrypt files are secure, removing the malware still leaves data encrypted and inaccessible.
The FBI advises affected businesses not to pay the ransom. Other experts say that paying the ransom has resulted in file decryption. Sometimes the attackers do not deliver the decryption key even after the ransom is paid. The targeted business is then left with no files and a monetary loss. You can remove the ransomware, but it is unlikely you’ll be able to recover the files without paying the ransom unless you have a backup.
Most anti-malware vendors have patches or downloadable solutions that remove ransomware. After clearing the malware, you can restore files from a backup. You can also restore the computer to factory settings. With the latter solution, your computer returns to the same state as when you first bought it. You would need to reinstall any third-party software.
Ransomware protection
You can protect devices and data from ransomware in several ways. Since infection usually starts with a malicious email message, start with anti-malware cybersecurity that scans incoming messages for suspicious links or attachments. If found, quarantine the messages, keeping them from reaching user inboxes.
Content filtering on the network is also effective. It stops users from accessing attacker-controlled websites. Combined with email filters, content filtering is an effective way to stop ransomware and most malware from accessing your internal network.
Anti-malware software should run on all network devices including smartphones. Anti-malware stops ransomware from encrypting files and removes it from the system before it sends the payload. If the organization has a bring-your-own-device (BYOD) policy, it is important to run an approved anti-malware application on user devices.
User training is a proactive way to protect from ransomware. Since ransomware often starts with phishing and social engineering, users trained to identify attacks are a good addition to other anti-malware measures. Combined, training and anti-malware systems greatly reduce cybersecurity risk. If anti-malware systems fail, users trained to identify an attack are not tricked into running malicious executables.
Ransomware examples
Several types of ransomware still affect businesses, even though the malware’s global threat was generally removed. They exist to extort money from individuals or businesses that don’t have effective protection in place.
One of the first known ransomware applications that made a global impact was CryptoLocker. CryptoLocker targeted Windows machines and was widespread in 2014. Infection usually started with an email and a malicious attachment. The software then encrypted important files with asymmetric (RSA) public / private key encryption.
RansomHub
RansomHub is a Ransomware-as-a-Service (RaaS) group first detected in February 2024 and has rapidly gained notoriety for its "big game hunting" strategy, by targeting large enterprises more likely to pay substantial ransoms. Tracked by Trend Micro as Water Bakunawa, RansomHub has been observed exploiting vulnerabilities in cloud storage backups and misconfigured Amazon S3 instances, leveraging the trust between providers and clients to enhance their extortion tactics.
Rhysida
Rhysida is a ransomware group that came to light in early 2023, employing double extortion tactics by both encrypting victims' data and threatening to publish it unless a ransom demand is paid in Bitcoin. They masquerade as a cybersecurity team offering to help their victims by highlighting security weaknesses in their networks and systems. They will use Phishing attacks to gain initial access and follow up with Cobalt Strike beacons for lateral movement in compromised machines before deploying their ransomware.

2024 Top Ransomware Intrusion Sets
Trend Micro’s 2024 data on the cybercriminal underground tracks information posted on ransomware groups’ leak sites.

In the Top Ransomware Intrusion Sets table, “breaches” refer to successful ransomware attacks on enterprises that chose not to pay ransom. This means that the actual number of successful attacks might be higher as some companies might have paid the ransom.
Trend Micro leak site monitoring shows that ransomware groups have the most victim enterprises from North America, with 369 successful breaches on companies that did not pay ransom in that region. Leak sites also published 104 successful breaches from enterprises in Europe and 47 from Asia. Companies in retail, wholesale, and distribution make up most of the breaches published in leak sites (13.9%), followed by enterprises from industrial products and services (9.4%).
Ransomware groups also published that they have victims from the transportation industry, information technology, and technology industries which make up the top five industries affected by ransomware attacks. Region and industry rankings on successful ransomware attacks likely reflect more on the resilience against ransomware attacks of enterprises from each region and industry, rather than ransomware group behavior, as they do not target regions or industries specifically. Enterprises can increase their resilience against ransomware attacks by making endpoint sensors work for them.
2024 Top Ransomware Intrusion Sets

This heatmap presents the regions and countries that Trend Micro telemetry tracked as having the most ransomware threat activity. Figures in each map represent ransomware threats that have been detected and blocked by our sensors. It’s important to note that cybercriminals do not target any country or region specifically. However, these numbers show areas that should take extra precautions to make enterprise systems more resilient against ransomware attacks.
Preventing ransomware
The above examples are just a few ransomware versions that still plague organizations. Ransomware developers continue to create new ways to hold files hostage for a ransom. If you understand how ransomware works, you can implement the right defenses. You can prevent ransomware with an effective anti-malware solution, user training, and email filters that block malicious messages.
Trend Micro Cyber Risk Report - 2025
Ransomware is a form of cyber extortion where attackers encrypt critical data and demand payment for its release. As highlighted in the Trend Micro 2025 Cyber Risk Report, ransomware remains one of the most visible and financially damaging threats to organizations worldwide.
Ransomware operators are no longer relying solely on traditional entry points like phishing emails or exposed RDP ports. Instead, they are exploiting overlooked and emerging vulnerabilities across an organization's digital ecosystem—what cybersecurity experts call the attack surface.
Discover how ransomware threats are evolving and what proactive strategies can help mitigate risk in Trend Micro’s 2025 Cyber Risk Report
How Trend Micro Helps You Stay Ahead of Ransomware Threats
As ransomware continues to be one of the most disruptive threats facing organizations today, the need for a unified, intelligent defense has never been greater. Trend Vision One™ offers a powerful solution that goes beyond traditional security tools—providing extended detection and response (XDR), attack surface risk management, and automated threat mitigation in a single, integrated platform.
With Trend Vision One™, security teams gain centralized visibility across endpoints, email, cloud, and network layers, enabling faster detection and response to ransomware activity. Backed by decades of threat intelligence and powered by Trend Micro’s Cybersecurity AI, the platform helps organizations proactively identify vulnerabilities, reduce exposure, and stop ransomware before it can cause damage.