Key Takeaways:
- Trend™ Research uncovered a campaign that makes use of Charon, a new ransomware family, and advanced APT-style techniques, including DLL sideloading, process injection, and anti-EDR capabilities, to target organisations with customised ransom demands.
- This recently identified ransomware campaign poses a significant business risk, leading to potential operational disruptions, data loss, and financial costs tied to downtime. The ransomware operator’s tactics can compromise both local and networked data, hampering recovery efforts.
- Trend Vision One™ detects and blocks specific Charon ransomware-linked indicators of compromise (IOCs) highlighted in this blog. Customers can also access tailored hunting queries, threat insights, and intelligence reports to better understand and proactively defend against Charon.
We recently identified a new ransomware family called Charon, deployed in a targeted attack observed in the Middle East's public sector and aviation industry. The threat actor employed a DLL sideloading technique notably similar to tactics previously documented in the Earth Baxia campaigns, which have historically targeted government sectors. The attack chain leveraged a legitimate browser-related file, Edge.exe (originally named cookie_exporter.exe), to sideload a malicious msedge.dll (SWORDLDR), which subsequently deployed the Charon ransomware payload.
Analysis of the msedge.dll component revealed it was designed to load a file named DumpStack.log, which was absent from our initial telemetry. Through forensic investigation, we recovered this missing file and confirmed it contained encrypted shellcode. Upon decryption, we identified the payload as Charon ransomware—marking the first documented instance of this ransomware family in the wild.
The ransomware's custom ransom note specifically references the victim organisation by name, confirming this was a targeted operation rather than opportunistic campaign. This targeted approach, combined with the distinctive DLL sideloading methodology, raises questions about potential connections to Earth Baxia. While we observe technical overlap—particularly the specific toolchain of using the same binary with a DLL to deploy encrypted shellcode—we cannot definitively attribute this attack to Earth Baxia. The techniques could represent either direct involvement, deliberate imitation, or independent development of similar tactics. Without corroborating evidence such as shared infrastructure or consistent targeting patterns, we assess this attack demonstrates limited but notable technical convergence with known Earth Baxia operations.
This case exemplifies a concerning trend: the adoption of APT-level techniques by ransomware operators. While DLL sideloading is not unique to any single group, the specific implementation observed here—matching toolchains and encrypted payload delivery—represents a sophistication typically associated with advanced persistent threats. This convergence of APT tactics with ransomware operations poses an elevated risk to organisations, combining sophisticated evasion techniques with the immediate business impact of ransomware encryption.
Charon ransomware attack chain
The attack chain observed in this incident uses DLL sideloading to facilitate the execution of the Charon ransomware payload. The threat actor initiates the intrusion by executing a legitimate Edge.exe binary, which is abused to sideload a malicious DLL named msedge.dll, also known as “SWORDLDR”. This loader is responsible for decrypting the embedded ransomware payload and injecting it into a newly spawned svchost.exe process. This technique allows the malware to masquerade as a legitimate Windows service, bypassing usual endpoint security controls.
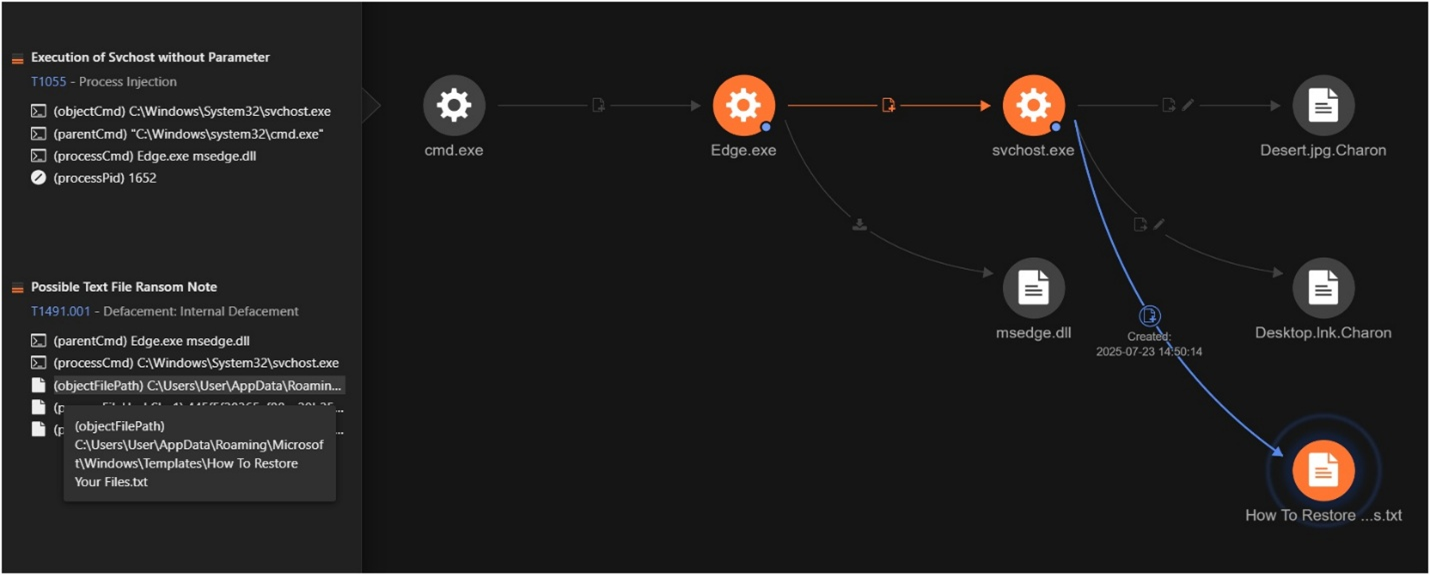
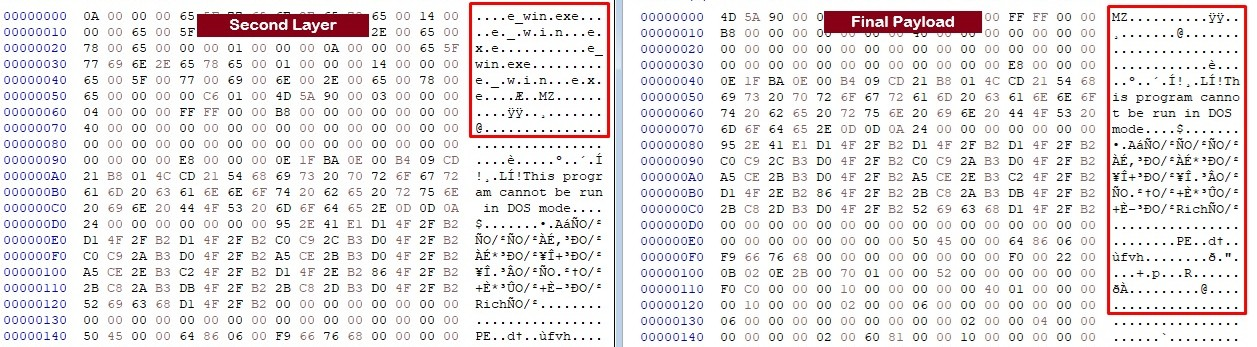
Charon uses a multistage payload extraction technique.During our investigation, DumpStack.log was identified as a critical component of the attack chain. Although it initially appeared to be a benign log file, further analysis revealed that it contained an encrypted shellcode responsible for delivering the ransomware payload. Decryption of the first layer revealed another payload. This additional layer included embedded configuration data, specifically indicating the use of svchost.exe for process injection, as highlighted in the Figure 2.
Further analysis revealed a second layer of encryption within the intermediate payload. After decrypting this layer, the final portable executable (PE) file was extracted, which we confirmed to be the Charon ransomware payload based on the observed file encryption activity.
Technical analysis of the Charon ransomware
The recovered executable, now free from its obfuscation layers, revealed sophisticated encryption capabilities and operational characteristics.
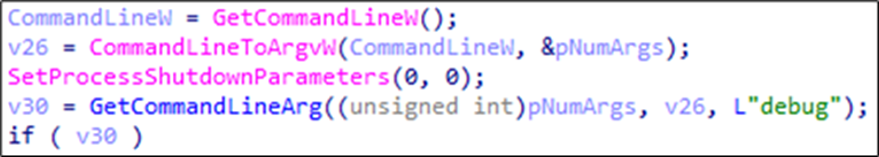
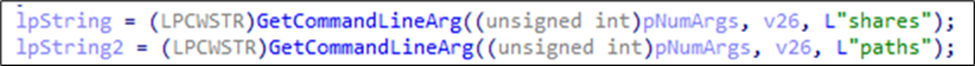
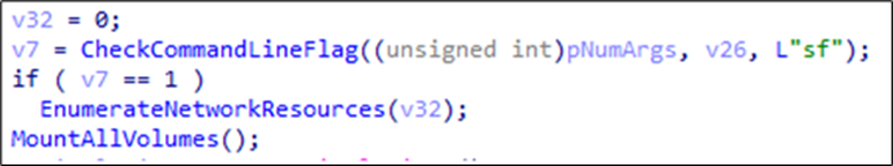
Upon initialisation, Charon accepts several command-line parameters that significantly influence its behaviour. The ransomware cheques for the following arguments:
| --debug=<path + file name > | Enables error logging to specified file path. Logs all errors during encryption |
| --shares=<network shares> | Lists network server names/IP addresses to target, as well as enumerates and encrypts all accessible shares on these servers (except ADMIN$) |
| --paths=<specific path> | Lists specific paths or drive letters to encrypt, which can be local paths (C:\folder) or drive letters (D:) |
| --sf | Refers to “Shares First” when this flag is set, it changes the encryption order, with network shares prioritised first, then local drives and vice versa |
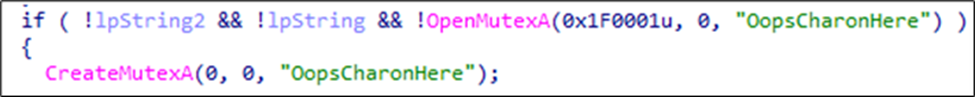
It creates a mutex named OopsCharonHere.
Before initiating its main encryption routine, it performs a series of disruptive actions aimed at maximising its chances of success and minimising the potential for recovery or interference. It stops security-related services and terminates active processes, including security-related services. This ensures that antivirus and endpoint protection software are disabled, reducing the likelihood of detection or interruption. The list of service and process names can be found here.
Following this, it systematically deletes all shadow copies on the system, eradicating shadow copies and backups that could be used for file restoration. To further hinder recovery efforts, it also empties the contents of the Recycle Bin, ensuring that recently deleted files cannot be easily recovered.
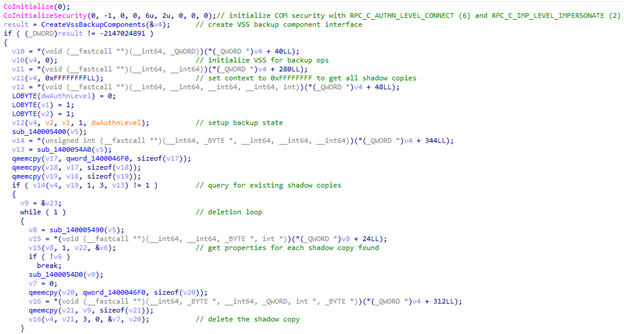
Once these are finished, it counts the number of processor cores available on the system and creates multiple threads dedicated to file encryption. By utilising multithreading, it maximises encryption speed and efficiency, allowing it to rapidly compromise large volumes of data across the infected host.
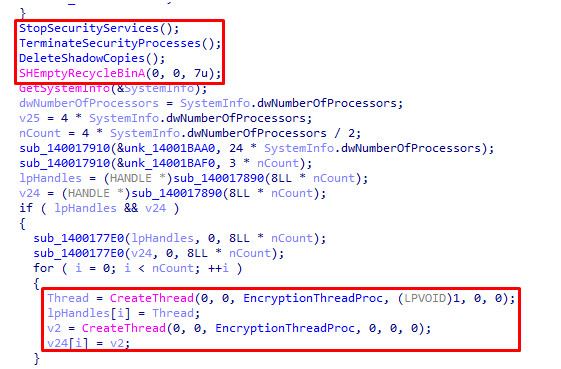
During its encryption routine, it specifically avoids encrypting the following files with the following extensions and file names:
- .exe
- .dll
- .Charon
- How To Restore Your Files.txt
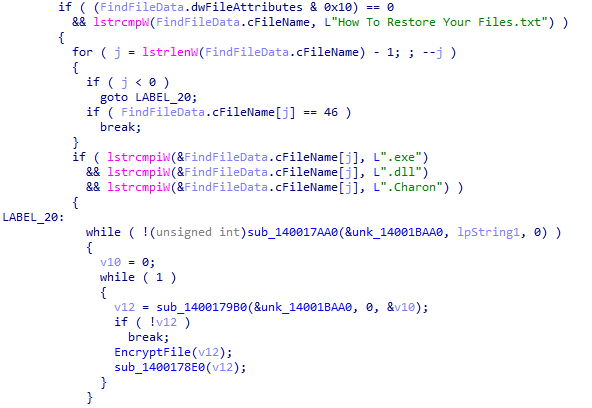
Then, it encrypts the files, appends the .Charon extension, then add an infection marker “hCharon is enter to the urworld!” to the encrypted files.
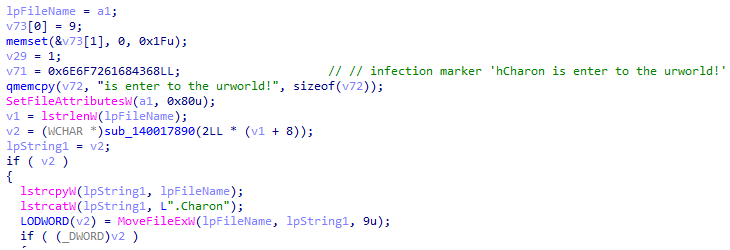
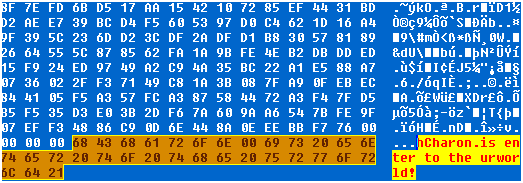
The encryption routine employs a hybrid cryptographic scheme that combines the Curve25519 elliptic curve cryptography with the ChaCha20 stream cypher. It begins by generating a 32-byte random private key using Windows’ cryptographic functions, which is then properly formatted according to Curve25519 specifications.
This private key is used to generate a public key, which is combined with the hardcoded public key (embedded in the binary) to create a shared secret through elliptic curve cryptography. This shared secret is processed through a custom hash function to derive a 256-bit key that initialises a modified ChaCha20 cypher for the actual file encryption. Each encrypted file receives a 72-byte footer containing the victim’s public key and encryption metadata, enabling decryption of files using a private key.
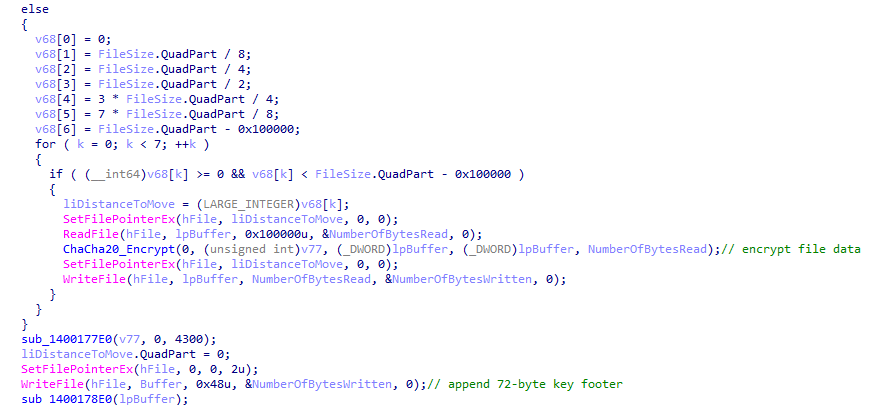
Charon implements the following partial encryption approach to balance speed and effectiveness:
- Files ≤ 64KB: Fully encrypted
- Files 64KB-5MB: Encrypts 3 chunks at beginning (0%), middle (50%), and end (75%)
- Files 5MB-20MB: Encrypts 5 evenly distributed chunks (each 1/5 of file size)
- Files >20MB: Encrypts 7 chunks at positions 0%, 12.5%, 25%, 50%, 75%, 87.5%, and near end
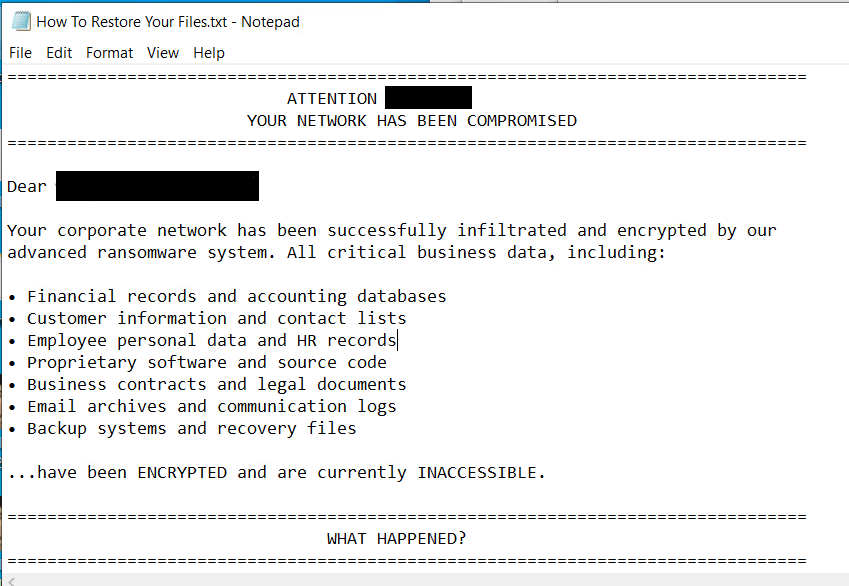
Finally, it drops “How To Restore Your Files.txt” as its ransom note in all drives, networks and directories.
Beyond its core encryption functionality, Charon also exhibits several other notable behaviours. It demonstrates network propagation capabilities, actively scanning for and encrypting accessible network shares across the infrastructure via NetShareEnum and WNetEnumResource. It processes both mapped drives and Universal Naming Convention (UNC) paths, although it skips ADMIN$ shares during enumeration to avoid detection.
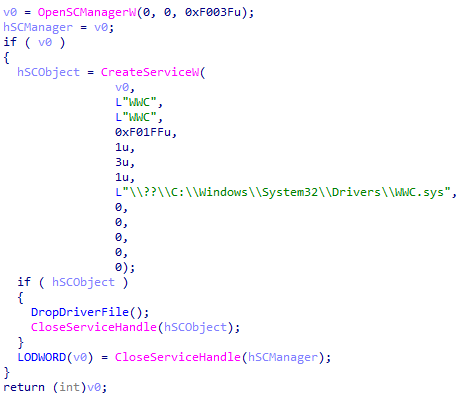
During our analysis of the initialisation routines, we also uncovered an interesting discovery. Charon’s binary includes a package built to slip past endpoint detection and response (EDR) defences. The ransomware includes a driver compiled from the public Dark-Kill project, designed to disable endpoint detection and response solutions.
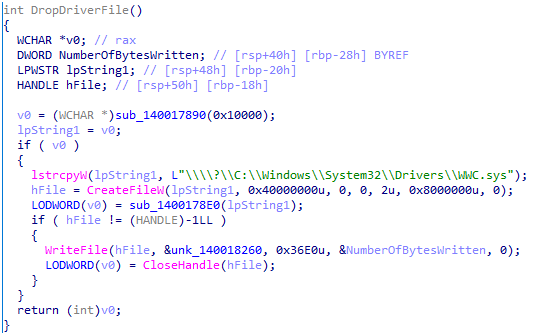
The malware attempts to drop this driver as %SystemRoot%\System32\Drivers\WWC.sys and register it as the "WWC" service. However, our analysis revealed that while this anti-EDR component exists in the data section, it remains dormant and is never called during execution. This suggests that the feature is still under development and hasn't been activated in this variant, possibly reserved for future versions.
Defending against Charon ransomware
Given the Charon threat actor’s blend of stealth, speed, and evasiveness, a multilayered defence is critical. Here are some actionable best practises for security teams:
- Harden against DLL sideloading and process injection by:
- Limiting which executables can run and load DLLs, especially in directories commonly abused for sideloading (e.g., app folders, temp locations).
- Alerting on suspicious process chains, such as Edge.exe or other signed binaries spawning nonstandard DLLs or svchost.exe instances.
- Watching out for unsigned or suspicious DLLs placed next to legitimate binaries.
- ·Ensure that EDR and antivirus agents are running with capabilities that prevent malware from disabling, tampering with, or uninstalling the security solutions.
- Limit lateral movement by restricting access between workstations, servers, and sensitive shares. Disable or closely monitor the use of ADMIN$ and other admin shares. Require strong authentication for all remote access.
- Strengthen backup and recovery capabilities by:
- Maintaining offline or immutable backup copies, separate from production systems, so that backups can’t be wiped by ransomware.
- Regularly validating that backups can be restored and that shadow copy deletion or Recycle Bin emptying won’t block recovery.
- Only allowing backup, shadow copy, and restore rights to specific, monitored accounts.
- Reinforce user awareness and privilege management by:
- Educating end users and training employees to avoid suspicious attachments, links, and executables, which may initiate the sideloading chain.
- Limiting user and service accounts to only the permissions needed for their roles to reduce the impact if a system is compromised.
The Charon ransomware campaign demonstrates the ongoing evolution of ransomware, blending advanced evasion tactics with highly targeted, disruptive capabilities. The convergence of techniques once reserved for APTs compels enterprises to reconsider traditional approaches and strengthen their security posture with layered defences, proactive threat intelligence, and robust incident response. Beyond immediate business disruption, Charon exposes organisations to data loss, operational downtime, reputational harm, regulatory penalties, and substantial financial costs associated with ransom payments and recovery. The targeted nature of these attacks means that even well-defended networks can be compromised, underscoring the urgent need for resilience and readiness at every level of the organisation.
Proactive security with Trend Vision One™
Trend Vision One™ is the only AI-powered enterprise cybersecurity platform that centralises cyber risk exposure management, security operations, and robust layered protection. This comprehensive approach helps you predict and prevent threats, accelerating proactive security outcomes across your entire digital estate. With Trend Vision One, you’re enabled to eliminate security blind spots, focus on what matters most, and elevate security into a strategic partner for innovation.
Trend Vision One™ Threat Intelligence
To stay ahead of evolving threats, Trend customers can access Trend Vision One™ Threat Insights, which provides the latest insights from Trend Research on emerging threats and threat actors.
Trend Vision One Threat Insights
- Threat Actor: Earth Baxia
- Emerging Threats: Threat Actor deploys Charon Ransomware using TTPs previously observed in Earth Baxia operations
Trend Vision One Intelligence Reports (IOC Sweeping)
Hunting Queries
Trend Vision One Search App
Trend Vision One customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
Charon ransomware detection
malName: *CHARON* AND eventName: MALWARE_DETECTION
More hunting queries are available for Trend Vision One customers with Threat Insights entitlement enabled.
Indicators of Compromise (IOC)
The indicators of compromise for this entry can be found here.