
Ransomware is malware that encrypts important files on local and network storage and demands a ransom to decrypt the files. Hackers develop this malware to make money through digital extortion.
Table of Contents
Understanding the Meaning of Ransomware and how it targets important information
Ransomware is encrypted, so the key cannot be forced and the only way to recover the information is from a backup.
The way ransomware works makes it especially damaging. Other types of malware destroy or steal data but leave other recovery options open. With ransomware, if there are no backups, you must pay the ransom to recover the data. Sometimes businesses pay the ransom, and the attacker does not send the decryption key.
Once the ransomware starts to work, it scans local and network storage, looking for files to encrypt. It targets files it assumes are important to your business or to individuals. This includes backup files that could help recover the information. Following are a few file types ransomware targets:
- Microsoft Office: .xlsx, .docx, and .pptx plus older versions
- Image: .jpeg, .png, .jpeg, .gif
- Business-related images: .dwg
- Data: .sql and .ai
- Video: .avi, .m4a, .mp4
Different types of ransomware target different sets of files, but there are also common targets. Most ransomware targets Microsoft Office files because they often store critical business information. Targeting important files increases the chance that you will pay the ransom.
Types of Ransomware
Leakware or Doxware
Leakware, also known as doxware, takes ransomware threats to a new level by not only encrypting files but also threatening to release sensitive or confidential data if the ransom is not paid. Unlike traditional ransomware, where the focus is on preventing access to data via encyrption, leakware takes advantage of people's fear of public exposure. Hackers will often use leakware as part of a double extortion strategy, demanding payment for both decryption and preventing data leaks.
Mobile Ransomware
Since mobile devices have become central to personal and business activities, it has made them become targets for ransomware attacks. Mobile ransomware often spreads through malicious apps or phishing messages. Once installed, the malware locks the device, displays ransom messages, or encrypts local storage, preventing users from accessing their apps, photos, and contacts. Hackers will typically demand payment in cryptocurrency to unlock the device.
Wipers
Wipers are among the most destructive forms of ransomware. Instead of encrypting files for ransom, wipers are designed to permanently delete or corrupt data, leaving no chance of recovery. These attacks often aim to cause chaos, disrupt operations, or send a political or ideological message. Wipers are sometimes disguised as traditional ransomware, tricking victims into paying a ransom even though the data is already irreversibly lost.
Scareware
Scareware relies on psychological manipulation to extort money from victims. It will often pose as an antivirus software or system alerts, claiming that the victim’s device is infected with malware or has critical vulnerabilities. The software then demands payment to "fix" the nonexistent problems. While scareware does not always encrypt files, it can lock users out of their systems or bombard them with persistent pop-up messages until a ransom is paid. Scareware preys on fear and lack of technical knowledge, making it an effective tool for targeting less tech-savvy users.
Phishing emails often contain ransomware
Ransomware is different from other malware because of what it does after it activates. It usually executes when a user opens an attachment or clicks on a link in a phishing email. The malware then downloads from an attacker-controlled server.
After ransomware downloads, it can stay dormant on your network drive or run directly on an infected computer. When it runs, it scans available local and network storage systems for targeted file extensions and encrypts them. Encryption is either asymmetric or symmetric, but many recent ransomware attacks use both.
Attackers demand payment
An attacker always demands payment in cryptocurrency, mainly Bitcoin. Taking payments this way reduces the risk of being caught. Attackers also use servers behind TOR, an anonymity network, to avoid being identified.
After the ransomware encrypts the files, it displays a message to your business. The attackers demand payment in exchange for keys to unlock the files. The ransom can be a few hundred dollars or a few million. If you do not not pay right away, the malware increases the ransom.
Some ransomware attacks feature double extortion. The attacker demands a fee to release the files. It also posts a list of organizations that were attacked but refused to pay. Double extortion further motivates the you to pay the ransom and avoid damage to your brand.
Ransomware is evolving
There are variations of ransomware that differ in how they encrypt data and stop users from getting the decryption key. Older ransomware used client or server asymmetric encryption or simple symmetric encryption. Newer ransomware combines the two to increase an attack’s effectiveness.
Symmetric encryption
Ransomware hackers today rarely use symmetric encryption alone. Symmetric encryption by itself uses a single key for encryption and decryption. The key is often stored on the local system. There, specialists and researchers can find it and decrypt the data without paying the ransom. To resolve this issue, hackers now more commonly use hybrid cryptography.
Client-side asymmetric encryption
Asymmetric encryption uses a public key to encrypt data, and a separate, private key to decrypt it. One common encryption method is RSA cryptography, which HTTPS also uses. RSA is slower than symmetric encryption, and all files must be encrypted before the attacker can send the private key to the server.
The software finishes encrypting, sends the private key to the attacker’s server, and deletes it from local storage. The risk is that the computer goes offline before encryption is complete. In that case, the private key is never transferred to the attacker’s server. The attacker is then unable to demand a ransom.
Server-side asymmetric encryption
Server-side asymmetric encryption solves the problem of client-side encryption by encrypting files when the computer comes online. The attacker’s server generates a private / public key pair and encrypts files with the server’s public key.
When you pay the ransom, the attacker transfers the private key for decryption. The risk to the attacker is that when the private key transfers, you can intercept and get the key. The risk to the attacker is that when the private key transfers, you can intercept and get the key, which can then be shared with other affected businesses, making the ransomware useless.
Hybrid encryption
Hackers discovered that the earlier versions of ransomware were vulnerable, so they designed hybrid versions. In the hybrid versions, the software generates two sets of keys, and a chain of encryption solves the issues with the older versions. The chain of encryption works like this:
- The symmetric key encrypts files.
- The software generates a client-side key pair. The client-side public key encrypts the symmetric key file.
- The software generates a server-side key pair. The server-side public key encrypts the client-side private key, and it then goes to the attacker.
- When you pay the ransom, the server-side private key decrypts the client-side private key, and this key goes to your business where the encryption chain reverses.
How to Prevent ransomware with backups
The best way to protect against ransomware is with backups. Backup files stored locally or on a network drive are vulnerable. Cloud storage is protected from ransomware network scans, so it is a good solution for recovery. An exception is if you map cloud storage as a local drive or subfolder.
To prevent ransomware damage, it is best to stop it before it starts. Most attacks start when users unintentionally download the software directly or run a malicious script by accident.
Two ways to stop users from downloading ransomware are DNS-based content filtering and email cybersecurity that incorporates artificial intelligence quarantining. DNS-based content filtering stops users from browsing blacklisted websites. Email filters send malicious content and attachments to quarantine for administrator review.
Finally, always run anti-malware software with machine learning and behavior monitoring on every device including mobile. A good anti-malware application detects ransomware before it can access memory and encrypt files. For greatest effectiveness, anti-malware software must always be patched and up to date so it can recognize the latest threats.
Ransomware attacks affect thousands
Ransomware attacks affect thousands of users globally. In some cases, even after victims think the ransomware is contained, it can continue to cause issues. Anti-malware programs catch many older versions, but hackers continually develop new types to avoid detection.
For instance, in 2018 and 2019, Ryuk ransomware disabled Windows System Restore functionality. Users were then unable to recover from a previous restore point in the operating system. Because it targeted businesses, Ryuk demanded hundreds of thousands of dollars in ransom.
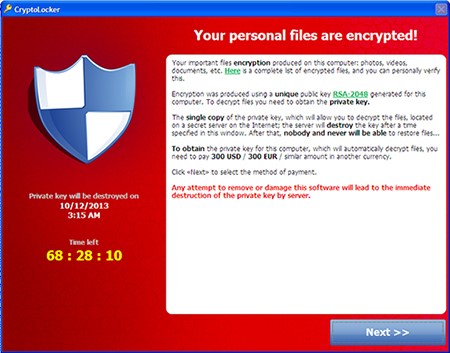
CryptoLocker, WannaCry, and Petya were all different forms of ransomware that caused global infrastructure shutdowns, affecting even banks and government agencies. WannaCry, in particular, targeted Windows machines and used an exploit developed by the United States National Security Agency (NSA) to scan open network drives and encrypt vulnerable files.
Ransomware threats that persist include Gandcrab, SamSam, Zeppelin, and REvil. While these variants are newer, they still persist as dangerous malware with the ability to destroy corporate systems.

Source: David Sancho - Senior Threat Researcher - Trend Micro
Trend Micro Cyber Risk Report - 2025
Ransomware is a form of cyber extortion where attackers encrypt critical data and demand payment for its release. As highlighted in the Trend Micro 2025 Cyber Risk Report, ransomware remains one of the most visible and financially damaging threats to organizations worldwide.
Ransomware operators are no longer relying solely on traditional entry points like phishing emails or exposed RDP ports. Instead, they are exploiting overlooked and emerging vulnerabilities across an organization's digital ecosystem—what cybersecurity experts call the attack surface.
Discover how ransomware threats are evolving and what proactive strategies can help mitigate risk in Trend Micro’s 2025 Cyber Risk Report
How Trend Micro Helps You Stay Ahead of Ransomware Threats
As ransomware continues to be one of the most disruptive threats facing organizations today, the need for a unified, intelligent defense has never been greater. Trend Vision One™ offers a powerful solution that goes beyond traditional security tools—providing extended detection and response (XDR), attack surface risk management, and automated threat mitigation in a single, integrated platform.
With Trend Vision One™, security teams gain centralized visibility across endpoints, email, cloud, and network layers, enabling faster detection and response to ransomware activity. Backed by decades of threat intelligence and powered by Trend Micro’s Cybersecurity AI, the platform helps organizations proactively identify vulnerabilities, reduce exposure, and stop ransomware before it can cause damage.
Frequently Asked Questions (FAQ's)
What is ransomware?
Ransomware is a type of malware that locks or encrypts your data and demands payment for its release.
How can you detect ransomware?
Look for unusual file extensions, locked files, a ransom note, or sudden system slowdown.
How do I know if I have ransomware?
You may see a ransom message on screen, be unable to open files, or notice strange system behavior.
What happens if you get ransomware?
- Ransomware locks or encrypts your files, and the attacker demands payment to restore access. This can disrupt your operations, compromise sensitive data, and cause significant downtime.
How do you remove ransomware?
Disconnect the infected device, run a malware scan, and restore clean backups. Avoid paying the ransom.
What is the most important protection against ransomware attacks?
Regular backups, employee training, and up-to-date security software are key to prevention.