Updated as of March 13, 2017, 8:06 PM, UTC-7: We updated the section on Trend Micro solutions, particularly on Deep Security™.
Updated as of August 9, 2017, 10:42 PM, UTC-7: We updated the section on Trend Micro solutions, particularly on Deep Discovery Inspector.
Apache Struts is a free and open-source framework used to build Java web applications. We looked into past several Remote Code Execution (RCE) vulnerabilities reported in Apache Struts, and observed that in most of them, attackers have used Object Graph Navigation Language (OGNL) expressions. The use of OGNL makes it easy to execute arbitrary code remotely because Apache Struts uses it for most of its processes.
Using OGNL, a researcher found a new remote code execution vulnerability in Apache Struts 2, designated as CVE-2017-5638. An exploit has been reported to be already in the wild; our own research and monitoring have also seen attacks using the vulnerability.
Attack Scenario
This particular vulnerability can be exploited if the attacker sends a crafted request to upload a file to a vulnerable server that uses a Jakarta-based plugin to process the upload request. The attacker can then send malicious code in the Content-Type header to execute the command on a vulnerable server. A proof of concept that demonstrates the attack scenario is publicly available.
Vulnerability Dissection
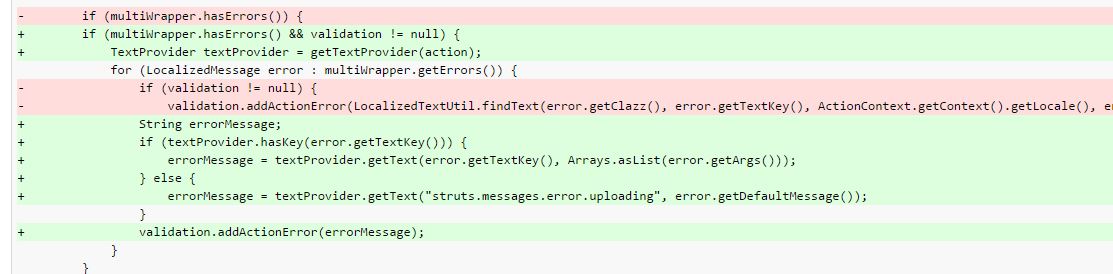
We took a closer look at the patch to further understand the vulnerability and found that the vendor removed the usage of Class “LocalizedTextUtil” from FileUploadInterceptor.java. This was meant to give an error message to the user if the file upload, using multipart HTTP request, is not successful.
Figure 1: Patch diff code snapshot
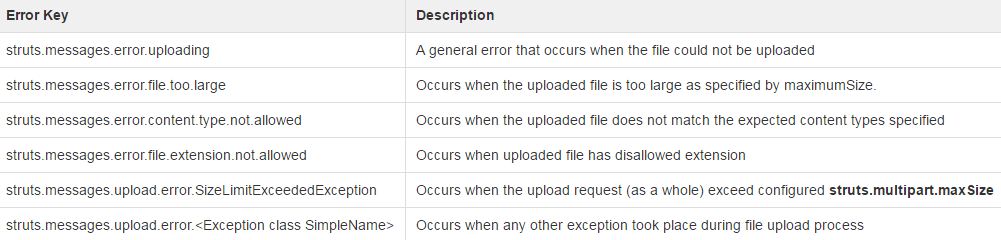
To provide an appropriate error message to the user, it used the function “findText” defined in LocalizedTextUtil to parse the error key message and get the defined error message for it.
Figure 2: Defined error messages in Apache Struts’ File Upload function
The findText function definition is:
public static String findText(Class aClass, String aTextName, Locale locale, String defaultMessage, Object[] args )
This function finds a locally saved text message for the given error key passed in variable “aTextName”. The parameters are:
aClass: FileUploadInterceptor passes the error class to use as the start point of the error message search
aTextName: the error key used to find the error message for it
Locale: the locale where the message is saved for the respective error key
defaultMessage: the message to be returned if no text message can be found in any resource bundle
args: the error arguments’ resource bundle
If the message is found, those will be treated as an OGNL expression and evaluated as such. So, if an attacker passes the OGNL expression in Content-Type header with “multipart/form-data”, it will be evaluated and could help the attacker to execute arbitrary code remotely.
To fix this issue, the vendor has removed the usage of class “LocalizedTextUtil”, along with “java.io.File”, which can be used to output the RCE result to the attacker.
Apache Struts versions Struts 2.3.5 - Struts 2.3.31, Struts 2.5 - Struts 2.5.10 are reported to be affected. If you are using the Jakarta-based file upload Multipart parser, upgrading to Apache Struts version 2.3.32 or 2.5.10.1 is recommended. You can also switch to a different implementation of the Multipart parser.
Trend Micro Solutions
Trend Micro™ Deep Security™ protects endpoints from threats that exploit vulnerabilities. Trend Micro™ Deep Discovery™ provides detection, in-depth analysis, and proactive response to attacks using exploits and other similar threats through specialized engines, custom sandboxing, and seamless correlation across the entire attack lifecycle, allowing it to detect these kinds of attacks even without any engine or pattern update.
Deep Security™ provides protection from any threats that may target this vulnerability via the following DPI rule:
- 1008207 - Apache Struts2 Remote Code Execution Vulnerability (CVE-2017-5638)
Deep Discovery Inspector protects customers from this threat via this DDI Rule:
- 2348 - CVE-2017-5638 - APACHE STRUTS EXPLOIT - HTTP (Request)
- 2352 - CVE-2017-5638 - APACHE STRUTS EXPLOIT - HTTP (Request) - Variant 2
TippingPoint customers are protected from this threat via these Custom Shield Writer (CSW) and MainlineDV filters:
- CSW: HTTP: Apache Struts Content-type Command Injection Vulnerability (CVE-2017-5638)
- 27410: HTTP: Apache Struts Content-type Command Injection Vulnerability (CVE-2017-5638)